Konni Hackers Turn Googles Find Hub into a Remote Data-Wiping Weapon – Internet
Published on: 2025-11-10
Intelligence Report: Konni Hackers Turn Google’s Find Hub into a Remote Data-Wiping Weapon – Internet
1. BLUF (Bottom Line Up Front)
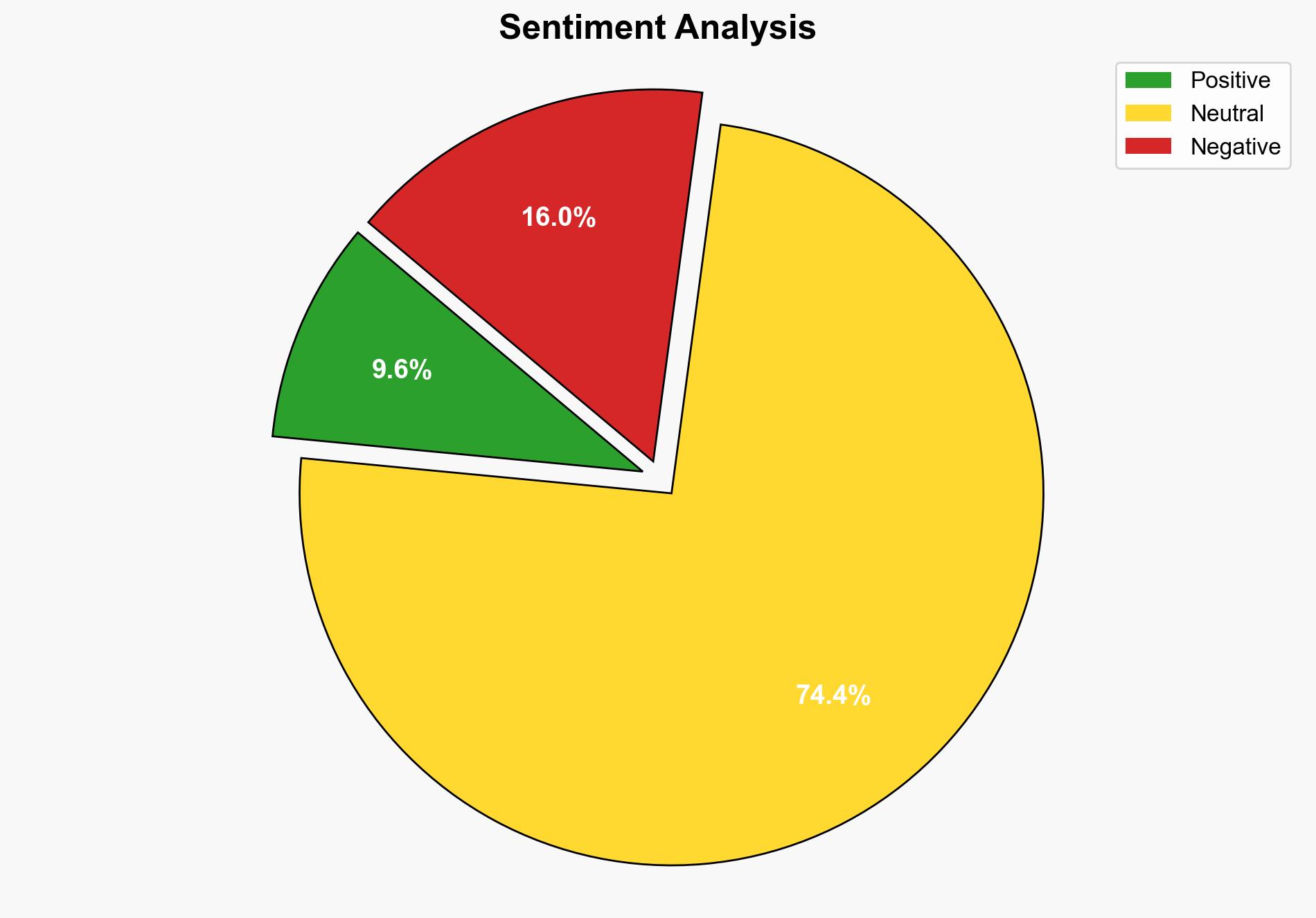
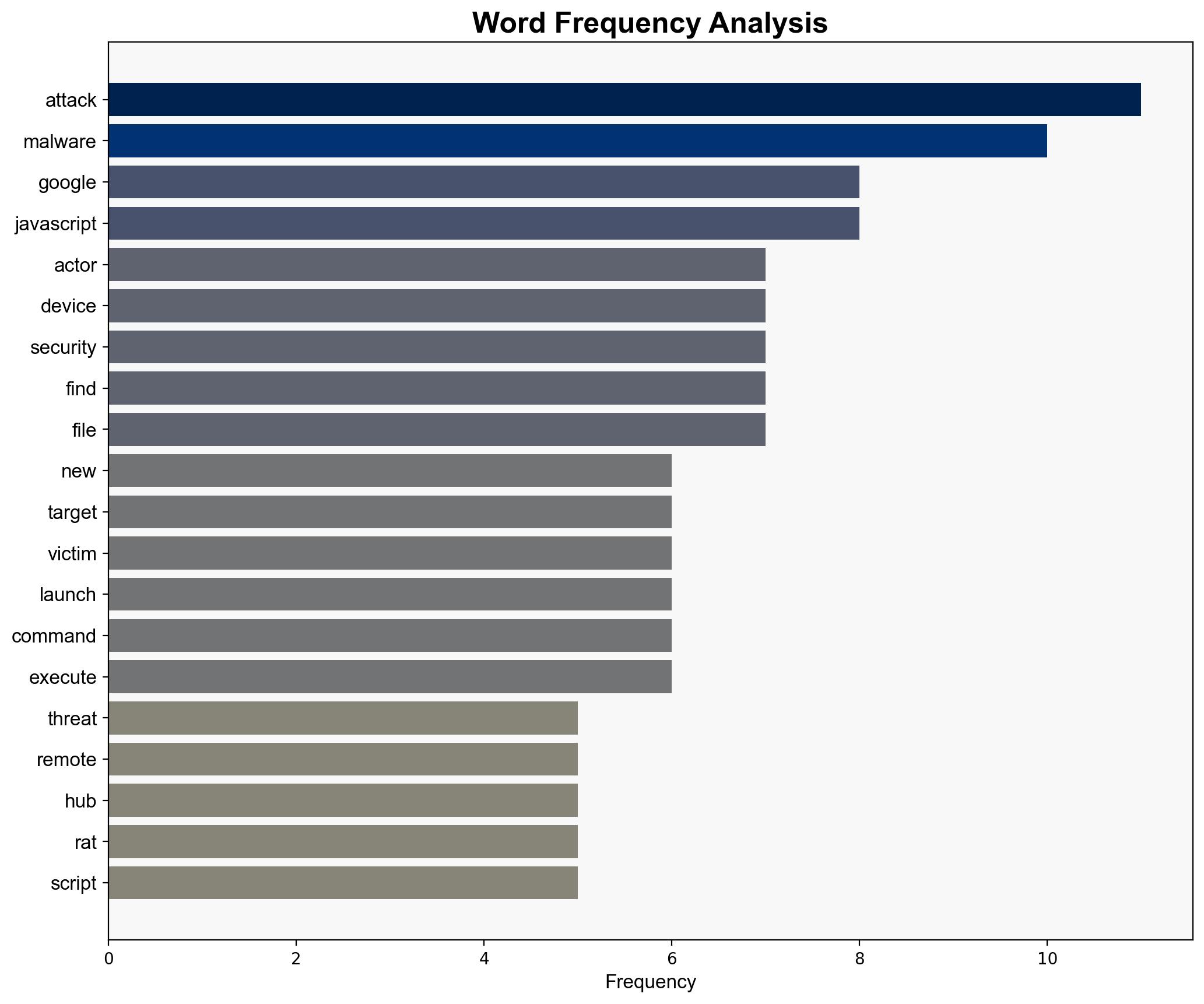
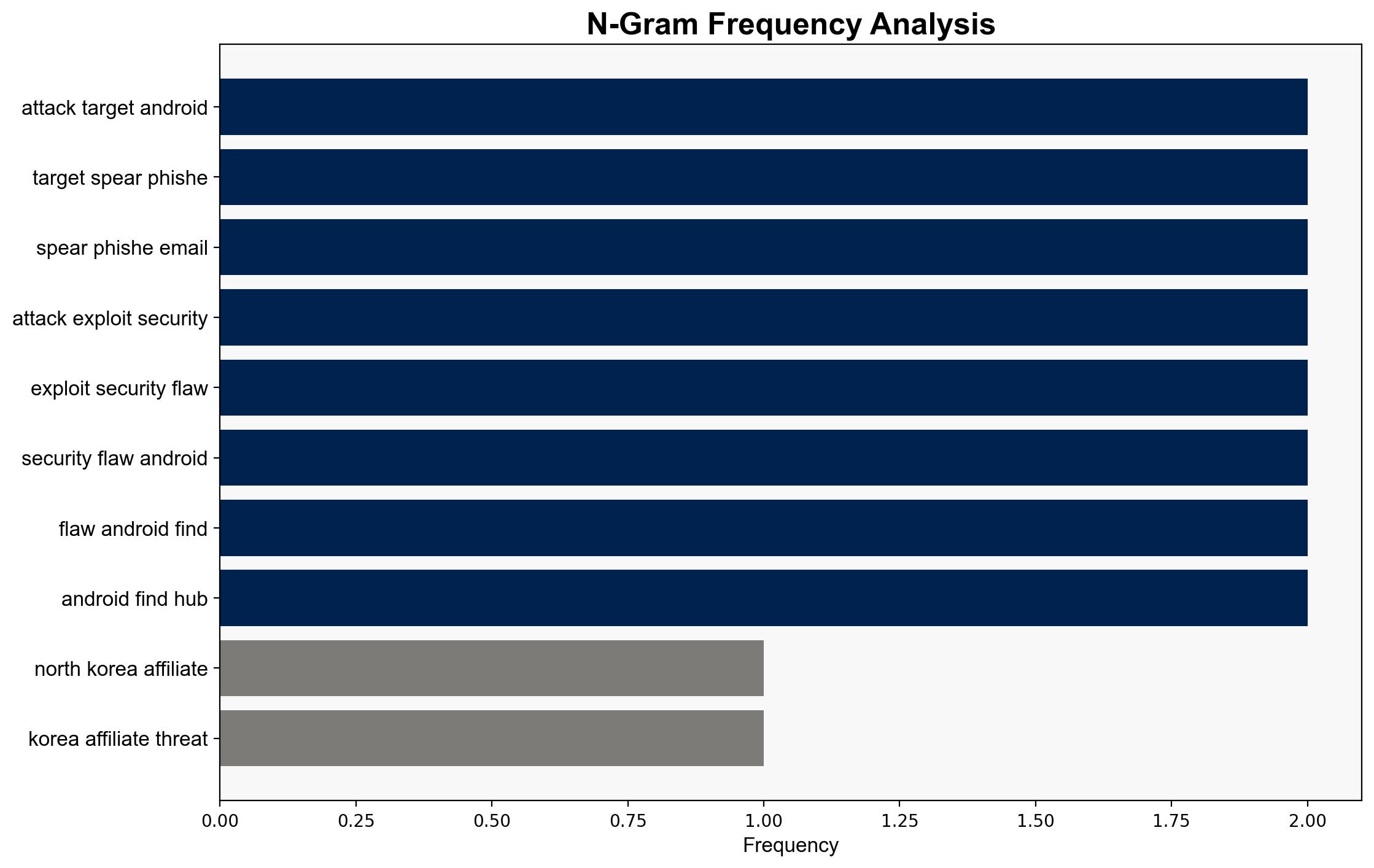
The Konni hacking group has weaponized Google’s Find Hub to remotely wipe data from targeted devices, posing a significant cybersecurity threat. The most supported hypothesis is that this is part of a broader campaign targeting South Korean entities, leveraging psychological manipulation and strategic deception. Confidence level: Moderate. Recommended action: Enhance cybersecurity protocols, particularly for South Korean organizations, and increase awareness of phishing tactics.
2. Competing Hypotheses
1. **Hypothesis A**: Konni’s activities are primarily aimed at disrupting South Korean organizations by exploiting Google’s Find Hub for data wiping, as part of a broader cyber-espionage campaign.
