Ingram Micro’s ransomware breach exposes personal data of 42,000 individuals
Published on: 2026-01-19
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Ransomware attack on Ingram Micro impacts 42000 individuals
1. BLUF (Bottom Line Up Front)
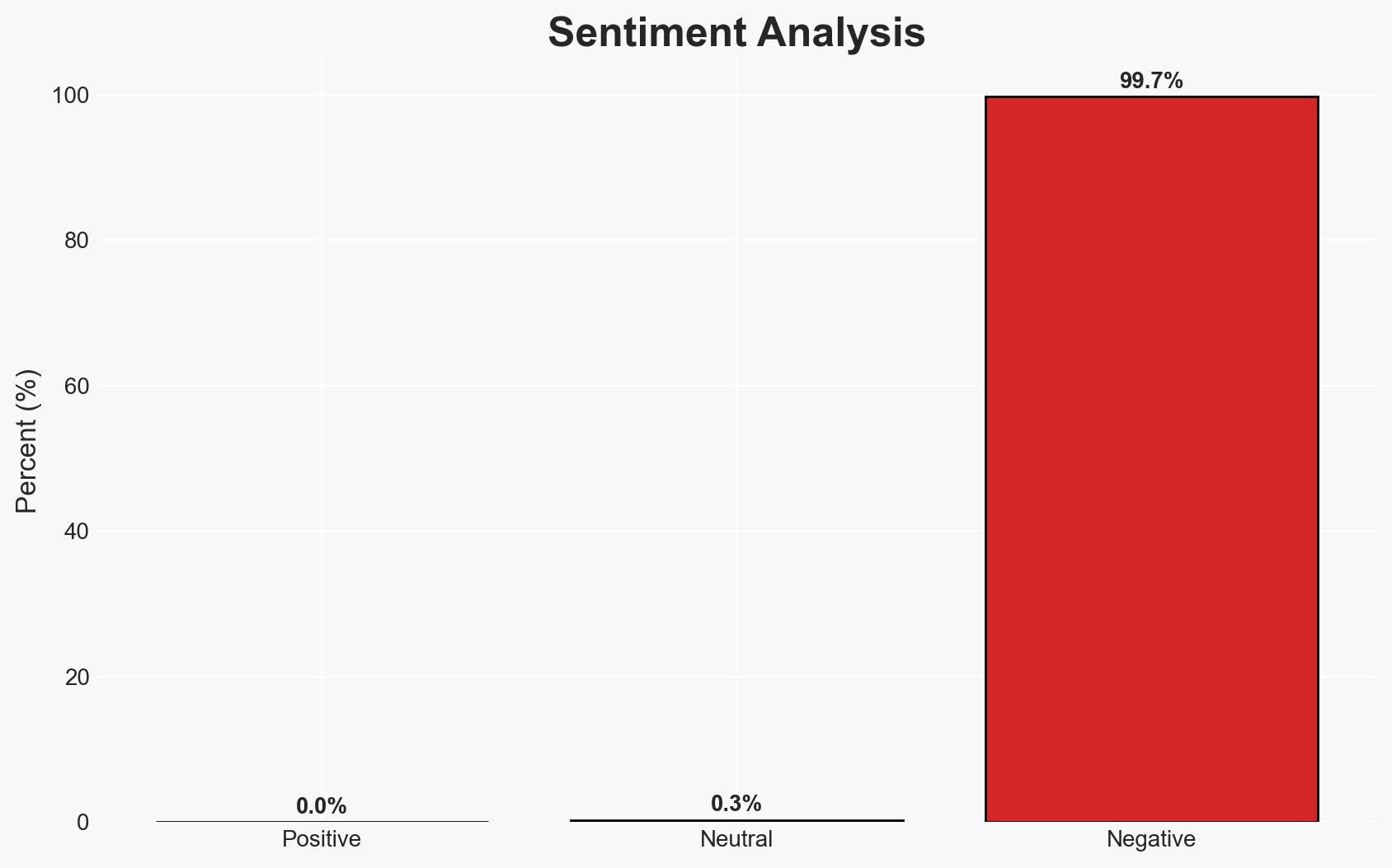
A ransomware attack on Ingram Micro has exposed the personal data of approximately 42,000 individuals, including sensitive information such as Social Security Numbers. The Safepay ransomware group has claimed responsibility, although this remains unverified. The incident highlights significant vulnerabilities in supply chain cybersecurity, with moderate confidence in the assessment due to incomplete attribution and potential data manipulation by the attackers.
2. Competing Hypotheses
- Hypothesis A: The attack was executed by the Safepay ransomware group, as claimed on their Tor leak site. Supporting evidence includes the group’s claim and the publication of stolen data. Contradicting evidence includes the lack of direct attribution from Ingram Micro and the non-functional download link, which may suggest deception or incomplete execution.
- Hypothesis B: The attack could have been conducted by another cybercriminal group, with Safepay’s claim being a false flag operation to mislead investigators. Supporting evidence includes the absence of direct attribution by Ingram Micro and the possibility of other groups using similar tactics. Contradicting evidence is the public claim by Safepay, which aligns with typical ransomware group behavior.
- Assessment: Hypothesis A is currently better supported due to the public claim by Safepay and the typical modus operandi of ransomware groups. However, further investigation into the group’s capabilities and past activities could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The Safepay group has the capability to execute such an attack; the data exposed is accurate and not manipulated; Ingram Micro’s response measures are effective in mitigating further risk.
- Information Gaps: Specific technical details of the breach; confirmation of the attacker’s identity; the full scope of data compromised.
- Bias & Deception Risks: Potential bias in attributing the attack to Safepay based solely on their claim; risk of deception by the attackers through false flag operations or data manipulation.
4. Implications and Strategic Risks
The attack on Ingram Micro could lead to increased scrutiny on supply chain cybersecurity practices and potential regulatory responses. The incident may also embolden other cybercriminal groups to target similar organizations.
- Political / Geopolitical: Potential for increased tensions between countries over cyber attribution and response, especially if state actors are suspected.
- Security / Counter-Terrorism: Heightened alert for similar attacks on critical infrastructure and supply chain entities.
- Cyber / Information Space: Increased focus on ransomware defense strategies and potential for information warfare tactics by cybercriminals.
- Economic / Social: Possible financial losses for Ingram Micro and affected individuals, leading to reputational damage and loss of trust.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of Ingram Micro’s systems for further breaches; engage with cybersecurity firms for threat intelligence sharing; advise affected individuals on protective measures.
- Medium-Term Posture (1–12 months): Develop stronger cybersecurity partnerships within the supply chain; invest in advanced threat detection and response capabilities; conduct regular security audits.
- Scenario Outlook:
- Best: Improved cybersecurity posture prevents future breaches, restoring trust.
- Worst: Additional breaches occur, leading to significant financial and reputational damage.
- Most-Likely: Incremental improvements in security with ongoing attempts by cybercriminals to exploit vulnerabilities.
6. Key Individuals and Entities
- Ingram Micro
- Safepay ransomware group
- Maine Attorney General’s Office
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, ransomware, data breach, supply chain security, cybercrime, information security, identity protection
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us