Instagram Users Alarmed by Unrequested Password Resets Amidst 175M Data Exposure Concerns
Published on: 2026-01-12
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Instagram Security Alert After 175M User Data Exposure Why Reset Emails Raised Alarms
1. BLUF (Bottom Line Up Front)
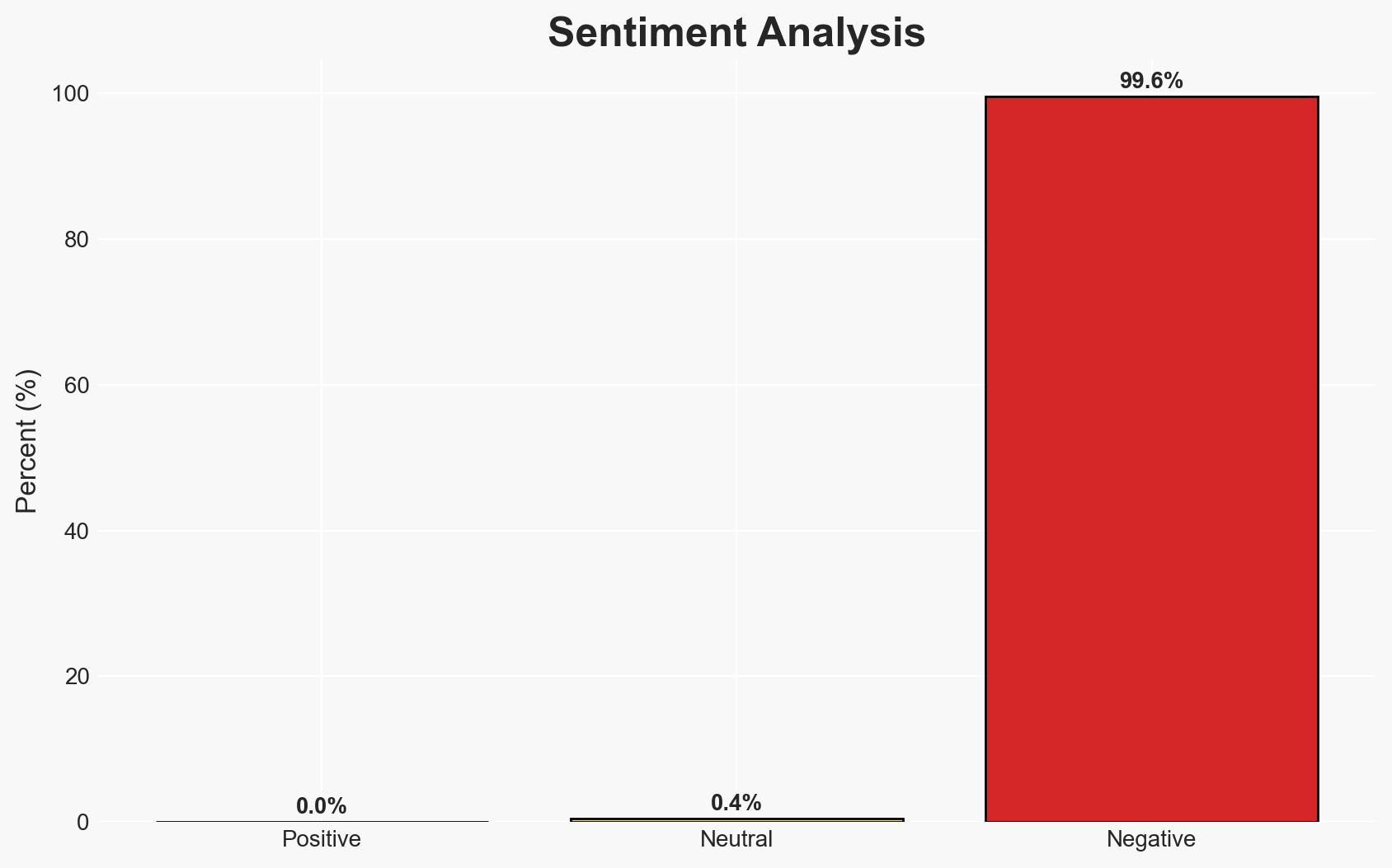
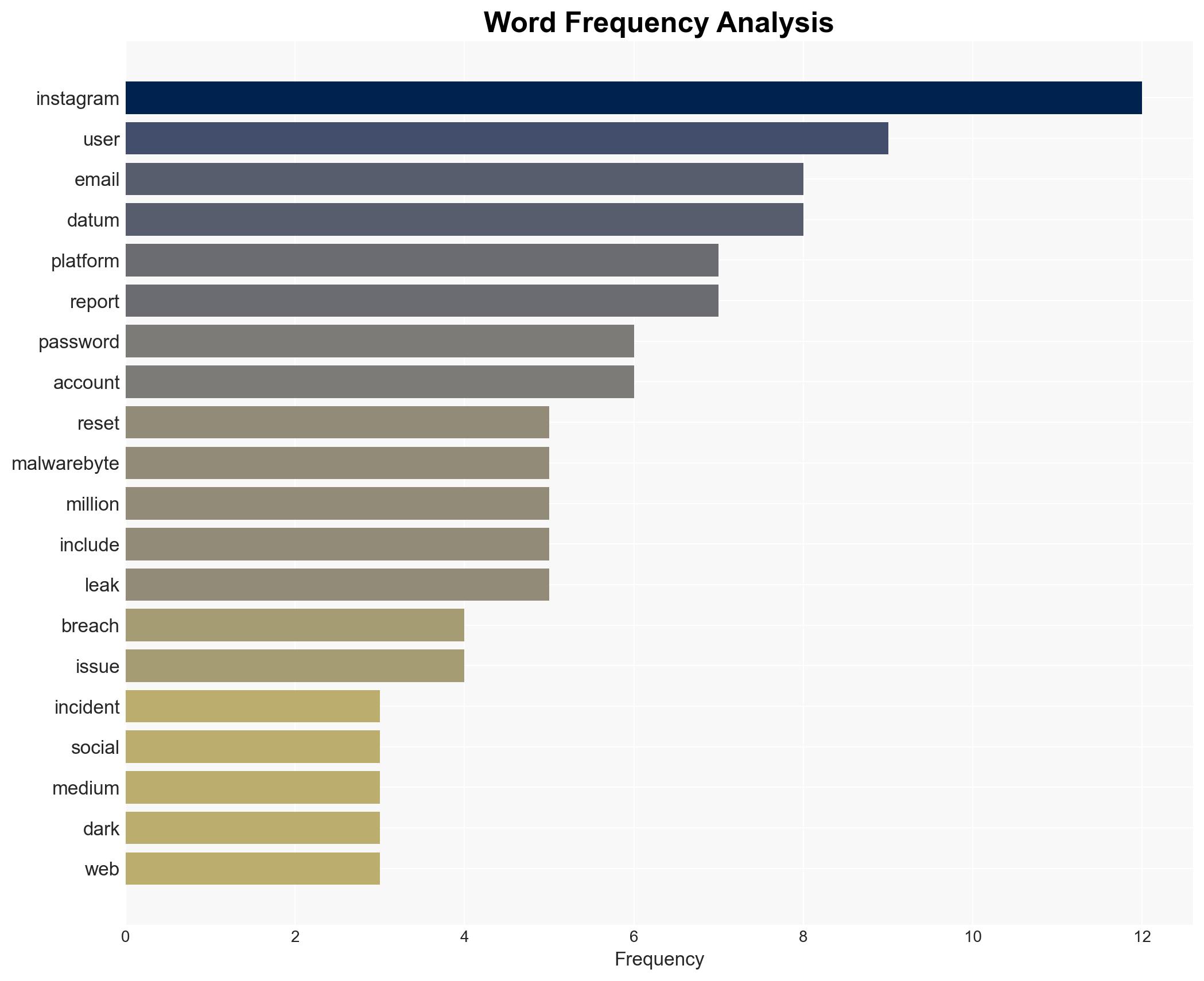
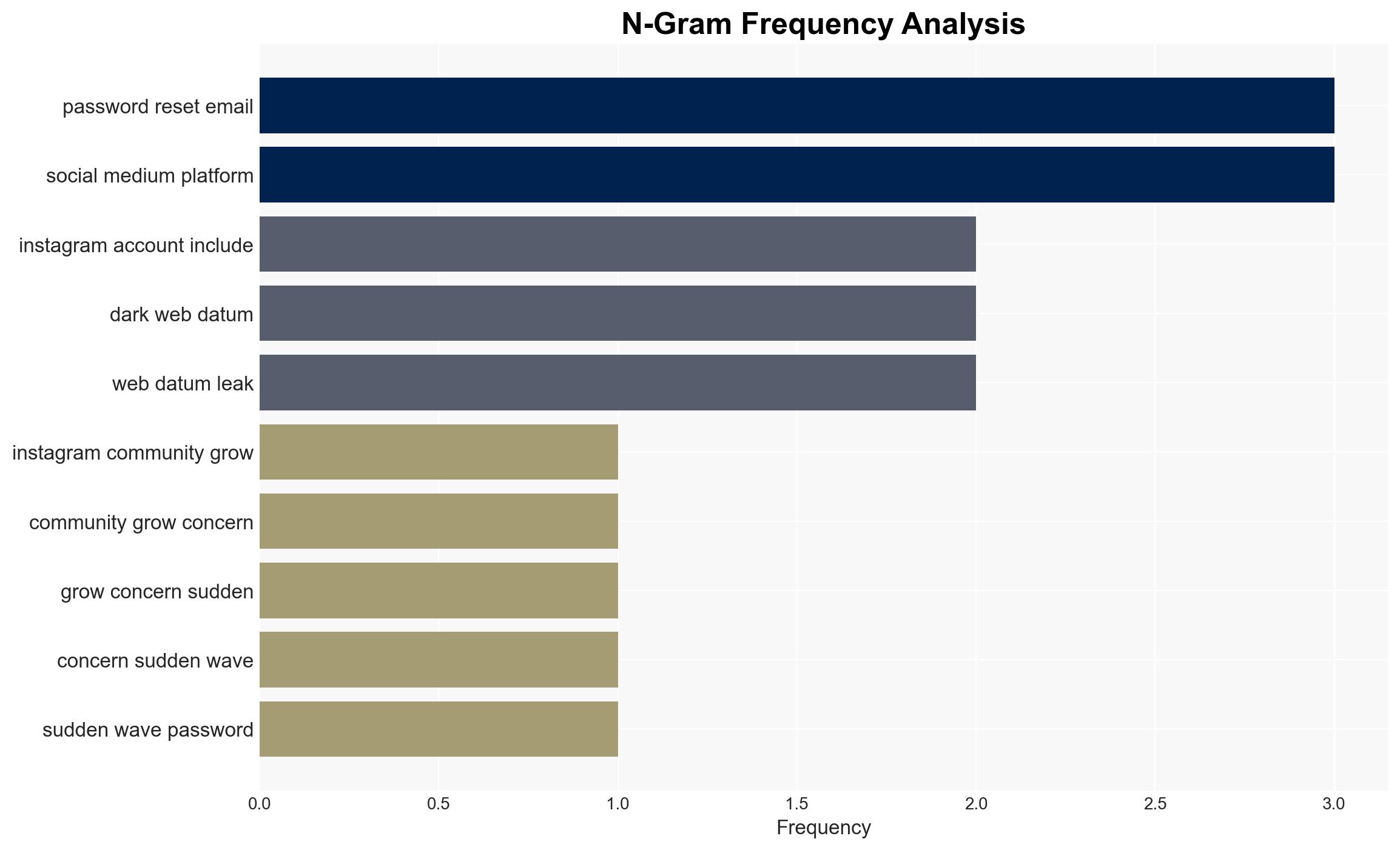
The exposure of 17.5 million Instagram user data on the dark web has raised significant cybersecurity concerns, with the peculiar password reset emails indicating potential exploitation. The most likely hypothesis is that the data leak originated from an external party exploiting a vulnerability, rather than a direct breach of Instagram’s systems. This incident affects Instagram users globally, with moderate confidence in this assessment due to corroborating reports and the nature of the data exposure.
2. Competing Hypotheses
- Hypothesis A: The data exposure resulted from an external party exploiting an Instagram API vulnerability or misconfiguration, leading to the unauthorized access and dissemination of user data. Supporting evidence includes the structured nature of the leaked data resembling API responses and the absence of direct system breach indicators. Key uncertainties involve the exact method of exploitation and the timeline of the vulnerability.
- Hypothesis B: The data exposure is a result of a coordinated internal compromise or insider threat within Instagram, leading to the deliberate release of user data. Contradicting evidence includes Meta’s denial of a system breach and the lack of internal breach indicators. This hypothesis is less supported due to the absence of corroborating internal compromise reports.
- Assessment: Hypothesis A is currently best supported due to the structured data leak resembling API responses and corroborating reports of external exploitation. Indicators that could shift this judgment include new evidence of internal compromise or further technical analysis revealing different exploitation methods.
3. Key Assumptions and Red Flags
- Assumptions: Instagram’s systems were not directly breached; the data leak was facilitated by an external vulnerability; Meta’s public statements are accurate; the data on the dark web is authentic.
- Information Gaps: Specific technical details of the vulnerability exploited; timeline and duration of the data exposure; identity and motivations of the external party involved.
- Bias & Deception Risks: Potential bias in Meta’s public communications to downplay the incident; deception risks from cybercriminals misrepresenting the scope or source of the data leak.
4. Implications and Strategic Risks
This development could lead to increased scrutiny on social media platforms’ data security practices and potential regulatory responses. The incident may also embolden cybercriminals to exploit similar vulnerabilities in other platforms.
- Political / Geopolitical: Potential for increased regulatory pressure on social media companies to enhance data protection measures.
- Security / Counter-Terrorism: Heightened risk of phishing and impersonation attacks targeting exposed users, potentially impacting personal and organizational security.
- Cyber / Information Space: Increased cyber threat landscape complexity, with potential for further exploitation of similar vulnerabilities across platforms.
- Economic / Social: Possible erosion of user trust in Instagram and similar platforms, impacting user engagement and platform revenue.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of dark web forums for further data exposure; advise users to enable two-factor authentication; issue clear communication to users about protective measures.
- Medium-Term Posture (1–12 months): Strengthen partnerships with cybersecurity firms for threat intelligence sharing; invest in advanced threat detection and response capabilities; review and update API security protocols.
- Scenario Outlook:
- Best: Rapid containment and mitigation of the data exposure, leading to minimal impact on user trust and platform security.
- Worst: Further exploitation of vulnerabilities leading to additional data breaches and significant reputational damage.
- Most-Likely: Incremental improvements in security measures with moderate impact on user trust and regulatory scrutiny.
6. Key Individuals and Entities
- Meta Platforms (Owner of Instagram)
- Malwarebytes (Cybersecurity firm reporting on the incident)
- Solonik (User reportedly offering the dataset on BreachForums)
- Instagram (Social media platform affected)
7. Thematic Tags
cybersecurity, data breach, social media, API vulnerability, phishing risks, user data exposure, regulatory implications
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us