Malicious Extensions Target Firefox, Chrome, and Edge Users, Compromising Browser Security
Published on: 2026-01-19
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Firefox joins Chrome and Edge as sleeper extensions spy on users
1. BLUF (Bottom Line Up Front)
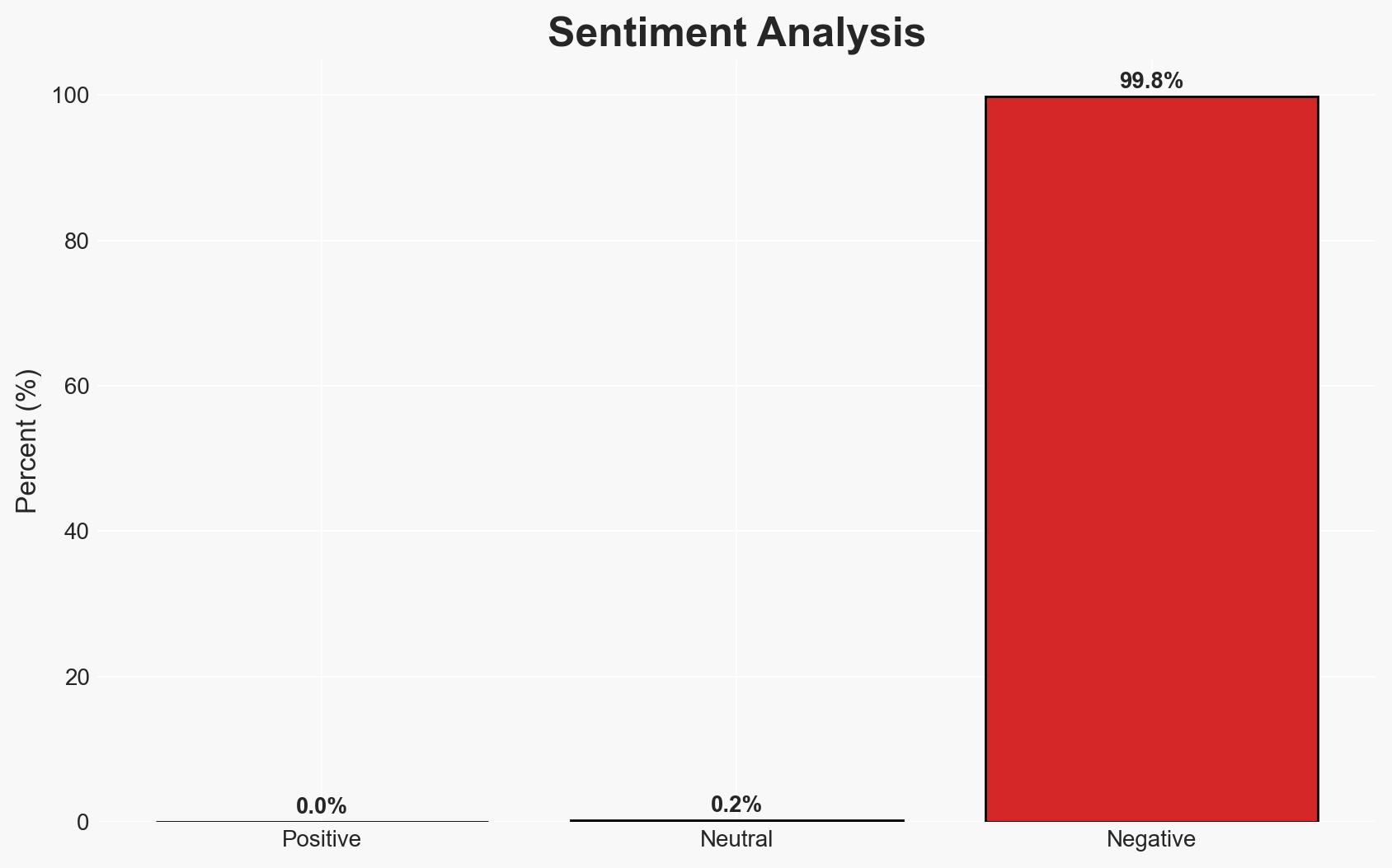
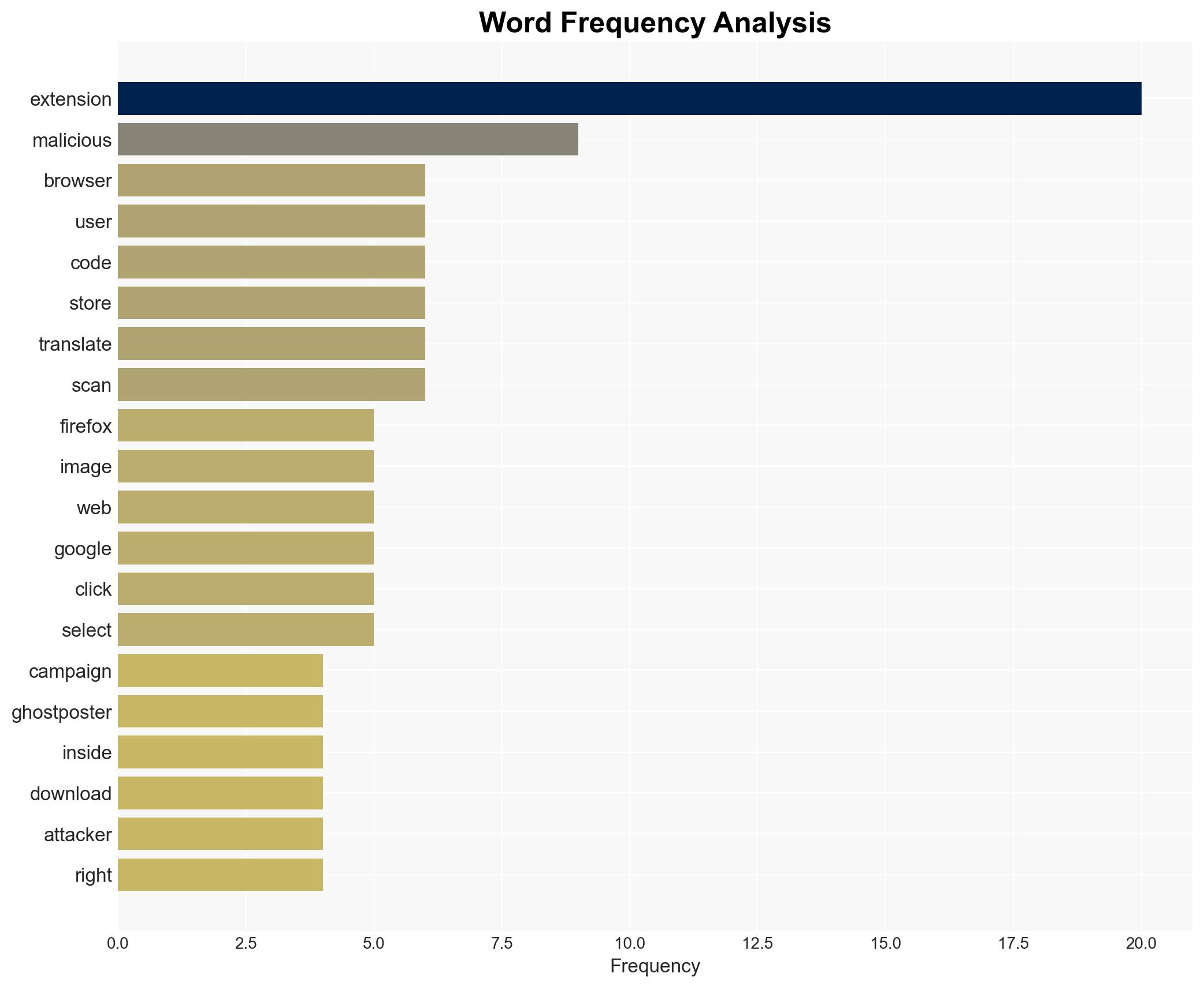
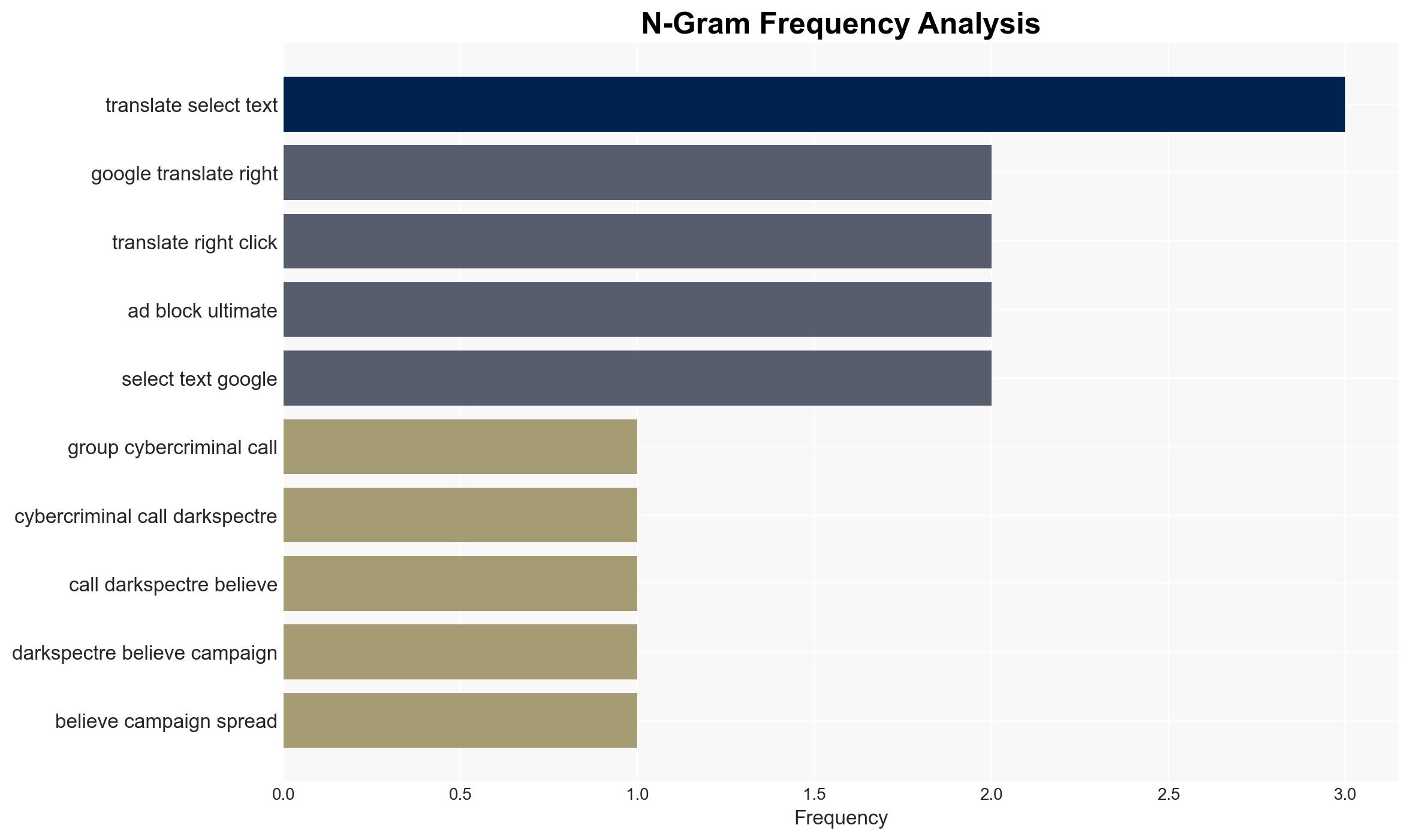
The cybercriminal group DarkSpectre is exploiting browser extensions to conduct espionage and potentially more harmful cyber activities. The group has successfully infiltrated Firefox, Chrome, and Edge through campaigns like GhostPoster, compromising user data on a large scale. This poses significant risks to user privacy and security, with moderate confidence in the assessment due to the evolving nature of the threat and limited visibility into the full scope of the campaigns.
2. Competing Hypotheses
- Hypothesis A: DarkSpectre is primarily focused on data collection for espionage purposes. This is supported by the detailed profiling capabilities of the extensions and the use of steganography to evade detection. However, the lack of evidence of direct financial exploitation leaves room for uncertainty.
