London boroughs gradually restoring services after prolonged cyberattack disruptions
Published on: 2026-01-23
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: London boroughs limping back online months after cyberattack
1. BLUF (Bottom Line Up Front)
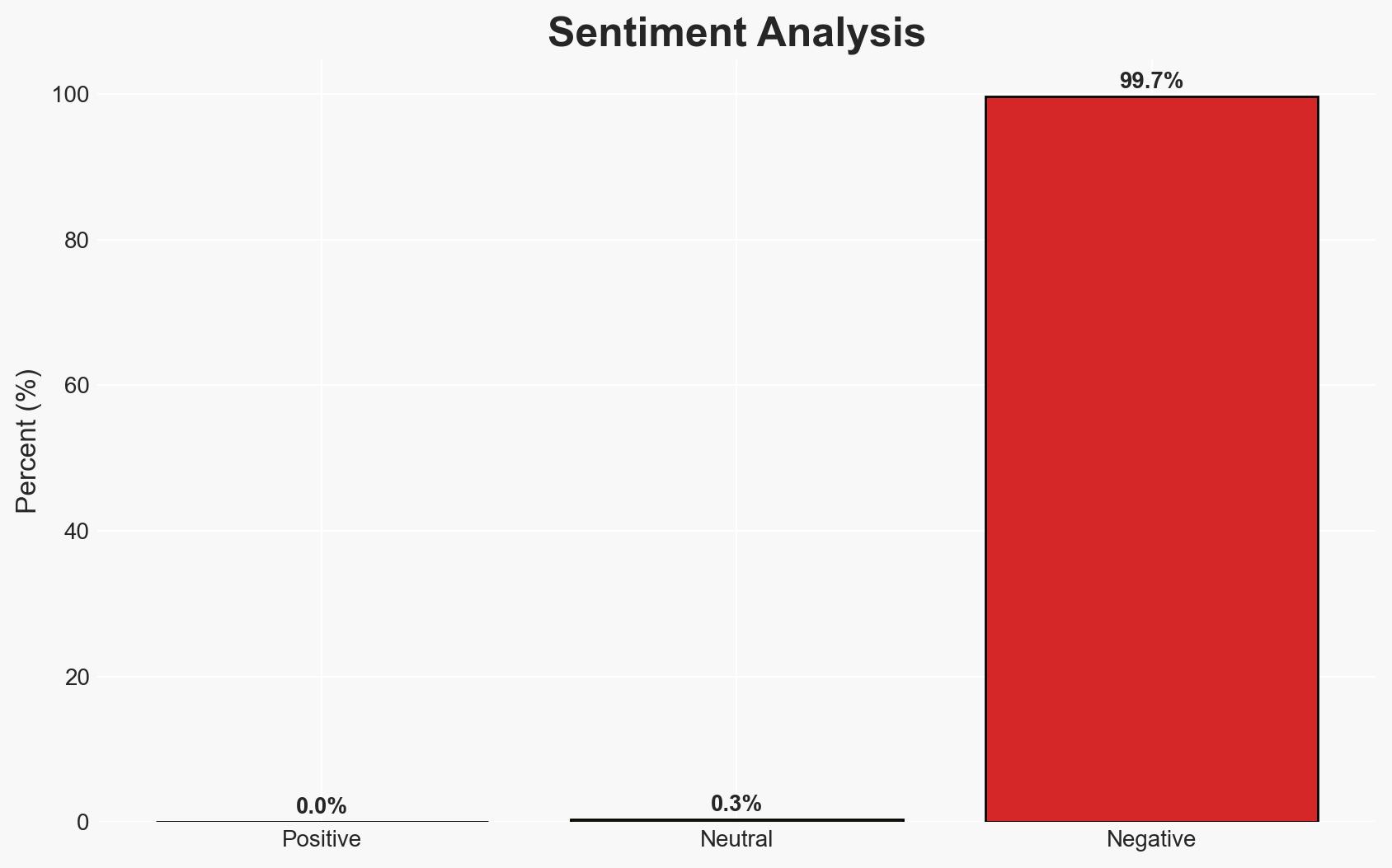
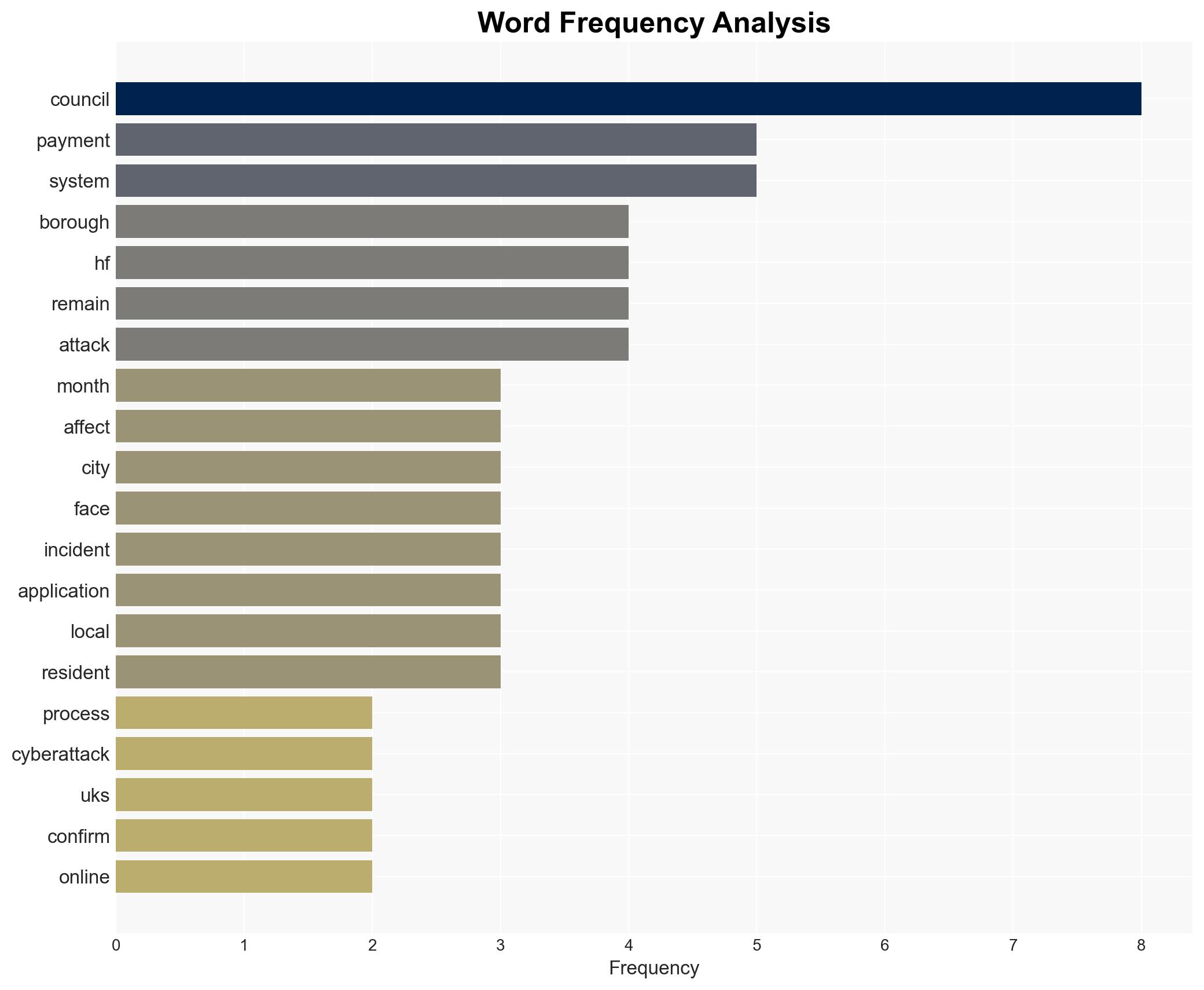
The cyberattack on multiple London boroughs, including Hammersmith & Fulham, Westminster City, and Kensington & Chelsea, has led to significant disruptions in public services. The attack appears to have criminal intent, with data compromise confirmed in at least one borough. The recovery is ongoing, with some services still offline. Given the complexity and scope of the attack, there is moderate confidence that the threat actors may have broader objectives, potentially linked to geopolitical tensions.
2. Competing Hypotheses
- Hypothesis A: The cyberattack was primarily financially motivated, targeting council systems to disrupt operations and extract ransom. Supporting evidence includes the criminal intent and data compromise reported by Kensington & Chelsea. However, the lack of explicit ransom demands in the snippet raises uncertainties.
- Hypothesis B: The attack was politically motivated, potentially linked to pro-Russia hacktivist groups aiming to disrupt UK local government operations. The NCSC’s warning about such groups targeting local authorities supports this hypothesis, though direct attribution remains unconfirmed.
- Assessment: Hypothesis B is currently better supported due to the broader geopolitical context and the NCSC’s warning. Indicators such as further coordinated attacks or explicit claims of responsibility could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The attack was coordinated and not an isolated incident; the boroughs’ cybersecurity measures were initially insufficient; the recovery process will continue to face challenges.
- Information Gaps: Specific details on the attackers’ identity and objectives; the full extent of data compromised; the effectiveness of enhanced security measures.
