Insights from Major Phishing Attacks Highlight Critical Vulnerabilities in Enterprise Security for 2026
Published on: 2026-01-05
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: What the Years Biggest Phishing Scams Reveal About Enterprise Blind Spots
1. BLUF (Bottom Line Up Front)
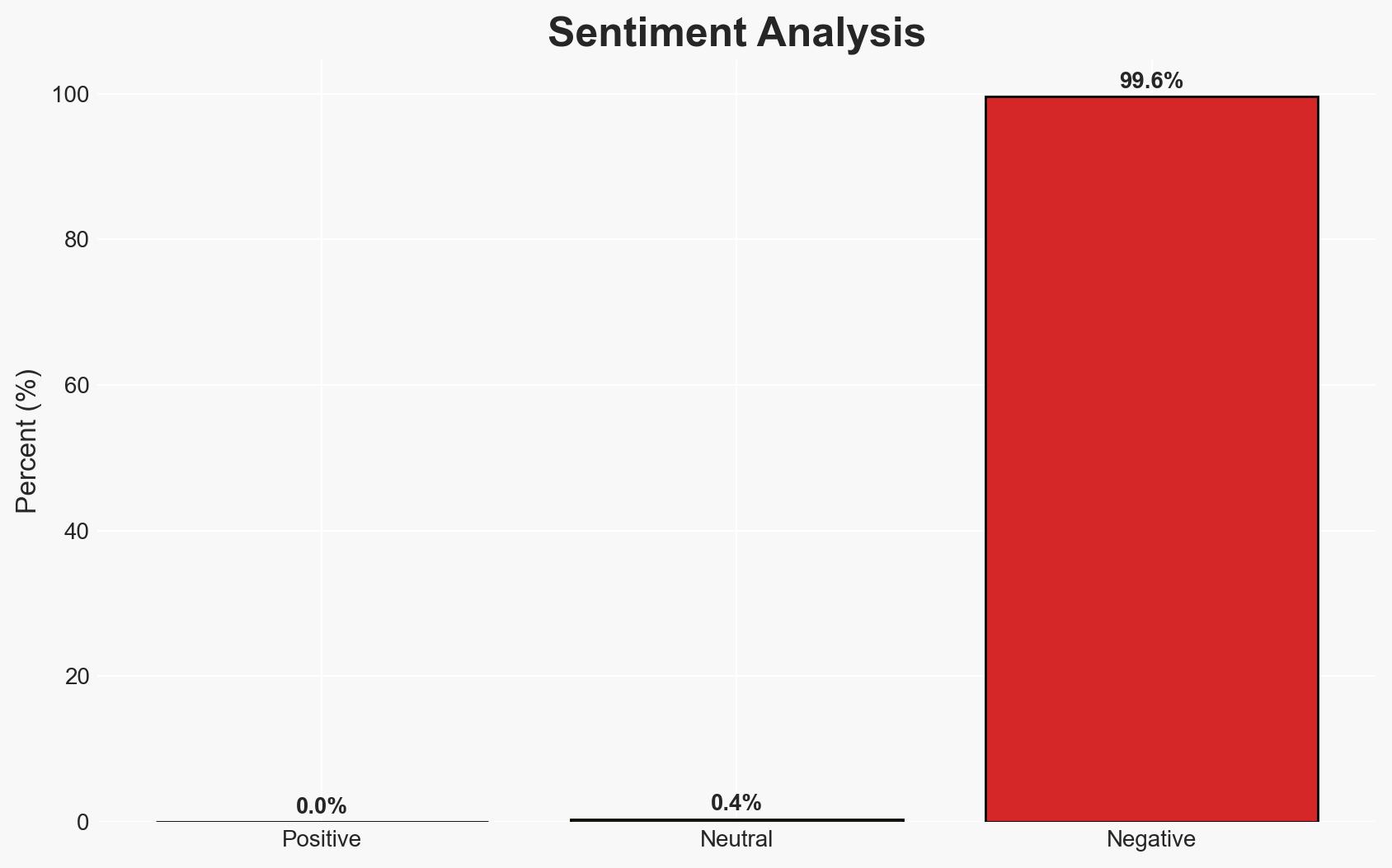
The most significant cyber threats in 2025 were characterized by social engineering attacks that exploited trust rather than technical vulnerabilities. These attacks targeted enterprises’ assumptions about identity and legitimacy, revealing critical blind spots. The shift from technical compromise to trust exploitation poses a substantial risk to enterprise security in 2026. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: The increase in phishing scams exploiting trust is primarily due to advancements in AI, which enable more convincing impersonation attacks. Supporting evidence includes the use of AI-powered impersonation to bypass traditional security controls. Key uncertainties involve the extent of AI’s role versus other factors like human error.
- Hypothesis B: The rise in trust-based phishing attacks is mainly due to enterprises’ inadequate adaptation to evolving social engineering tactics. While AI plays a role, the primary issue is the failure to update security protocols to address non-technical threats. Contradicting evidence includes the continued reliance on outdated security measures.
- Assessment: Hypothesis B is currently better supported, as the evidence suggests enterprises have not sufficiently adapted to social engineering threats. Indicators that could shift this judgment include new data on AI’s direct impact on increasing attack success rates.
3. Key Assumptions and Red Flags
- Assumptions: Enterprises will continue to rely on traditional security measures; attackers will increasingly use social engineering tactics; AI will enhance the sophistication of impersonation attacks.
- Information Gaps: Detailed data on the specific role of AI in recent phishing scams; comprehensive statistics on enterprise security protocol updates.
- Bias & Deception Risks: Potential overestimation of AI’s role due to media narratives; underreporting of successful phishing attempts by enterprises to protect reputation.
4. Implications and Strategic Risks
The shift towards exploiting trust in cyber-attacks could lead to significant changes in enterprise security strategies and broader cybersecurity policies. This evolution may affect various domains over time.
- Political / Geopolitical: Potential for increased regulatory scrutiny and international cooperation on cybersecurity standards.
- Security / Counter-Terrorism: Heightened focus on human factors in security training and awareness programs.
- Cyber / Information Space: Increased demand for AI-driven security solutions and behavioral analysis tools.
- Economic / Social: Potential economic impacts from increased cyber insurance premiums and loss of consumer trust.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct comprehensive security audits focusing on social engineering vulnerabilities; enhance employee training on phishing detection.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms specializing in behavioral analysis; invest in AI-driven security technologies.
- Scenario Outlook:
- Best Case: Enterprises successfully adapt to new threats, reducing phishing incidents.
- Worst Case: Continued reliance on outdated security measures leads to significant financial losses and reputational damage.
- Most Likely: Gradual improvement in security protocols with intermittent high-profile breaches driving change.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, social engineering, phishing, enterprise security, AI in cybercrime, trust exploitation, security protocols
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us