- Hypothesis B: DarkSpectre’s activities are a precursor to more aggressive cyber operations, such as credential theft and financial fraud. The potential for session hijacking and targeting online banking workflows supports this hypothesis, though current evidence of such activities is limited.
- Assessment: Hypothesis A is currently better supported due to the observed focus on data collection and the sophistication of the evasion techniques. Indicators that could shift this judgment include evidence of financial exploitation or direct attacks on critical infrastructure.
3. Key Assumptions and Red Flags
- Assumptions: The group behind the campaigns is indeed DarkSpectre; the primary goal is data collection; browser extension stores will continue to be vulnerable to such exploits.
- Information Gaps: Specific motivations of DarkSpectre; full extent of compromised extensions; potential state sponsorship or affiliations.
- Bias & Deception Risks: Potential confirmation bias in attributing all similar activities to DarkSpectre; risk of underestimating the group’s capabilities or future intentions.
4. Implications and Strategic Risks
The development could lead to increased scrutiny of browser extension security and potential regulatory changes. The threat may evolve into more direct cyber-attacks, impacting broader cybersecurity dynamics.
- Political / Geopolitical: Potential for international tensions if state sponsorship is suspected; increased pressure on tech companies to enhance security measures.
- Security / Counter-Terrorism: Heightened alert for cyber espionage and potential infrastructure attacks; need for enhanced cybersecurity protocols.
- Cyber / Information Space: Increased focus on securing digital ecosystems; potential for new cyber defense partnerships or initiatives.
- Economic / Social: Potential economic impact from compromised user data; erosion of trust in digital platforms and services.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Increase monitoring of browser extension activities; conduct security audits of existing extensions; enhance public awareness campaigns.
- Medium-Term Posture (1–12 months): Develop partnerships with tech companies for improved security protocols; invest in research on detecting steganography in digital content.
- Scenario Outlook:
- Best: Enhanced security measures prevent further exploitation.
- Worst: DarkSpectre escalates to direct financial attacks.
- Most-Likely: Continued data collection with sporadic attempts at financial exploitation.
6. Key Individuals and Entities
- DarkSpectre (cybercriminal group)
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, cyber-espionage, browser extensions, data privacy, DarkSpectre, steganography, cybercrime
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us