Major Data Breach: 50 Companies Compromised Due to Lack of Multi-Factor Authentication
Published on: 2026-01-06
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Dozens of organizations fall victim to infostealers after failing to enforce MFA
1. BLUF (Bottom Line Up Front)
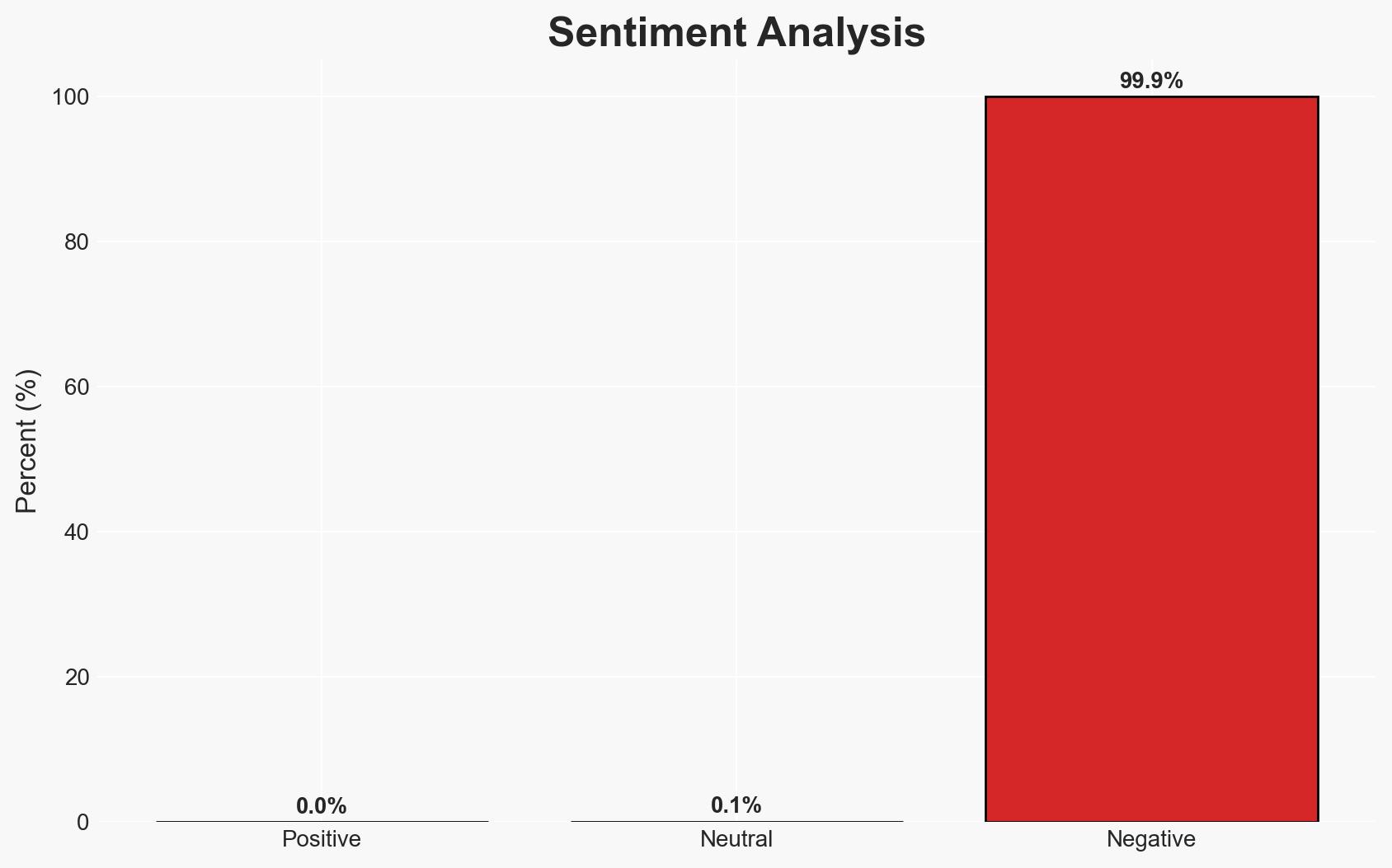
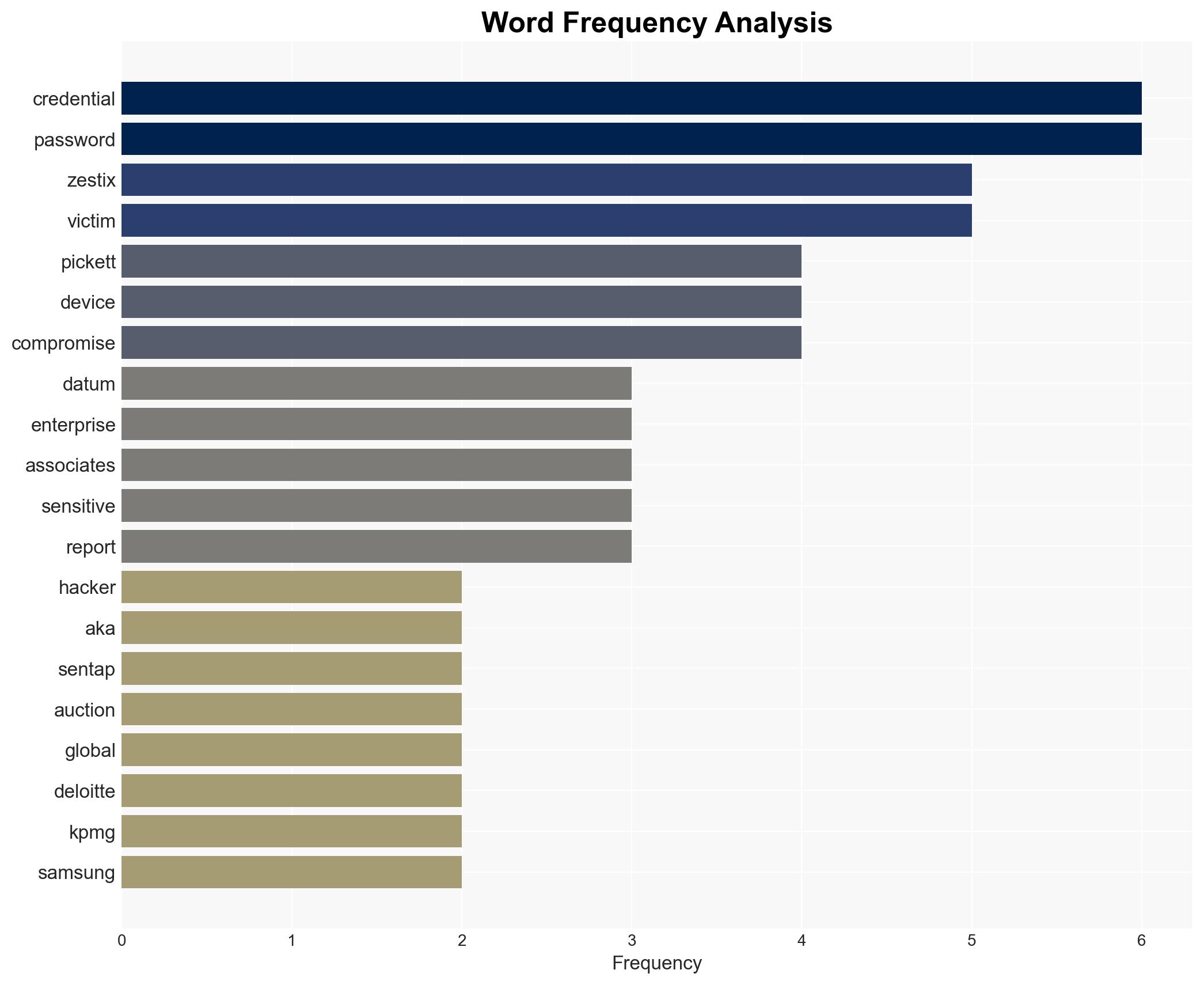
The hacking campaign led by the actor known as “Zestix” has compromised sensitive data from 50 global enterprises due to inadequate cybersecurity practices, specifically the lack of multi-factor authentication (MFA). The most likely hypothesis is that the exploitation was facilitated by infostealer malware and poor credential hygiene. This incident highlights significant vulnerabilities in corporate cybersecurity defenses. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
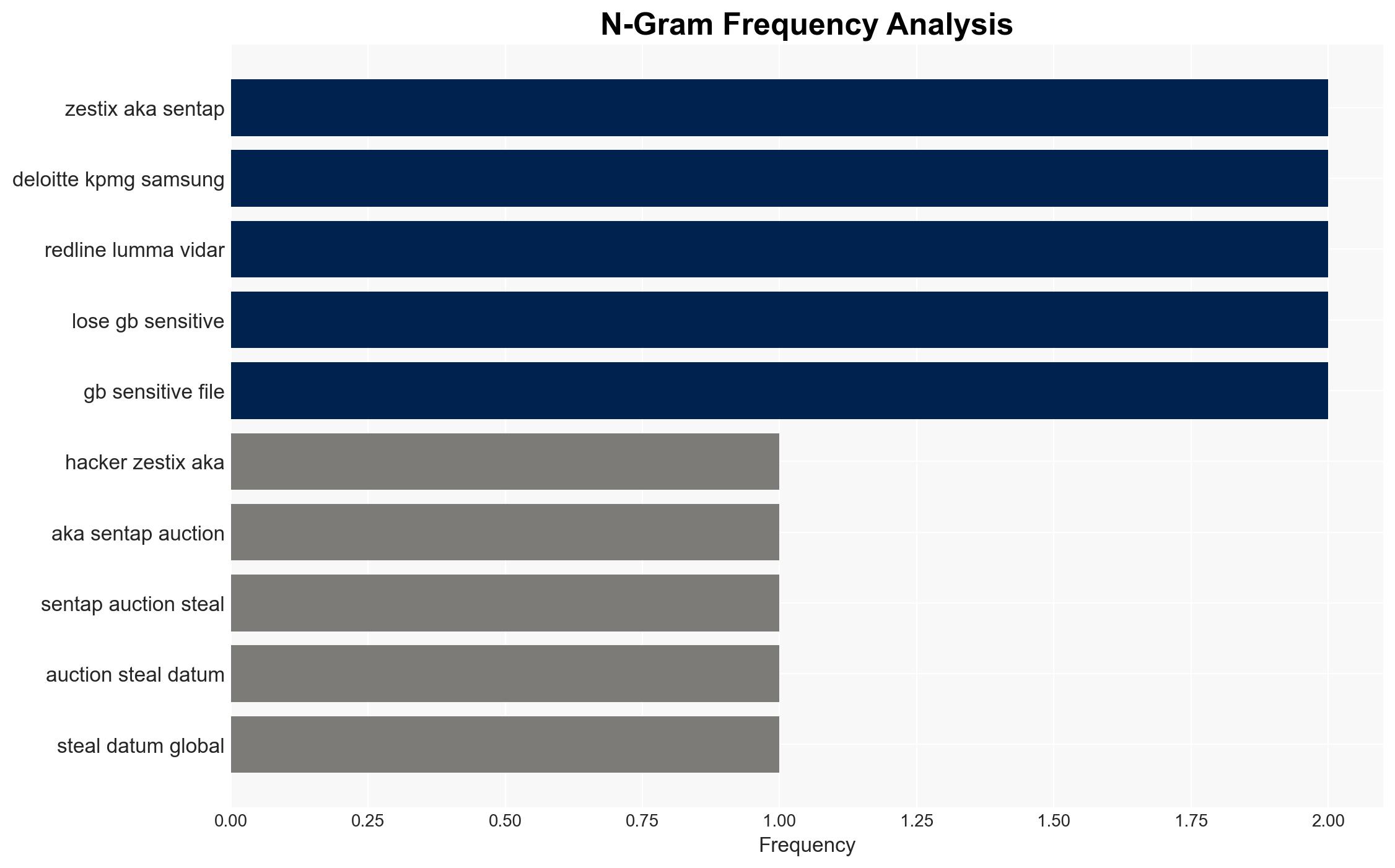
- Hypothesis A: The breaches were primarily due to the lack of MFA and poor password hygiene, which allowed infostealer malware to exfiltrate credentials. This is supported by the consistent pattern of compromised credentials across all affected organizations and the specific mention of infostealers like RedLine, Lumma, and Vidar.
- Hypothesis B: The breaches could be part of a coordinated insider threat or a sophisticated phishing campaign that exploited existing vulnerabilities beyond just the absence of MFA. This hypothesis is less supported due to the lack of specific evidence pointing to insider involvement or advanced phishing techniques.
