Intelligence Officials Raise Alarm Over Domestic Security Risks Linked to Afghanistan Withdrawal After Recent…
Published on: 2026-01-15
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Intelligence Sources Warn of ‘Embedded’ Security Threats Following US Withdrawal From Afghanistan
1. BLUF (Bottom Line Up Front)
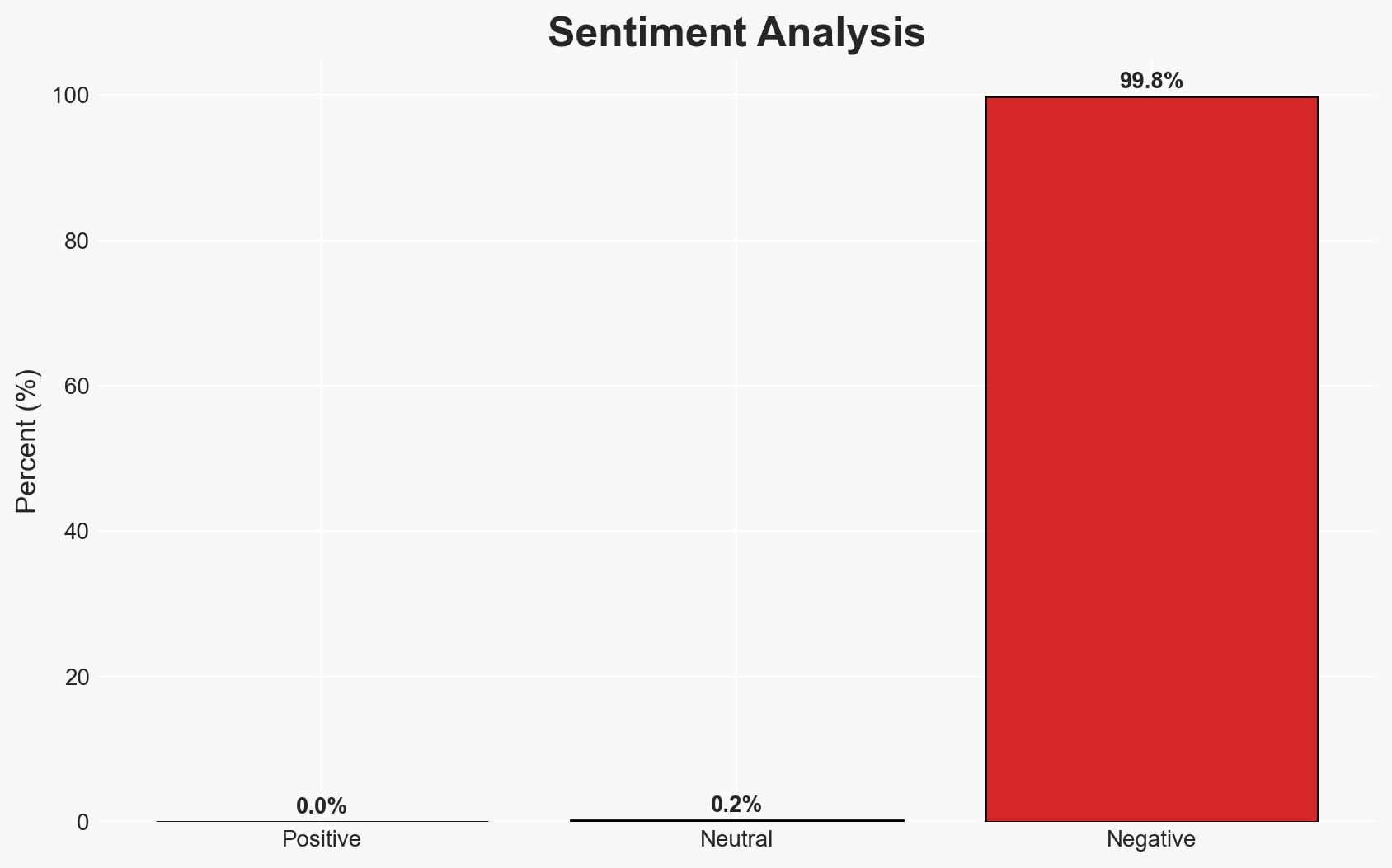
The recent ambush near the White House and other incidents involving Afghan nationals highlight potential embedded security threats within the United States, stemming from the chaotic 2021 withdrawal from Afghanistan. This situation poses a significant risk to national security, with moderate confidence in the assessment that some evacuees may have been inadequately vetted. The primary concern is the potential for coordinated attacks by individuals with military training. This affects national security agencies and local law enforcement.
2. Competing Hypotheses
- Hypothesis A: The incidents are isolated acts of violence by individuals with extremist tendencies, not indicative of a coordinated threat. Supporting evidence includes the lone wolf nature of the attacks and the lack of evidence of broader coordination. Key uncertainties include the potential for undiscovered networks or cells.
- Hypothesis B: The incidents are part of a coordinated effort by a ‘shadow army’ of radicalized individuals embedded within the US. Supporting evidence includes the backgrounds of the suspects and their military training. Contradicting evidence is the absence of a clear command structure or communication among suspects.
- Assessment: Hypothesis B is currently better supported due to the systematic nature of the suspects’ backgrounds and the potential for further attacks. Indicators that could shift this judgment include discovery of communication between suspects or additional isolated incidents without a pattern.
3. Key Assumptions and Red Flags
- Assumptions: The vetting process during the 2021 evacuation was insufficient; individuals with military training pose a higher threat; current intelligence efforts can identify and mitigate threats.
- Information Gaps: Details on the vetting process specifics, communication between suspects, and the extent of radicalization among evacuees.
