Infosec2025 Threat Actors Weaponizing Hardware Devices to Exploit Fortified Environments – Infosecurity Magazine
Published on: 2025-06-05
Intelligence Report: Infosec2025 Threat Actors Weaponizing Hardware Devices to Exploit Fortified Environments – Infosecurity Magazine
1. BLUF (Bottom Line Up Front)
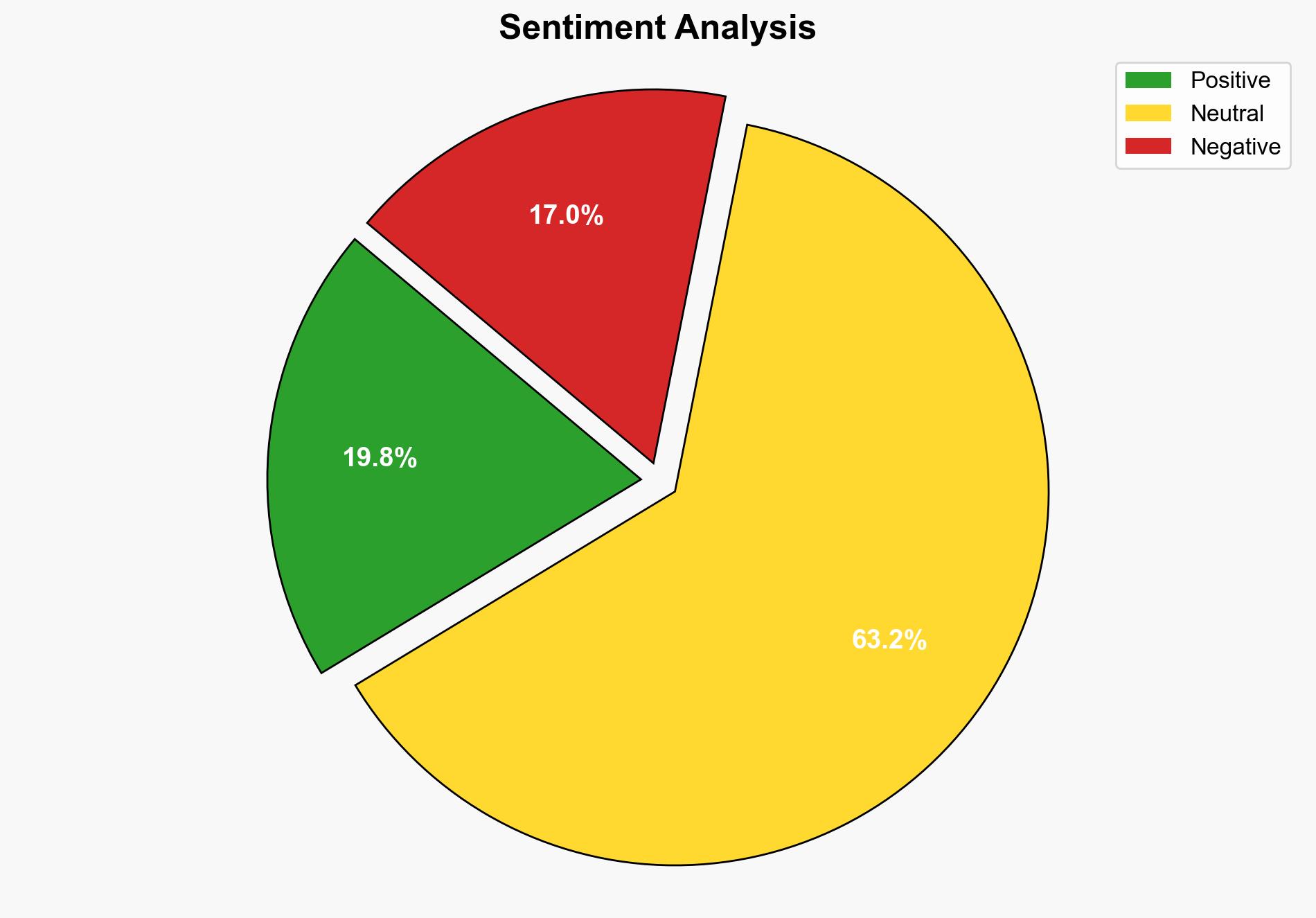
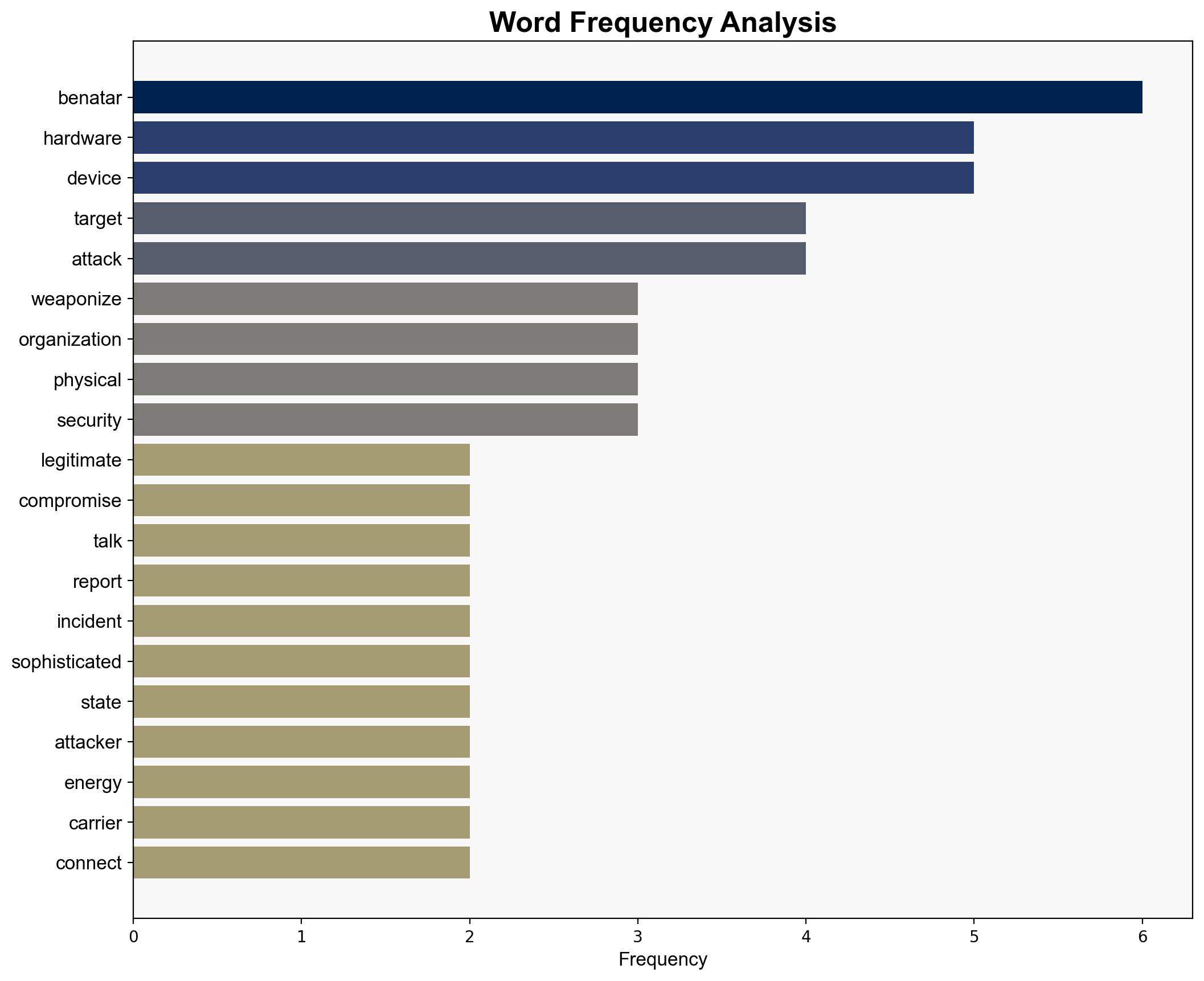
Recent intelligence indicates a significant increase in the weaponization of legitimate hardware devices by threat actors to compromise highly secured environments. These actors, including nation-states and financially motivated groups, are leveraging sophisticated techniques to infiltrate sensitive targets such as banks and energy carriers. It is crucial for organizations to enhance their physical security measures and employ advanced detection systems to mitigate these threats.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
Simulations reveal that adversaries are increasingly using hardware devices smuggled into organizations to bypass traditional cybersecurity defenses.
Indicators Development
Key indicators include unusual network connections and unauthorized device installations, which can serve as early warning signs of potential breaches.
Bayesian Scenario Modeling
Probabilistic models suggest a high likelihood of continued attacks via hardware vectors, with potential for significant data and financial theft.
Network Influence Mapping
Mapping reveals complex relationships between threat actors and their targets, highlighting the need for comprehensive security strategies.
3. Implications and Strategic Risks
The weaponization of hardware devices poses a multi-dimensional threat, impacting not only cybersecurity but also economic stability and national security. The potential for cascading effects is high, as successful breaches can lead to widespread disruption and loss of trust in critical infrastructure.
4. Recommendations and Outlook
- Enhance physical security protocols to prevent unauthorized device installations.
- Implement continuous monitoring systems to detect and respond to anomalies in real-time.
- Consider scenario-based planning to prepare for best case, worst case, and most likely attack scenarios.
- Foster collaboration between industry and government to share intelligence and develop unified defense strategies.
5. Key Individuals and Entities
Bentsi Benatar
6. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus