Malicious Activity Integrates Seamlessly into Open-Source Development Processes, Exploiting Trust and Automat…
Published on: 2026-02-03
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Open-source attacks move through normal development workflows
1. BLUF (Bottom Line Up Front)
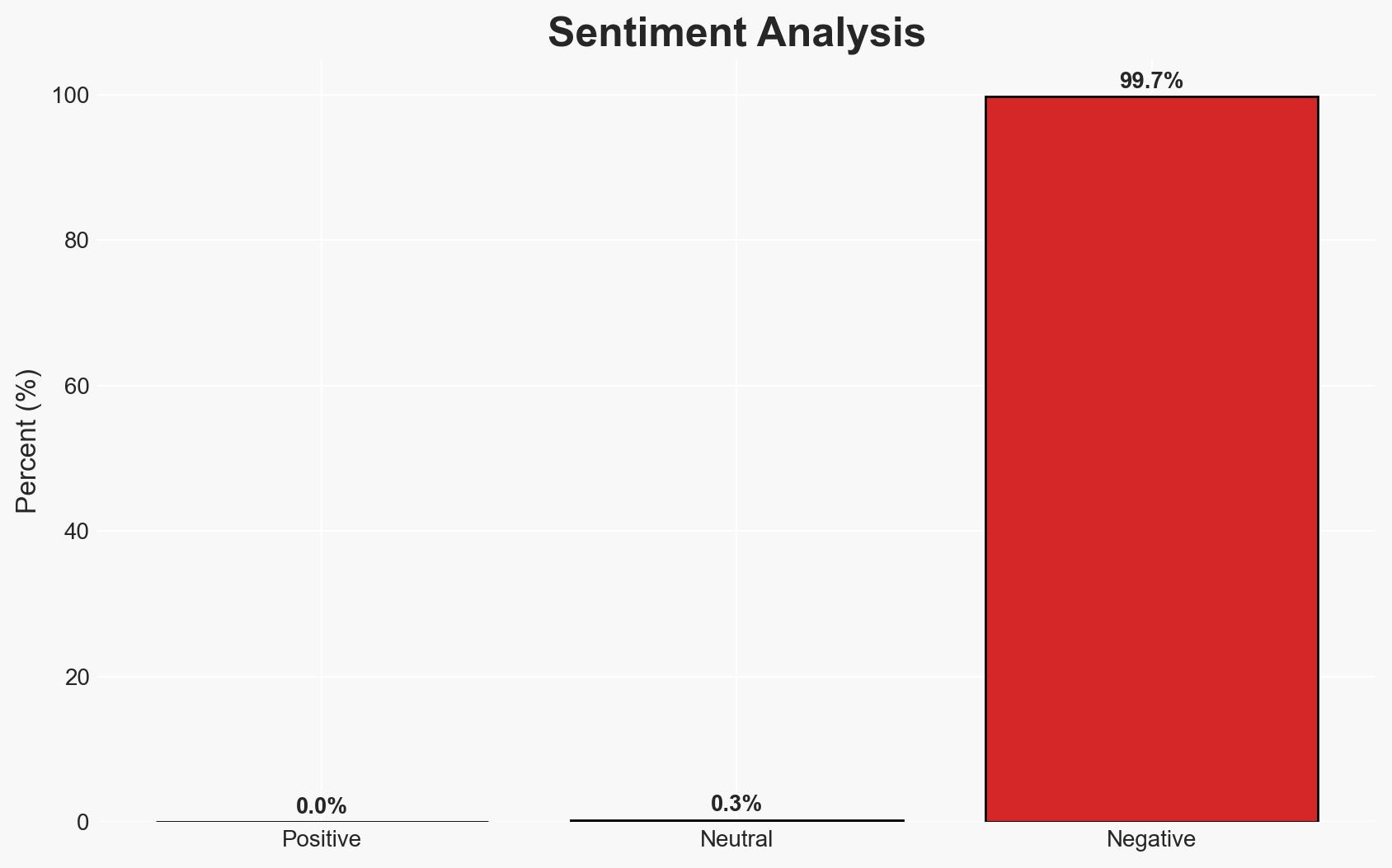
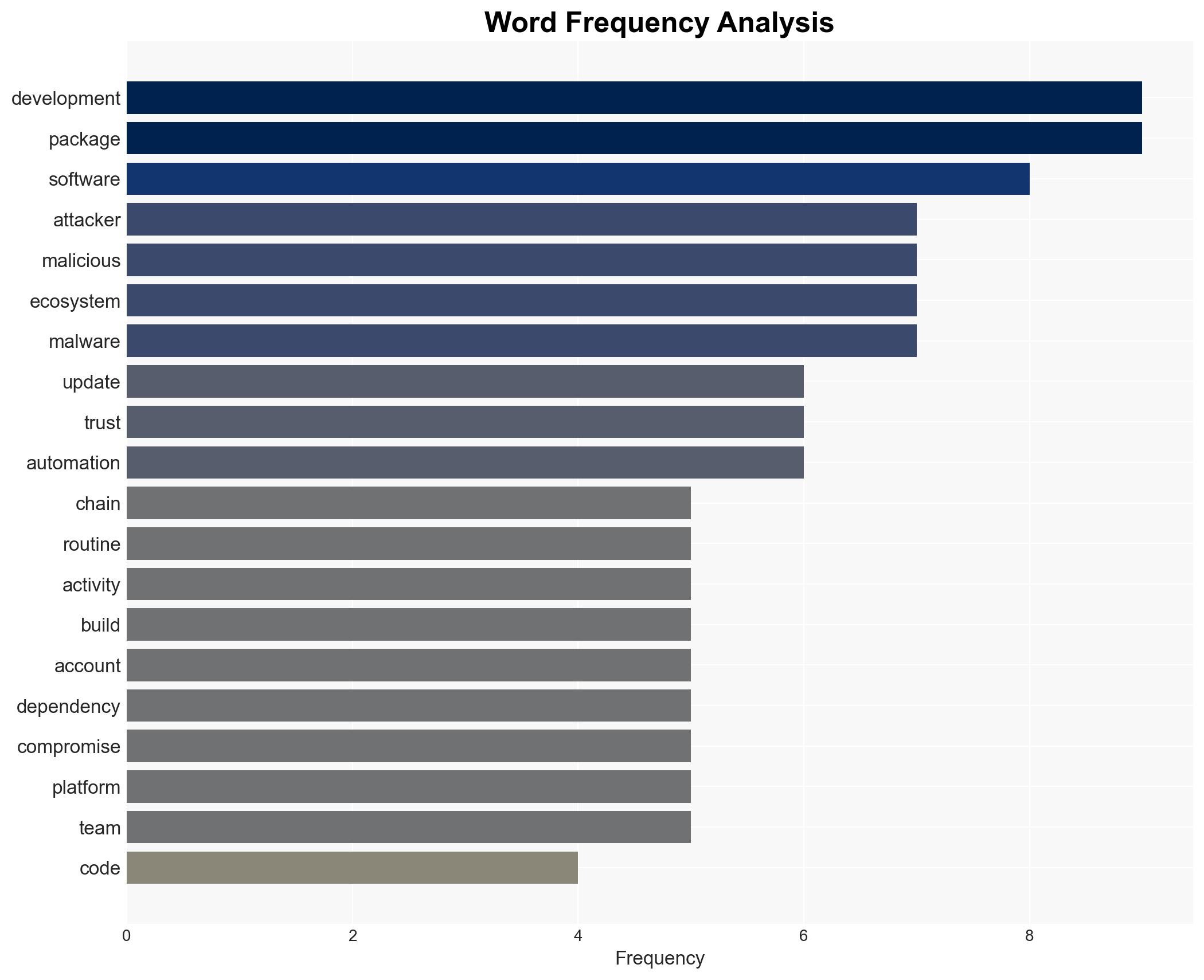
The software supply chain, particularly within open-source ecosystems like npm, has become a significant vector for cyberattacks, exploiting trust and automation to distribute malware. The Shai-hulud worm exemplifies the potential for widespread disruption. This assessment holds moderate confidence due to the reliance on open-source reporting and potential biases in source data.
2. Competing Hypotheses
- Hypothesis A: Attackers are primarily exploiting inherent vulnerabilities in open-source ecosystems due to their reliance on trust and automation. Evidence includes the widespread impact of the Shai-hulud worm and the use of compromised maintainer accounts. Key uncertainties include the full extent of ecosystem-specific vulnerabilities and attacker motivations.
- Hypothesis B: The observed attacks are opportunistic, targeting ecosystems with weaker governance and security measures. Supporting evidence includes the decline in attacks on platforms with stronger controls, such as Python Package Index and NuGet. Contradicting evidence includes the continued targeting of npm despite its prominence.
- Assessment: Hypothesis A is currently better supported due to the scale and sophistication of attacks like the Shai-hulud worm, which indicate a strategic exploitation of systemic vulnerabilities. Indicators that could shift this judgment include increased attacks on platforms with robust security measures or evidence of coordinated campaigns across multiple ecosystems.
3. Key Assumptions and Red Flags
- Assumptions: Open-source ecosystems will continue to rely heavily on trust and automation; attackers have the capability to exploit these systems at scale; current security measures are insufficient to prevent similar future incidents.
