Infostealer Breach Hits 50 Companies Due to Lack of Multi-Factor Authentication Security
Published on: 2026-01-07
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: MFA Failure Enables Infostealer Breach At 50 Enterprises
1. BLUF (Bottom Line Up Front)
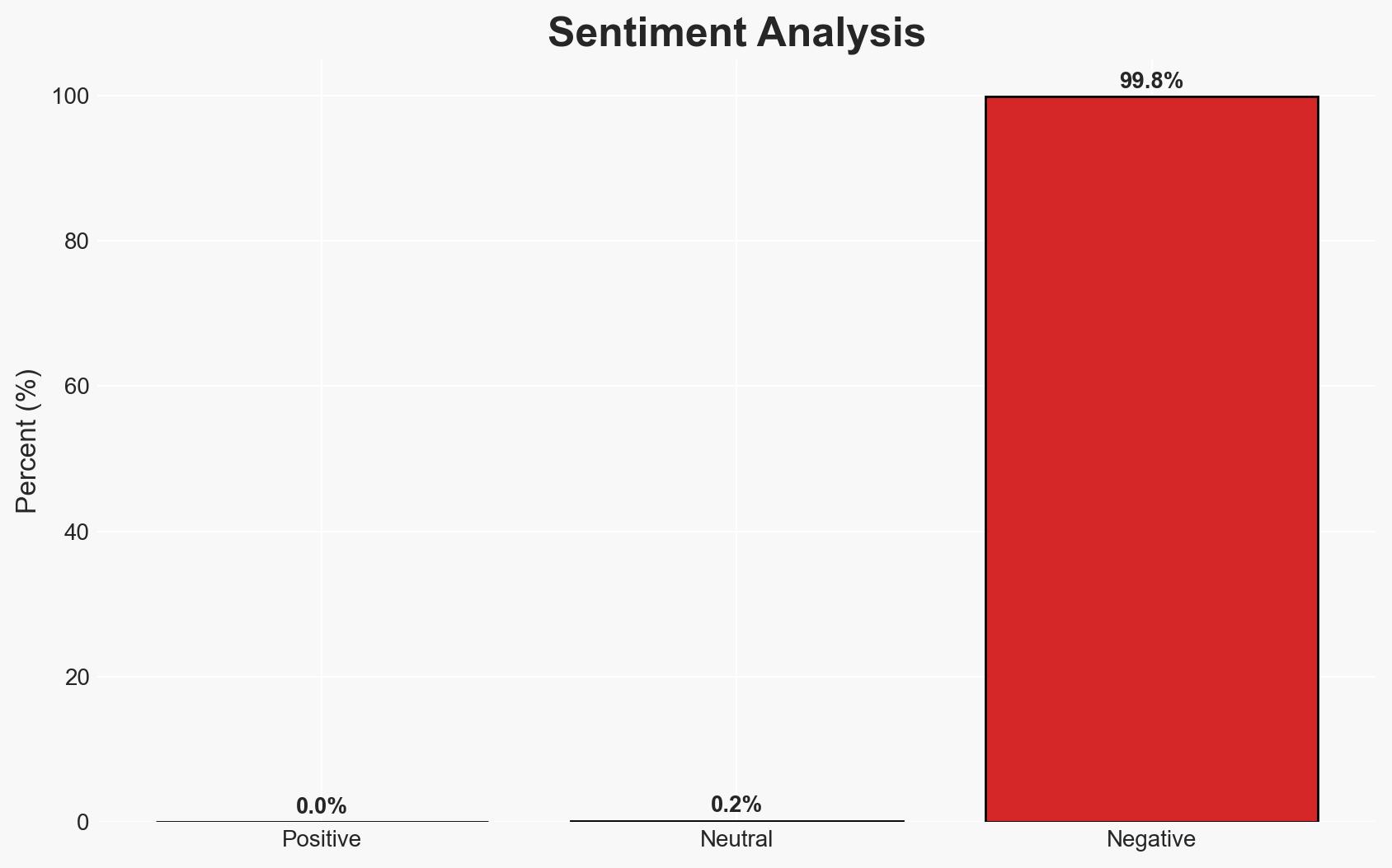
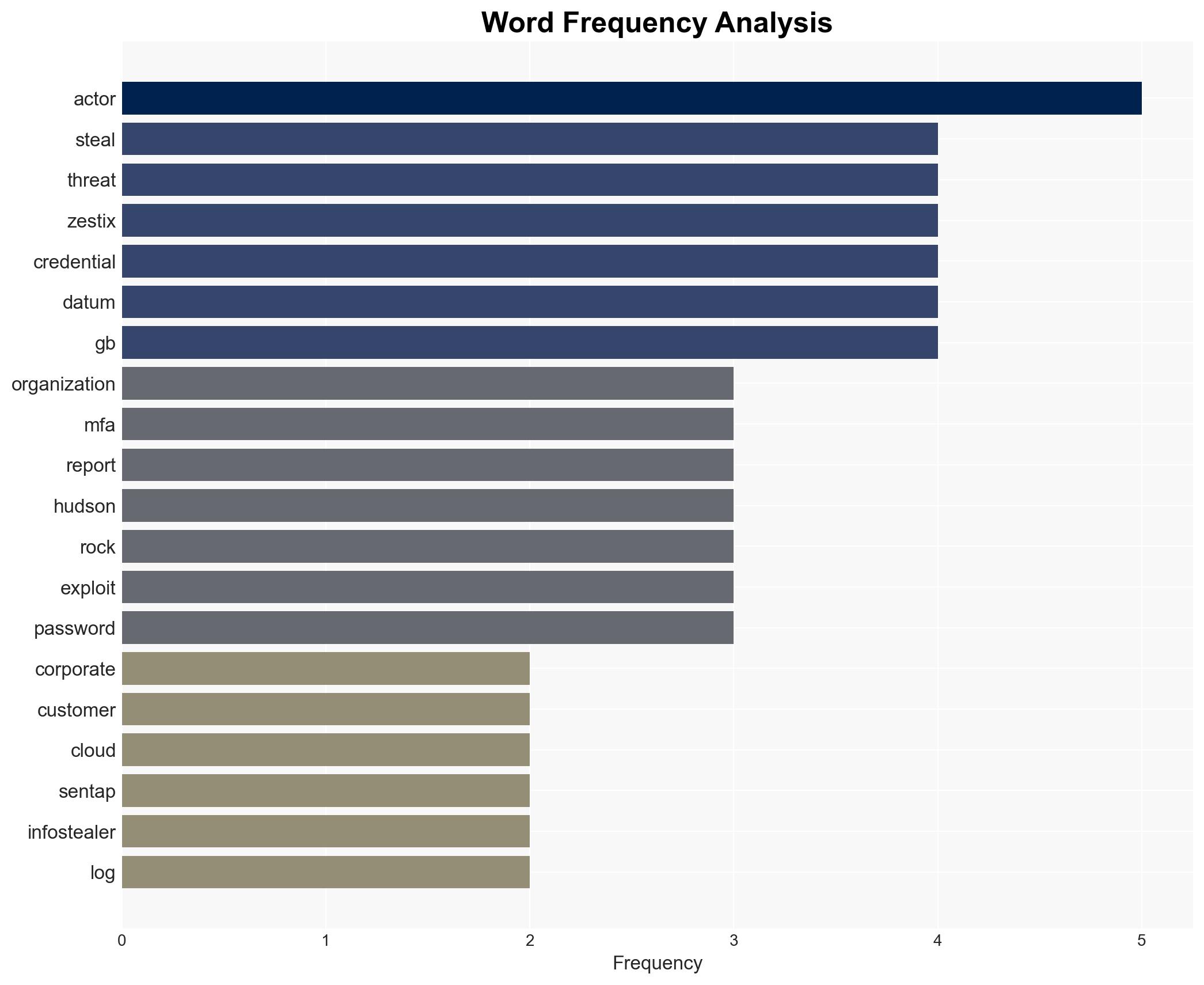
A significant breach involving 50 enterprises was facilitated by the absence of multi-factor authentication (MFA), allowing the threat actor “Zestix” to exfiltrate sensitive data. The breach underscores systemic credential hygiene failures. The most likely hypothesis is that the threat actor exploited existing vulnerabilities without sophisticated methods. This assessment is made with moderate confidence.
2. Competing Hypotheses
- Hypothesis A: Zestix exploited the lack of MFA and poor credential hygiene to access and exfiltrate data. This is supported by the report’s emphasis on credential logs and the absence of sophisticated exploits. However, the extent of Zestix’s technical capabilities remains uncertain.
- Hypothesis B: The breach was facilitated by an insider threat or collusion with an internal party. This is less supported as there is no direct evidence of insider involvement, but the possibility cannot be entirely dismissed without further investigation.
- Assessment: Hypothesis A is currently better supported due to the explicit mention of credential misuse and lack of MFA as primary factors. Indicators such as insider access or complex technical breaches would shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: Organizations did not implement MFA; Zestix acted independently; credential logs were accessible on the dark web.
- Information Gaps: Details on the exact methods used to access and exfiltrate data; full scope of Zestix’s network and affiliations.
- Bias & Deception Risks: Potential bias in the report due to reliance on a single cybersecurity vendor; possibility of Zestix using deception to mask true capabilities or affiliations.
