Leaked Oracle EBS exploit scripts expected to drive new wave of attacks CVE-2025-61882 – Help Net Security
Published on: 2025-10-07
Intelligence Report: Leaked Oracle EBS exploit scripts expected to drive new wave of attacks CVE-2025-61882 – Help Net Security
1. BLUF (Bottom Line Up Front)
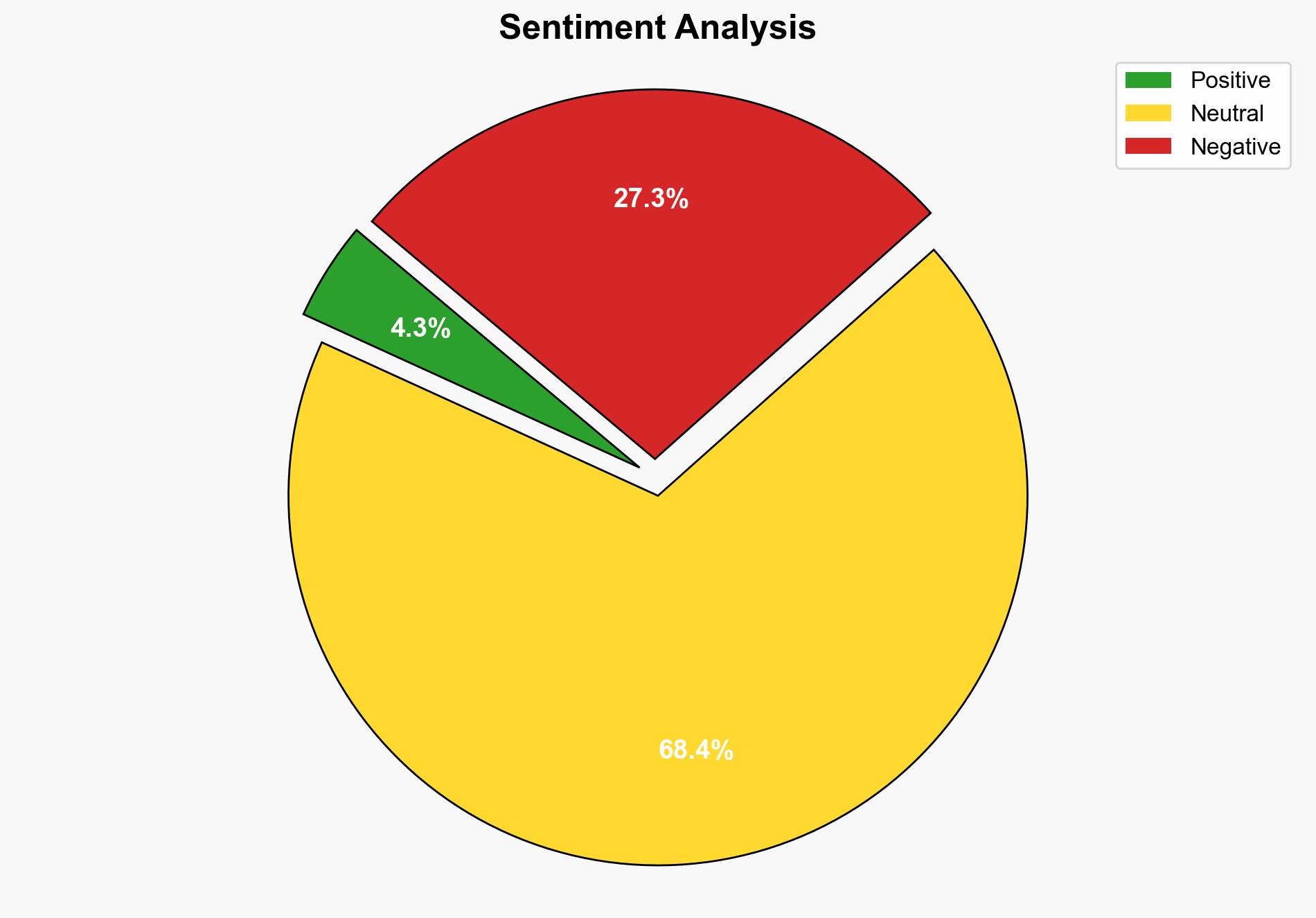
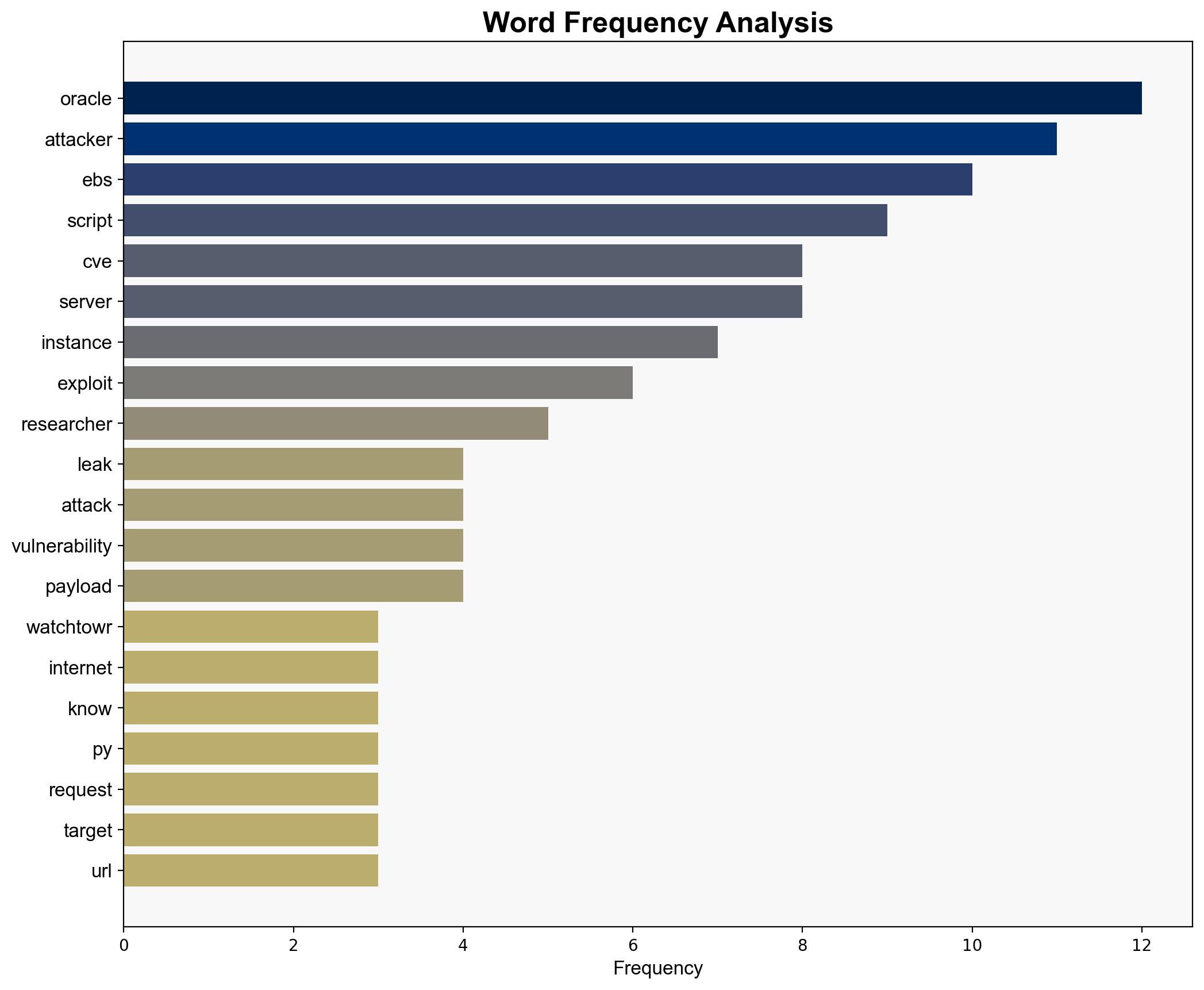
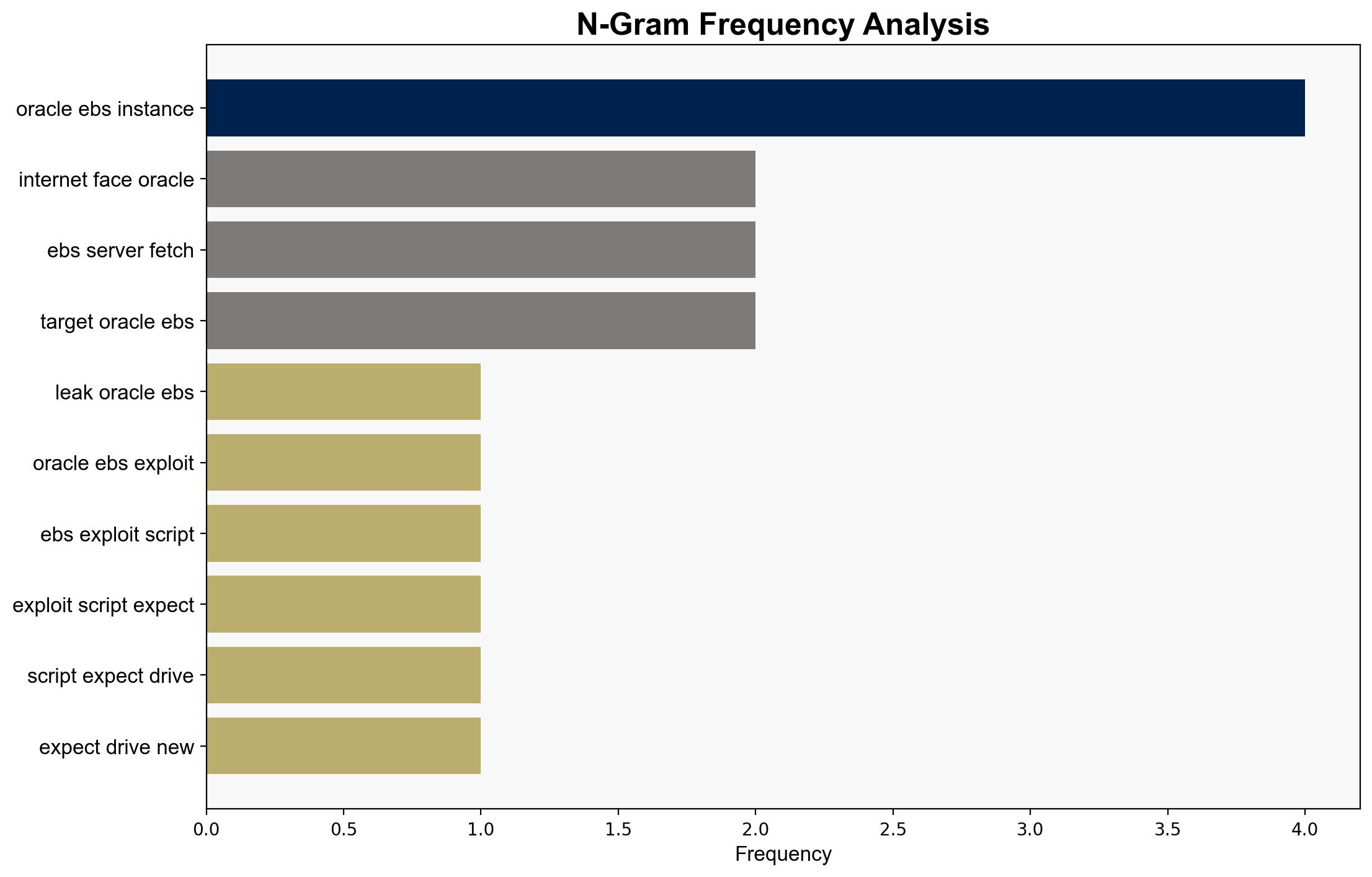
The most supported hypothesis is that the leaked Oracle EBS exploit scripts will lead to an increase in targeted cyberattacks on organizations with vulnerable Oracle EBS instances. This is based on the observed capabilities of the exploit and the historical use of similar vulnerabilities by threat actors. Confidence Level: High. Recommended action includes immediate patching of Oracle EBS systems and enhanced monitoring for indicators of compromise.
2. Competing Hypotheses
