Ingram Micro reports ransomware breach impacting over 42,000 individuals’ personal data
Published on: 2026-01-19
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Ingram Micro says ransomware attack affected 42000 people
1. BLUF (Bottom Line Up Front)
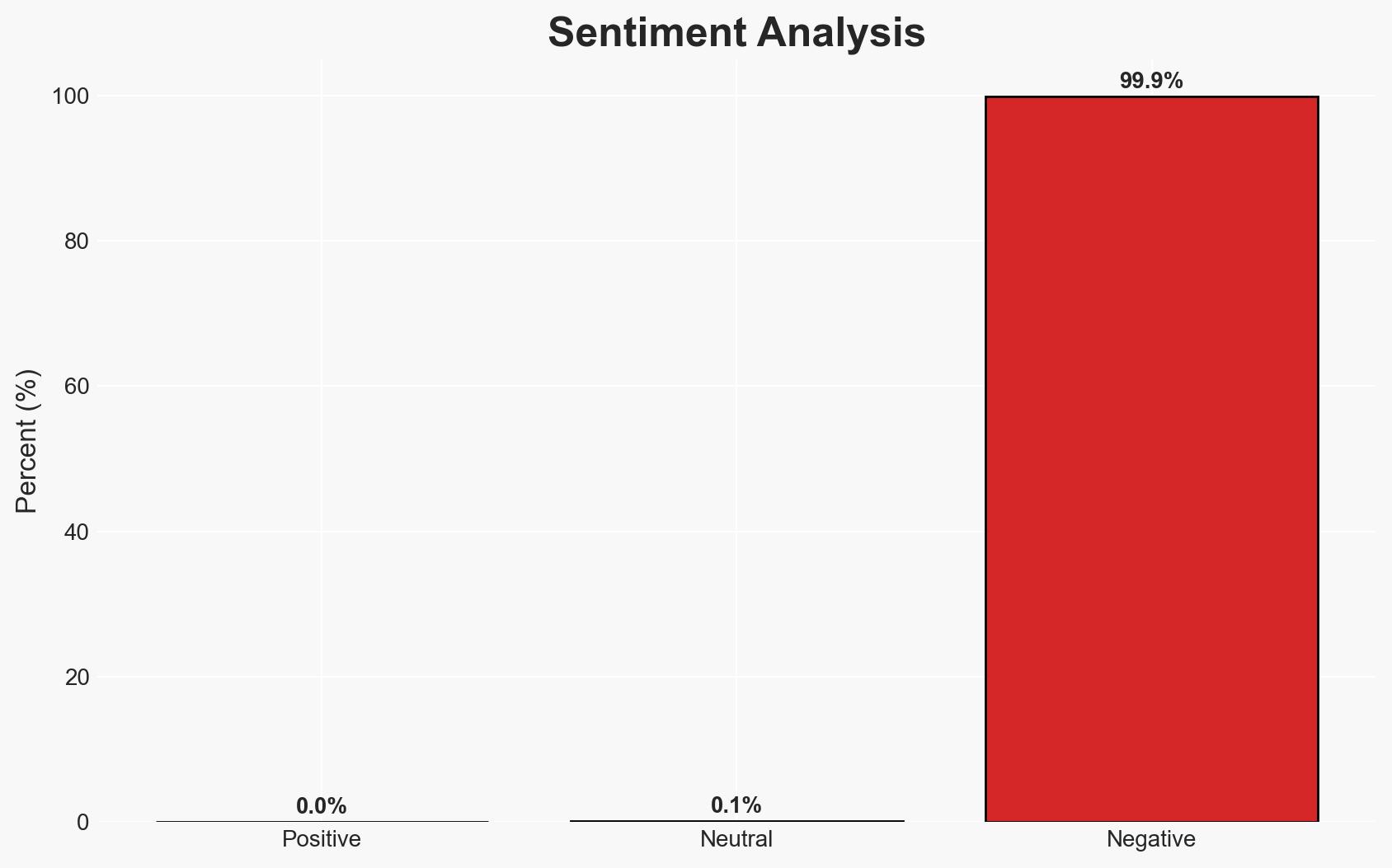
The ransomware attack on Ingram Micro in July 2025, attributed to the SafePay group, compromised the personal data of over 42,000 individuals. This incident highlights the growing threat of ransomware groups using double-extortion tactics. The attack’s impact on Ingram Micro’s operations and data security underscores the need for enhanced cybersecurity measures. Overall confidence in this assessment is moderate due to limited direct attribution and incomplete information on the attack’s full scope.
2. Competing Hypotheses
- Hypothesis A: The SafePay ransomware group is responsible for the attack, as evidenced by their claim of responsibility and the attack’s alignment with their known tactics. However, the absence of direct confirmation from Ingram Micro introduces uncertainty.
- Hypothesis B: Another threat actor could be responsible, using SafePay’s tactics to mislead attribution. The lack of direct evidence linking SafePay and the potential for deception by other groups supports this hypothesis.
- Assessment: Hypothesis A is currently better supported due to SafePay’s claim and the attack’s characteristics matching their known methods. Confirmation from Ingram Micro or further forensic evidence could solidify this judgment.
3. Key Assumptions and Red Flags
- Assumptions: SafePay’s claim is genuine; Ingram Micro’s reported data breach scope is accurate; the attack’s timing and tactics align with SafePay’s known operations.
- Information Gaps: Detailed forensic analysis results; confirmation of SafePay’s involvement from Ingram Micro; specifics on the ransom demand and payment status.
- Bias & Deception Risks: Potential bias in attributing the attack to SafePay without conclusive evidence; risk of deception by other threat actors mimicking SafePay’s tactics.
4. Implications and Strategic Risks
The attack on Ingram Micro could have significant repercussions across multiple domains, influencing cybersecurity policies and operational resilience strategies.
- Political / Geopolitical: Increased pressure on governments to address ransomware threats and enhance international cooperation on cybersecurity.
- Security / Counter-Terrorism: Potential for increased targeting of critical infrastructure and large enterprises by ransomware groups.
- Cyber / Information Space: Escalation in ransomware tactics, including double-extortion, could lead to more sophisticated cyber defenses and threat intelligence sharing.
- Economic / Social: Financial losses for Ingram Micro and potential reputational damage, affecting customer trust and market position.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of ransomware group activities; verify SafePay’s involvement; strengthen Ingram Micro’s cybersecurity posture.
- Medium-Term Posture (1–12 months): Develop resilience measures against ransomware; foster partnerships for intelligence sharing; invest in employee cybersecurity training.
- Scenario Outlook:
- Best: Improved defenses deter future attacks, reducing ransomware incidents.
- Worst: Ransomware tactics evolve, leading to more frequent and severe breaches.
- Most-Likely: Continued ransomware activity with gradual improvements in organizational defenses.
6. Key Individuals and Entities
- Ingram Micro
- SafePay ransomware group
- Maine’s Attorney General
- BleepingComputer (reporting entity)
7. Thematic Tags
cybersecurity, ransomware, data breach, SafePay, double-extortion, cyber defense, threat intelligence
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us