Jingle Thief Hackers Exploit Cloud Infrastructure to Steal Millions in Gift Cards – Internet
Published on: 2025-10-23
Intelligence Report: Jingle Thief Hackers Exploit Cloud Infrastructure to Steal Millions in Gift Cards – Internet
1. BLUF (Bottom Line Up Front)
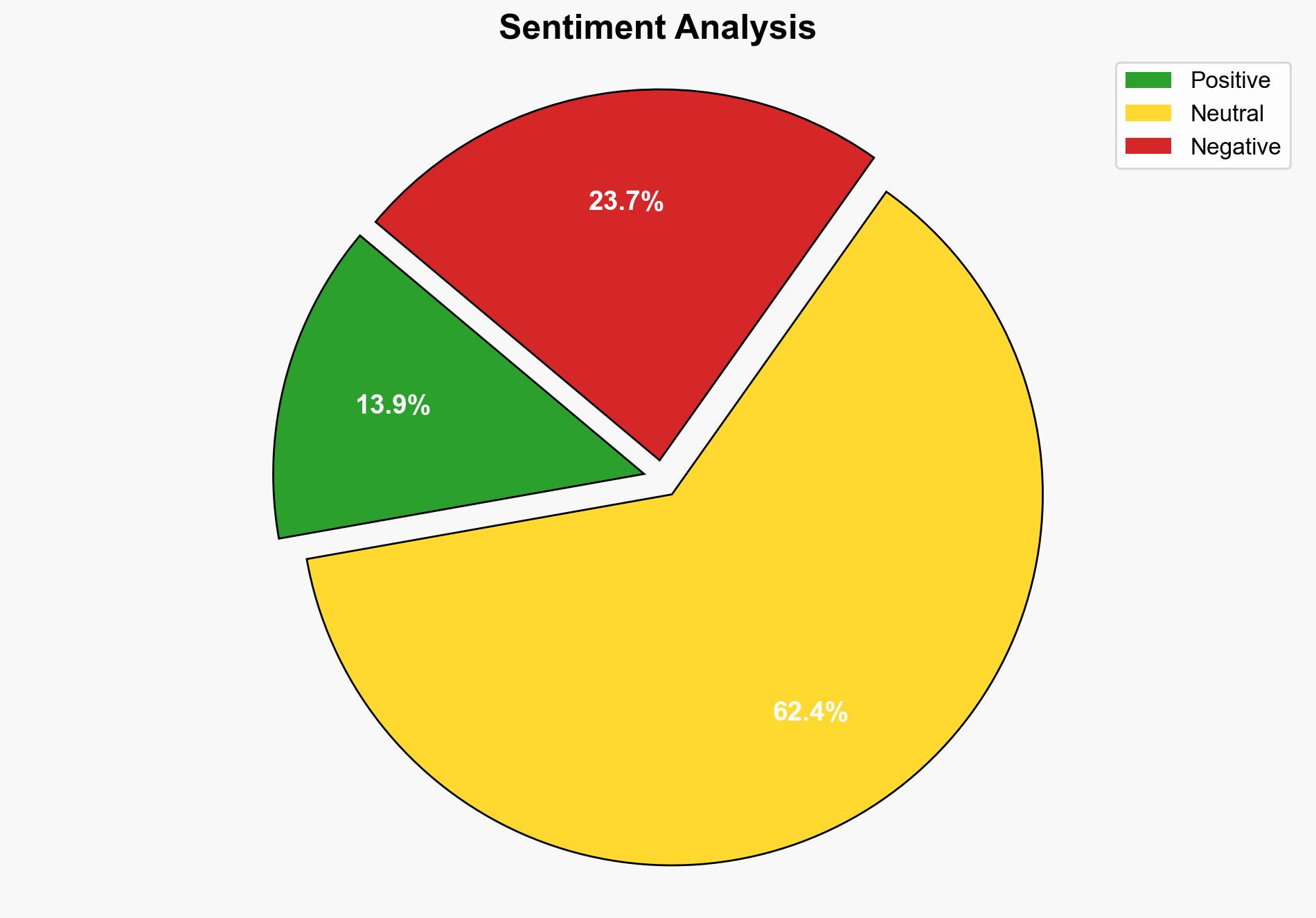
The Jingle Thief cybercriminal group has been exploiting cloud infrastructure to conduct large-scale gift card fraud, particularly targeting retail and consumer service sectors. The most supported hypothesis is that Jingle Thief operates with a high level of sophistication and persistence, maintaining long-term access to compromised environments. Confidence in this assessment is moderate due to the complexity and stealth of their operations. It is recommended to enhance cloud security protocols and increase vigilance during peak holiday seasons.
2. Competing Hypotheses
1. **Hypothesis A**: Jingle Thief is a highly organized and technically skilled group that conducts detailed reconnaissance and exploits cloud vulnerabilities to maintain prolonged access for gift card fraud.
2. **Hypothesis B**: Jingle Thief is a loosely organized group relying on social engineering and opportunistic attacks, with less emphasis on technical sophistication but effective use of phishing and credential theft.
Using the Analysis of Competing Hypotheses (ACH) 2.0, Hypothesis A is better supported. The group’s ability to maintain access for extended periods and conduct extensive reconnaissance suggests a higher level of organization and technical capability.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that Jingle Thief has consistent access to advanced tools and techniques. There is also an assumption that their operations are primarily financially motivated.
– **Red Flags**: The lack of concrete attribution to a specific nation-state or criminal organization raises questions about potential underestimation of their capabilities. The timing of attacks during festive seasons could indicate strategic planning or opportunistic behavior.
4. Implications and Strategic Risks
The pattern of attacks during holiday periods suggests a strategic exploitation of increased consumer activity, posing economic risks to affected sectors. The potential for these tactics to be replicated by other groups increases the threat landscape. If left unchecked, these operations could escalate, leading to broader financial instability and loss of consumer trust in digital transactions.
5. Recommendations and Outlook
- Enhance multi-factor authentication and monitoring of cloud environments to detect unauthorized access.
- Conduct regular security audits and employee training to mitigate phishing risks.
- Scenario Projections:
- **Best Case**: Improved security measures prevent future breaches, and Jingle Thief’s operations are disrupted.
- **Worst Case**: Jingle Thief adapts to security measures, increasing attack frequency and sophistication.
- **Most Likely**: Continued sporadic attacks with gradual improvements in organizational defenses.
6. Key Individuals and Entities
– Stav Setty
– Shachar Roitman
– Palo Alto Networks
– Microsoft
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus