Malicious npm Packages Exploit Ethereum Smart Contracts – Infosecurity Magazine
Published on: 2025-09-03
Intelligence Report: Malicious npm Packages Exploit Ethereum Smart Contracts – Infosecurity Magazine
1. BLUF (Bottom Line Up Front)
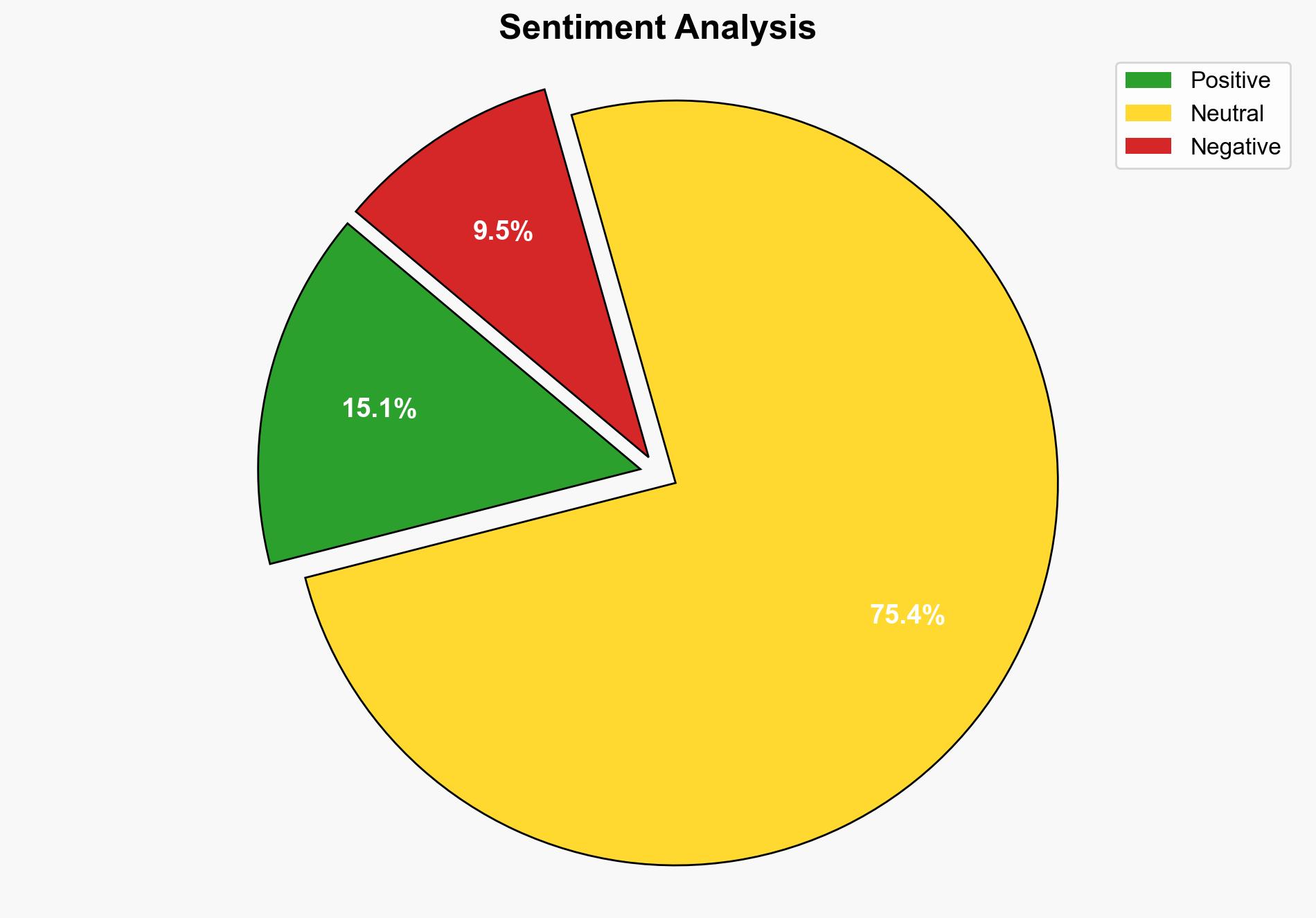
The most supported hypothesis is that the malicious npm packages are part of a sophisticated campaign leveraging blockchain technology to evade detection and target cryptocurrency-focused developers. Confidence in this hypothesis is moderate due to the evolving nature of the tactics and the complexity of the infrastructure. Recommended actions include enhancing monitoring of open-source repositories and implementing stringent vetting processes for npm packages.
2. Competing Hypotheses
Hypothesis 1: The malicious npm packages are part of a targeted campaign using Ethereum smart contracts to conceal command and control infrastructure, specifically aimed at exploiting vulnerabilities in cryptocurrency development environments.
Hypothesis 2: The campaign is a broader initiative targeting open-source software repositories indiscriminately, with the use of Ethereum smart contracts as a novel method to evade detection, but not specifically focused on cryptocurrency developers.
Using ACH 2.0, Hypothesis 1 is more supported due to the specific targeting of cryptocurrency-related repositories and the use of blockchain technology, which aligns with the interests of threat actors in this domain. Hypothesis 2 lacks specific indicators of targeting beyond the use of open-source repositories.
3. Key Assumptions and Red Flags
– Assumption: The use of Ethereum smart contracts is primarily for evasion rather than a secondary objective.
– Red Flag: The rapid evolution of tactics suggests a highly adaptable threat actor, indicating potential gaps in current detection capabilities.
– Blind Spot: Limited visibility into the full scope of the campaign and potential connections to other malicious activities.
4. Implications and Strategic Risks
The campaign represents a significant threat to the software supply chain, particularly for developers in the cryptocurrency sector. The use of blockchain for command and control could inspire similar tactics across other domains, increasing the complexity of cyber defense. Economically, successful exploitation could lead to financial losses and undermine trust in open-source platforms. Geopolitically, if state-sponsored, this could escalate tensions in the cyber domain.
5. Recommendations and Outlook
- Enhance monitoring and vetting processes for npm packages, focusing on unusual patterns and rapid changes in repository activity.
- Develop and deploy advanced detection tools capable of identifying blockchain-based command and control structures.
- Scenario Projections:
- Best Case: Improved detection and response capabilities mitigate the threat, with minimal impact on the software supply chain.
- Worst Case: The campaign expands, leading to widespread exploitation and significant economic damage.
- Most Likely: Continued adaptation by threat actors, requiring ongoing vigilance and investment in cybersecurity measures.
6. Key Individuals and Entities
– Karlo Zanki: Researcher at ReversingLabs who uncovered the campaign.
7. Thematic Tags
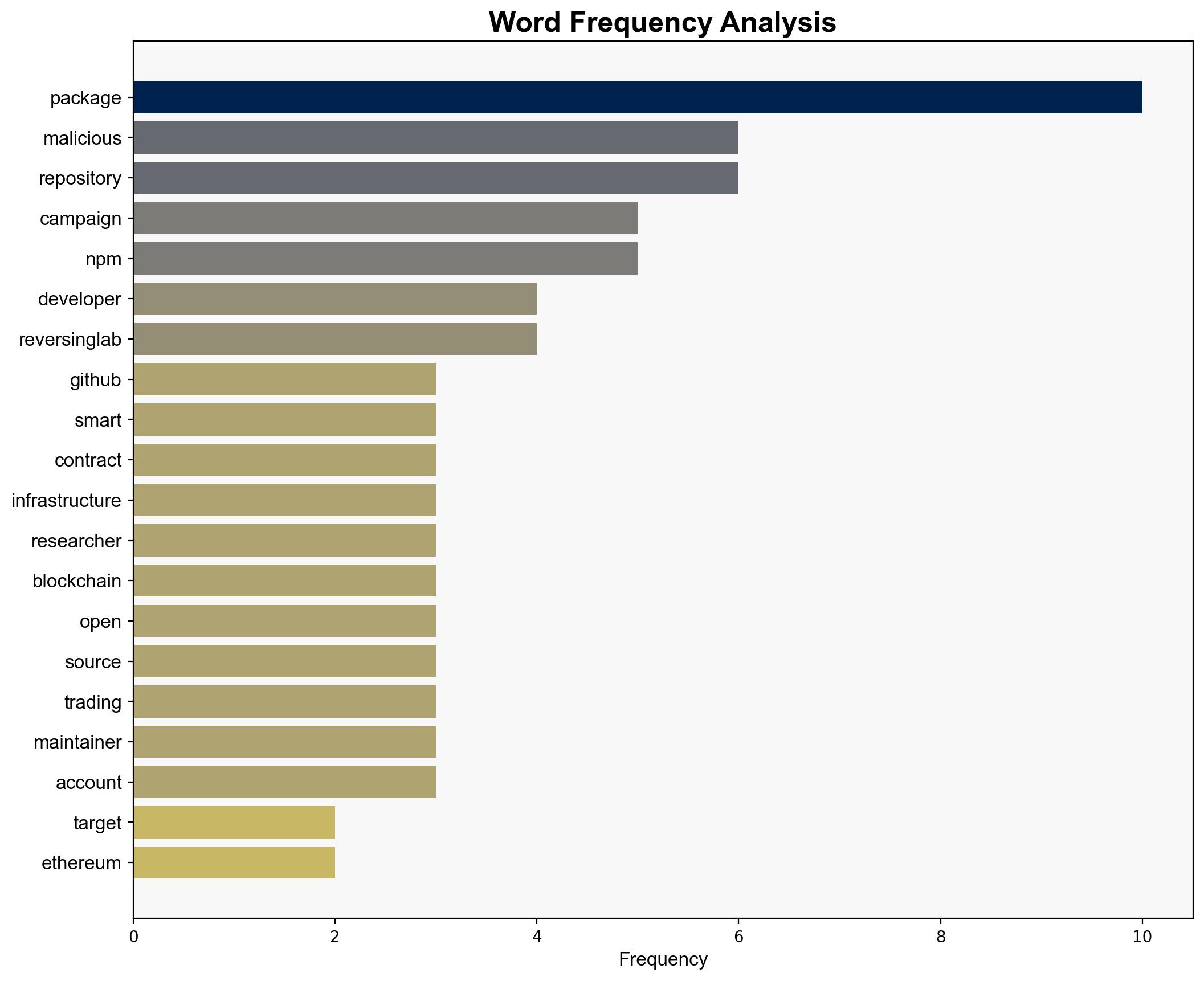
national security threats, cybersecurity, software supply chain, blockchain technology, cryptocurrency security