2. **Hypothesis B**: The attacks serve as a testbed for developing more sophisticated cyber weapons, with South Korean targets chosen due to their geopolitical significance and vulnerability to psychological operations.
Using ACH 2.0, Hypothesis A is better supported due to the specific targeting of South Korean entities and the use of spear-phishing tactics that align with known Konni strategies.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that Konni is acting independently and not as a proxy for a larger state-sponsored operation. The effectiveness of the phishing tactics assumes a lack of cybersecurity awareness among targets.
– **Red Flags**: The absence of direct attribution to a state actor raises questions about the ultimate objectives. The use of legitimate services like Google’s Find Hub suggests potential exploitation of other similar services.
4. Implications and Strategic Risks
The weaponization of legitimate services for cyber-attacks indicates a shift towards more covert and sophisticated methods, increasing the difficulty of detection and prevention. This could lead to heightened tensions in the Korean Peninsula and potentially provoke retaliatory cyber operations. The psychological impact on targeted individuals and organizations could undermine trust in digital services and increase operational costs due to enhanced security measures.
5. Recommendations and Outlook
- **Mitigation**: Implement advanced cybersecurity training focused on phishing awareness and response. Strengthen multi-factor authentication and monitoring of device management services.
- **Exploitation**: Leverage the incident to advocate for improved international cybersecurity standards and cooperation.
- **Scenarios**:
- **Best Case**: Increased awareness leads to improved defenses, reducing the effectiveness of similar attacks.
- **Worst Case**: Escalation of cyber-attacks leads to significant data breaches and geopolitical instability.
- **Most Likely**: Continued low-level cyber skirmishes with incremental improvements in defensive measures.
6. Key Individuals and Entities
– Konni (hacking group)
– Genian Security Center (GSC)
– Google (service exploited)
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus