Is your Android smartphone at risk Heres what you need to know – TalkAndroid
Published on: 2025-04-04
Intelligence Report: Is your Android smartphone at risk? Here’s what you need to know – TalkAndroid
1. BLUF (Bottom Line Up Front)
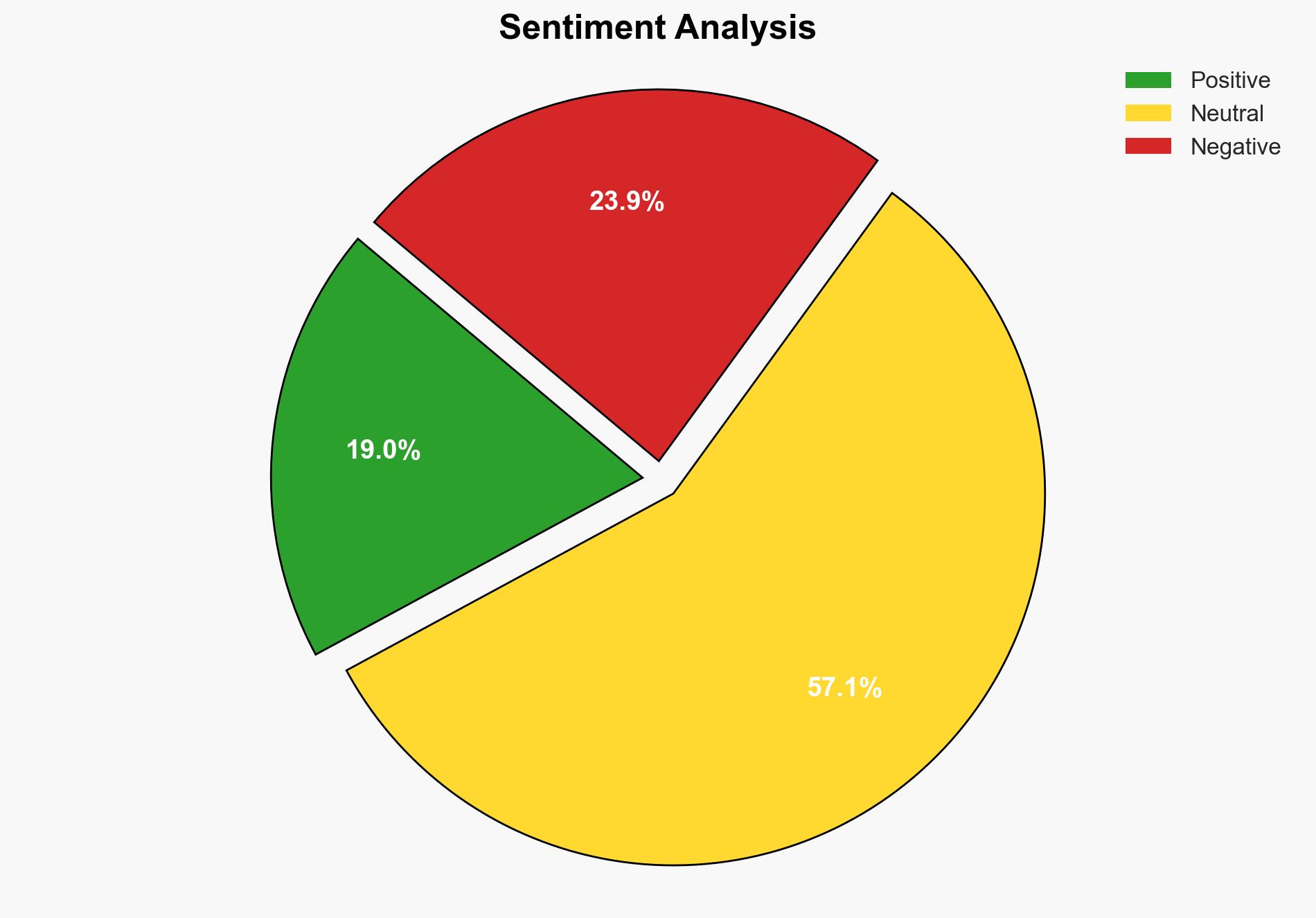
A critical vulnerability in Android systems has been identified and is actively being exploited by sophisticated threat actors, including nation-state entities. This vulnerability allows for unauthorized access and data theft, posing significant risks to personal and national security. Immediate action is recommended to mitigate these risks through software updates and heightened user awareness.