- Assessment: Hypothesis A is currently better supported due to the direct linkage between the lack of MFA and the use of infostealers as reported by Hudson Rock. Indicators that could shift this judgment include evidence of insider collusion or advanced social engineering tactics.
3. Key Assumptions and Red Flags
- Assumptions: Organizations did not implement MFA due to oversight or resource constraints; infostealers were the primary tool for credential theft; data auctioning is motivated by financial gain.
- Information Gaps: Specific methods of initial malware infection; full scope of data compromised; potential insider involvement.
- Bias & Deception Risks: Potential bias in reporting from Hudson Rock due to vested interests; risk of deception by Zestix in overstating the extent of the breach to inflate data value.
4. Implications and Strategic Risks
This development underscores the critical need for robust cybersecurity measures and could lead to increased regulatory scrutiny and pressure on organizations to adopt MFA. The incident may also embolden other cybercriminals to exploit similar vulnerabilities.
- Political / Geopolitical: Potential for increased international cooperation on cybersecurity standards and practices.
- Security / Counter-Terrorism: Heightened threat environment as cybercriminals may target similar vulnerabilities in critical infrastructure.
- Cyber / Information Space: Likely increase in infostealer malware distribution and dark web data auctions.
- Economic / Social: Potential financial losses and reputational damage for affected enterprises, leading to broader economic impacts.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Urge affected organizations to implement MFA immediately and conduct thorough security audits to identify and remediate vulnerabilities.
- Medium-Term Posture (1–12 months): Develop partnerships for information sharing on cyber threats and invest in employee training on cybersecurity best practices.
- Scenario Outlook:
- Best: Rapid adoption of MFA and improved cybersecurity measures reduce vulnerability.
- Worst: Continued exploitation of similar vulnerabilities leads to further breaches.
- Most-Likely: Gradual improvement in cybersecurity practices with occasional breaches as organizations adapt.
6. Key Individuals and Entities
- Zestix (aka Sentap) – Hacker responsible for the campaign.
- Hudson Rock – Israeli cybersecurity startup reporting on the incident.
- Not clearly identifiable from open sources in this snippet – Specific individuals within affected organizations.
7. Thematic Tags
cybersecurity, data breach, infostealers, multi-factor authentication, credential theft, dark web, cybercrime
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us