Iranian-backed hackers go to work after US strikes – ABC News
Published on: 2025-06-25
Intelligence Report: Iranian-backed hackers go to work after US strikes – ABC News
1. BLUF (Bottom Line Up Front)
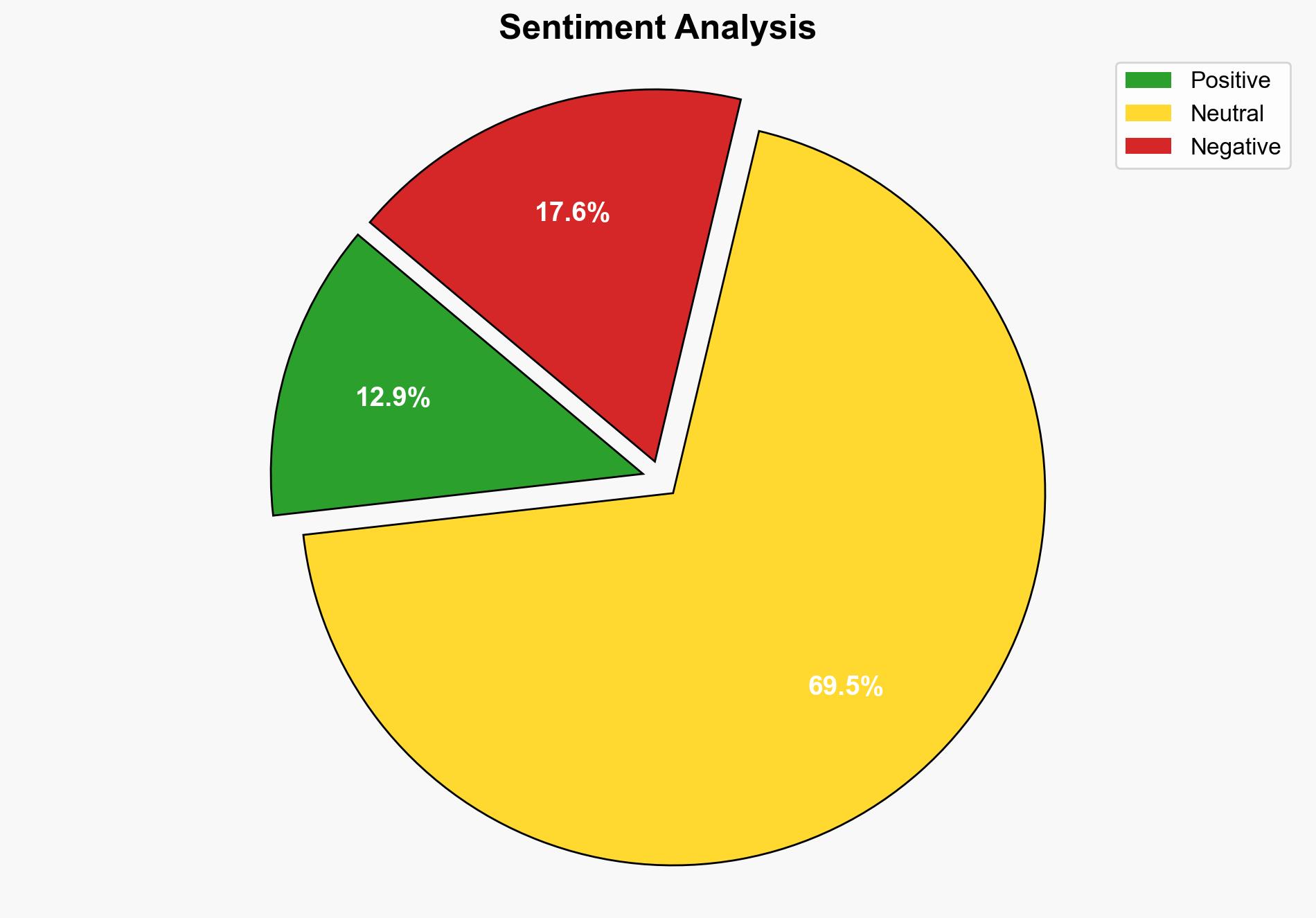
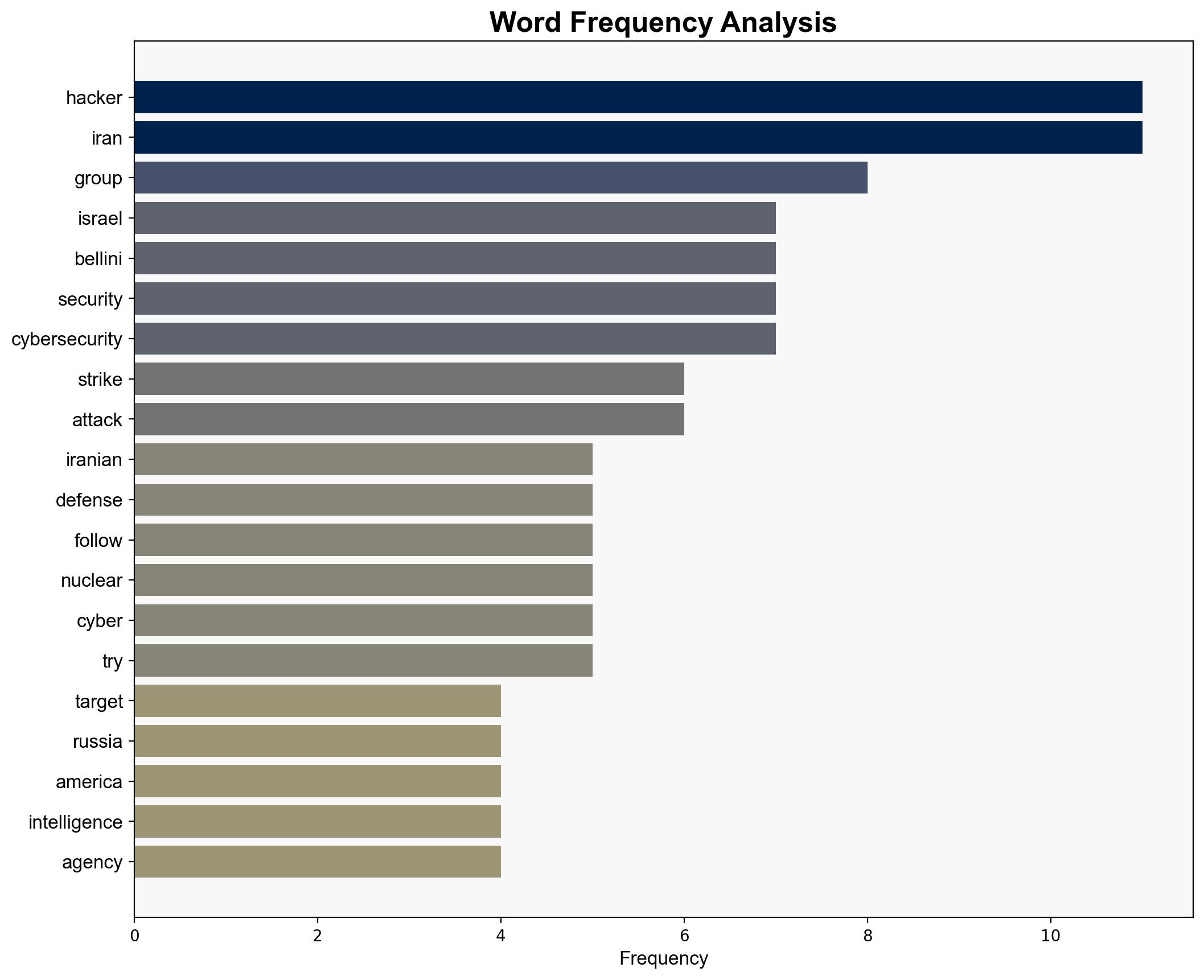
Following recent US strikes on Iranian nuclear facilities, Iranian-backed hackers have intensified cyber operations targeting critical infrastructure sectors such as banking, defense, and oil. This escalation highlights the strategic use of cyber capabilities as a form of asymmetric warfare. Immediate measures are recommended to bolster cybersecurity defenses across vulnerable sectors to mitigate potential disruptions.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Cognitive Bias Stress Test
Potential biases in assessing the threat level of Iranian cyber capabilities have been addressed through red teaming exercises, ensuring a balanced view of their operational reach and intent.
Bayesian Scenario Modeling
Probabilistic forecasting suggests a high likelihood of continued cyber operations from Iranian-backed groups, with potential escalation if geopolitical tensions persist.
Network Influence Mapping
Analysis of influence networks indicates a coordinated effort among Iranian-backed groups, with possible support from allied nations such as Russia and China, enhancing their cyber warfare capabilities.
3. Implications and Strategic Risks
The increased cyber activity poses significant risks to critical infrastructure, potentially leading to economic disruption and psychological impacts. The interconnected nature of global digital networks means that attacks could have cascading effects, impacting international markets and diplomatic relations.
4. Recommendations and Outlook
- Enhance cybersecurity protocols across critical infrastructure sectors, focusing on real-time threat detection and response capabilities.
- Strengthen international cooperation to share intelligence and coordinate responses to cyber threats.
- Scenario-based projections:
- Best Case: Diplomatic efforts lead to de-escalation, reducing cyber threats.
- Worst Case: Cyber attacks escalate, causing widespread economic and infrastructural damage.
- Most Likely: Continued cyber skirmishes with periodic disruptions in targeted sectors.
5. Key Individuals and Entities
Arnie Bellini, Ziv Mador, Jake Williams
6. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus