Jaguar Land Rover Cyber Attack Compromises Employee Payroll Data, Impacting UK Economy
Published on: 2025-12-15
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: JLR payroll data stolen in cybercrime that shook UK economy
1. BLUF (Bottom Line Up Front)
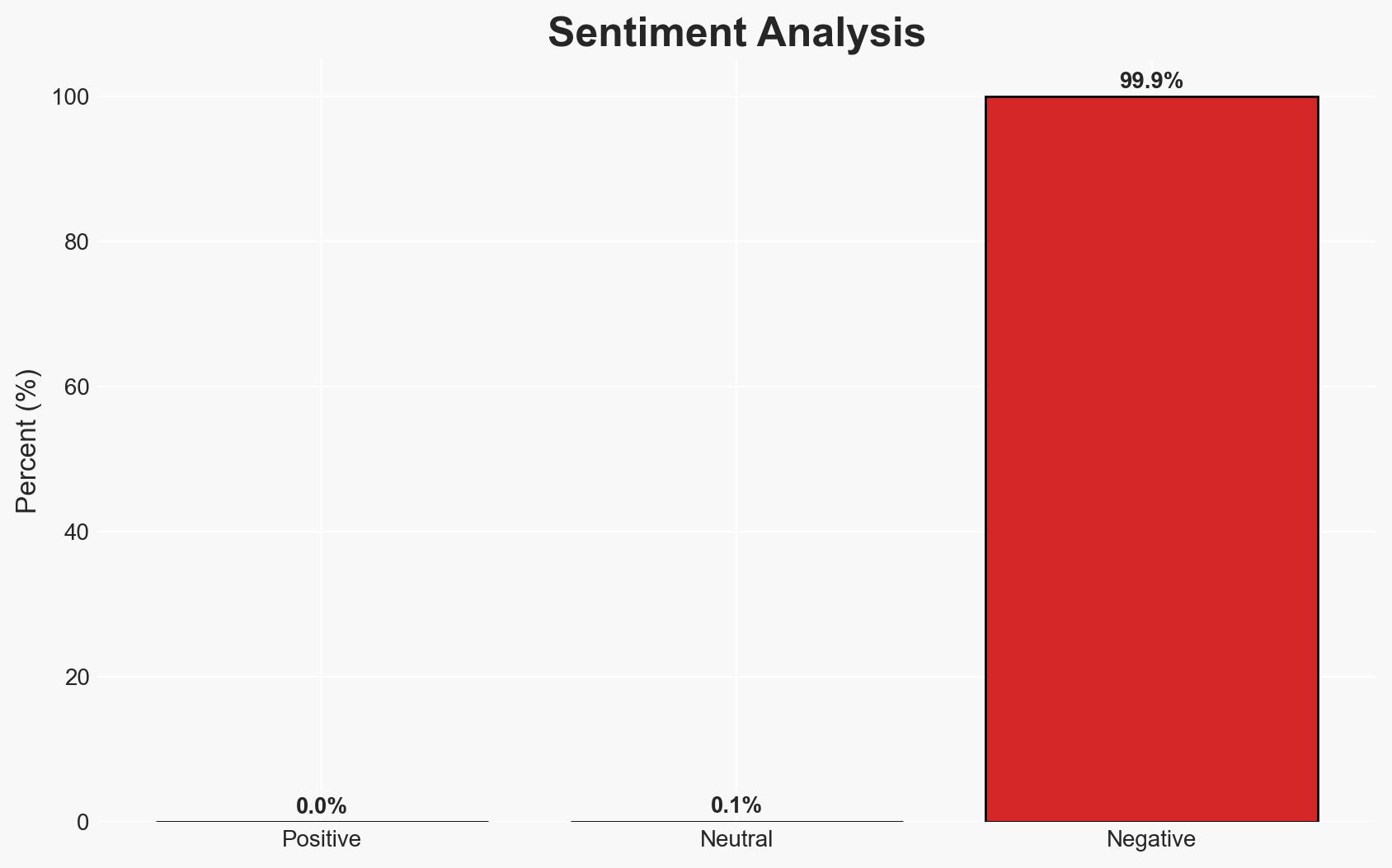
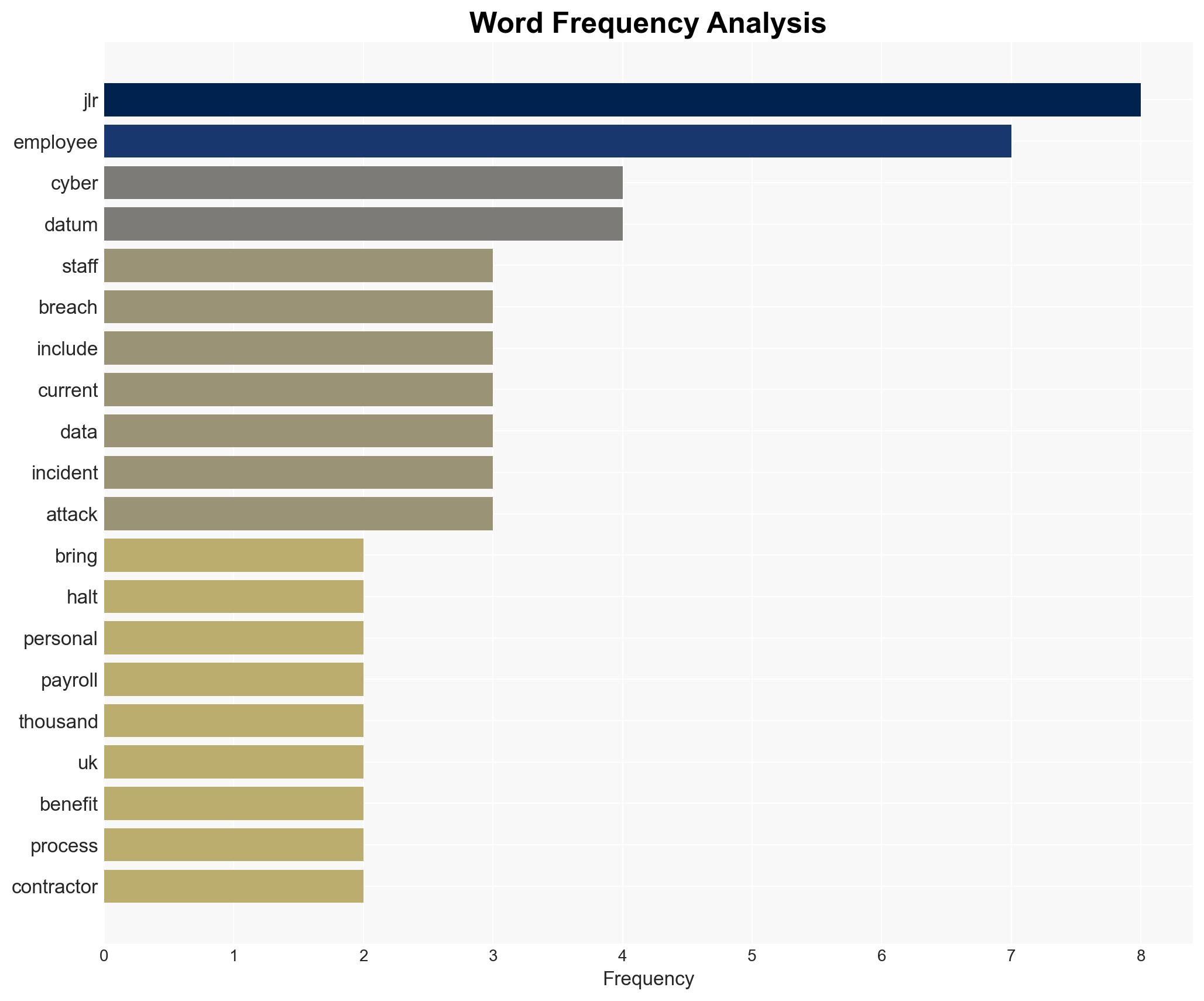
The cyberattack on Jaguar Land Rover (JLR) by the Scattered Lapsus Hunters group resulted in a significant breach of employee payroll data and halted production, causing substantial economic losses. The incident underscores the vulnerabilities of major corporations to cyber threats, with potential systemic impacts on the UK economy. The most likely hypothesis is that the attack was financially motivated, with moderate confidence in this assessment due to the lack of evidence of data misuse thus far.
2. Competing Hypotheses
- Hypothesis A: The attack was financially motivated, aiming to exploit stolen data for monetary gain. This is supported by the theft of sensitive payroll data and the hacker group’s history of targeting large corporations. However, the absence of confirmed misuse of data introduces uncertainty.
- Hypothesis B: The attack was intended to disrupt JLR’s operations as part of a broader campaign against UK economic interests. The significant operational disruption and economic impact support this hypothesis, but the lack of direct evidence linking the attack to geopolitical motives contradicts it.
- Assessment: Hypothesis A is currently better supported due to the nature of the data stolen and the hacker group’s known financial motivations. Indicators that could shift this judgment include evidence of data misuse or geopolitical links.
3. Key Assumptions and Red Flags
- Assumptions: JLR’s cybersecurity measures were insufficient to prevent the breach; the hacker group is primarily financially motivated; the UK economy is vulnerable to cyber disruptions.
- Information Gaps: The exact method of the breach, the full extent of data compromised, and any potential geopolitical motivations remain unclear.
- Bias & Deception Risks: Potential bias in attributing motives based on past incidents; reliance on JLR’s public statements without independent verification may obscure the full impact.
4. Implications and Strategic Risks
The JLR cyberattack could lead to increased scrutiny of corporate cybersecurity practices and potential regulatory changes. It may also embolden other hacker groups to target similar vulnerabilities.
- Political / Geopolitical: Potential strain on UK economic stability and international confidence in UK cybersecurity resilience.
- Security / Counter-Terrorism: Increased threat of similar attacks on critical infrastructure and major corporations.
- Cyber / Information Space: Heightened awareness and potential for increased investment in cybersecurity measures across industries.
- Economic / Social: Short-term economic contraction and potential long-term impacts on employment and consumer confidence.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of financial transactions for fraud, engage with cybersecurity experts to assess vulnerabilities, and communicate transparently with affected employees.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms, invest in advanced threat detection systems, and conduct regular security audits.
- Scenario Outlook:
- Best: No misuse of data occurs, and JLR strengthens its cybersecurity posture.
- Worst: Data is exploited, leading to financial losses and reputational damage.
- Most-Likely: JLR mitigates immediate risks, but faces ongoing challenges in restoring full operational capacity and confidence.
6. Key Individuals and Entities
- Jaguar Land Rover (JLR)
- Scattered Lapsus Hunters
- Cyber Monitoring Centre
- Office for National Statistics
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, economic impact, data breach, corporate vulnerability, UK economy, cybercrime, operational disruption
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us