Major Cyberattacks Target Bumble, Panera Bread, Match Group, and CrunchBase, Prompting Law Enforcement Involv…
Published on: 2026-01-29
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Bumble Panera Bread CrunchBase Match Hit By Cyberattacks
1. BLUF (Bottom Line Up Front)
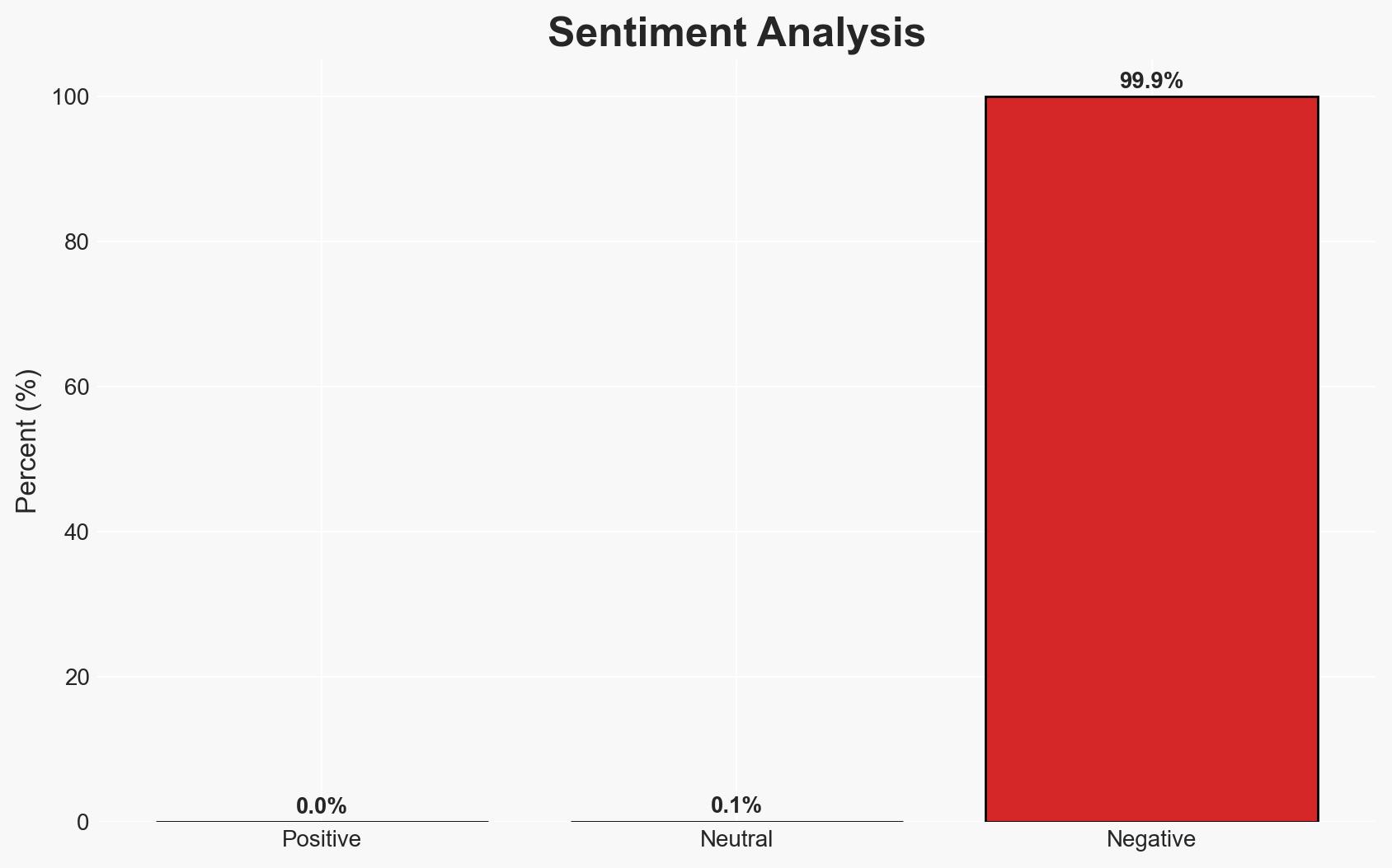
A coordinated wave of cyberattacks has targeted Bumble Inc., Panera Bread Co., Match Group Inc., and CrunchBase Inc., likely perpetrated by the group known as ShinyHunters. The attacks primarily involved social engineering techniques to gain unauthorized access to company networks. Current evidence moderately supports the hypothesis that these attacks are part of a broader campaign targeting US companies. The overall confidence level in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: The cyberattacks are part of a coordinated campaign by ShinyHunters targeting US companies using social engineering techniques. This is supported by the recent warnings from cybersecurity experts and the group’s claim of responsibility. However, independent verification of ShinyHunters’ involvement is lacking, creating uncertainty.
- Hypothesis B: The cyberattacks are isolated incidents carried out by opportunistic hackers exploiting vulnerabilities in these companies’ systems. This hypothesis is contradicted by the timing and method of attacks, which suggest a coordinated effort rather than isolated incidents.
- Assessment: Hypothesis A is currently better supported due to the pattern of attacks and the attribution to ShinyHunters by cybersecurity experts. Key indicators that could shift this judgment include independent verification of ShinyHunters’ involvement or evidence of different actors.
3. Key Assumptions and Red Flags
- Assumptions: The attacks are primarily motivated by financial gain through extortion; ShinyHunters has the capability to execute such coordinated attacks; affected companies have accurately reported the scope of the breaches.
- Information Gaps: Lack of detailed technical analysis of the breaches; absence of independent verification of ShinyHunters’ claims; incomplete timeline of the attacks.
- Bias & Deception Risks: Potential bias in company disclosures aiming to minimize perceived impact; possible deception by ShinyHunters in claiming responsibility to enhance their reputation.
4. Implications and Strategic Risks
The cyberattacks could signal a trend of increased targeting of US companies by sophisticated threat actors, potentially leading to heightened cybersecurity measures and regulatory scrutiny.
- Political / Geopolitical: Increased tension between the US and countries perceived to harbor cybercriminals; potential for diplomatic repercussions if state-sponsored involvement is suspected.
- Security / Counter-Terrorism: Heightened alertness in cybersecurity protocols across industries; potential for increased collaboration between private and public sectors in cybersecurity defense.
- Cyber / Information Space: Possible escalation in cyber threat landscape, with more actors adopting social engineering techniques; increased focus on securing single sign-on systems.
- Economic / Social: Potential financial losses for affected companies; erosion of consumer trust in digital platforms if data breaches become more frequent.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of network traffic for signs of intrusion; conduct thorough forensic analysis of breaches; engage with law enforcement and cybersecurity agencies for support.
- Medium-Term Posture (1–12 months): Invest in employee training to recognize and respond to phishing attempts; strengthen partnerships with cybersecurity firms; develop incident response plans tailored to social engineering threats.
- Scenario Outlook:
- Best: Enhanced security measures deter future attacks, and affected companies recover without significant data loss.
- Worst: Continued attacks lead to major data breaches, resulting in regulatory penalties and loss of consumer trust.
- Most-Likely: Companies bolster defenses, reducing the frequency of successful attacks, but the threat persists as attackers adapt.
6. Key Individuals and Entities
- ShinyHunters (hacker group)
- Bumble Inc. (affected company)
- Panera Bread Co. (affected company)
- Match Group Inc. (affected company)
- CrunchBase Inc. (affected company)
- Mandiant (cybersecurity firm)
7. Thematic Tags
cybersecurity, social engineering, data breach, ShinyHunters, US companies, phishing, cyber threat
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us