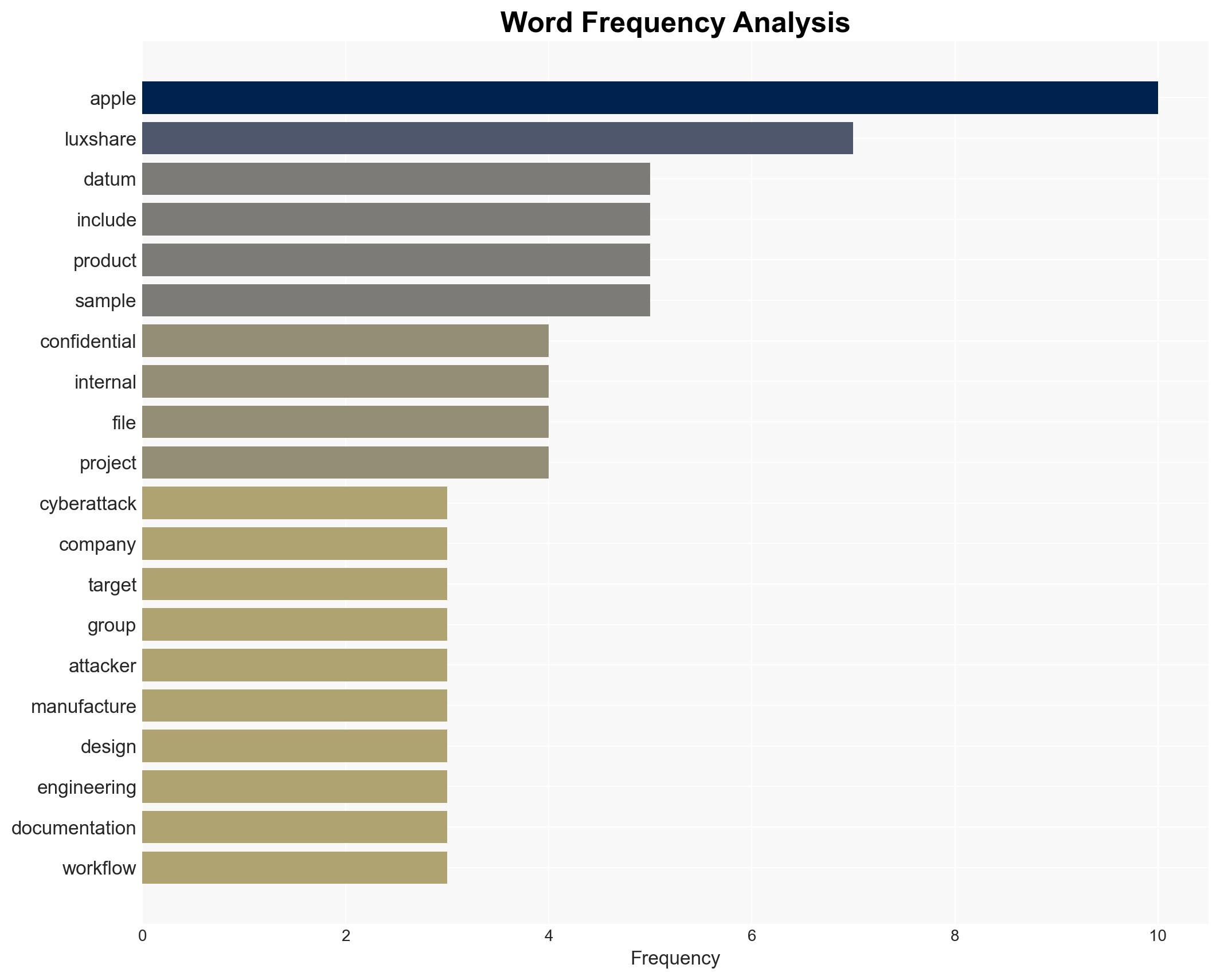
Luxshare Cyberattack Exposes Over 1TB of Confidential Apple Product Data
Published on: 2026-01-21
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Apple’s Secret Product Plans Stolen in Luxshare Cyberattack
1. BLUF (Bottom Line Up Front)
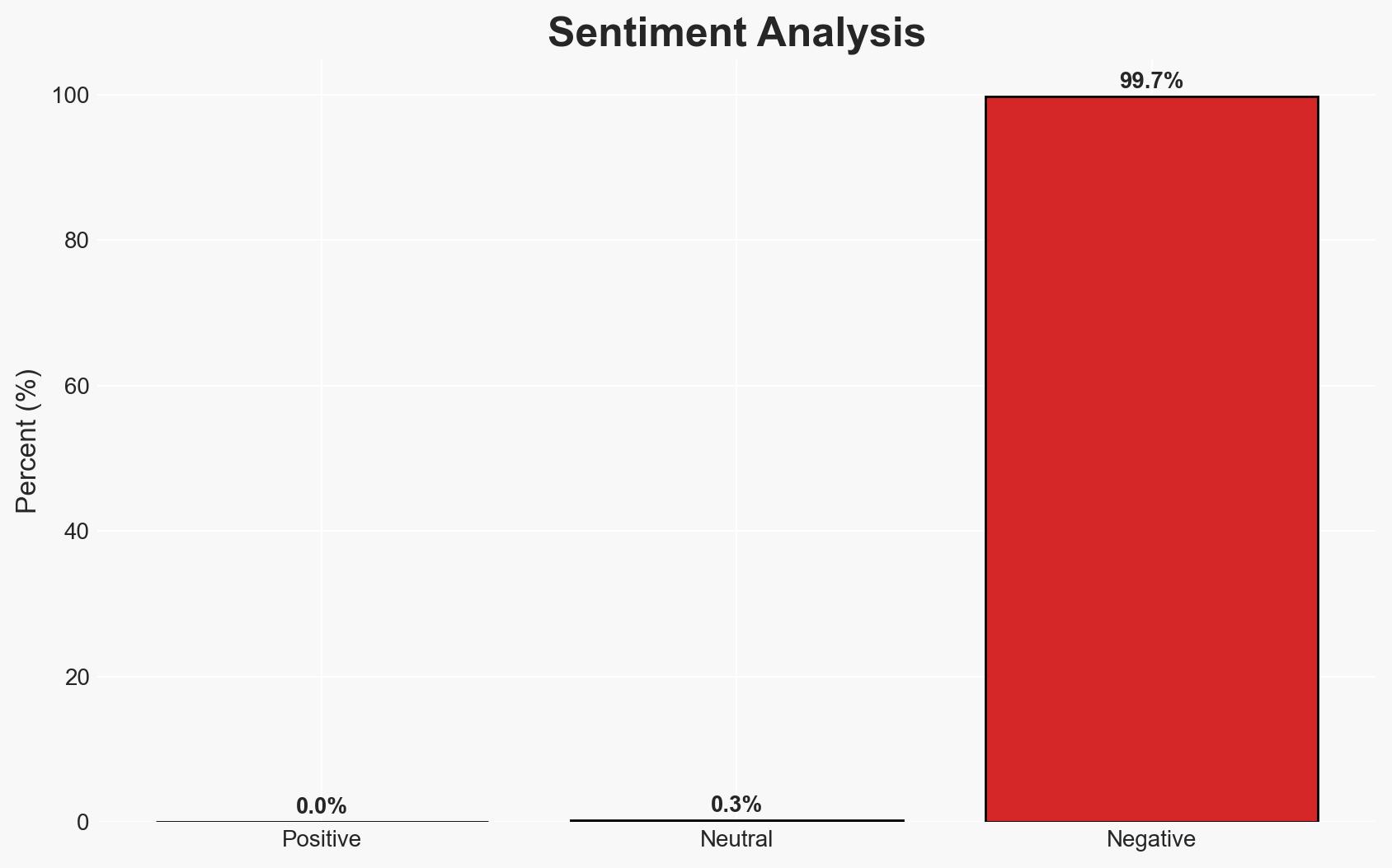
The cyberattack on Luxshare, a major Apple supplier, resulted in the theft of over 1TB of sensitive Apple data, potentially impacting multiple high-profile clients. The breach poses significant risks of intellectual property theft and operational disruption. Current analysis supports the hypothesis that the attack was financially motivated, with moderate confidence due to the attackers’ ransom demands and data leak threats.
2. Competing Hypotheses
- Hypothesis A: The attack was primarily financially motivated, aiming to extort Luxshare by threatening to release confidential data. This is supported by the ransom demands and the public posting of data samples as proof of compromise. However, the full extent of the attackers’ objectives remains unclear.
- Hypothesis B: The attack was state-sponsored, targeting strategic economic and technological information for geopolitical advantage. This is less supported due to the lack of direct evidence linking state actors and the overt ransom demands, which are atypical of state-sponsored operations.
- Assessment: Hypothesis A is currently better supported due to the attackers’ explicit ransom demands and the nature of the data exfiltrated. Indicators that could shift this judgment include evidence of state actor involvement or strategic use of the stolen data beyond financial extortion.
3. Key Assumptions and Red Flags
- Assumptions: The attackers have no undisclosed objectives beyond financial gain; Luxshare’s response strategy remains passive; the data samples released are representative of the entire breach.
- Information Gaps: The identity and motivations of the attackers, the full scope of the data compromised, and Luxshare’s internal response measures.
