Malicious npm Code Reached 10 of Cloud Environments – Infosecurity Magazine
Published on: 2025-09-10
Intelligence Report: Malicious npm Code Reached 10 of Cloud Environments – Infosecurity Magazine
1. BLUF (Bottom Line Up Front)
The most supported hypothesis is that the malicious npm code incident is a targeted supply chain attack aimed at cryptocurrency theft via cloud environments. This conclusion is based on the structured analysis of the rapid deployment and specific targeting of cryptocurrency-related APIs. Confidence level is moderate due to the limited timeframe of the attack and the swift removal of the malicious code. Recommended actions include enhancing monitoring of npm packages and implementing stricter security protocols for cloud environments.
2. Competing Hypotheses
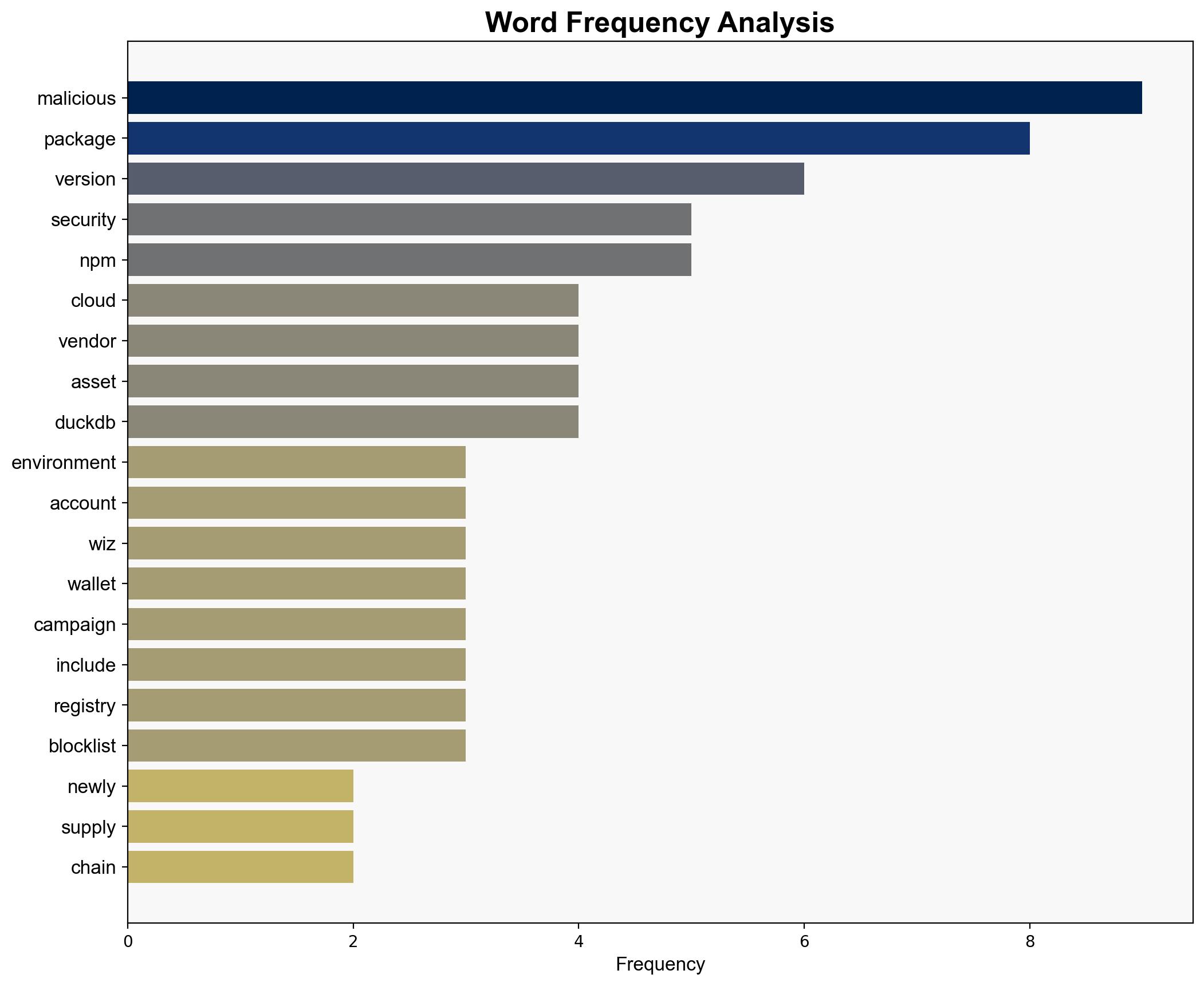
1. **Hypothesis 1**: The attack is a targeted supply chain attack aimed at stealing cryptocurrency by compromising npm packages used in cloud environments.
– **Supporting Evidence**: The malicious code specifically targets cryptocurrency wallet APIs, suggesting a focused intent on financial theft. The rapid spread and incorporation into cloud environments indicate a premeditated strategy.
2. **Hypothesis 2**: The attack is a broader test of vulnerabilities in npm and cloud environments, with cryptocurrency theft as a secondary objective.
– **Supporting Evidence**: The quick removal and limited timeframe of the attack could indicate a probing action to assess security measures and response times, with the cryptocurrency aspect serving as a cover or secondary goal.
Using ACH 2.0, Hypothesis 1 is better supported due to the specificity of the malicious code’s actions and the choice of target (cryptocurrency APIs), which aligns with known cybercriminal motivations.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that the primary goal of the attackers was financial gain through cryptocurrency theft. Another assumption is that the hijacked npm account was the sole vector for the attack.
– **Red Flags**: The rapid removal of the malicious code and limited information on the attackers’ identity or broader intentions are significant gaps. The possibility of additional compromised accounts or packages remains unverified.
– **Cognitive Bias**: Confirmation bias may lead to overemphasizing the cryptocurrency aspect without considering alternative motives.
4. Implications and Strategic Risks
The incident highlights vulnerabilities in software supply chains and cloud environments, with potential for significant financial losses if similar attacks are not mitigated. The attack could inspire copycat actions, escalating risks to other sectors reliant on npm packages. Geopolitically, such attacks could strain international relations if state actors are suspected.
5. Recommendations and Outlook
- Enhance npm package monitoring and validation processes to detect anomalies early.
- Implement stricter security protocols for cloud environments, focusing on cryptocurrency-related applications.
- Scenario Projections:
- **Best Case**: Improved security measures prevent future attacks, and no further incidents occur.
- **Worst Case**: Similar attacks proliferate, leading to widespread financial and operational disruptions.
- **Most Likely**: Incremental improvements in security reduce the frequency of attacks, but isolated incidents continue.
6. Key Individuals and Entities
– **Qix**: The npm account reportedly hijacked to publish the malicious package.
– **Wiz**: The security vendor that identified and reported the malicious code’s reach.
– **JFrog**: Cited for research on the campaign’s scope and impact.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus