January 2026 Microsoft Patch Tuesday addresses 112 vulnerabilities, including a critical zero-day exploit.
Published on: 2026-01-14
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Microsoft Patch Tuesday security updates for January 2026 fixed actively exploited zero-day
1. BLUF (Bottom Line Up Front)
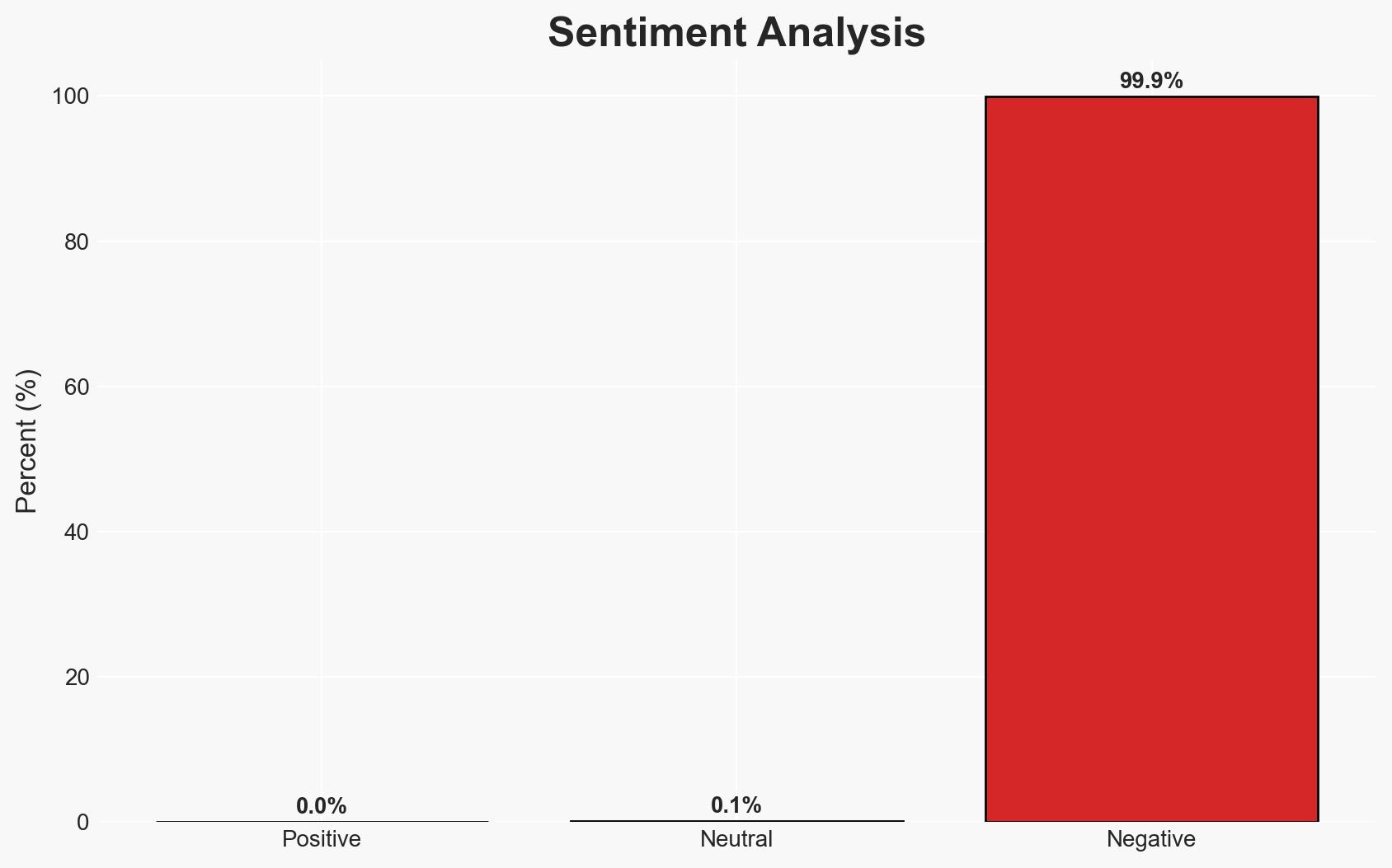
The January 2026 Microsoft Patch Tuesday addressed 114 vulnerabilities, including an actively exploited zero-day (CVE-2026-20805) in Windows Desktop Window Manager. This vulnerability, while not directly executing malicious code, facilitates security bypasses for more severe exploits. The updates also remediate publicly known issues in modem drivers and Secure Boot. The overall confidence in this assessment is moderate, given the limited details on exploitation methods.
2. Competing Hypotheses
- Hypothesis A: The active exploitation of CVE-2026-20805 is part of a targeted campaign by a sophisticated threat actor aiming to gather intelligence or prepare for future attacks. Supporting evidence includes the nature of the vulnerability, which aids in bypassing security protections. However, the lack of detailed attack vectors limits confirmation.
- Hypothesis B: The exploitation of CVE-2026-20805 is opportunistic, conducted by various actors leveraging publicly available information to exploit vulnerable systems indiscriminately. This is supported by the public disclosure of the vulnerability and the commonality of such exploits. Contradictory evidence includes the absence of widespread reports of exploitation.
- Assessment: Hypothesis B is currently better supported due to the public nature of the vulnerabilities and the typical behavior of opportunistic attackers. Key indicators that could shift this judgment include evidence of coordinated attack patterns or attribution to a known threat group.
3. Key Assumptions and Red Flags
- Assumptions: Microsoft’s patches are effective in mitigating the vulnerabilities; attackers have access to the same public information; the vulnerabilities are not part of a broader, undisclosed campaign.
- Information Gaps: Detailed technical analysis of the exploitation methods; specific threat actor attribution; scope and scale of exploitation.
- Bias & Deception Risks: Potential bias in underestimating the sophistication of attackers; reliance on vendor-reported data without independent verification.
4. Implications and Strategic Risks
The resolution of these vulnerabilities could reduce immediate cyber risks but may not deter future exploitation attempts. The ongoing exposure of sensitive information poses a risk of escalated cyber operations.
- Political / Geopolitical: Potential for increased tensions if state-sponsored actors are implicated in exploiting these vulnerabilities.
- Security / Counter-Terrorism: Enhanced risk of cyber espionage and data breaches, particularly targeting critical infrastructure and government systems.
- Cyber / Information Space: Possible increase in cyber defense measures and information sharing among affected entities.
- Economic / Social: Potential disruptions to organizations relying on vulnerable systems, impacting productivity and financial stability.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Urgently apply all relevant patches; monitor systems for signs of exploitation; enhance logging and anomaly detection capabilities.
- Medium-Term Posture (1–12 months): Develop partnerships for threat intelligence sharing; invest in cybersecurity training and awareness programs; assess and update legacy systems.
- Scenario Outlook:
- Best: Successful patching leads to a decrease in exploit attempts.
- Worst: New vulnerabilities are discovered, leading to further exploitation.
- Most-Likely: Continued attempts to exploit patched vulnerabilities, with varying success rates.
6. Key Individuals and Entities
- Microsoft Corporation
- Threat actors exploiting CVE-2026-20805
- Organizations using Windows, Office, Azure, Edge, SharePoint, SQL Server, SMB
7. Thematic Tags
cybersecurity, zero-day vulnerabilities, software patching, threat intelligence, information security, cyber defense, vulnerability management
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us