- Bias & Deception Risks: Potential bias in interpreting the attackers’ public statements as truthful; risk of deception in the data samples provided as proof of compromise.
4. Implications and Strategic Risks
The breach could lead to significant operational and reputational damage for Apple and its partners, with potential long-term impacts on supply chain security and intellectual property protection.
- Political / Geopolitical: Escalation of tensions in US-China tech relations; potential for increased scrutiny of Chinese supply chain vulnerabilities.
- Security / Counter-Terrorism: Heightened risk of similar attacks on other high-value targets; potential for increased cyber defense measures.
- Cyber / Information Space: Likelihood of increased cyber espionage activities; potential for misinformation campaigns leveraging leaked data.
- Economic / Social: Potential financial losses for affected companies; impact on consumer trust and market stability.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of dark web forums for further data leaks; initiate incident response protocols to mitigate potential data misuse.
- Medium-Term Posture (1–12 months): Strengthen cybersecurity partnerships and information-sharing networks; invest in advanced threat detection and response capabilities.
- Scenario Outlook:
- Best: Successful containment and mitigation of data misuse; minimal long-term impact.
- Worst: Widespread release of sensitive data leading to significant financial and reputational damage.
- Most-Likely: Partial data release with moderate operational disruptions and increased cybersecurity measures.
6. Key Individuals and Entities
- Luxshare
- Apple
- Nvidia
- LG
- Tesla
- Geely
- RansomHub (attack group)
7. Thematic Tags
cybersecurity, intellectual property, supply chain, ransomware, data breach, technology espionage, geopolitical tensions
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us