Malicious Python Packages on PyPI Disguised as Spellcheckers Distribute Remote Access Trojan
Published on: 2026-01-28
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Fake Python Spellchecker Packages on PyPI Delivered Hidden Remote Access Trojan
1. BLUF (Bottom Line Up Front)
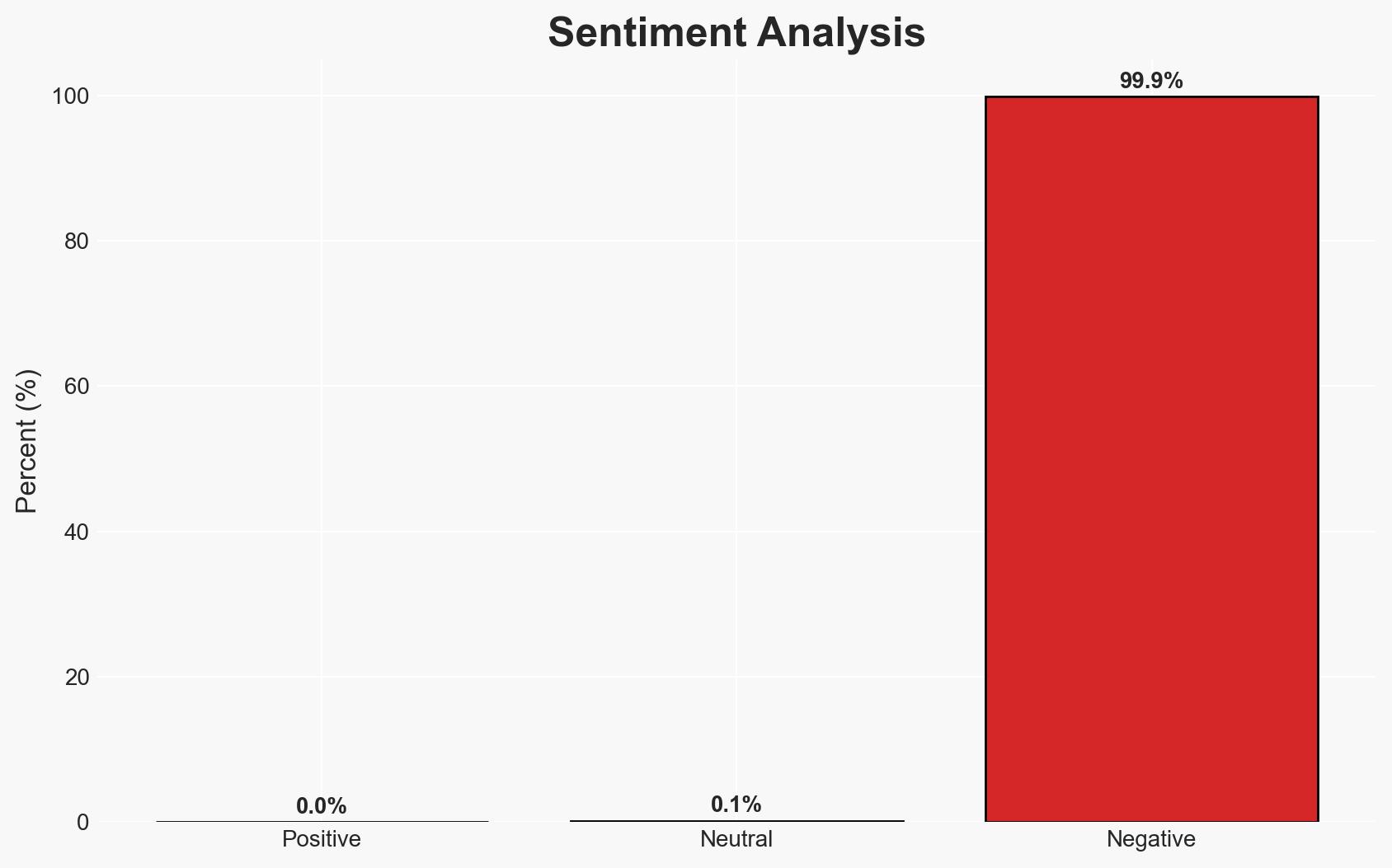
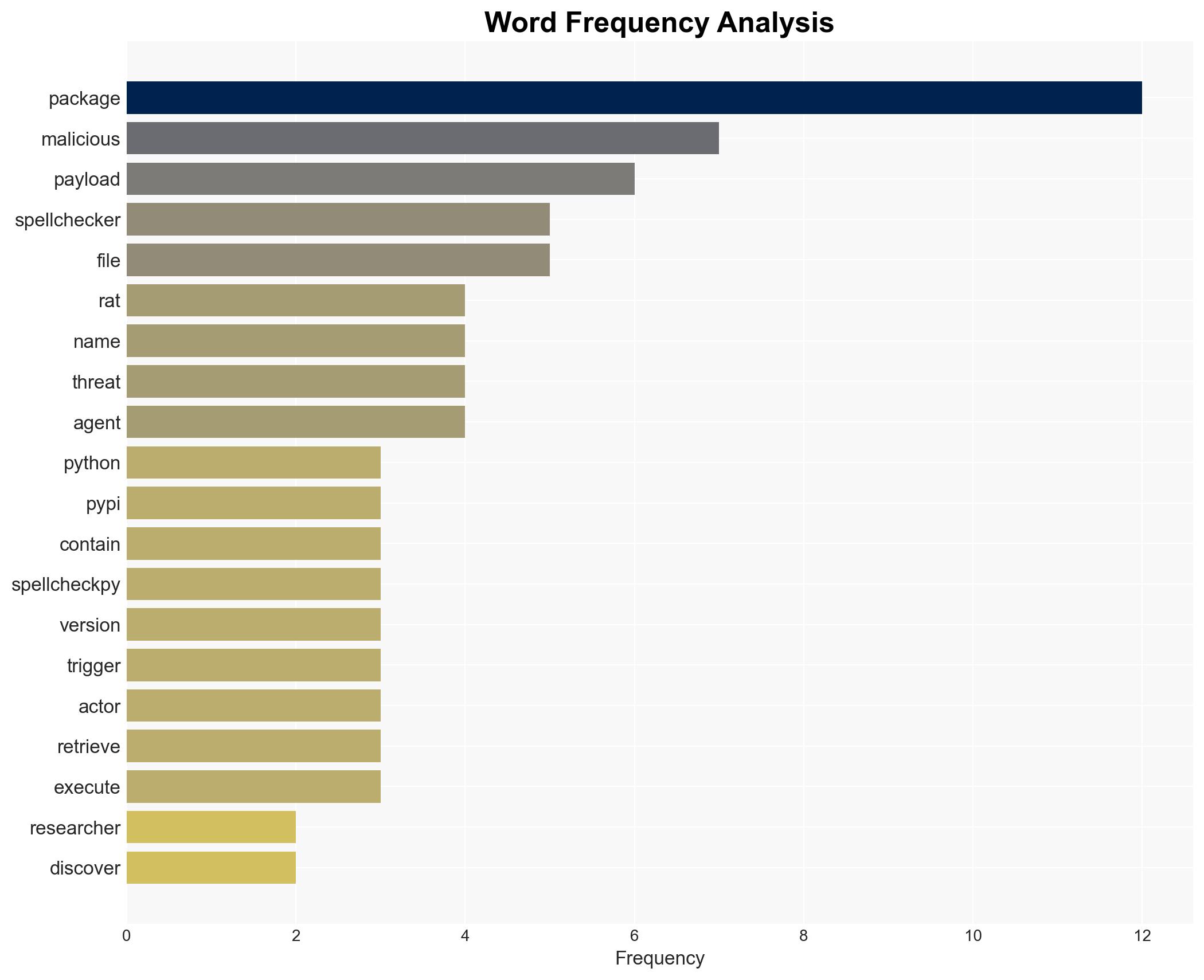
Malicious packages on PyPI, disguised as spellcheckers, have been used to deploy a remote access trojan (RAT), affecting over 1,000 users. The attack is linked to a domain associated with a hosting provider known for nation-state group affiliations. The most likely hypothesis is that this is a coordinated cyber operation targeting specific sectors, with moderate confidence due to the limited scope of known downloads and the sophistication of the attack.
2. Competing Hypotheses
- Hypothesis A: This is a targeted cyber espionage campaign by a nation-state actor aiming to infiltrate specific industrial and energy sectors. The use of sophisticated obfuscation techniques and the association with a known hosting provider support this hypothesis. However, the limited number of downloads introduces uncertainty.
- Hypothesis B: The attack is conducted by a financially motivated cybercriminal group seeking to exploit vulnerabilities in software supply chains. The presence of similar attacks on npm packages and the potential for data theft support this hypothesis, but the sophistication of the attack is atypical for purely financial motives.
- Assessment: Hypothesis A is currently better supported due to the strategic targeting and complexity of the attack. Key indicators that could shift this judgment include the identification of specific targets or further evidence of financial motives.
3. Key Assumptions and Red Flags
- Assumptions: The RAT deployment is intentional and coordinated; the hosting provider is complicit or negligent; the attack targets are within the industrial and energy sectors.
- Information Gaps: Specific identities of the threat actors; detailed analysis of the RAT’s capabilities; confirmation of targeted entities.