- Information Gaps: Detailed data on the specific vulnerabilities exploited by the Shai-hulud worm; comprehensive analysis of the motivations and affiliations of the attackers.
- Bias & Deception Risks: Potential bias in reporting from security firms with vested interests in highlighting vulnerabilities; risk of deception in attacker tactics to mislead attribution efforts.
4. Implications and Strategic Risks
The evolution of these attacks could lead to increased scrutiny and regulatory pressure on open-source ecosystems, potentially affecting their growth and innovation. The reliance on automated systems may necessitate a reevaluation of security protocols across the software development lifecycle.
- Political / Geopolitical: Potential for international regulatory responses targeting software supply chain security.
- Security / Counter-Terrorism: Increased risk of cyber threats to critical infrastructure reliant on open-source software.
- Cyber / Information Space: Heightened focus on securing development pipelines and improving threat detection capabilities.
- Economic / Social: Possible economic impact on businesses reliant on open-source software due to increased security costs and potential disruptions.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of open-source dependencies; implement stricter access controls for maintainer accounts; increase awareness and training on supply chain risks.
- Medium-Term Posture (1–12 months): Develop partnerships with open-source communities to improve governance; invest in automated threat detection and response capabilities; advocate for industry-wide security standards.
- Scenario Outlook:
- Best: Adoption of robust security measures across ecosystems reduces attack vectors.
- Worst: Continued exploitation leads to significant disruptions and loss of trust in open-source software.
- Most-Likely: Incremental improvements in security practices with ongoing targeted attacks.
6. Key Individuals and Entities
- Tomislav Peričin, CTO at ReversingLabs
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, open-source, software supply chain, malware, npm, automation, trust exploitation
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us