Investigators looking at who sent Hegseth’s Signal texts sources say – ABC News
Published on: 2025-06-07
Intelligence Report: Investigators looking at who sent Hegseth’s Signal texts sources say – ABC News
1. BLUF (Bottom Line Up Front)
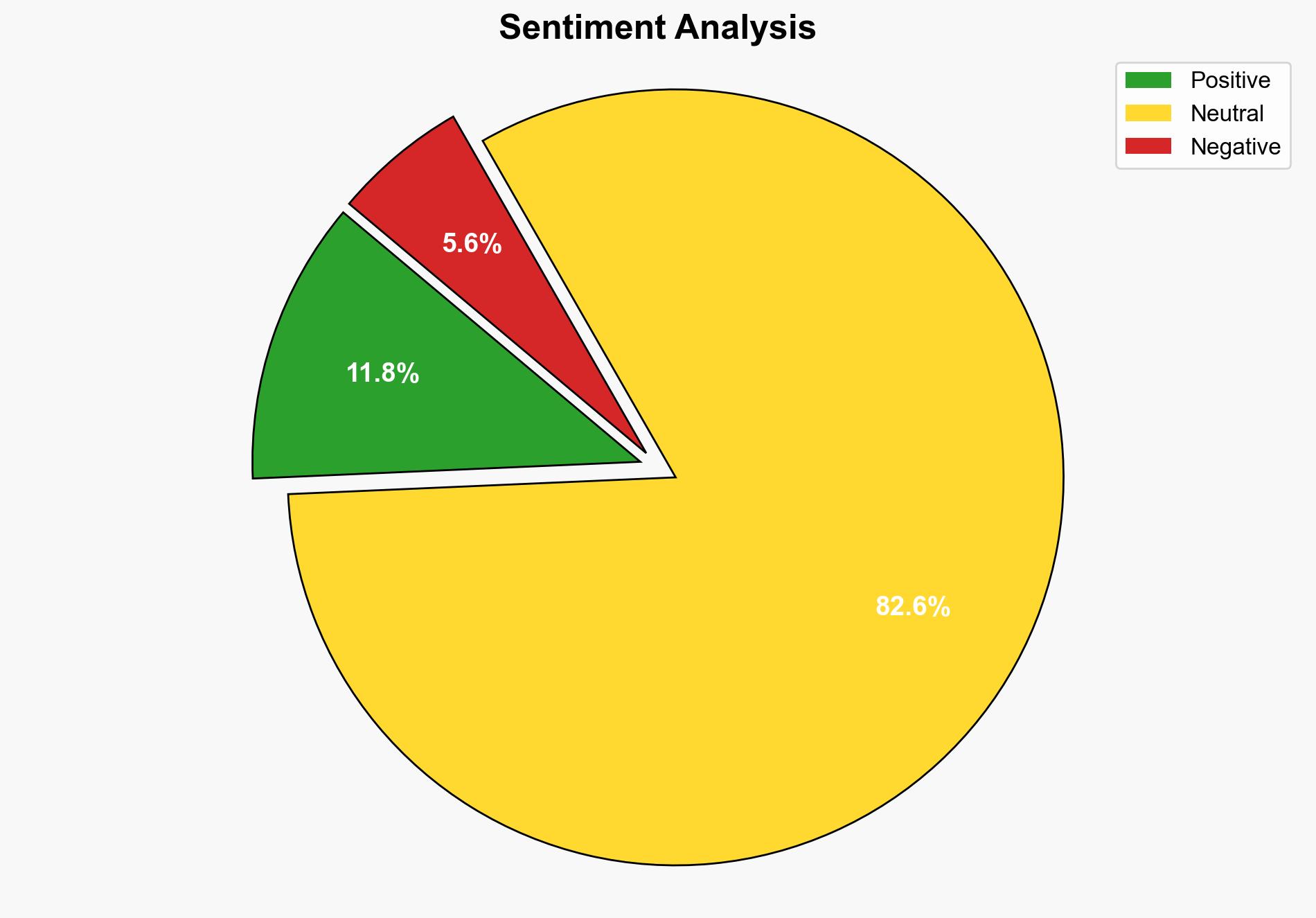
Investigators are examining the unauthorized sharing of military plans via Signal, involving Pete Hegseth. This incident raises concerns about the handling of classified information and potential breaches of national security protocols. Immediate attention is required to assess the scope of the leak and implement measures to prevent future occurrences.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Cognitive Bias Stress Test
Potential biases were identified in the assessment of the leak’s impact, ensuring a balanced view of the situation’s severity and implications.
Bayesian Scenario Modeling
Probabilistic forecasting suggests a moderate likelihood of further unauthorized disclosures if current communication practices remain unchanged.
Network Influence Mapping
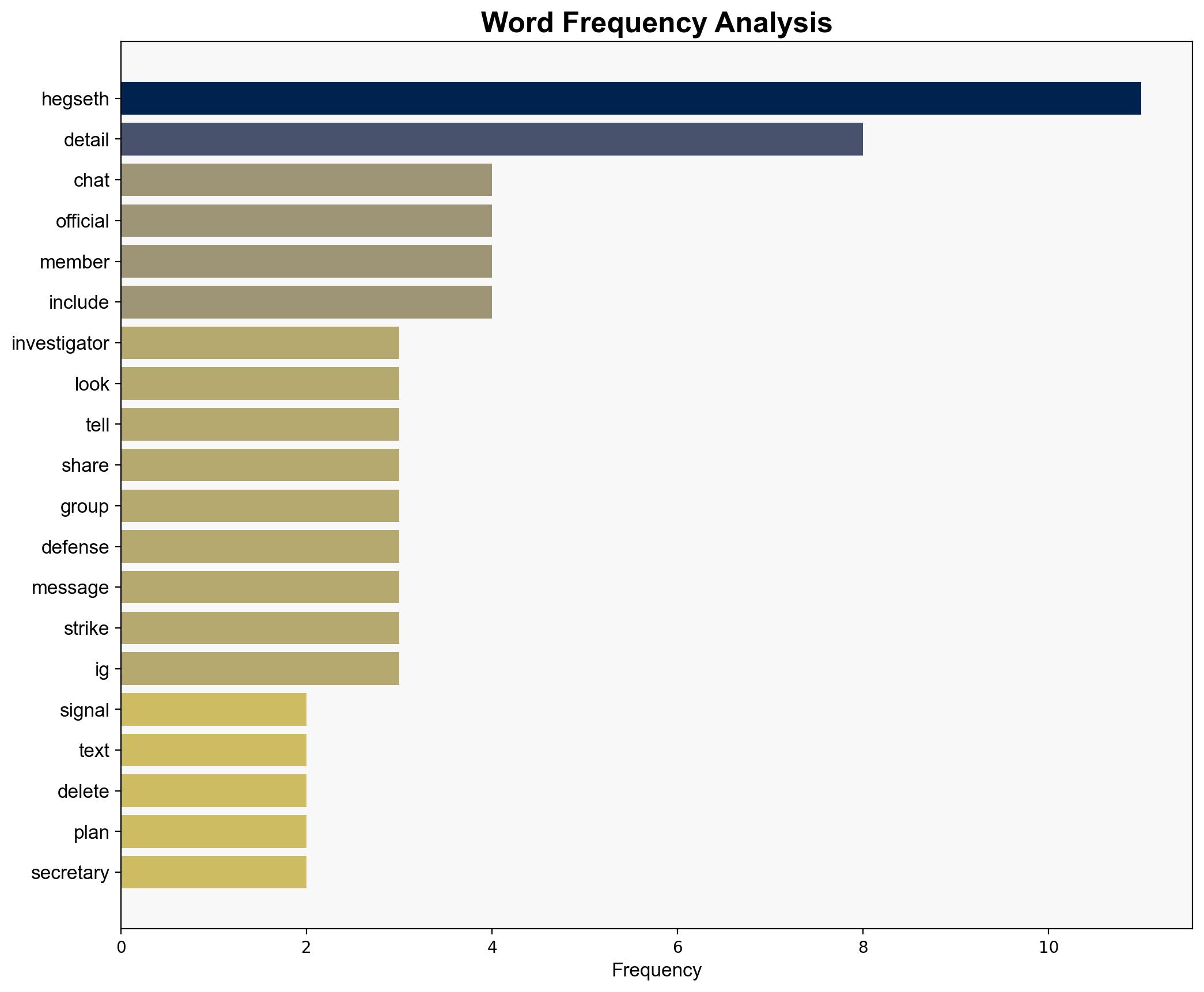
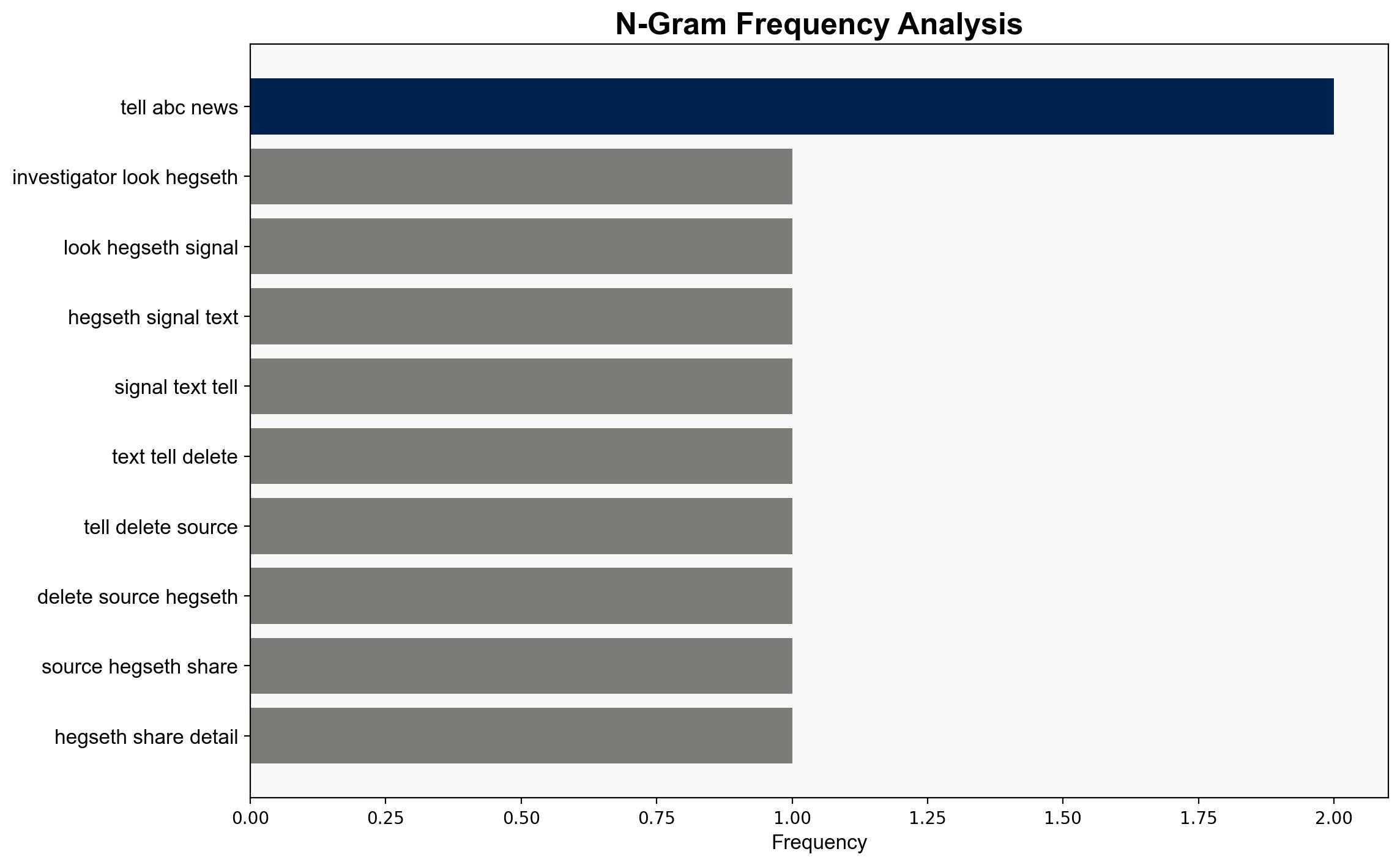
The analysis identified key individuals involved in the communication chain, assessing their potential influence and connections within government structures.
3. Implications and Strategic Risks
The unauthorized sharing of sensitive military plans poses significant risks to national security, potentially compromising operational integrity and diplomatic relations. The incident highlights vulnerabilities in communication protocols and the need for stringent cybersecurity measures.
4. Recommendations and Outlook
- Implement stricter controls and monitoring of communication channels used for sharing classified information.
- Conduct a comprehensive review of current cybersecurity policies and practices to identify and address potential weaknesses.
- Scenario-based projections suggest that without intervention, similar incidents could recur, leading to increased security risks.
5. Key Individuals and Entities
Pete Hegseth, JD Vance, Jennifer Hegseth
6. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus