Ivanti Releases Security Updates for Connect Secure Policy Secure ZTA Gateways Vulnerability CVE-2025-22457 – Cisa.gov
Published on: 2025-04-04
Intelligence Report: Ivanti Releases Security Updates for Connect Secure Policy Secure ZTA Gateways Vulnerability CVE-2025-22457 – Cisa.gov
1. BLUF (Bottom Line Up Front)
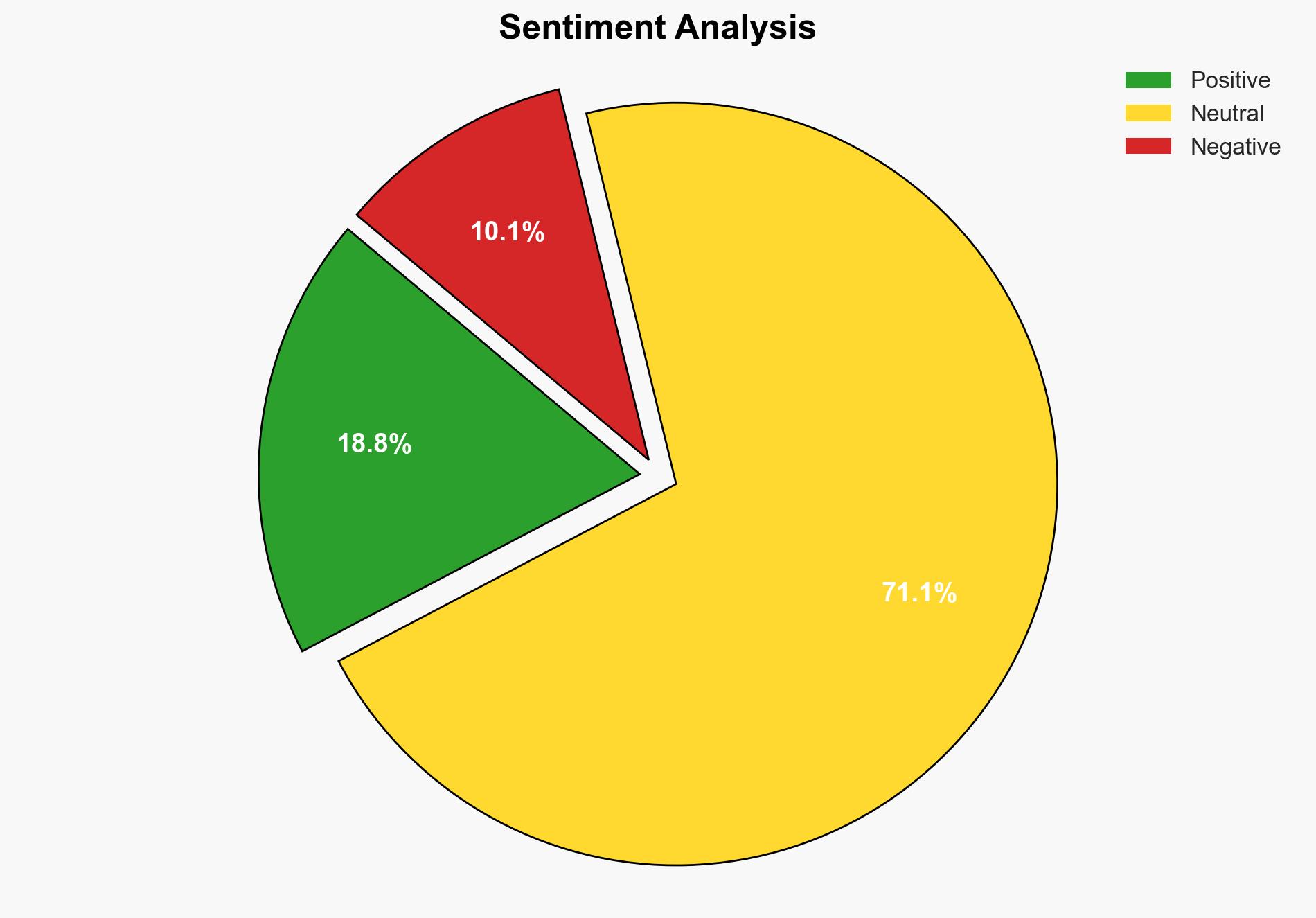
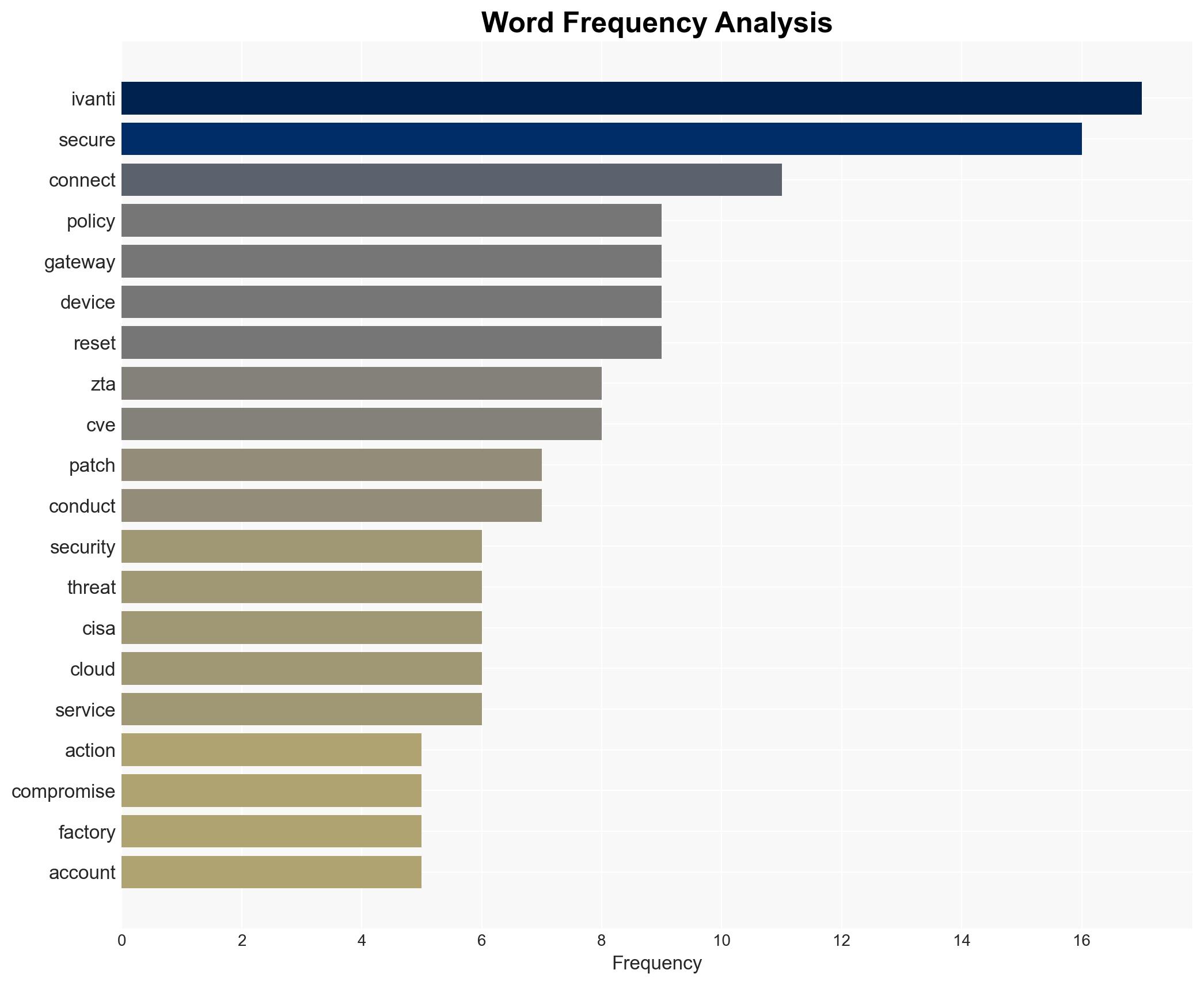
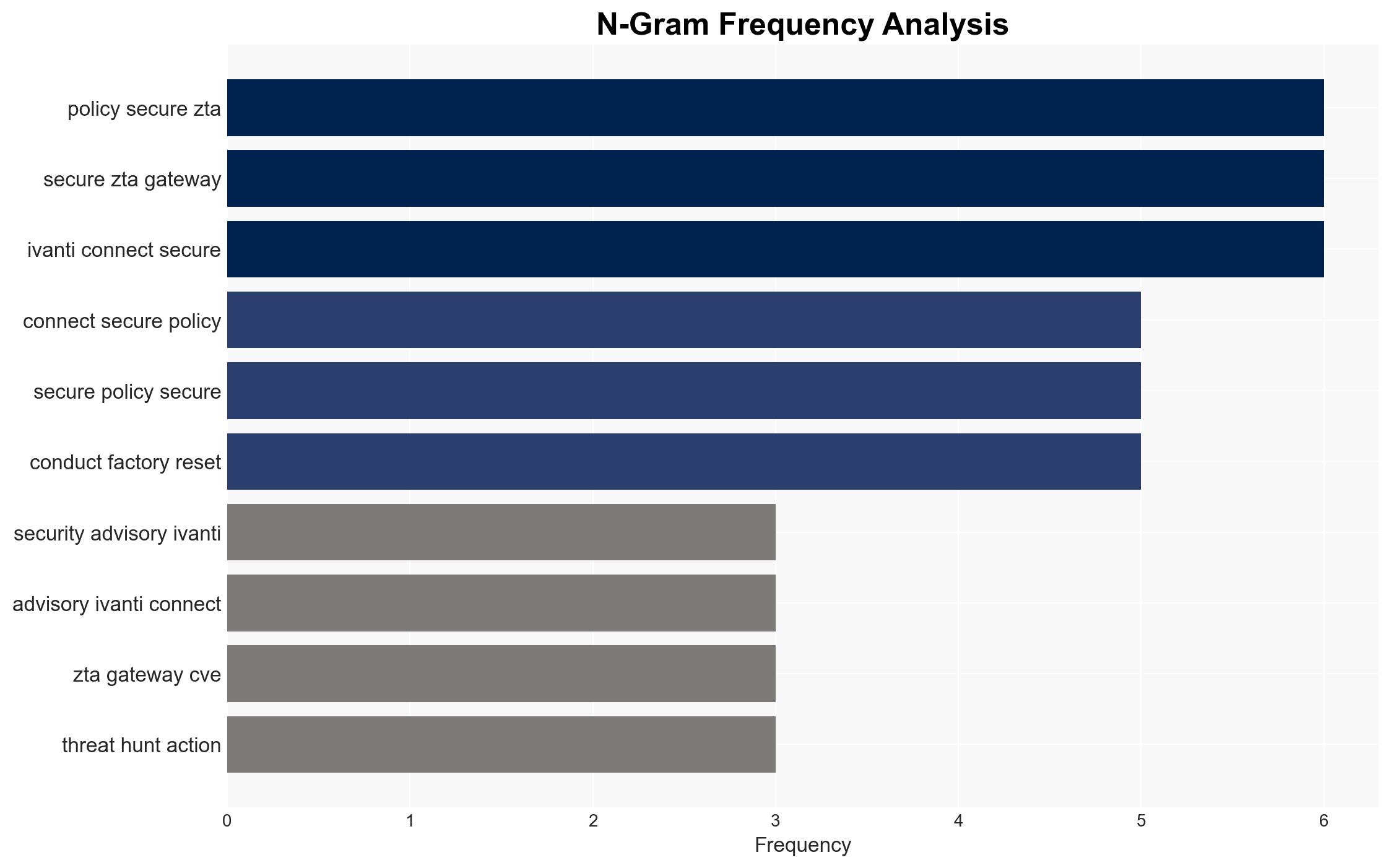
Ivanti has released a security update to address a critical vulnerability, CVE-2025-22457, in its Connect Secure and Policy Secure ZTA Gateways. This vulnerability is being actively exploited by cyber threat actors, suspected to have a nexus with China. Immediate action is required to mitigate potential risks, including conducting threat hunting, applying patches, and resetting compromised systems.
2. Detailed Analysis
The following structured analytic techniques have been applied for this analysis:
General Analysis
The vulnerability CVE-2025-22457 in Ivanti’s Connect Secure and Policy Secure ZTA Gateways has been identified as a critical security threat. Cyber threat actors are actively exploiting this vulnerability, potentially compromising systems globally. The vulnerability allows unauthorized access, posing significant risks to the integrity and confidentiality of affected systems. Ivanti’s security update aims to mitigate these risks by providing patches and guidance for securing affected devices.
3. Implications and Strategic Risks
The exploitation of CVE-2025-22457 poses several strategic risks:
- National Security: Potential unauthorized access to sensitive government and corporate networks.
- Regional Stability: Increased cyber threats may destabilize regional cybersecurity frameworks.
- Economic Interests: Compromised systems could lead to financial losses and damage to critical infrastructure.
4. Recommendations and Outlook
Recommendations:
- Conduct immediate threat hunting and apply Ivanti’s security patches to all affected systems.
- Reset compromised systems using known clean images and revoke compromised credentials.
- Enhance monitoring of authentication and identity management services.
- Implement regular audits of privileged access accounts to prevent unauthorized access.
Outlook:
Best-case scenario: Rapid implementation of security updates and threat mitigation strategies will minimize the impact of the vulnerability.
Worst-case scenario: Delayed response could lead to widespread exploitation, resulting in significant data breaches and operational disruptions.
Most likely outcome: With timely intervention, the majority of systems will be secured, though isolated incidents of exploitation may continue.
5. Key Individuals and Entities
The report mentions significant individuals and organizations involved in the response to the vulnerability. These include Ivanti and CISA, both playing crucial roles in addressing the security threat.