Lab Engineers Simulate Attacks on Security Chips to Identify Vulnerabilities and Prepare for Quantum Threats
Published on: 2026-01-18
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: I oversee a lab where engineers try to destroy my lifes work Its the only way to prepare for quantum threats
1. BLUF (Bottom Line Up Front)
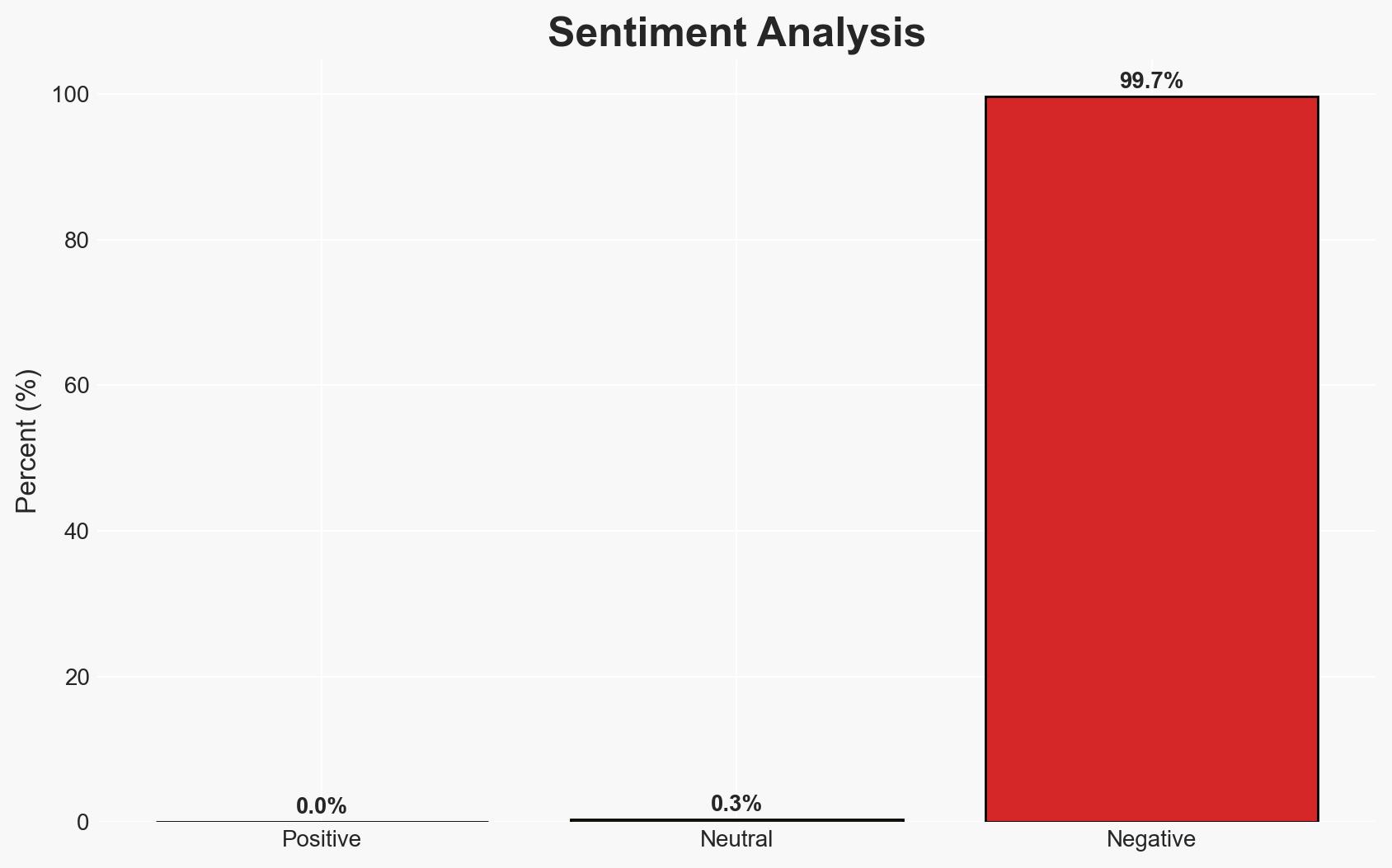
The practice of intentionally attacking secure chips to identify vulnerabilities is crucial for maintaining security in an evolving threat landscape, particularly with the advent of quantum computing. This proactive approach is most likely to enhance resilience against future cyber threats, affecting industries reliant on secure chips. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: The deliberate destruction of secure chips is essential for identifying vulnerabilities and strengthening security measures. This is supported by the historical success of such practices in improving security protocols. However, there is uncertainty about the effectiveness of these measures against future quantum threats.
- Hypothesis B: The focus on attacking secure chips may be insufficient, as it could lead to complacency or over-reliance on current methodologies, potentially overlooking novel attack vectors introduced by quantum computing. Evidence supporting this includes the rapid evolution of technology and the potential for unknown vulnerabilities.
- Assessment: Hypothesis A is currently better supported due to the established track record of vulnerability testing in enhancing security. Key indicators that could shift this judgment include breakthroughs in quantum computing that render current security measures obsolete.
3. Key Assumptions and Red Flags
- Assumptions: The current methods of testing secure chips are effective against emerging threats; quantum computing will significantly impact cryptographic security; secure chips remain a foundational element of digital security.
- Information Gaps: Specific details on the capabilities of quantum computing in breaking current encryption standards; the timeline for widespread quantum computing adoption.
- Bias & Deception Risks: Potential overconfidence in existing security testing methods; source bias from industry insiders with vested interests in current security paradigms.
4. Implications and Strategic Risks
The ongoing evolution of secure chip testing is likely to influence global security standards and practices, particularly in the context of quantum computing advancements.
- Political / Geopolitical: Nations may escalate efforts to develop quantum-resistant technologies, potentially leading to new alliances or rivalries.
- Security / Counter-Terrorism: Enhanced chip security could reduce vulnerabilities exploited by cyber-terrorists, but new threats may emerge with quantum advancements.
- Cyber / Information Space: The focus on chip security may drive innovations in cybersecurity, but also necessitate updates to existing infrastructure.
- Economic / Social: Industries reliant on secure chips may face increased costs for upgrading systems, impacting economic stability and consumer trust.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Increase monitoring of quantum computing developments; engage with industry experts to assess current security measures.
- Medium-Term Posture (1–12 months): Develop partnerships with academic and industry leaders to advance quantum-resistant technologies; invest in research for next-generation security protocols.
- Scenario Outlook:
- Best: Development of effective quantum-resistant security measures, maintaining global digital security.
- Worst: Quantum breakthroughs outpace security advancements, leading to widespread vulnerabilities.
- Most-Likely: Gradual improvements in security measures with intermittent challenges from emerging technologies.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, quantum computing, secure chips, vulnerability testing, cryptographic security, digital infrastructure, technology evolution
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us