Legislation Aims to Enhance Cybersecurity for U.S. Utilities and Pipeline Infrastructure
Published on: 2026-01-30
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Tech Bills of the Week Measures seek to boost cyber posture of utilities
1. BLUF (Bottom Line Up Front)
The proposed legislative measures aim to enhance the cybersecurity and physical security of U.S. energy infrastructure, particularly targeting pipelines, liquefied natural gas facilities, and smaller electric utilities. These initiatives are likely to improve resilience against cyber threats, but their effectiveness will depend on implementation and coordination across federal, state, and industry levels. The overall confidence in this assessment is moderate due to uncertainties in execution and potential resistance from stakeholders.
2. Competing Hypotheses
- Hypothesis A: The legislative measures will significantly enhance the cybersecurity posture of U.S. energy infrastructure by improving coordination and resource allocation. This is supported by the structured approach to funding, information sharing, and training. However, uncertainties include the adequacy of funding and the speed of implementation.
- Hypothesis B: The measures will have limited impact due to potential bureaucratic delays, insufficient funding, and lack of industry engagement. While the bills propose comprehensive frameworks, the complexity of coordination across multiple levels may hinder timely and effective action.
- Assessment: Hypothesis A is currently better supported due to the structured legislative approach and targeted funding. Key indicators that could shift this judgment include delays in program initiation, lack of industry participation, or insufficient funding allocation.
3. Key Assumptions and Red Flags
- Assumptions: The proposed funding levels are sufficient to achieve the desired cybersecurity enhancements; industry stakeholders will actively participate in the initiatives; federal and state coordination will be effective.
- Information Gaps: Specific details on implementation timelines, metrics for success, and the extent of industry engagement are not provided.
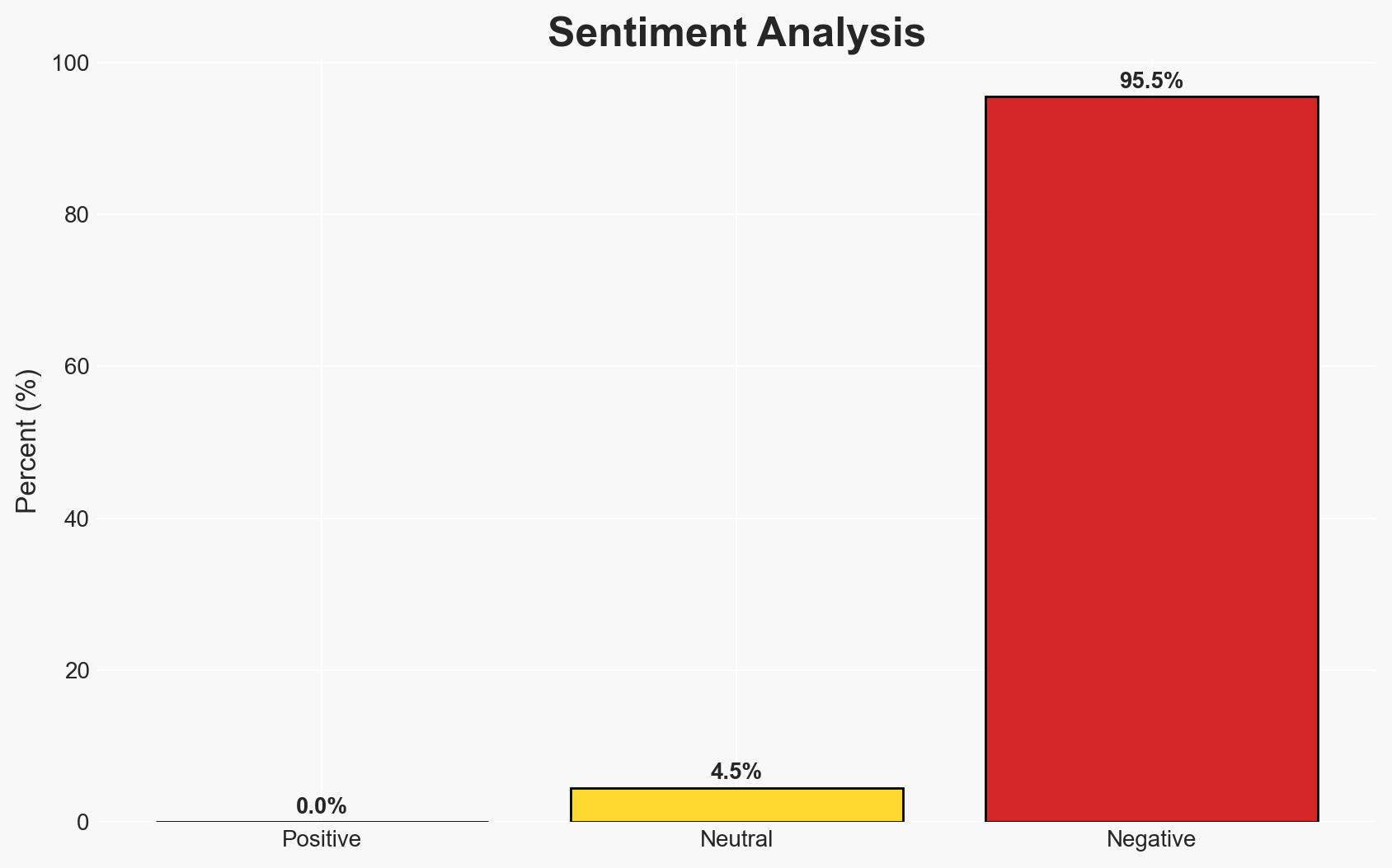
- Bias & Deception Risks: There is a risk of optimism bias in assessing the potential effectiveness of the measures. Additionally, industry stakeholders may underreport vulnerabilities to avoid regulatory scrutiny.