- Bias & Deception Risks: Potential confirmation bias towards nation-state involvement; source bias from cybersecurity firms with vested interests; possible false flag operations by the attackers.
4. Implications and Strategic Risks
This development could signal an escalation in cyber operations targeting critical infrastructure, potentially leading to increased geopolitical tensions and a reevaluation of software supply chain security.
- Political / Geopolitical: Potential attribution to a nation-state could heighten diplomatic tensions and lead to retaliatory cyber or economic measures.
- Security / Counter-Terrorism: Increased threat to critical infrastructure sectors, necessitating heightened security measures and threat intelligence sharing.
- Cyber / Information Space: Highlights vulnerabilities in open-source repositories, prompting a reevaluation of software supply chain security practices.
- Economic / Social: Potential economic disruptions if critical infrastructure is compromised, leading to broader social impacts.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of PyPI and similar repositories; issue alerts to potentially affected sectors; initiate forensic analysis of compromised systems.
- Medium-Term Posture (1–12 months): Develop partnerships for information sharing on software supply chain threats; invest in resilience measures for critical infrastructure sectors.
- Scenario Outlook:
- Best: Rapid identification and neutralization of the threat actor, leading to minimal impact.
- Worst: Successful infiltration of critical infrastructure, causing significant operational disruptions.
- Most-Likely: Continued low-level attacks with gradual improvements in detection and mitigation strategies.
6. Key Individuals and Entities
- Charlie Eriksen, Aikido researcher
- RouterHosting LLC (aka Cloudzy)
- HelixGuard
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, remote access trojan, software supply chain, nation-state actors, critical infrastructure, PyPI, cyber espionage
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us