MadeYouReset An HTTP2 vulnerability thwarted by Rapid Reset mitigations – Cloudflare.com
Published on: 2025-08-14
Intelligence Report: MadeYouReset An HTTP2 vulnerability thwarted by Rapid Reset mitigations – Cloudflare.com
1. BLUF (Bottom Line Up Front)
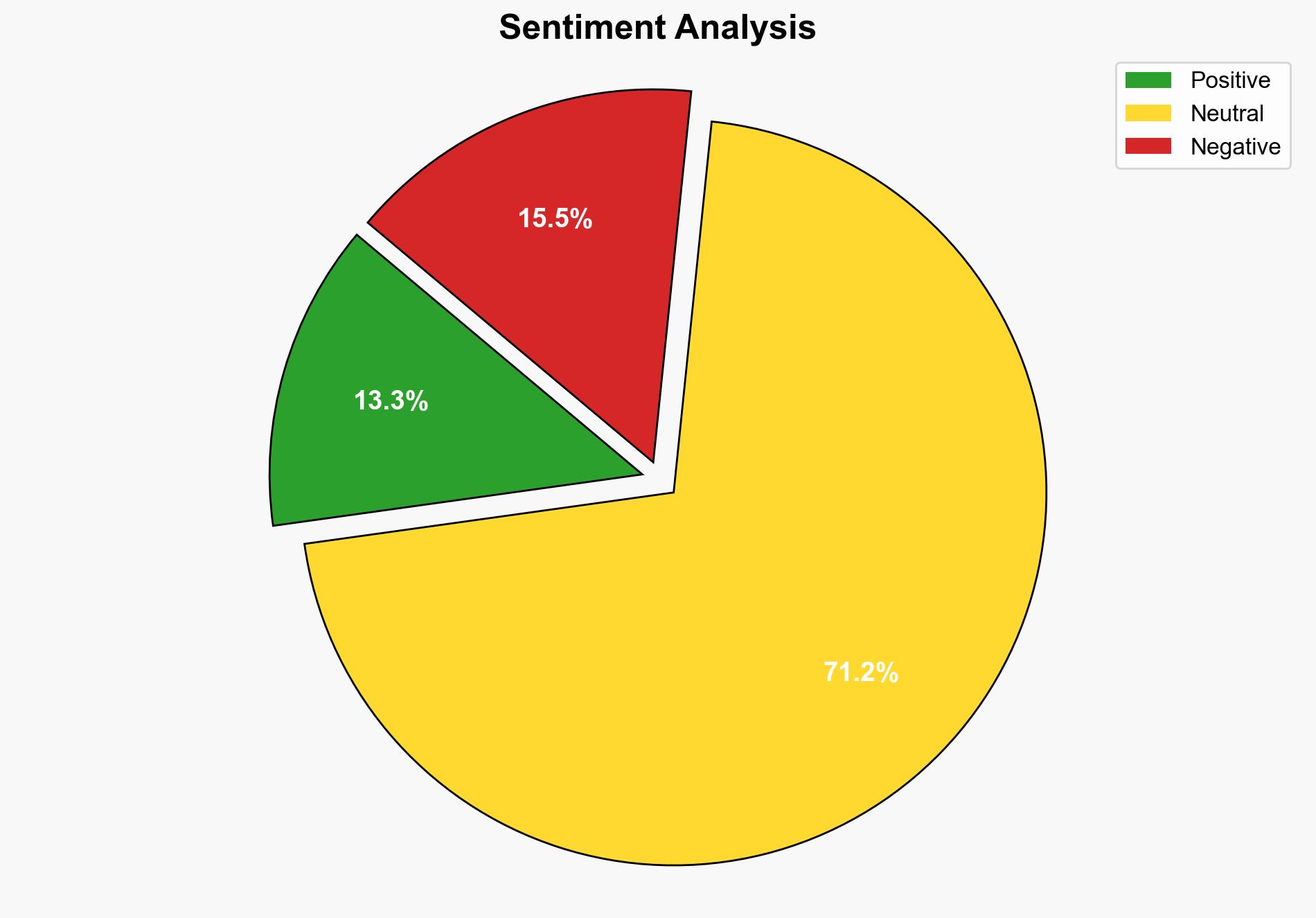
The vulnerability “MadeYouReset” in HTTP2, identified by researchers from Tel Aviv University, poses a limited threat due to existing mitigations like Rapid Reset. The most supported hypothesis is that the vulnerability’s impact is minimal due to proactive measures by major service providers, including Cloudflare. Confidence level: High. Recommended action: Continue monitoring for any new implementations or variations of the vulnerability and ensure all systems are patched promptly.
2. Competing Hypotheses
Hypothesis 1: The MadeYouReset vulnerability poses a minimal threat due to widespread mitigations and limited implementation in vulnerable systems.
Hypothesis 2: The vulnerability could be exploited more widely if attackers find new methods to bypass existing mitigations or if more systems remain unpatched.
Using ACH 2.0, Hypothesis 1 is better supported as major implementations have already taken proactive measures, and the vulnerability affects a small number of systems.
3. Key Assumptions and Red Flags
Assumptions include the belief that all major systems have implemented effective mitigations and that attackers will not quickly adapt to exploit the vulnerability. A red flag is the potential underestimation of the vulnerability’s impact if new attack vectors are discovered. There is also a blind spot regarding the speed of patch deployment across all affected systems.
4. Implications and Strategic Risks
The primary risk is a potential increase in denial-of-service attacks if the vulnerability is exploited before all systems are patched. Economically, affected companies could face service disruptions. Cyber risks include the possibility of cascading effects if attackers leverage the vulnerability to target interconnected systems. Geopolitically, there could be increased tension if state actors exploit the vulnerability for espionage or disruption.
5. Recommendations and Outlook
- Ensure all systems are updated and patched promptly to mitigate risks.
- Encourage continuous monitoring and threat intelligence sharing among cybersecurity communities.
- Scenario-based projections:
- Best case: All systems are patched, and no significant exploitation occurs.
- Worst case: Attackers find new vectors, leading to widespread service disruptions.
- Most likely: Limited exploitation with minor disruptions due to effective mitigations.
6. Key Individuals and Entities
Gal Bar Nahum, Anat Bremler-Barr, Yaniv Harel (researchers from Tel Aviv University) are credited with discovering the vulnerability.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus