Major Security Vulnerabilities Discovered in Four Widely Used VS Code Extensions with 125 Million Downloads
Published on: 2026-02-18
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Critical Flaws Found in Four VS Code Extensions with Over 125 Million Installs
1. BLUF (Bottom Line Up Front)
Recent disclosures reveal critical vulnerabilities in four widely-used VS Code extensions, posing significant risks of data exfiltration and remote code execution. These vulnerabilities could compromise entire organizations, especially those with inadequate cybersecurity measures. The most likely hypothesis is that these vulnerabilities are being actively exploited by threat actors, with moderate confidence due to the lack of direct evidence of exploitation.
2. Competing Hypotheses
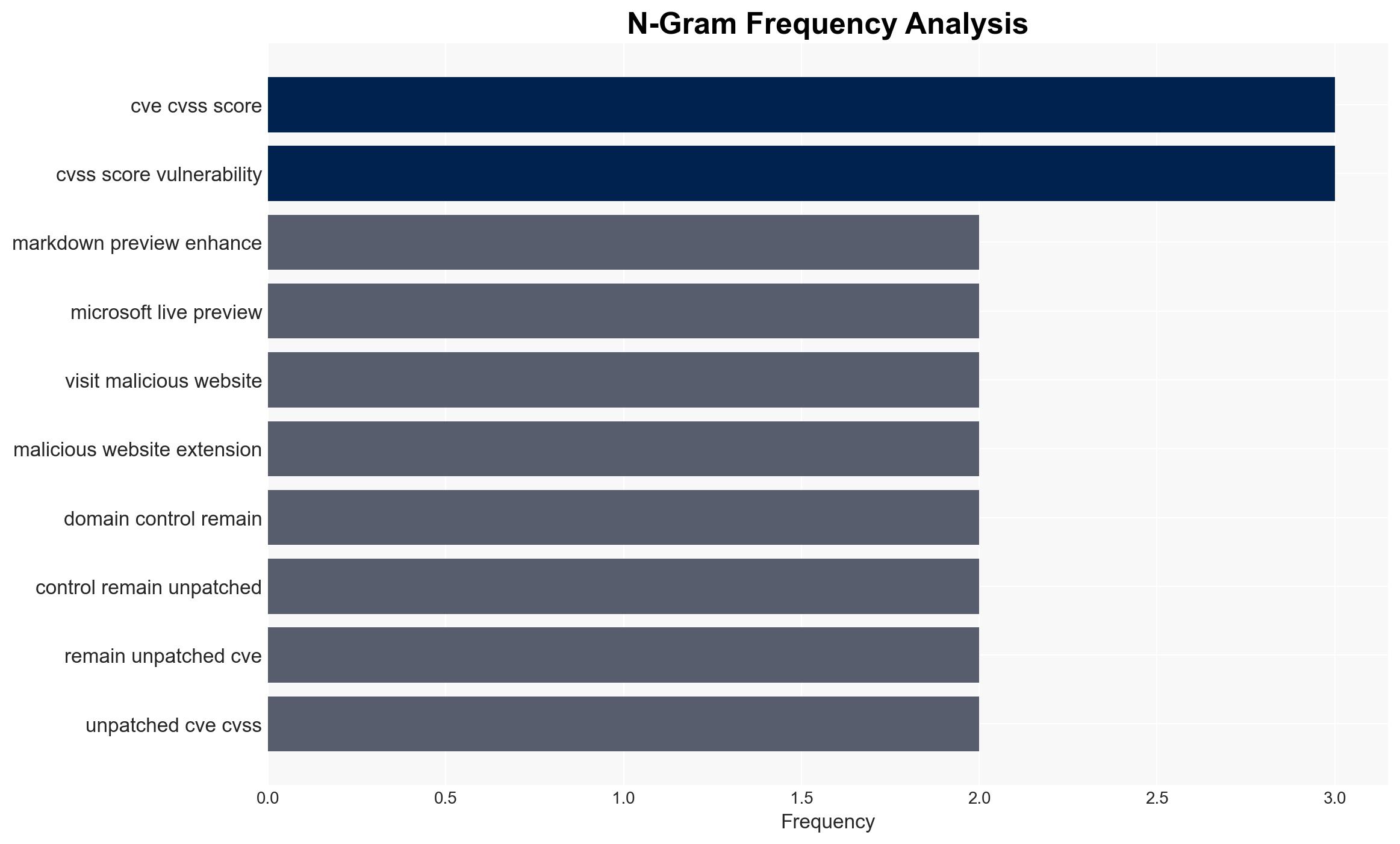
- Hypothesis A: The vulnerabilities in the VS Code extensions are being actively exploited by threat actors to compromise organizational networks. This is supported by the high CVSS scores and the widespread use of the extensions. However, there is no direct evidence of exploitation, creating uncertainty.
- Hypothesis B: The vulnerabilities, while severe, have not yet been exploited on a large scale due to recent disclosure and ongoing mitigation efforts. This is supported by the lack of reported incidents and the silent patching of one vulnerability by Microsoft. However, the unpatched status of other vulnerabilities contradicts this.
- Assessment: Hypothesis A is currently better supported due to the severity of the vulnerabilities and the potential for exploitation. Indicators such as reports of active exploitation or increased network anomalies could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: Organizations are not fully aware of the vulnerabilities; threat actors have the capability and intent to exploit these vulnerabilities; Microsoft and other stakeholders are actively working on patches.
- Information Gaps: Lack of data on actual exploitation incidents; unclear timeline for patch releases for unpatched vulnerabilities.
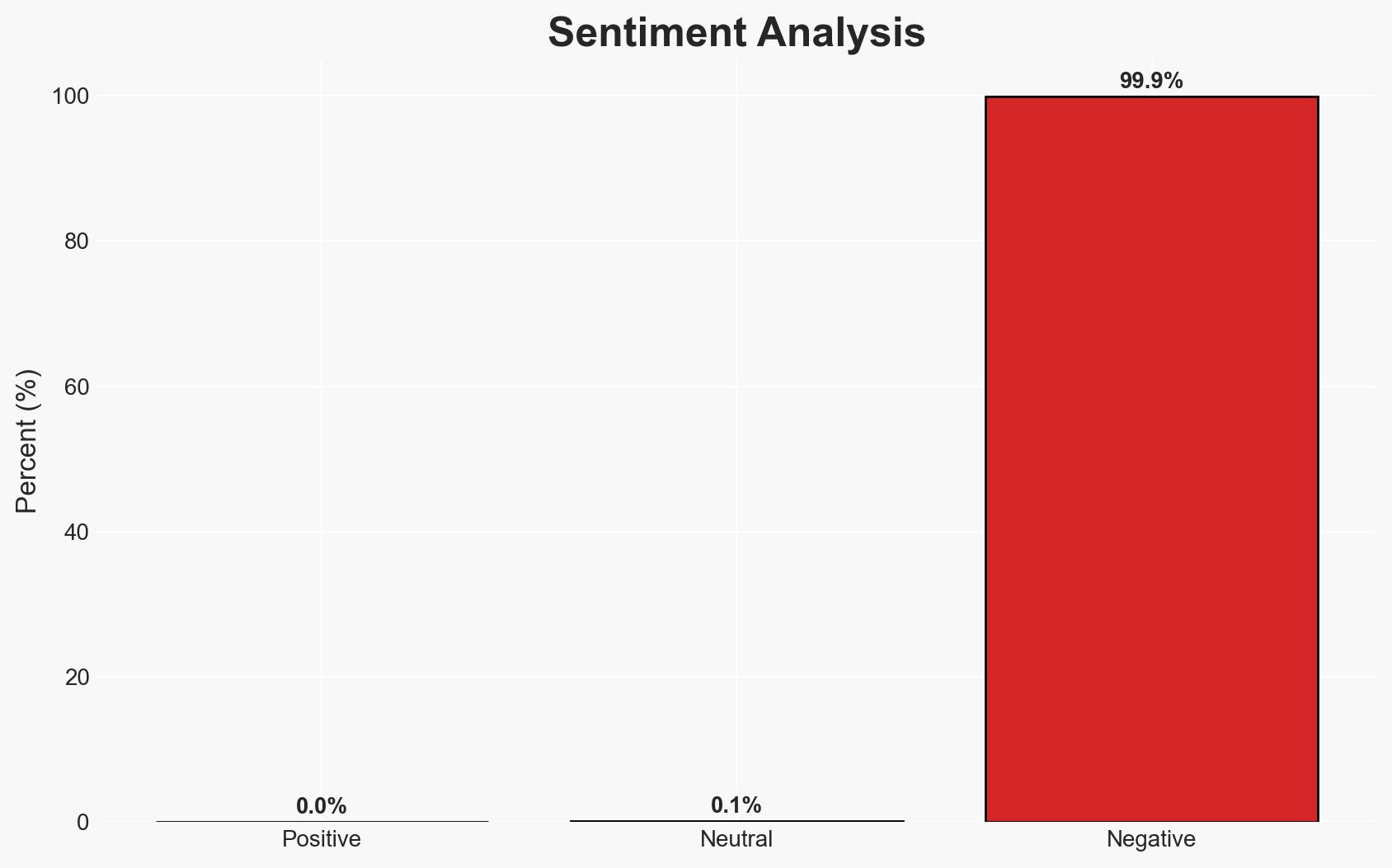
- Bias & Deception Risks: Potential bias in reporting severity due to the source’s vested interest in cybersecurity; lack of independent verification of vulnerability exploitation claims.
4. Implications and Strategic Risks
The vulnerabilities could lead to significant security breaches, affecting organizations’ operational integrity and data confidentiality. Over time, this could erode trust in widely-used software tools and increase scrutiny on software supply chains.
- Political / Geopolitical: Potential for increased regulatory scrutiny on software security standards.
- Security / Counter-Terrorism: Heightened risk of cyber espionage and data theft targeting critical infrastructure.
- Cyber / Information Space: Increased focus on securing development environments and software supply chains.
- Economic / Social: Potential financial losses for affected organizations and reputational damage to software vendors.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Organizations should audit and update their VS Code extensions, apply network segmentation, and enhance monitoring for suspicious activities.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms for threat intelligence sharing; invest in secure software development practices.
- Scenario Outlook:
- Best: Vulnerabilities are patched promptly, with no major exploitation incidents.
- Worst: Widespread exploitation leads to significant data breaches and operational disruptions.
- Most-Likely: Some exploitation occurs before patches are fully implemented, leading to targeted breaches.
6. Key Individuals and Entities
- OX Security researchers Moshe Siman Tov Bustan and Nir Zadok
- Microsoft (as the developer of VS Code)
- Not clearly identifiable from open sources in this snippet regarding specific threat actors
7. Thematic Tags
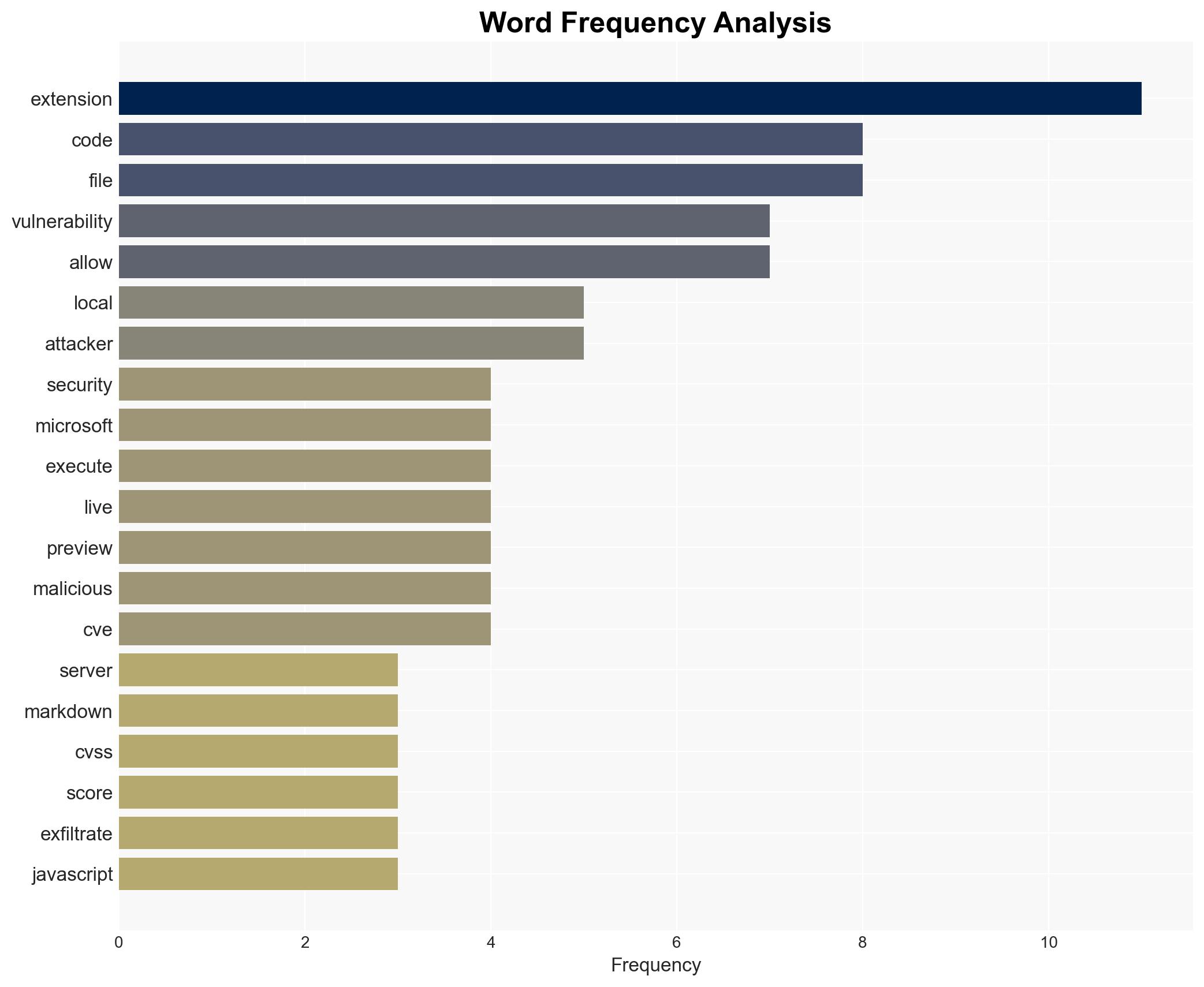
cybersecurity, software vulnerabilities, data exfiltration, remote code execution, software supply chain, threat intelligence
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us