Israeli Spyware Company Paragon Solutions Unintentionally Reveals Surveillance Operations on LinkedIn
Published on: 2026-02-16
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: The Israeli spyware firm that accidentally just exposed itself
1. BLUF (Bottom Line Up Front)
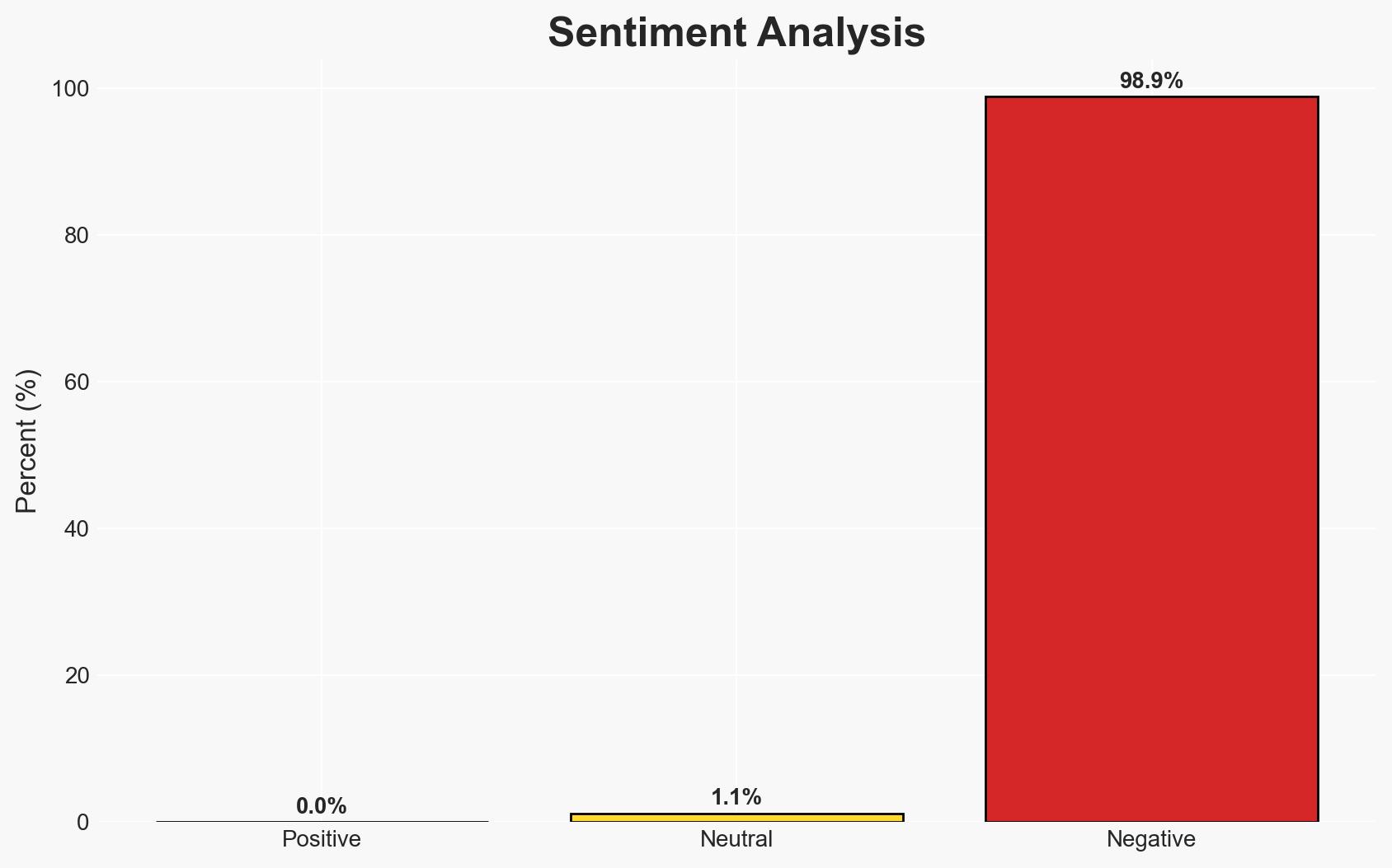
The inadvertent exposure of Paragon Solutions’ spyware dashboard has revealed significant operational details about its surveillance capabilities, impacting global privacy and security. The incident underscores vulnerabilities in the operational security of commercial spyware firms and raises questions about the ethical use of such technologies. This development is likely to affect stakeholders including state agencies, private equity investors, and individuals targeted by such surveillance. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: The exposure was an accidental operational security failure. Supporting evidence includes the unexpected nature of the LinkedIn post and the subsequent public disclosure of sensitive operational details. Key uncertainties include whether this was truly accidental or a deliberate act by an insider.
- Hypothesis B: The exposure was a deliberate act by a whistleblower or insider. This hypothesis is supported by the potential for internal dissent or ethical concerns within the company. However, there is a lack of direct evidence pointing to intentional disclosure.
