Infosecurity 2025 NCA cyber intelligence head spells out trends – ComputerWeekly.com
Published on: 2025-06-02
Intelligence Report: Infosecurity 2025 NCA Cyber Intelligence Head Spells Out Trends – ComputerWeekly.com
1. BLUF (Bottom Line Up Front)
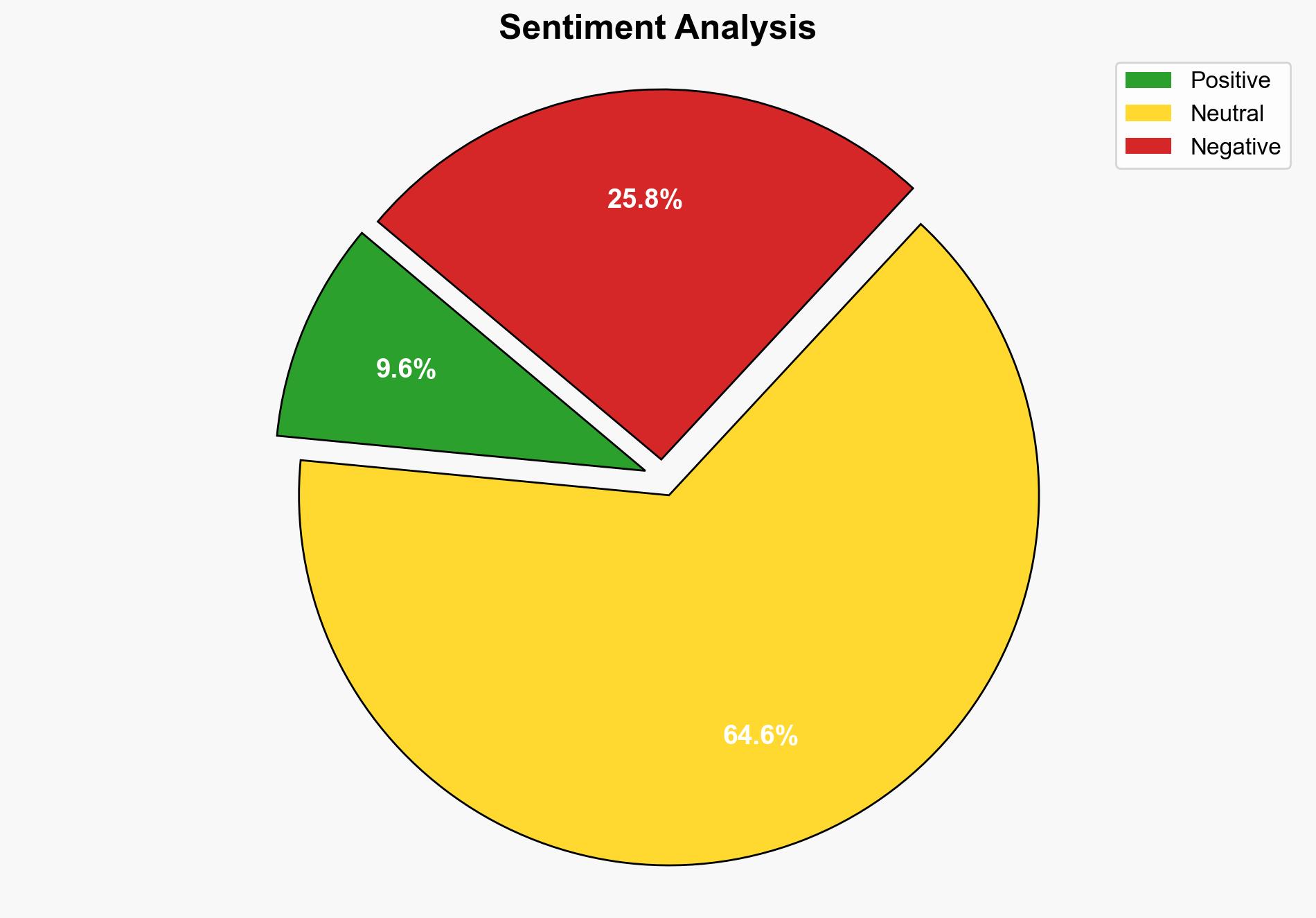
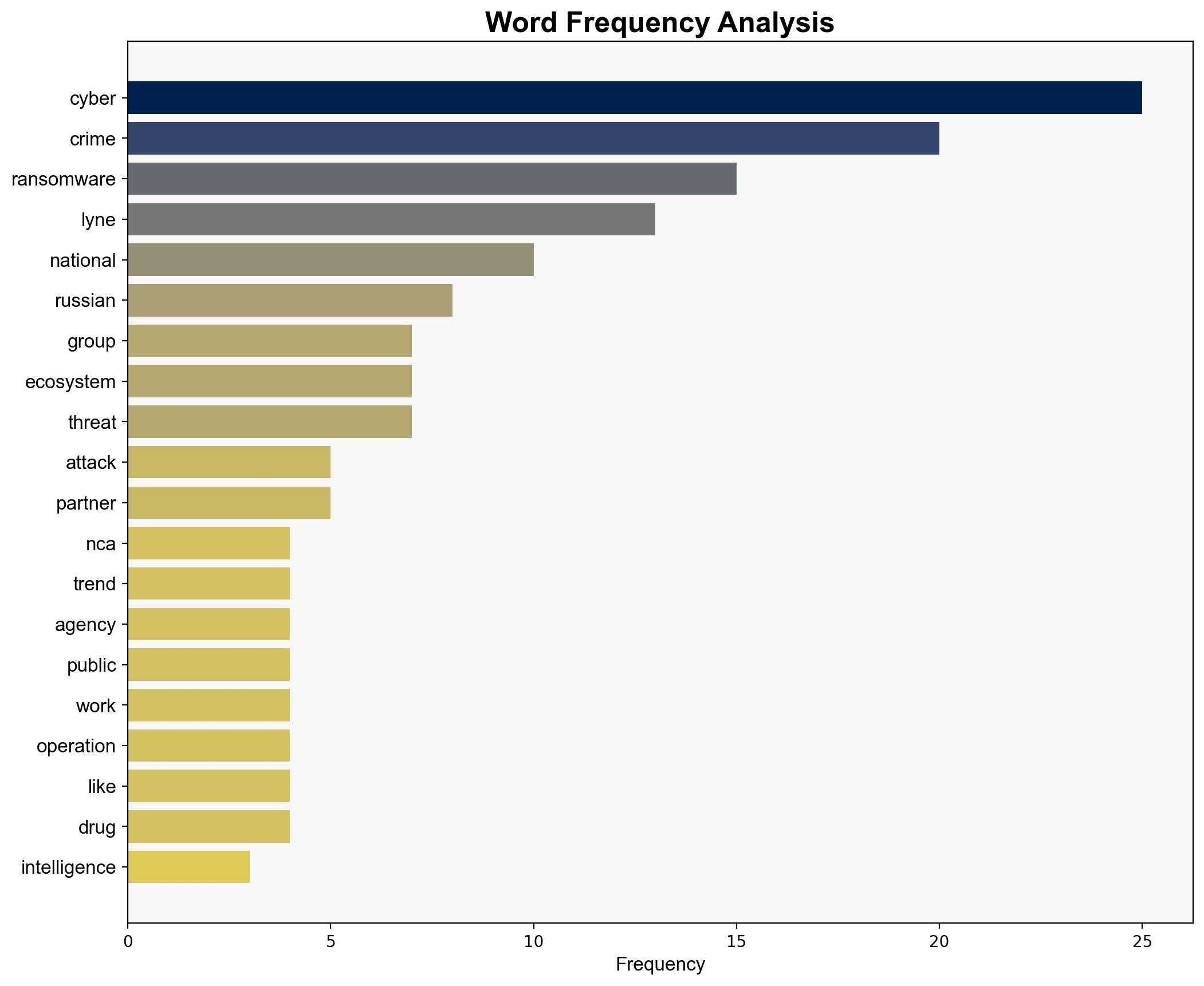
The report highlights the evolving landscape of cybercrime, with ransomware identified as a significant and persistent threat. The democratization of cybercrime tools, facilitated by generative AI, lowers entry barriers for non-traditional actors. The strategic focus should be on enhancing resilience against ransomware and understanding the broader cybercrime ecosystem.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
Simulated actions of cyber adversaries reveal vulnerabilities in critical infrastructure, emphasizing the need for robust defense mechanisms.
Indicators Development
Developed indicators to monitor anomalies, focusing on ransomware patterns and the commoditization of cybercrime tools.
Bayesian Scenario Modeling
Predicted cyberattack pathways, highlighting the increasing sophistication and frequency of ransomware attacks.
Network Influence Mapping
Mapped influence relationships within cybercrime networks, identifying key actors and their potential impact on global security.
3. Implications and Strategic Risks
The proliferation of cybercrime tools poses a significant risk to national security, with potential cascading effects on economic stability and public safety. The integration of AI in cybercrime operations could exacerbate these threats, necessitating a proactive and adaptive defense strategy.