2. Detailed Analysis
The following structured analytic techniques have been applied for this analysis:
General Analysis
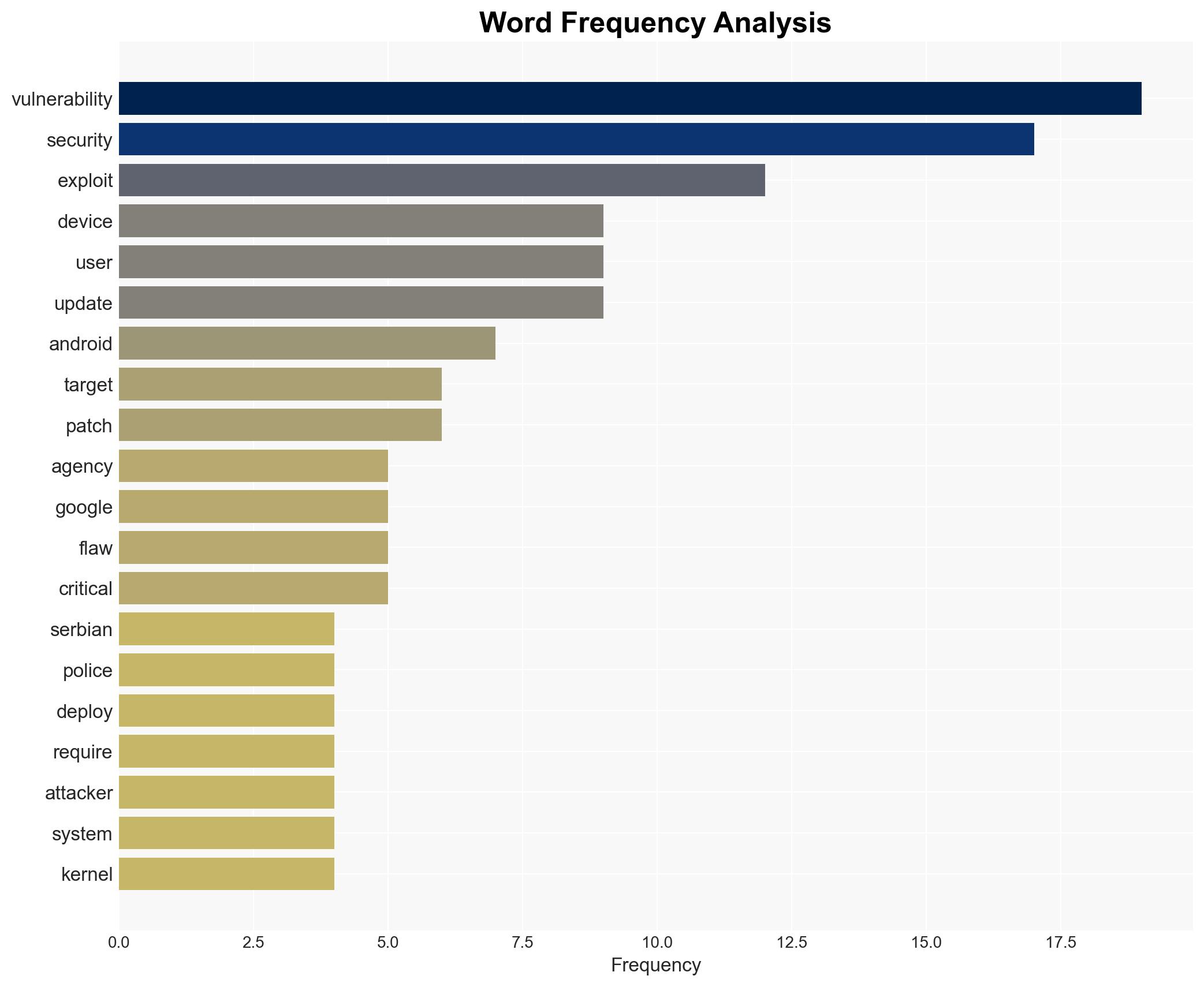
The vulnerability, disclosed in Google’s March security bulletin, affects Android’s code and has been classified as high severity. It is being exploited in targeted attacks, suggesting involvement by advanced cybercriminal groups. The flaw enables attackers to elevate privileges and potentially implant malware, compromising entire systems. Notably, the Serbian police have reportedly used this vulnerability for surveillance purposes, raising concerns about state-sponsored exploitation.
3. Implications and Strategic Risks
The exploitation of this vulnerability poses several strategic risks:
- National Security: Potential for espionage and unauthorized data access by foreign entities.
- Regional Stability: Increased tensions due to state-sponsored surveillance activities.
- Economic Interests: Potential financial losses from compromised corporate data and consumer trust erosion.
The involvement of government agencies in exploiting this vulnerability highlights the need for robust cybersecurity measures and international cooperation.
4. Recommendations and Outlook
Recommendations:
- Encourage immediate deployment of the latest security patches across all Android devices.
- Enhance public awareness campaigns to educate users on avoiding social engineering attacks.
- Strengthen international cybersecurity collaboration to address state-sponsored threats.
Outlook:
Best-case scenario: Rapid patch deployment and user education significantly reduce exploitation incidents.
Worst-case scenario: Continued exploitation leads to widespread data breaches and geopolitical tensions.
Most likely outcome: Ongoing targeted attacks with gradual mitigation as patches are implemented and awareness increases.
5. Key Individuals and Entities
The report mentions significant individuals and organizations, including Google, Serbian police, and cybersecurity researchers. These entities are central to the discovery, exploitation, and mitigation of the identified vulnerability.