Lazarus Group Introduces Enhanced BeaverTail Malware Variant Targeting Developers and Crypto Traders
Published on: 2025-12-18
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Lazarus Group Embed New BeaverTail Variant in Developer Tools
1. BLUF (Bottom Line Up Front)
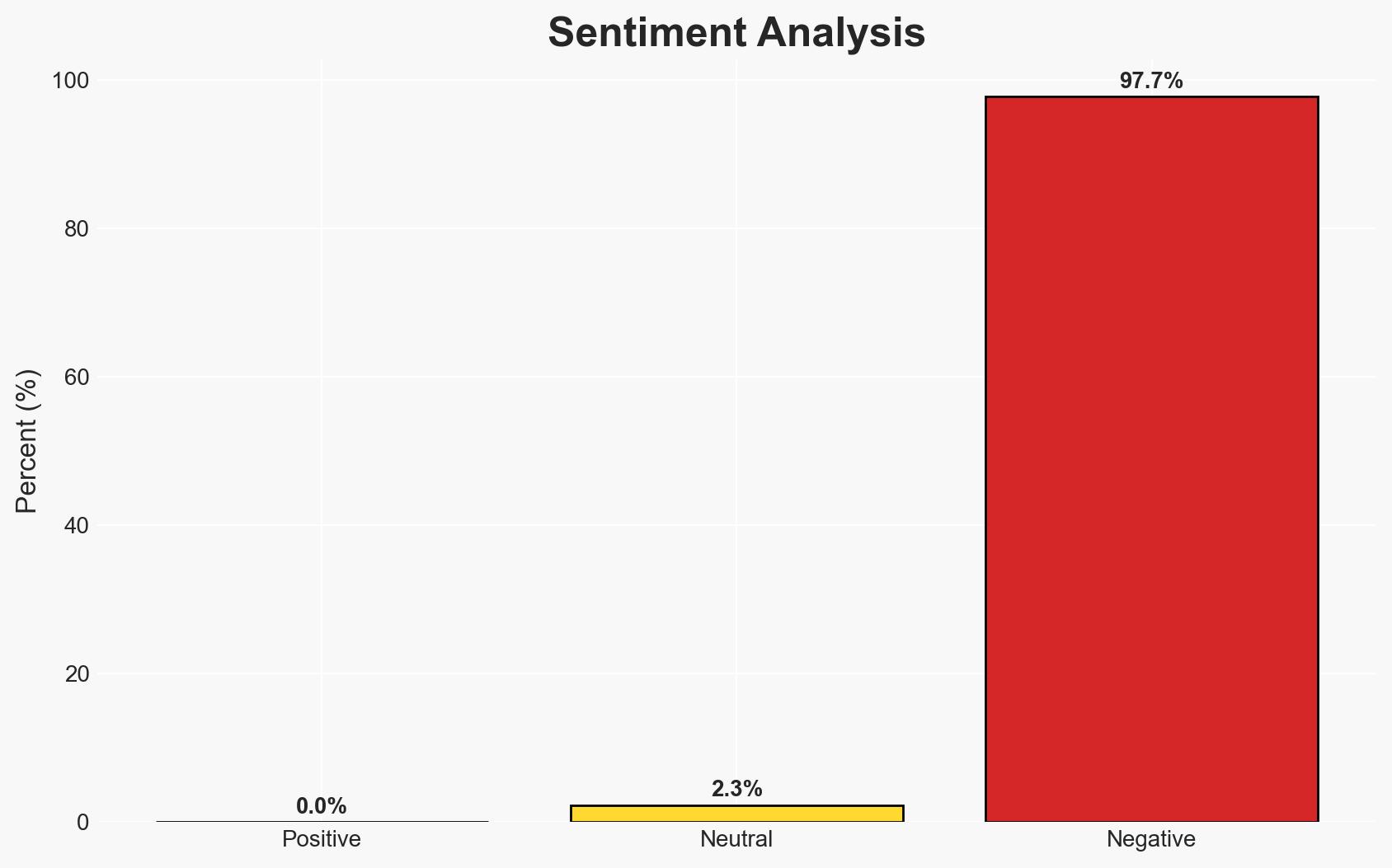
The Lazarus Group has developed a new variant of the BeaverTail malware, significantly enhancing its capabilities and concealment techniques, posing a heightened threat to the financial and cryptocurrency sectors. The malware’s integration into developer tools and its use of blockchain for command storage indicate advanced tradecraft. This development is assessed with moderate confidence due to the complexity and sophistication of the malware.
2. Competing Hypotheses
- Hypothesis A: The Lazarus Group is primarily targeting financial and cryptocurrency sectors to fund North Korean state activities. This is supported by the malware’s focus on stealing financial data and its sophisticated concealment methods. However, the exact scale and success rate of these operations remain uncertain.
- Hypothesis B: The primary goal is to disrupt and destabilize international financial systems rather than direct financial gain. This hypothesis is less supported due to the malware’s specific targeting of financial credentials and cryptocurrency keys, which suggests a financial motive.
- Assessment: Hypothesis A is currently better supported given the direct financial targeting and the historical context of North Korean cyber operations aimed at generating revenue. Indicators such as shifts in target sectors or changes in malware capabilities could alter this assessment.
3. Key Assumptions and Red Flags
- Assumptions: The Lazarus Group has the technical capability to maintain and evolve complex malware; financial gain is a primary motivator; blockchain technology will continue to be used for concealment.
- Information Gaps: Detailed success metrics of the malware’s deployment; comprehensive understanding of the malware’s full capabilities and potential targets.
- Bias & Deception Risks: Potential bias in attributing all activities to the Lazarus Group without considering other actors; risk of overestimating the malware’s capabilities based on limited samples.
4. Implications and Strategic Risks
This development could lead to increased cyber threats to financial institutions and a potential rise in geopolitical tensions involving North Korea. The malware’s sophistication may inspire similar tactics by other state and non-state actors.
- Political / Geopolitical: Potential for increased sanctions or diplomatic actions against North Korea.
- Security / Counter-Terrorism: Heightened alert levels in financial sectors; increased demand for cybersecurity measures.
- Cyber / Information Space: Potential proliferation of advanced malware techniques; increased difficulty in detecting and mitigating threats.
- Economic / Social: Possible financial instability if major breaches occur; erosion of trust in digital financial transactions.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of developer tool platforms; conduct awareness campaigns about fake job offers; strengthen authentication processes for financial transactions.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms for intelligence sharing; invest in advanced threat detection technologies; promote cross-sector collaboration on cybersecurity standards.
- Scenario Outlook:
- Best: Effective countermeasures reduce the malware’s impact, leading to decreased threat levels.
- Worst: Major financial institutions suffer significant breaches, leading to economic disruption.
- Most-Likely: Continued attempts by the Lazarus Group with moderate success, prompting ongoing cybersecurity enhancements.
6. Key Individuals and Entities
- Darktrace (Cybersecurity firm)
- Lazarus Group (North Korean cyber threat actor)
- Famous Chollima, Gwisin Gang, Tenacious Pungsan (Sub-groups linked to Lazarus Group)
- Jason Soroko (Senior Fellow, Darktrace)
7. Thematic Tags
cybersecurity, North Korea, financial sector, malware, Lazarus Group, cryptocurrency, blockchain
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us