- Bias & Deception Risks: Potential bias in attributing the attack to geopolitical actors without concrete evidence; deception risks from threat actors providing false claims or misleading information.
4. Implications and Strategic Risks
The cyberattack on London boroughs could set a precedent for future attacks on local government entities, potentially influencing broader cybersecurity policies and international relations.
- Political / Geopolitical: Escalation of tensions between the UK and state actors perceived to be behind the attack, potentially affecting diplomatic relations.
- Security / Counter-Terrorism: Increased vulnerability of local government systems to cyber threats, necessitating enhanced security protocols.
- Cyber / Information Space: Heightened awareness and potential increase in cyber defense investments; risk of misinformation campaigns exploiting the incident.
- Economic / Social: Disruption to public services could erode trust in local government, impacting social cohesion and economic stability.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a comprehensive forensic investigation; enhance monitoring of council systems; engage with NCSC for threat intelligence sharing.
- Medium-Term Posture (1–12 months): Develop resilience measures, including staff training and system upgrades; strengthen partnerships with cybersecurity agencies.
- Scenario Outlook:
- Best: Full recovery with no further incidents; improved cybersecurity posture.
- Worst: Additional attacks causing prolonged disruptions; significant data breaches.
- Most-Likely: Gradual recovery with intermittent challenges; increased cybersecurity awareness and measures.
6. Key Individuals and Entities
- Hammersmith & Fulham Council
- Westminster City Council
- Royal Borough of Kensington & Chelsea
- UK National Cyber Security Centre (NCSC)
- GCHQ
7. Thematic Tags
cybersecurity, local government, geopolitical tensions, cyberattack recovery, public service disruption, UK-Russia relations
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us