- Assessment: Hypothesis A is currently better supported due to the lack of direct evidence for intentional disclosure. Indicators that could shift this judgment include insider testimonies or further leaks suggesting deliberate exposure.
3. Key Assumptions and Red Flags
- Assumptions: The exposure was not sanctioned by Paragon’s leadership; Paragon’s spyware capabilities are representative of industry norms; the data revealed is accurate and unaltered.
- Information Gaps: The full scope of Paragon’s client list and target demographics; internal communications within Paragon regarding the exposure; potential legal repercussions for Paragon and its clients.
- Bias & Deception Risks: Potential bias in interpreting the exposure as purely accidental; risk of deception by Paragon in downplaying the significance of the exposure.
4. Implications and Strategic Risks
This development could lead to increased scrutiny and regulatory pressure on the commercial spyware industry, affecting its operational landscape and market dynamics.
- Political / Geopolitical: Potential diplomatic tensions as countries reassess their use of foreign surveillance technologies.
- Security / Counter-Terrorism: Possible shifts in threat vectors as adversaries adapt to exposed surveillance techniques.
- Cyber / Information Space: Increased awareness and countermeasures against spyware, potentially leading to a cybersecurity arms race.
- Economic / Social: Impact on investor confidence in surveillance technology firms and potential public backlash against perceived privacy violations.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Monitor for further disclosures or leaks; engage with cybersecurity experts to assess potential vulnerabilities; initiate dialogue with regulatory bodies.
- Medium-Term Posture (1–12 months): Develop resilience measures against spyware threats; foster partnerships with ethical tech firms; enhance internal security protocols.
- Scenario Outlook: Best: Strengthened regulatory frameworks and ethical standards; Worst: Escalation of spyware capabilities and erosion of privacy; Most-Likely: Gradual adaptation of industry practices with increased oversight.
6. Key Individuals and Entities
- Paragon Solutions
- AE Industrial Partners
- Ehud Barak
- John Scott-Railton
- Citizen Lab
7. Thematic Tags
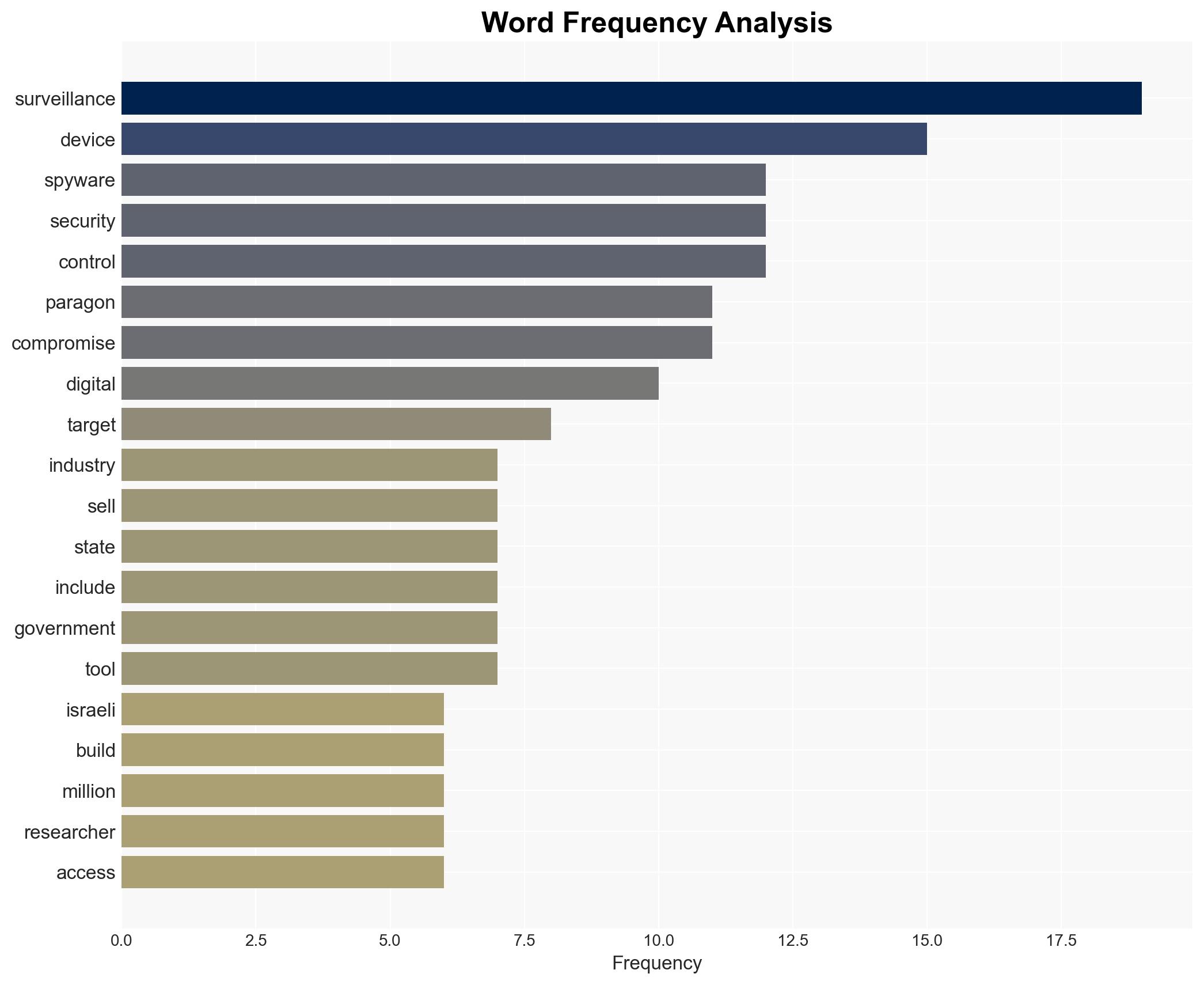
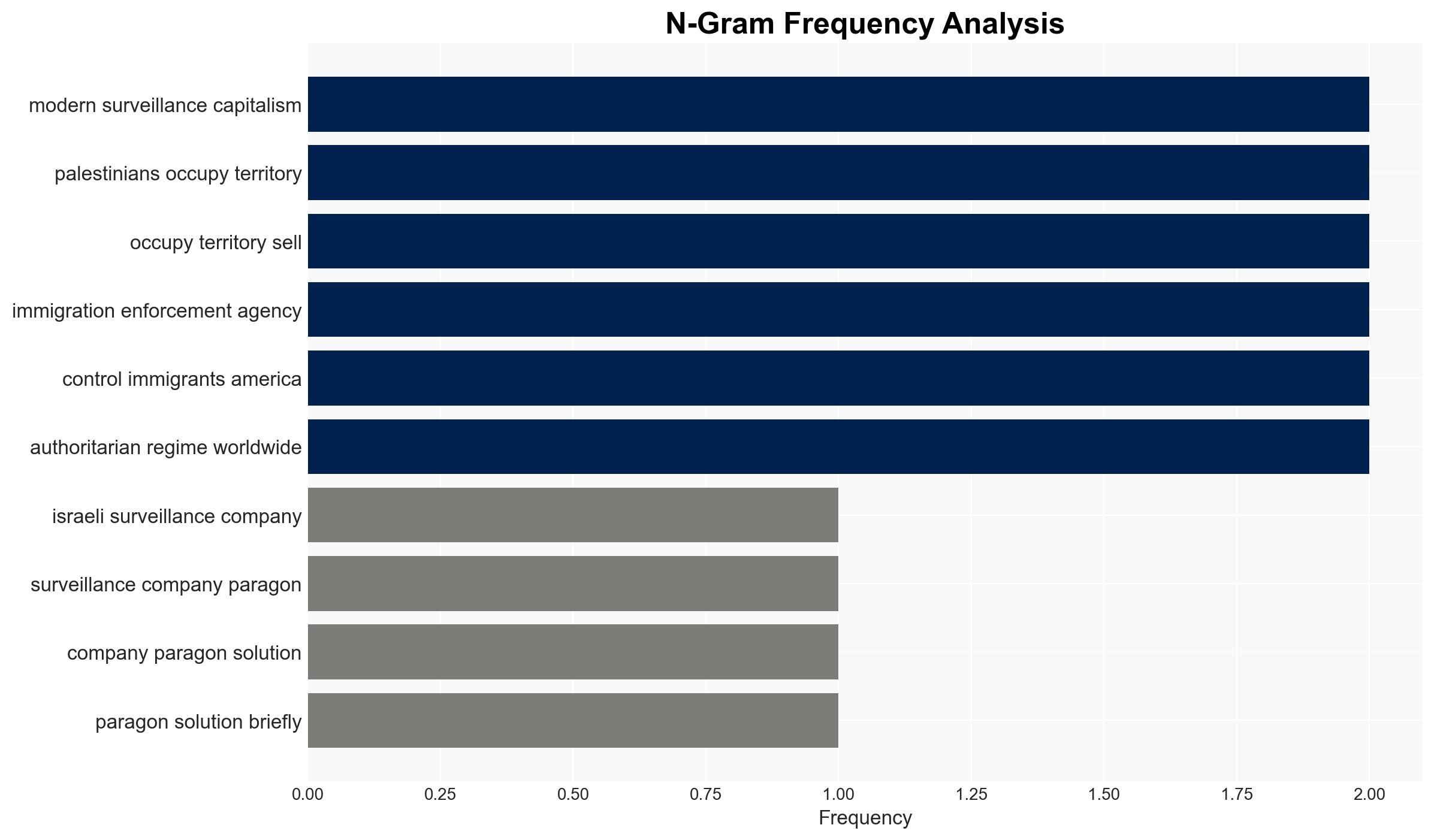
cybersecurity, surveillance, operational security, privacy, spyware industry, regulatory scrutiny, digital rights
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us