4. Implications and Strategic Risks
The development of these legislative measures could lead to a more robust cybersecurity framework for U.S. energy infrastructure, but challenges in execution could limit their effectiveness.
- Political / Geopolitical: Enhanced cybersecurity could reduce vulnerabilities to foreign cyber threats, potentially altering geopolitical dynamics by reducing leverage from adversaries.
- Security / Counter-Terrorism: Improved resilience of critical infrastructure may lower the risk of successful cyberattacks by terrorist groups.
- Cyber / Information Space: Increased information sharing and improved cybersecurity tools could enhance threat detection and response capabilities.
- Economic / Social: Strengthened infrastructure security could prevent economic disruptions and maintain public confidence in energy reliability.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Monitor legislative progress and stakeholder engagement; assess readiness of agencies to implement proposed measures.
- Medium-Term Posture (1–12 months): Develop partnerships with industry stakeholders; enhance training programs and information-sharing mechanisms.
- Scenario Outlook: Best: Full implementation leads to significant cybersecurity improvements. Worst: Delays and insufficient funding result in minimal impact. Most-Likely: Incremental improvements with ongoing challenges in coordination and resource allocation.
6. Key Individuals and Entities
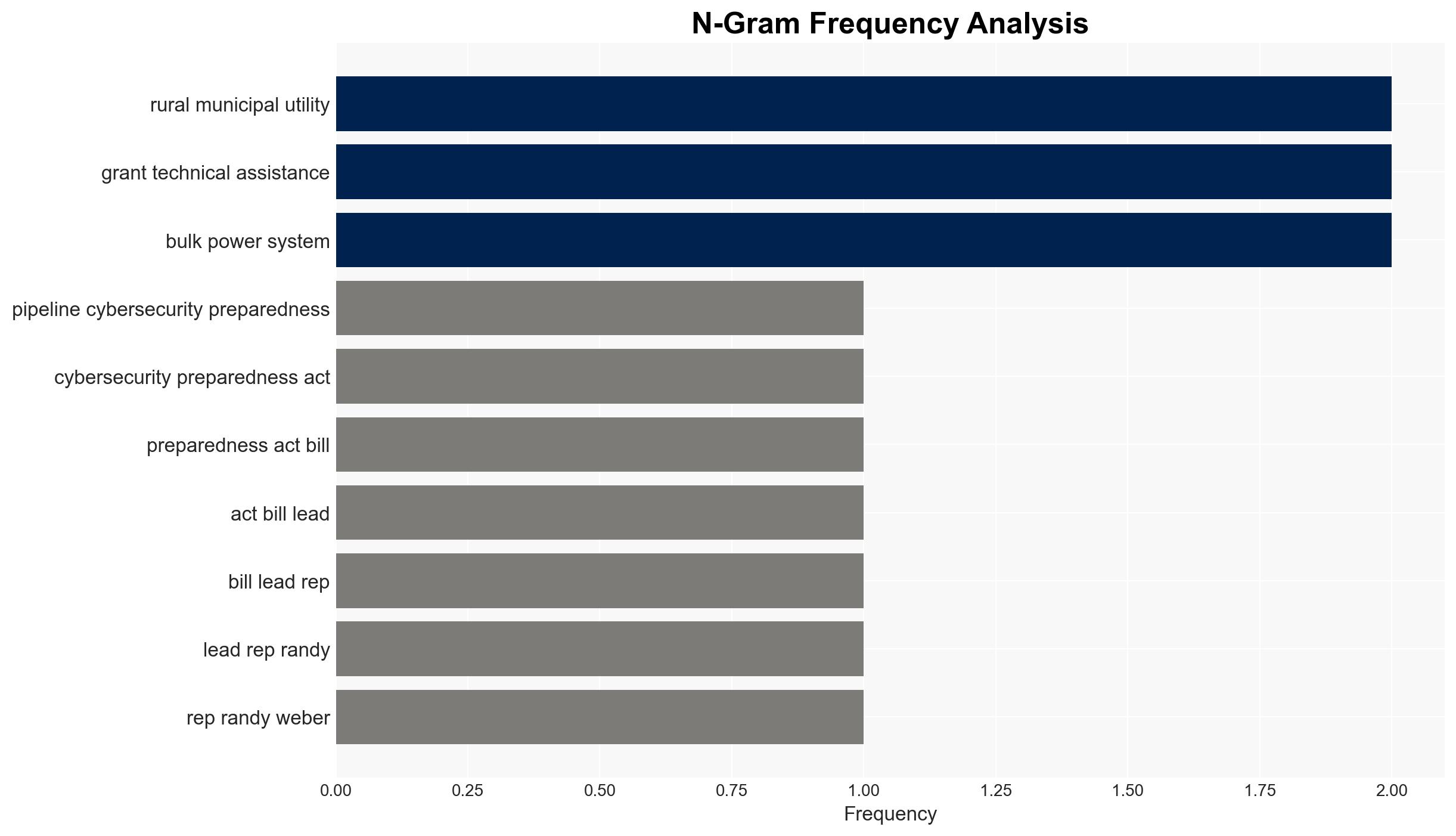
- Rep. Randy Weber, R-Texas
- Rep. Mariannette Miller-Meeks, R-Iowa
- Rep. Bob Latta, R-Ohio
- U.S. Department of Energy
- Rural electric cooperatives and municipal utilities
7. Thematic Tags
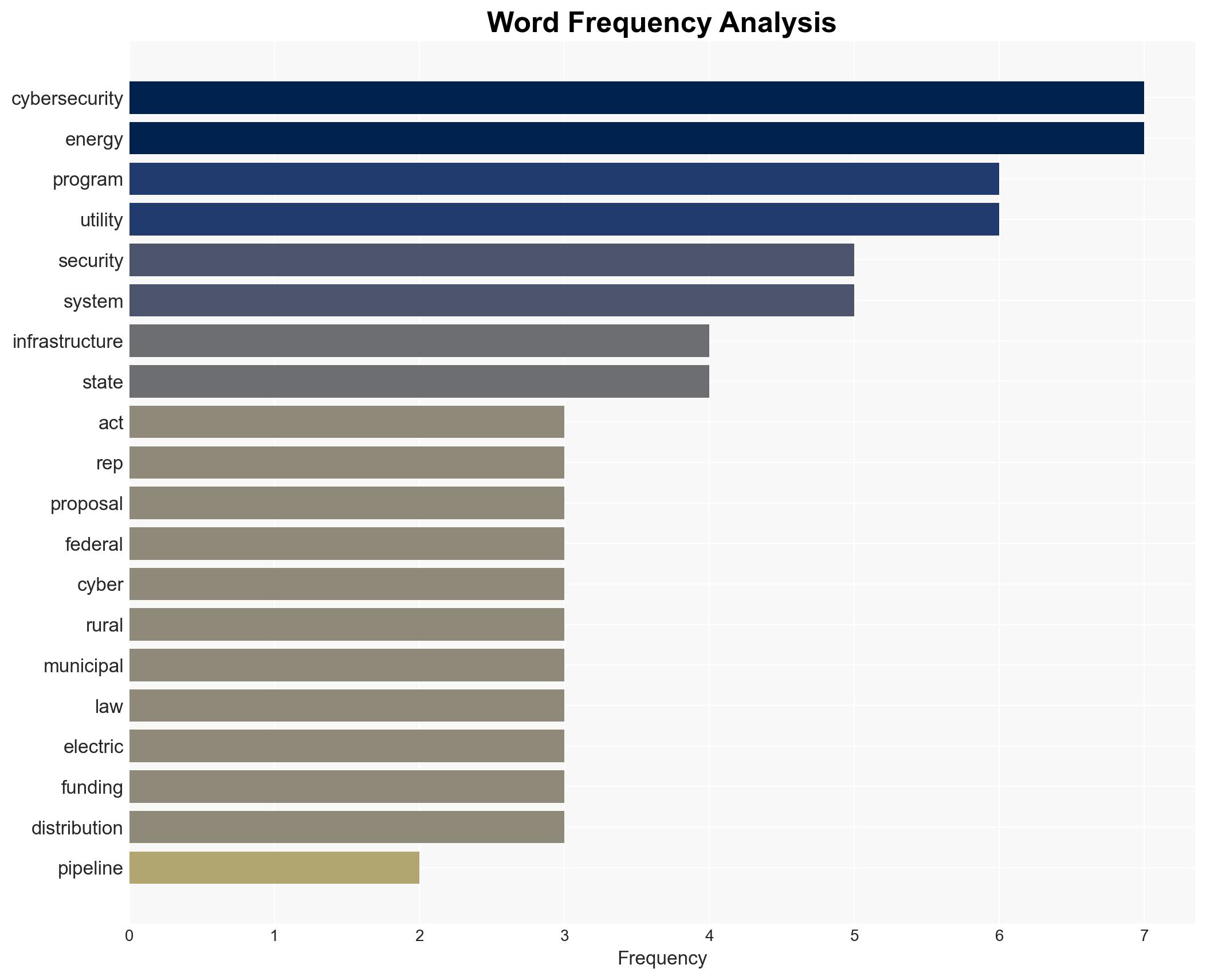
cybersecurity, energy infrastructure, legislative measures, information sharing, critical infrastructure protection, federal-state coordination, energy resilience
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us