John Goerzen Performant Full-Disk Encryption on a Raspberry Pi but Foiled by Twisty UARTs – Complete.org
Published on: 2025-09-11
Intelligence Report: John Goerzen Performant Full-Disk Encryption on a Raspberry Pi but Foiled by Twisty UARTs – Complete.org
1. BLUF (Bottom Line Up Front)
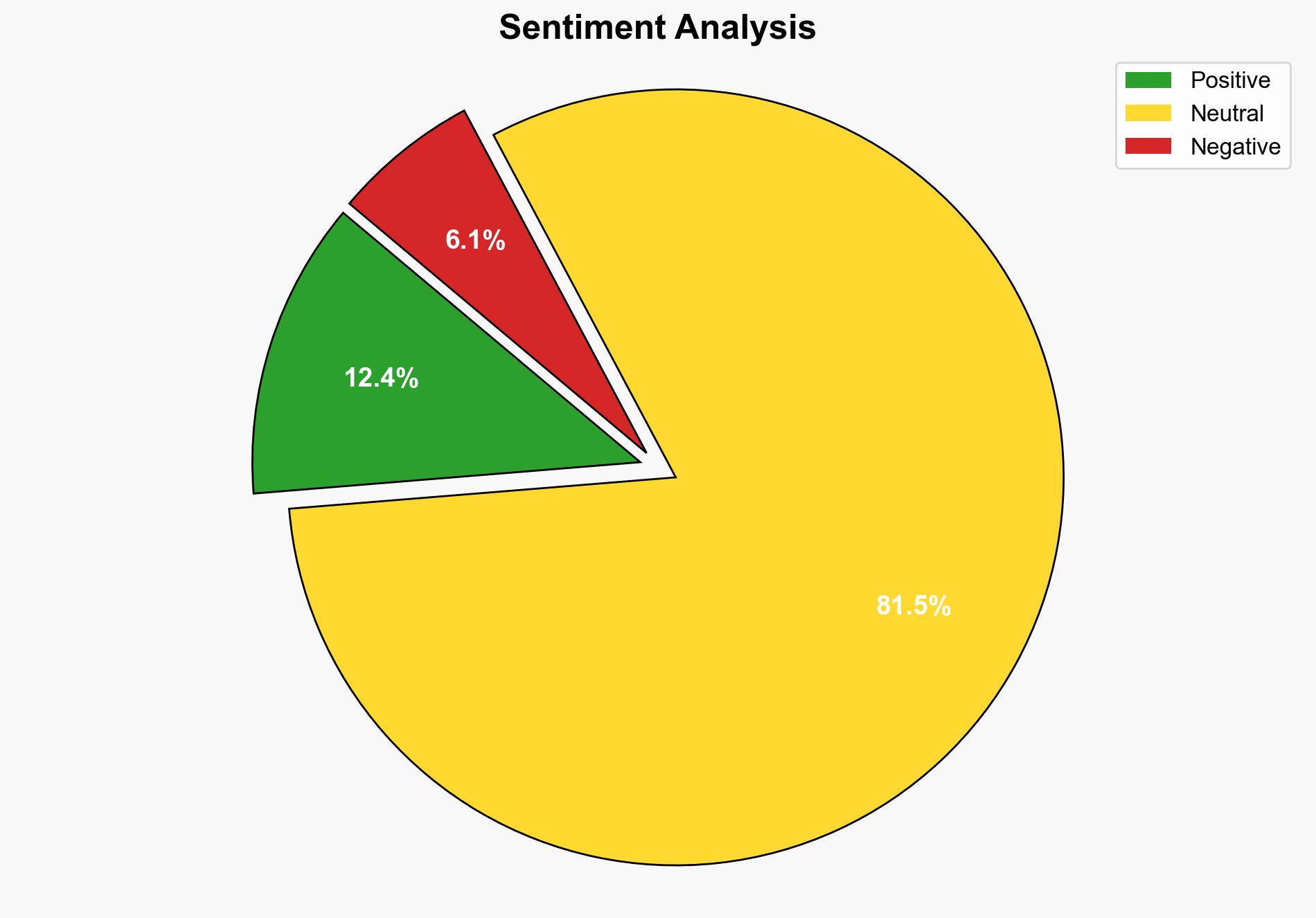
The analysis suggests a moderate confidence level that the primary challenge in implementing full-disk encryption on a Raspberry Pi stems from hardware limitations and configuration complexities, particularly with UARTs. The most supported hypothesis is that these technical obstacles are inherent to the Raspberry Pi’s architecture rather than a result of user error or oversight. It is recommended to explore alternative hardware solutions or custom configurations to overcome these limitations.
2. Competing Hypotheses
1. **Hypothesis A**: The difficulties encountered in implementing full-disk encryption are primarily due to the Raspberry Pi’s hardware limitations, particularly its UART configuration and lack of native AES instruction support.
2. **Hypothesis B**: The challenges are largely due to user configuration errors or lack of familiarity with the Raspberry Pi’s system architecture and available resources.
Using the Analysis of Competing Hypotheses (ACH) 2.0, Hypothesis A is better supported. The source text highlights specific hardware constraints, such as the absence of certain modules in the initramfs and the need for custom kernel builds, which align with known limitations of the Raspberry Pi platform.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that the Raspberry Pi’s hardware limitations are the primary barrier to successful encryption implementation. It is also assumed that the user has a reasonable level of expertise in handling such configurations.
– **Red Flags**: The absence of detailed documentation on UART configurations and potential user errors in kernel parameter settings could skew the analysis. Additionally, the reliance on anecdotal evidence from a single source may introduce bias.
4. Implications and Strategic Risks
The inability to implement robust encryption on widely used devices like the Raspberry Pi poses cybersecurity risks, especially if these devices are deployed in sensitive environments. This could lead to data breaches or unauthorized access. The broader implication is the potential vulnerability of IoT devices that rely on similar architectures.
5. Recommendations and Outlook
- **Mitigation**: Consider using alternative hardware with better support for encryption, such as devices with native AES instruction sets.
- **Exploitation**: Develop and distribute comprehensive guides for configuring encryption on Raspberry Pi, addressing common pitfalls and hardware constraints.
- **Scenario Projections**:
– **Best Case**: Successful implementation of encryption through community-driven solutions and hardware upgrades.
– **Worst Case**: Persistent vulnerabilities leading to widespread exploitation of Raspberry Pi devices.
– **Most Likely**: Gradual improvement in encryption capabilities through iterative software updates and community support.
6. Key Individuals and Entities
John Goerzen is the primary individual mentioned, providing firsthand insights into the challenges faced with Raspberry Pi encryption.
7. Thematic Tags
cybersecurity, IoT security, hardware limitations, encryption challenges