Hypothesis 1: The leaked exploit scripts will result in a significant increase in cyberattacks targeting Oracle EBS systems, primarily by known threat actors such as CLP and Lapsus$.
Hypothesis 2: The impact of the leaked exploit scripts will be minimal due to rapid patching by organizations and the complexity of executing the exploit, limiting its use to highly skilled threat actors.
3. Key Assumptions and Red Flags
Assumptions:
– Organizations with Oracle EBS instances are aware of the vulnerability and have the capability to patch promptly.
– Threat actors have the necessary skills and resources to exploit the vulnerability effectively.
Red Flags:
– Lack of detailed information on the unknown threat actor involved in the script leak.
– Potential underestimation of the exploit’s complexity and the speed of organizational response.
4. Implications and Strategic Risks
The exploitation of Oracle EBS systems could lead to data breaches, financial losses, and reputational damage for affected organizations. There is a risk of cascading effects if attackers leverage compromised systems to infiltrate other networks or systems. The geopolitical dimension includes potential state-sponsored exploitation, increasing tensions in cybersecurity domains.
5. Recommendations and Outlook
- Organizations should prioritize patching Oracle EBS systems and conduct thorough security audits to identify vulnerabilities.
- Implement enhanced monitoring and incident response protocols to detect and mitigate potential breaches.
- Scenario Projections:
- Best Case: Rapid patching and effective monitoring prevent significant exploitation.
- Worst Case: Widespread exploitation leads to major data breaches and financial losses.
- Most Likely: A moderate increase in targeted attacks, with some organizations experiencing breaches before patching.
6. Key Individuals and Entities
– Sina Kheirkhah
– Jake Knot
– CLP
– Lapsus$
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus