Inside the Multimillion-Dollar Plan to Make Mobile Voting Happen – Wired
Published on: 2025-11-14
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Inside the Multimillion-Dollar Plan to Make Mobile Voting Happen – Wired
1. BLUF (Bottom Line Up Front)
The initiative to implement mobile voting, spearheaded by Bradley Tusk and supported by Joe Kiniry, presents both opportunities and significant cybersecurity risks. The most supported hypothesis is that while mobile voting could increase voter turnout, the current technological and security challenges make widespread adoption premature. Confidence Level: Moderate. Recommended action is to continue research and development while implementing rigorous security testing and pilot programs to assess viability and security.
2. Competing Hypotheses
Hypothesis 1: Mobile voting will significantly increase voter turnout and enhance democratic participation, as claimed by Tusk. This hypothesis is supported by the potential convenience and accessibility of mobile voting.
Hypothesis 2: The security risks associated with mobile voting are insurmountable at this time, making it an impractical solution for secure elections. This hypothesis is supported by the skepticism of cybersecurity experts like Joe Kiniry and Ron Rivest.
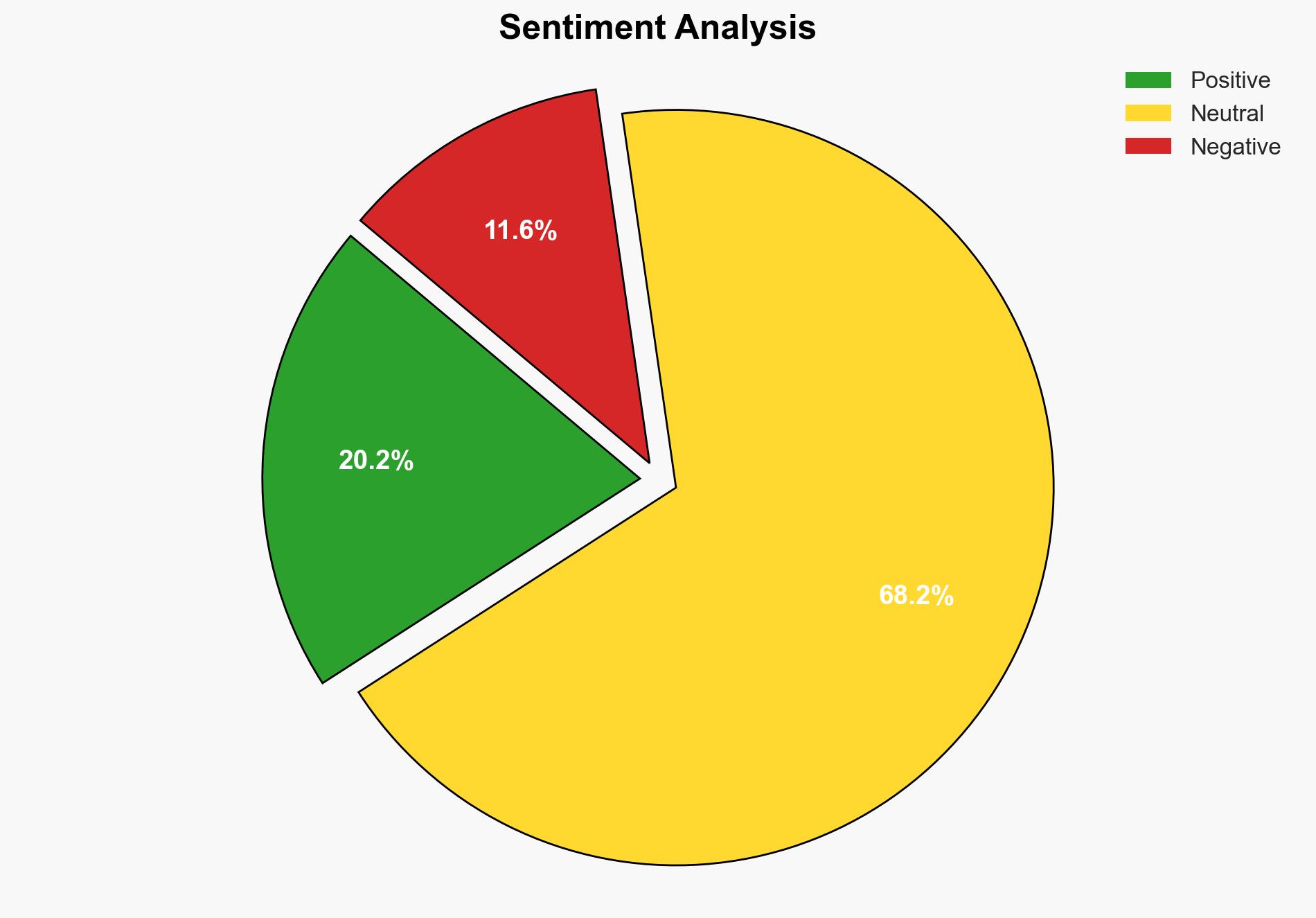
Assessment: Hypothesis 2 is more likely given the current state of cybersecurity and the high stakes involved in election integrity.
3. Key Assumptions and Red Flags
Assumptions: It is assumed that mobile voting technology can be made secure enough for widespread use. It is also assumed that increased convenience will lead to higher voter turnout.
Red Flags: The lack of peer-reviewed research and the potential for over-reliance on unproven technology are significant concerns. The involvement of high-profile individuals with vested interests could introduce bias.
4. Implications and Strategic Risks
Political implications include the potential for increased voter turnout and engagement. However, cybersecurity risks could lead to compromised election integrity, undermining public trust. Economically, significant investment in unproven technology could result in wasted resources if security issues are not resolved. Informational risks include the spread of misinformation regarding the security and reliability of mobile voting.
5. Recommendations and Outlook
- Conduct extensive security testing and pilot programs in controlled environments to evaluate the technology’s viability.
- Engage with cybersecurity experts to address potential vulnerabilities before broader implementation.
- Best-case scenario: Successful pilot programs lead to secure, widespread adoption, increasing voter turnout.
- Worst-case scenario: Security breaches occur, undermining election integrity and public trust.
- Most-likely scenario: Continued development and testing with limited initial adoption in low-stakes elections.
6. Key Individuals and Entities
Bradley Tusk, Joe Kiniry, Ron Rivest
7. Thematic Tags
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us
·