4. Implications and Strategic Risks
This development highlights vulnerabilities in enterprise cybersecurity practices, particularly around credential management and MFA implementation. It may prompt increased scrutiny and regulatory pressure on organizations to enhance security measures.
- Political / Geopolitical: Potential for increased tensions if linked to state-sponsored actors; regulatory responses could vary by region.
- Security / Counter-Terrorism: Increased risk of similar breaches; potential exploitation by other threat actors.
- Cyber / Information Space: Likely increase in demand for MFA solutions; potential rise in dark web activity related to credential sales.
- Economic / Social: Financial losses for affected companies; potential reputational damage and loss of customer trust.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Implement MFA across all systems; conduct thorough credential audits and rotate passwords; monitor dark web for potential data sales.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms for threat intelligence sharing; invest in employee training on cybersecurity best practices.
- Scenario Outlook:
- Best: Rapid adoption of MFA and improved credential hygiene reduces breach incidents.
- Worst: Continued breaches lead to significant economic and reputational damage.
- Most-Likely: Incremental improvements in security posture with periodic breaches due to lagging implementation.
6. Key Individuals and Entities
- Zestix (aka Sentap) – Threat actor
- Hudson Rock – Cybersecurity vendor
- Xcape’s John Carberry – Commentator
- Funksec – Cybercrime group
- Iberia Airlines, Burris & Macomber, Maida Health, Intecro Robotics – Affected organizations
7. Thematic Tags
cybersecurity, credential hygiene, multi-factor authentication, data breach, infostealer, cybercrime, threat actor
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us