4. Recommendations and Outlook
- Enhance cybersecurity frameworks to address the evolving threat landscape, focusing on ransomware resilience.
- Invest in AI-driven threat detection systems to anticipate and mitigate emerging cyber threats.
- Scenario-based projections suggest a continued rise in ransomware incidents; prioritize cross-sector collaboration for effective response.
5. Key Individuals and Entities
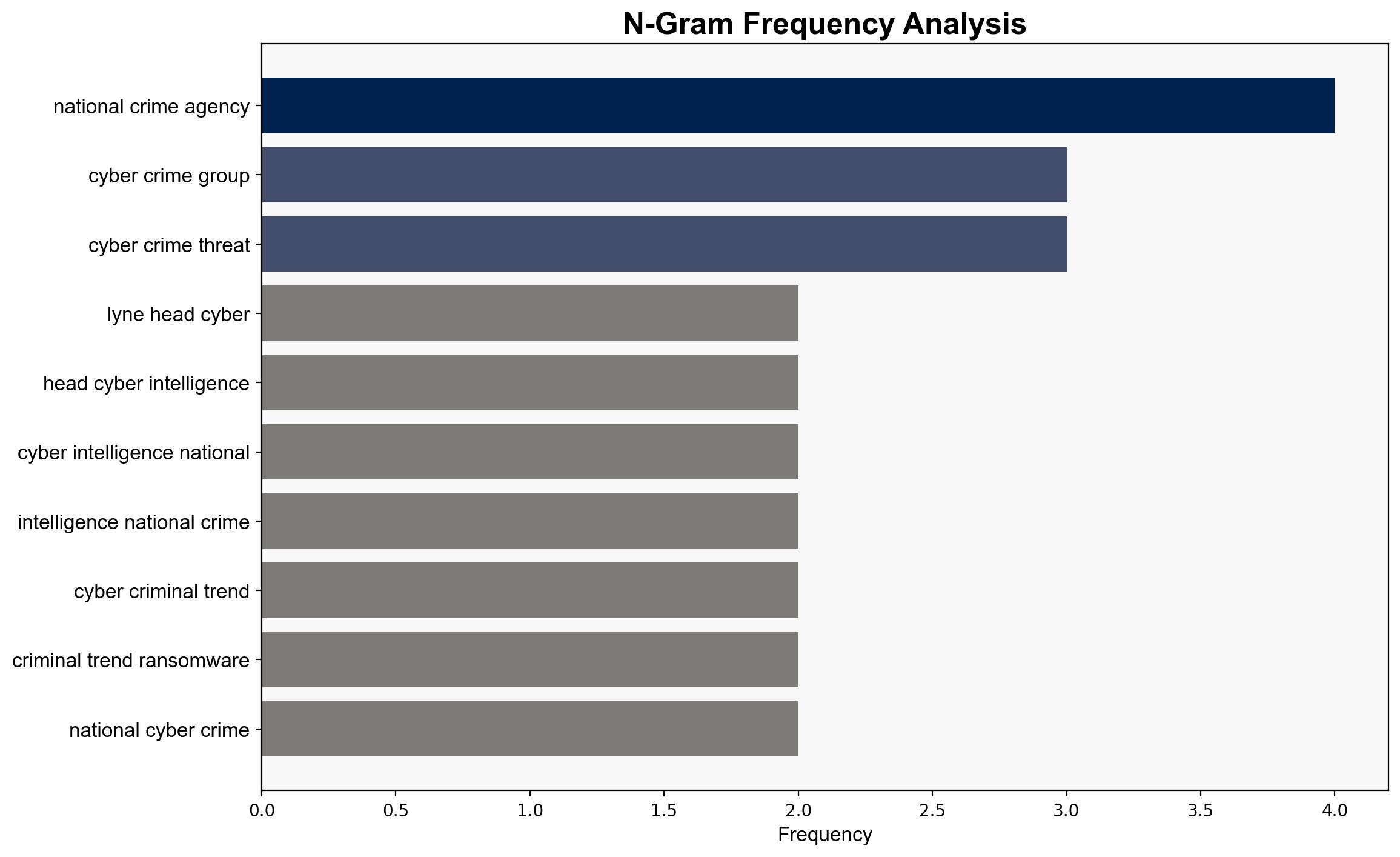
– Lyne
– Jeremy
– Magnus
– Jen
6. Thematic Tags
national security threats, cybersecurity, ransomware, cybercrime ecosystem