Insecure Credential Storage Detected in Backdoor.Win32.ControlTotal.t (MVID-2025-0702)
Published on: 2025-12-23
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: BackdoorWin32ControlTotalt Insecure Credential Storage MVID-2025-0702
1. BLUF (Bottom Line Up Front)
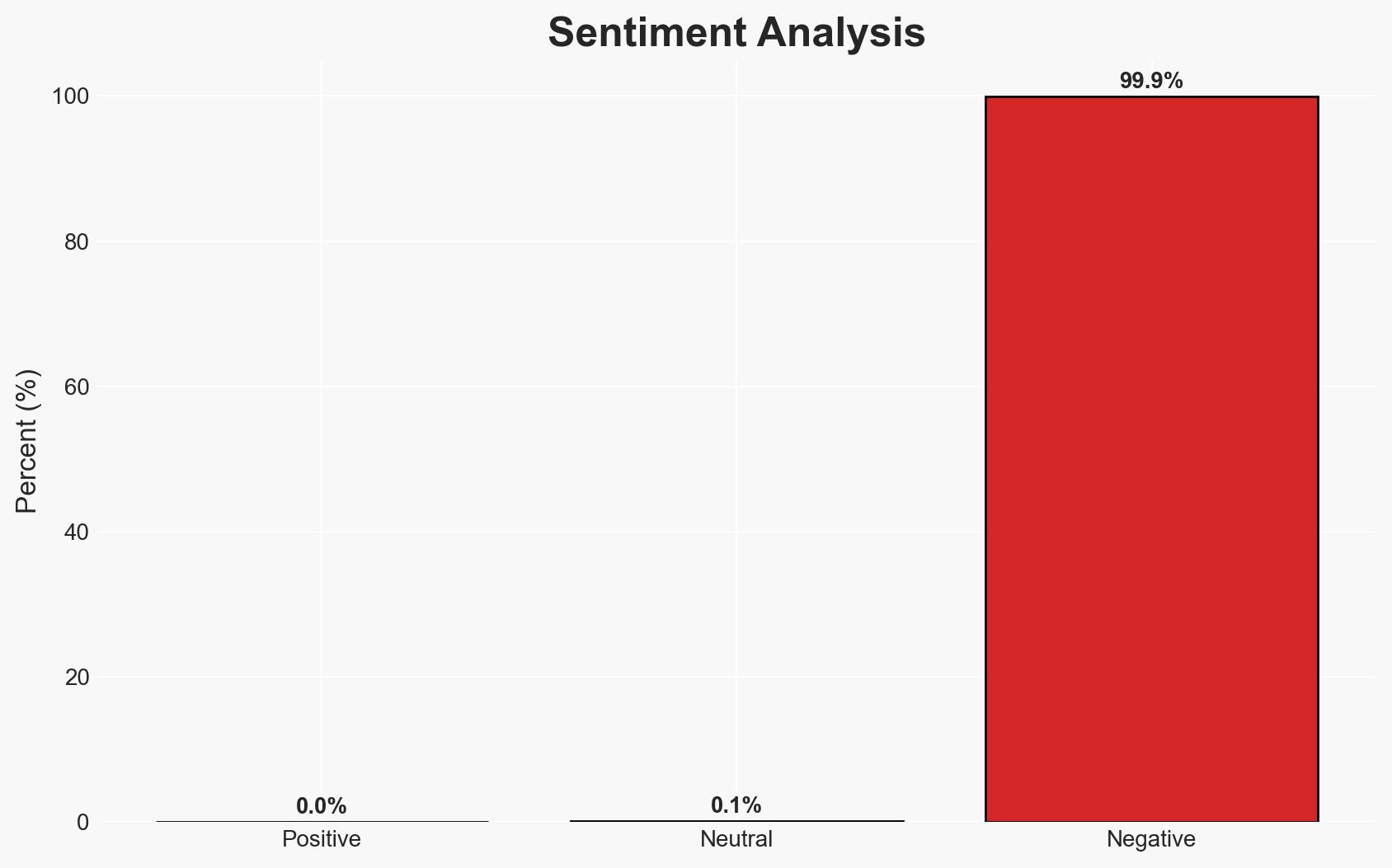
The Backdoor.Win32.ControlTotal.t malware presents a significant cybersecurity threat due to its insecure credential storage, which could be exploited by malicious actors to gain unauthorized access. The malware’s reliance on a hardcoded password stored in cleartext increases the risk of exploitation. This vulnerability primarily affects systems where the malware is deployed, posing a risk to data integrity and confidentiality. Overall confidence in this assessment is moderate, given the limited scope of the available data.
2. Competing Hypotheses
- Hypothesis A: The malware is primarily used for targeted attacks against specific organizations or individuals, leveraging insecure credential storage to maintain persistent access. Supporting evidence includes the use of a hardcoded password, suggesting an intent for repeated access. Key uncertainties include the identity of the threat actors and the specific targets.
- Hypothesis B: The malware is part of a broader campaign aimed at indiscriminate mass exploitation, with the insecure credential storage being a result of poor design rather than a targeted strategy. This is supported by the generic nature of the password and lack of sophistication in credential storage. Contradicting evidence includes the requirement for authentication, which may indicate a more deliberate targeting strategy.
- Assessment: Hypothesis A is currently better supported due to the requirement for authentication, which suggests a more targeted approach. Indicators that could shift this judgment include evidence of widespread deployment across diverse systems or identification of a campaign targeting specific sectors.
3. Key Assumptions and Red Flags
- Assumptions: The malware’s insecure credential storage is a deliberate design choice; the threat actors have the capability to exploit this vulnerability; the malware is actively being used in the wild.
- Information Gaps: Specific details about the threat actors, their objectives, and the extent of the malware’s deployment are unknown.
- Bias & Deception Risks: There is a risk of confirmation bias in assuming the malware’s design is intentional without further evidence. The source may also have inherent biases, given its focus on vulnerability disclosure.
4. Implications and Strategic Risks
This development could lead to increased cyber threats against vulnerable systems, potentially impacting data security and privacy. The insecure credential storage may be leveraged by threat actors to conduct further attacks, leading to broader security challenges.
- Political / Geopolitical: Potential for escalation if linked to state-sponsored actors targeting critical infrastructure.
- Security / Counter-Terrorism: Increased risk of data breaches and unauthorized access, potentially impacting national security.
- Cyber / Information Space: Highlights the need for improved cybersecurity practices and the risks associated with poor credential management.
- Economic / Social: Potential economic impact due to data breaches, loss of consumer trust, and costs associated with remediation.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a thorough review of systems for signs of the malware, implement stronger credential management practices, and monitor for indicators of compromise.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms for threat intelligence sharing, enhance incident response capabilities, and invest in cybersecurity training.
- Scenario Outlook:
- Best Case: The vulnerability is patched, and no significant exploitation occurs.
- Worst Case: Widespread exploitation leads to significant data breaches and operational disruptions.
- Most-Likely: Targeted exploitation occurs, prompting increased cybersecurity measures and awareness.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, malware, credential management, threat intelligence, vulnerability disclosure
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us