- Bias & Deception Risks: Potential cognitive bias in overestimating the threat due to recent events; source bias from intelligence agencies emphasizing threat to justify increased measures; possible deception by suspects to mislead investigations.
4. Implications and Strategic Risks
This development could lead to increased domestic security measures and strain on intelligence resources. It may also influence public opinion on immigration and national security policies.
- Political / Geopolitical: Potential for increased political pressure on immigration policies and scrutiny of past administration decisions.
- Security / Counter-Terrorism: Heightened alert levels and resource allocation to monitor and prevent further attacks.
- Cyber / Information Space: Potential for misinformation campaigns exploiting the situation to sow discord.
- Economic / Social: Possible impact on community relations and increased xenophobia affecting social cohesion.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance vetting and monitoring of evacuees with military backgrounds, increase intelligence sharing between agencies, and deploy targeted community outreach programs.
- Medium-Term Posture (1–12 months): Develop resilience measures including improved vetting processes, strengthen partnerships with local law enforcement, and invest in counter-radicalization programs.
- Scenario Outlook:
- Best: No further incidents occur, and effective policies are implemented, reducing the threat level.
- Worst: Coordinated attacks occur, leading to significant casualties and political fallout.
- Most-Likely: Sporadic incidents continue, prompting ongoing security adjustments and policy debates.
6. Key Individuals and Entities
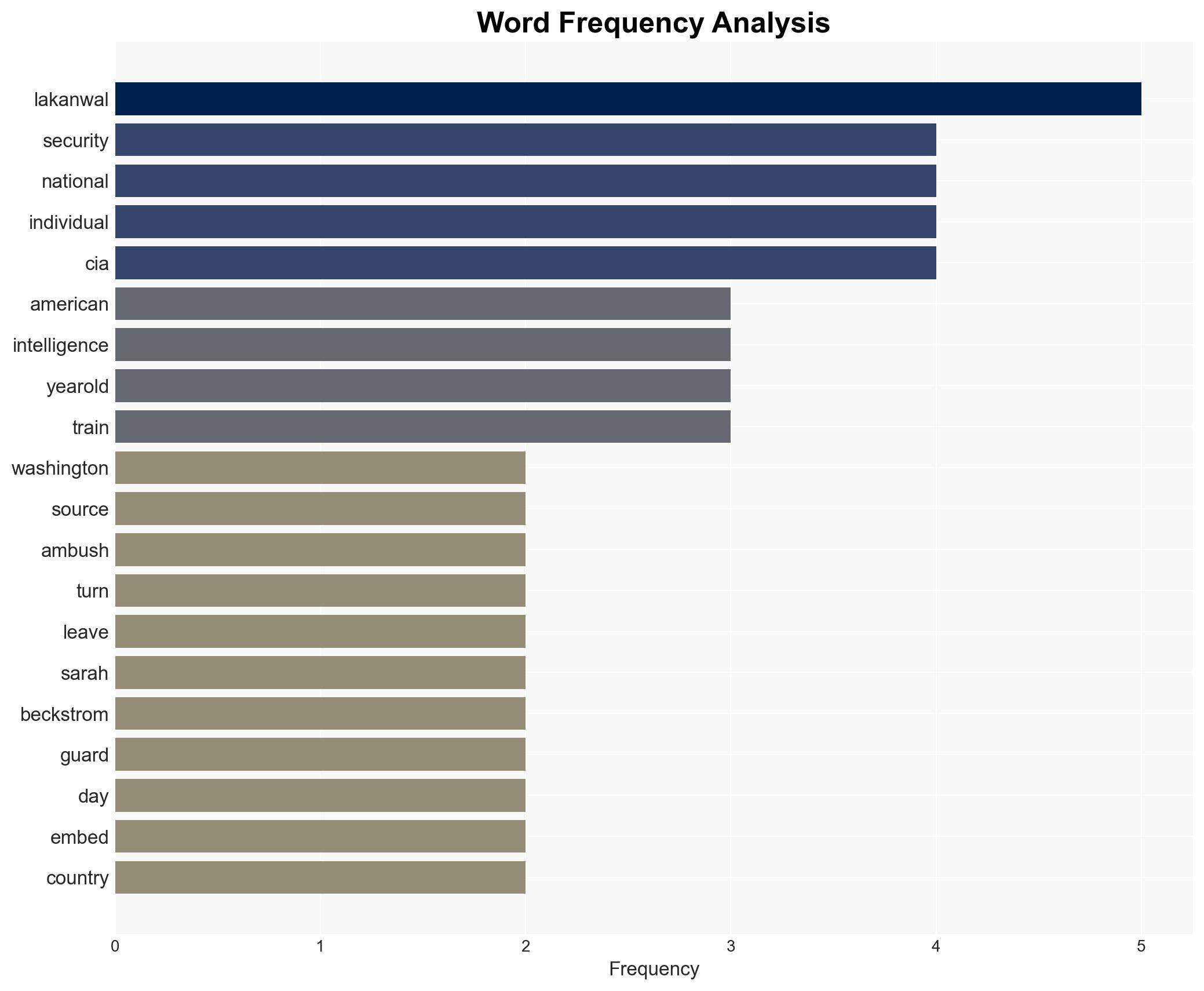
- Rahmanullah Lakanwal
- Mohammad Dawood Alokozay
- John Ratcliffe
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
Counter-Terrorism, national security, immigration policy, intelligence oversight, radicalization, domestic security
Structured Analytic Techniques Applied
- ACH 2.0: Reconstruct likely threat actor intentions via hypothesis testing and structured refutation.
- Indicators Development: Track radicalization signals and propaganda patterns to anticipate operational planning.
- Narrative Pattern Analysis: Analyze spread/adaptation of ideological narratives for recruitment/incitement signals.
Explore more:
Counter-Terrorism Briefs ·
Daily Summary ·
Support us