Israel Says Iran Is Hacking Security Cameras for Spying – Wired
Published on: 2025-06-21
Intelligence Report: Israel Says Iran Is Hacking Security Cameras for Spying – Wired
1. BLUF (Bottom Line Up Front)
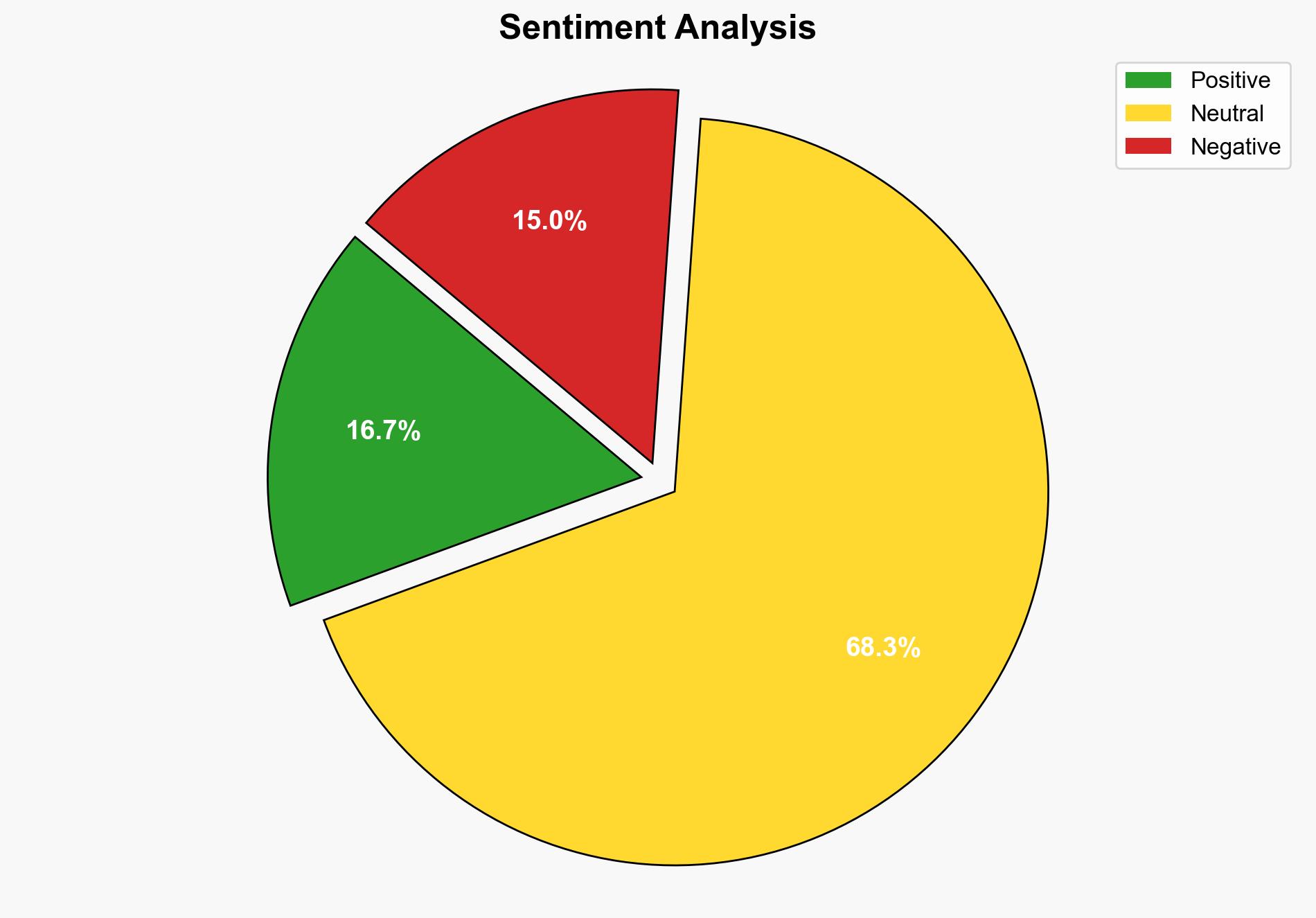
Recent reports indicate that Iran is allegedly hacking private security cameras in Israel for espionage purposes. This activity is part of a broader cyber conflict involving both nations, with potential implications for regional stability and international cybersecurity norms. Immediate measures to enhance cybersecurity protocols are recommended to mitigate these threats.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Causal Layered Analysis (CLA)
– **Surface Events**: Reports of Iranian hacking activities targeting Israeli security cameras.
– **Systemic Structures**: Ongoing cyber conflict between Israel and Iran, characterized by reciprocal cyberattacks.
– **Worldviews**: Perception of cyber capabilities as a strategic tool for national security.
– **Myths**: The narrative of technological superiority as a means of geopolitical influence.
Cross-Impact Simulation
– Potential escalation in cyber activities could lead to increased tensions between Israel and Iran, impacting regional allies and global cybersecurity policies.
Scenario Generation
– **Best Case**: Strengthened cybersecurity measures prevent further breaches, leading to de-escalation.
– **Worst Case**: Escalation of cyberattacks results in significant infrastructure damage and regional instability.
– **Most Likely**: Continued low-level cyber skirmishes with periodic escalations.
Network Influence Mapping
– Key actors include Israeli and Iranian cyber units, regional allies, and international cybersecurity organizations. Their interactions shape the strategic landscape.
3. Implications and Strategic Risks
The hacking incidents underscore vulnerabilities in civilian infrastructure, highlighting the need for robust cybersecurity frameworks. The potential for these cyber activities to spill over into physical conflicts poses a significant risk to regional stability. Additionally, the involvement of non-state actors and proxy groups could complicate diplomatic resolutions.
4. Recommendations and Outlook
- Enhance cybersecurity measures for critical infrastructure, focusing on securing IoT devices like security cameras.
- Engage in diplomatic efforts to establish cyber norms and reduce the risk of escalation.
- Monitor developments closely to anticipate shifts in cyber tactics and strategies.
5. Key Individuals and Entities
– Refael Franco
6. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus