La Sapienza University in Rome remains offline following a ransomware attack disrupting operations since Febr…
Published on: 2026-02-07
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Italian university La Sapienza still offline to mitigate recent cyber attack
1. BLUF (Bottom Line Up Front)
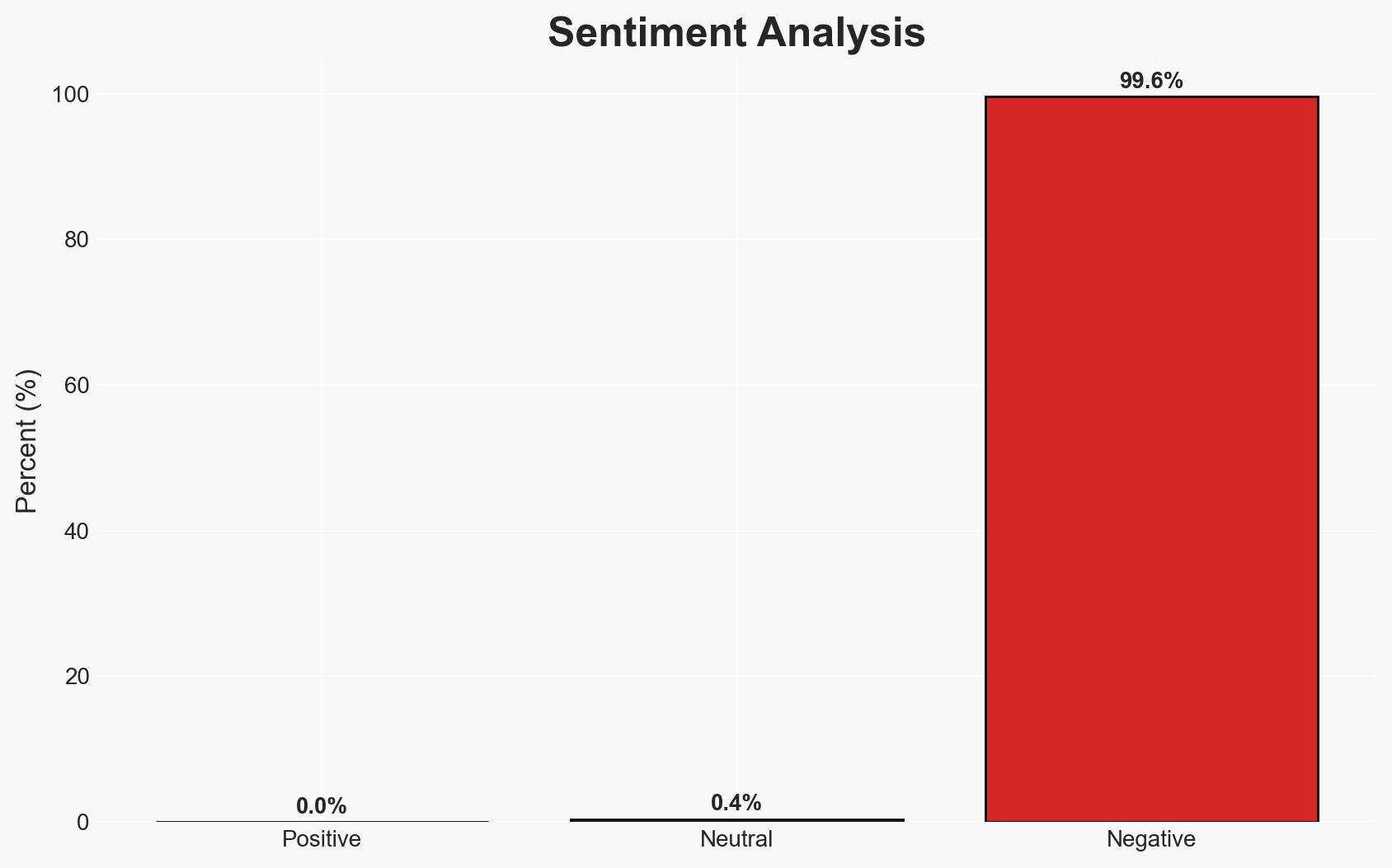
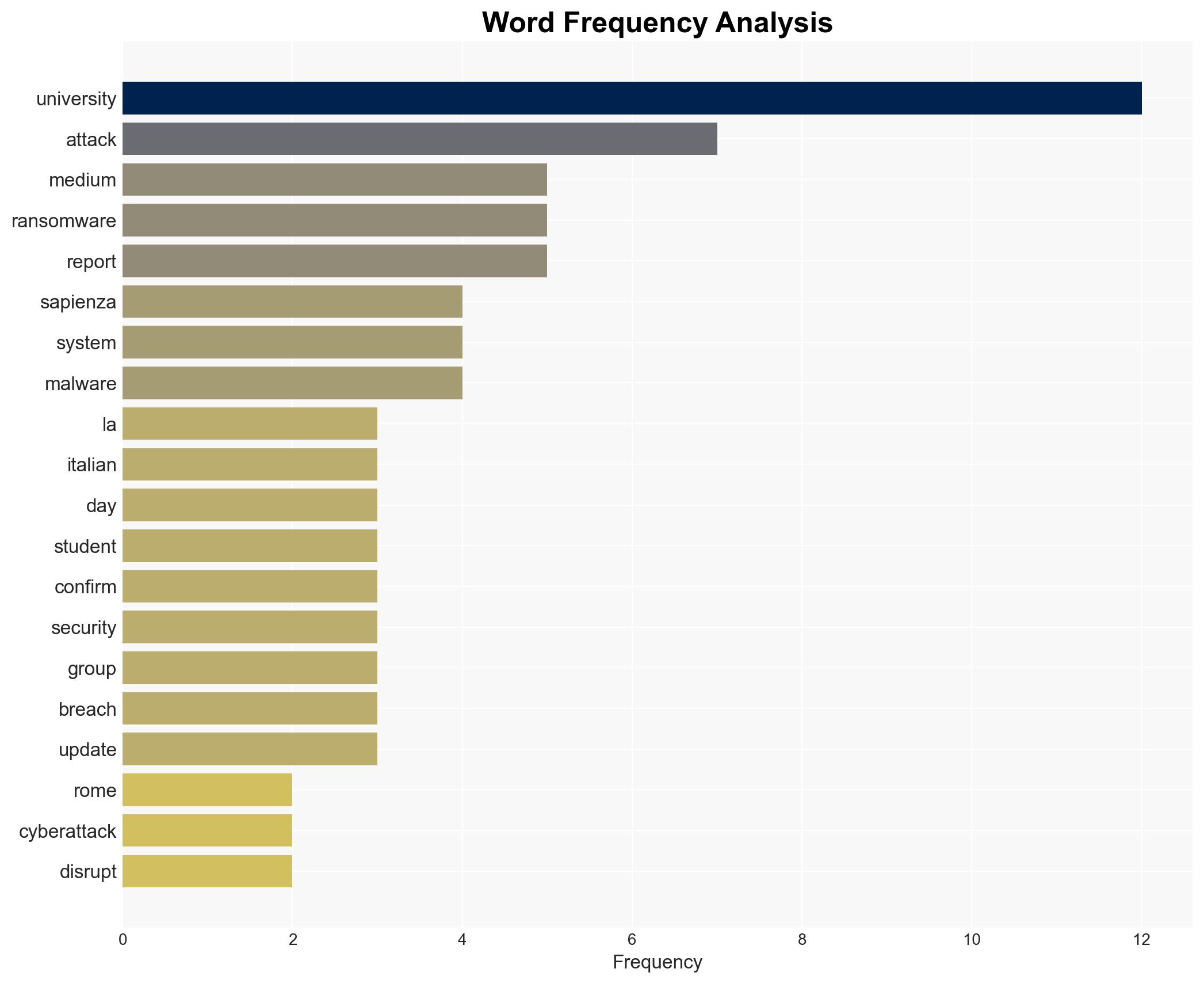
La Sapienza University in Rome remains offline following a cyberattack attributed to the Bablock ransomware, potentially linked to a pro-Russian group. This incident has disrupted university operations, affecting students and faculty. The most likely hypothesis is that this attack was a deliberate action by a new Russian cybercrime group, Femwar02. Overall confidence in this assessment is moderate due to the limited public information and ongoing investigation.
2. Competing Hypotheses
- Hypothesis A: The cyberattack on La Sapienza was conducted by the Russian cybercrime group Femwar02 using Bablock ransomware. This is supported by media reports and the malware’s characteristics, which avoid encrypting devices set to Russian languages. However, the group’s motives and identity remain uncertain.
- Hypothesis B: The attack was carried out by an unrelated cybercriminal group using Bablock ransomware, exploiting the geopolitical tensions to mislead attribution. This hypothesis is less supported due to the lack of evidence contradicting the pro-Russian link.
- Assessment: Hypothesis A is currently better supported due to consistent media reports and malware behavior patterns. Key indicators that could shift this judgment include new forensic evidence or credible claims of responsibility from other groups.
3. Key Assumptions and Red Flags
- Assumptions: The attack was financially motivated; Femwar02 is a new entity with limited operational history; Bablock ransomware is primarily used by Russian-affiliated groups.
- Information Gaps: Detailed forensic analysis of the attack; clear attribution evidence; motives of the attackers.
- Bias & Deception Risks: Potential bias in media reporting due to geopolitical tensions; risk of misattribution due to common malware use; deception by attackers to obscure true origins.
4. Implications and Strategic Risks
This cyberattack could signal a new wave of ransomware targeting educational institutions, potentially escalating tensions between European states and Russia. The incident may also encourage similar attacks by other groups.
- Political / Geopolitical: Potential strain on Italy-Russia relations; increased scrutiny of Russian cyber activities.
- Security / Counter-Terrorism: Heightened alert for educational institutions; possible increase in cyber defense measures.
- Cyber / Information Space: Increased focus on ransomware threats; potential for misinformation or propaganda exploitation.
- Economic / Social: Disruption to academic schedules; potential financial impact on the university and students.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of cyber threats targeting educational institutions; collaborate with cybersecurity agencies for threat intelligence sharing.
- Medium-Term Posture (1–12 months): Develop resilience measures, including improved cybersecurity protocols and incident response plans; foster partnerships with international cybersecurity bodies.
- Scenario Outlook:
- Best Case: Attackers are identified and apprehended, leading to improved security measures.
- Worst Case: Continued attacks on educational institutions, escalating geopolitical tensions.
- Most-Likely: Ongoing investigations lead to partial attribution, with incremental security improvements.
6. Key Individuals and Entities
- Femwar02 (Russian cybercrime group)
- La Sapienza University (target)
- Italian National Cybersecurity Agency (ACN)
- Bablock ransomware (malware used)
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, ransomware, higher education, Russia, geopolitical tensions, cybercrime, information security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us