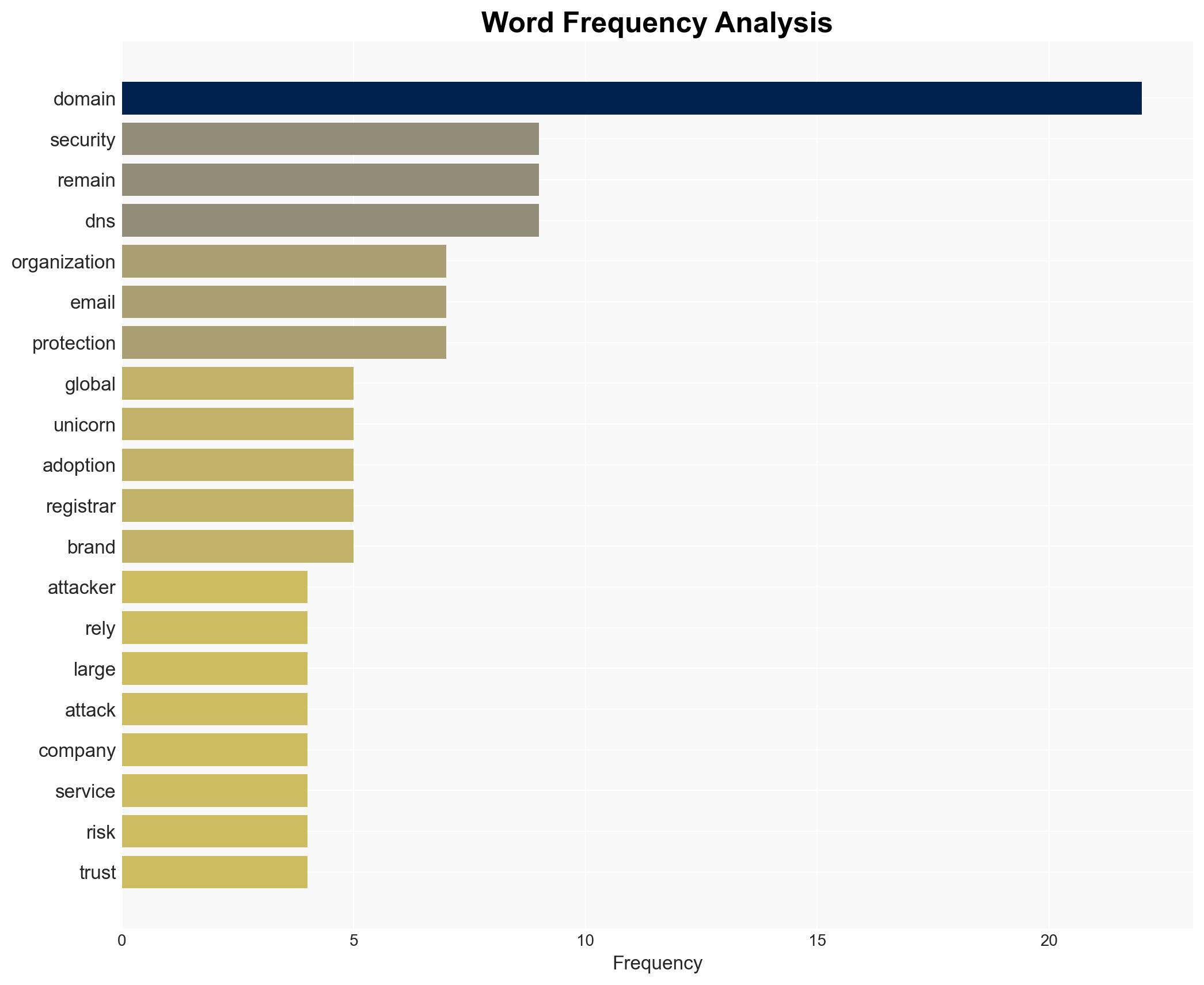
Legacy domain security remains a critical vulnerability for enterprises amid rising cyber threats.
Published on: 2026-01-22
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: The internet’s oldest trust mechanism is still one of its weakest links
1. BLUF (Bottom Line Up Front)
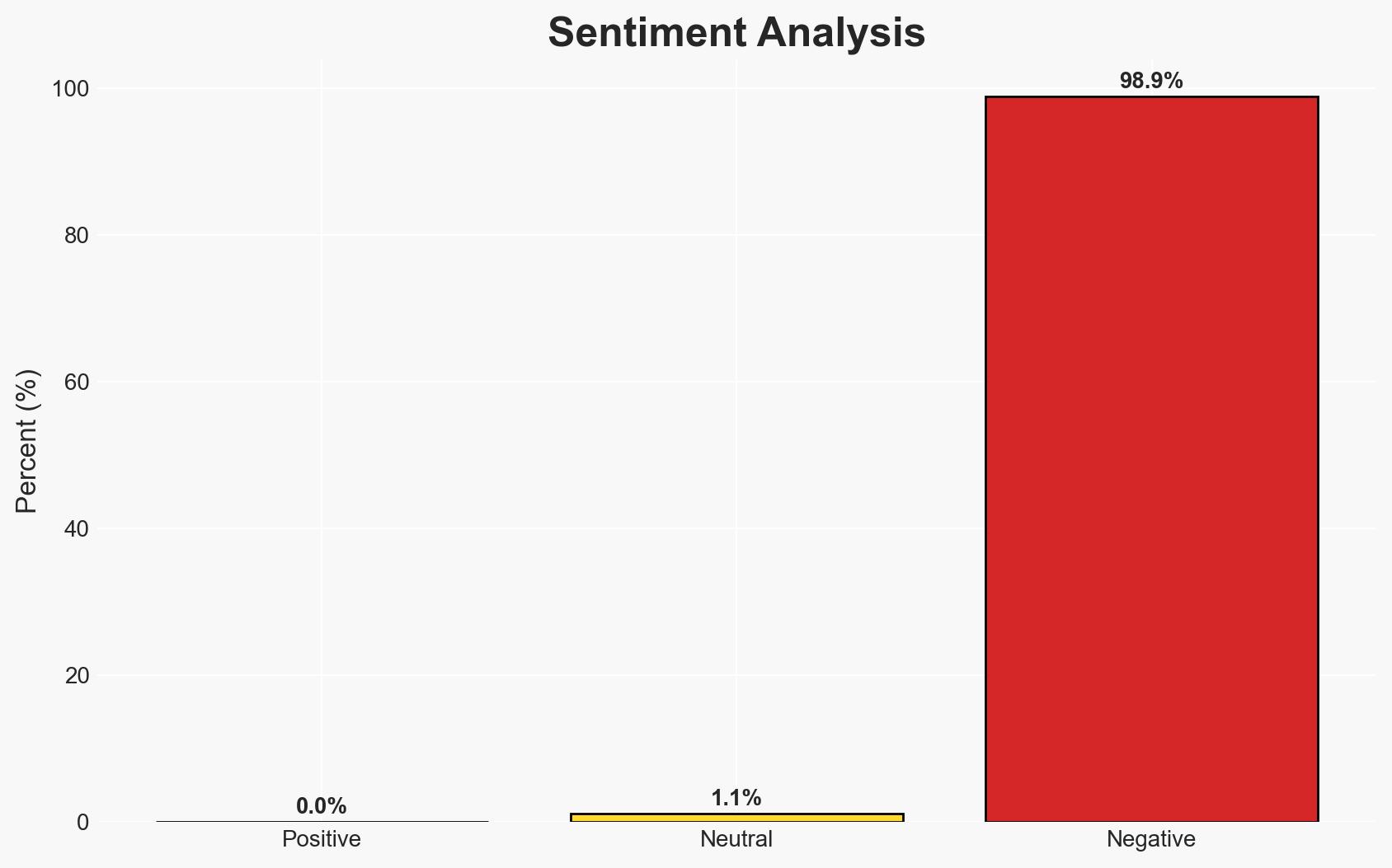
Domain names remain a critical vulnerability in enterprise cybersecurity, with large organizations inadequately protecting this attack vector. The reliance on single DNS providers and insufficient domain security measures increase exposure to cyber threats. This issue affects global enterprises, particularly those in critical infrastructure sectors. Overall confidence in this assessment is moderate due to incomplete data on specific organizational practices.
2. Competing Hypotheses
- Hypothesis A: Organizations are aware of domain vulnerabilities but prioritize other cybersecurity measures due to resource constraints. Evidence includes uneven adoption of domain security measures and cost pressures driving DNS consolidation. Key uncertainties include the extent of awareness and prioritization within organizations.
- Hypothesis B: Organizations underestimate the risk posed by domain vulnerabilities, leading to inadequate protection measures. Supporting evidence includes the persistent use of consumer-oriented registrars and low adoption of advanced domain protections. Contradictory evidence is the improvement in email authentication driven by regulatory pressure.
- Assessment: Hypothesis B is currently better supported as the primary issue appears to be underestimation of risk rather than resource allocation. Indicators that could shift this judgment include new regulatory frameworks or significant breaches that raise awareness.
3. Key Assumptions and Red Flags
- Assumptions: Organizations have the capability to enhance domain security if prioritized; regulatory pressures will continue to drive improvements in cybersecurity.
- Information Gaps: Specific data on organizational decision-making processes regarding cybersecurity priorities; detailed statistics on domain-related breaches.
- Bias & Deception Risks: Potential bias in reporting from cybersecurity firms emphasizing threats to promote services; lack of transparency from organizations about security practices.
4. Implications and Strategic Risks
The persistence of domain vulnerabilities could lead to increased cyber incidents, affecting global economic stability and trust in digital infrastructure.
- Political / Geopolitical: Potential for increased regulatory intervention and international collaboration on cybersecurity standards.
- Security / Counter-Terrorism: Enhanced threat landscape with potential for exploitation by state and non-state actors.
- Cyber / Information Space: Increased risk of phishing, impersonation, and malware attacks leveraging domain vulnerabilities.
- Economic / Social: Potential economic disruptions from cyber incidents affecting critical infrastructure sectors.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a comprehensive audit of domain security practices; enhance monitoring of domain-related threats.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms for advanced domain protection; invest in dual DNS infrastructure.
- Scenario Outlook:
- Best: Rapid improvement in domain security practices driven by regulatory incentives.
- Worst: Major cyber incident exploiting domain vulnerabilities leads to significant economic and reputational damage.
- Most-Likely: Gradual improvements in domain security with periodic incidents highlighting vulnerabilities.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, domain security, phishing, critical infrastructure, DNS vulnerabilities, regulatory compliance, cyber risk management
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us