Malware Campaigns Target macOS Users with Python Infostealers Masquerading as AI Software
Published on: 2026-02-05
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: macOS Users Hit by Python Infostealers Posing as AI Installers
1. BLUF (Bottom Line Up Front)
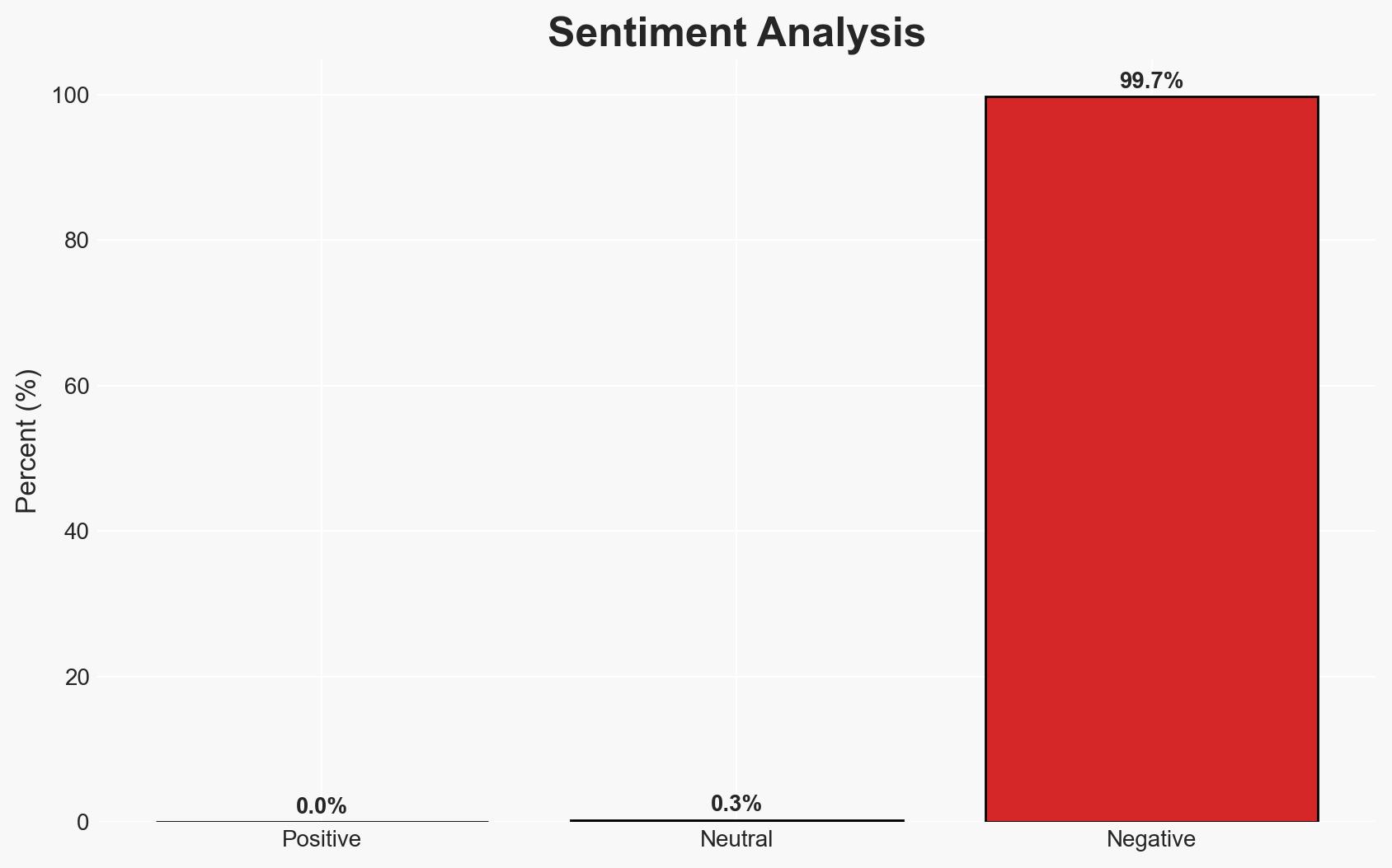
Recent malware campaigns targeting macOS users employ infostealers disguised as AI tools to exfiltrate sensitive data, including cryptocurrency and developer credentials. The campaigns exploit social engineering tactics, posing significant risks to individuals and businesses. Current analysis supports the hypothesis that these attacks are part of a broader trend of increasing threats to macOS platforms. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: The malware campaigns are isolated incidents driven by opportunistic cybercriminals exploiting macOS users’ false sense of security. Evidence includes the use of social engineering and the targeting of high-value data. Key uncertainties involve the scale and coordination of these attacks.
- Hypothesis B: The campaigns are part of a coordinated effort by a sophisticated threat actor group aiming to establish long-term access to macOS environments. Supporting evidence includes the strategic targeting of developer credentials and the use of advanced evasion techniques. Contradicting evidence is the lack of direct attribution to a known group.
- Assessment: Hypothesis B is currently better supported due to the complexity and specificity of the attacks, suggesting a level of coordination and intent beyond opportunistic behavior. Indicators such as increased targeting of macOS and the sophistication of the malware could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: macOS users have a false sense of security; the malware campaigns are financially motivated; the threat actors have advanced capabilities.
- Information Gaps: Lack of detailed attribution to specific threat actors; insufficient data on the full extent of the campaigns’ reach and impact.
- Bias & Deception Risks: Potential bias in underestimating macOS vulnerabilities; risk of deception in malware attribution due to sophisticated evasion tactics.
4. Implications and Strategic Risks
The development of these malware campaigns could signal a shift in threat actor focus towards macOS platforms, potentially leading to increased vulnerabilities and exploitation in the future.
- Political / Geopolitical: Potential for increased cyber tensions if state actors are involved or implicated.
- Security / Counter-Terrorism: Enhanced threat landscape for macOS users, necessitating improved security measures.
- Cyber / Information Space: Increased sophistication in malware targeting macOS could lead to broader adoption of similar tactics across platforms.
- Economic / Social: Financial losses for individuals and businesses could erode trust in digital security and macOS platforms.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Increase monitoring of macOS environments; educate users on social engineering risks; enhance detection capabilities for infostealers.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms for threat intelligence sharing; invest in macOS-specific security training and tools.
- Scenario Outlook:
- Best: Improved defenses lead to reduced impact of future attacks.
- Worst: Escalation in attack sophistication overwhelms current defenses.
- Most-Likely: Continued targeting of macOS with incremental improvements in security posture.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
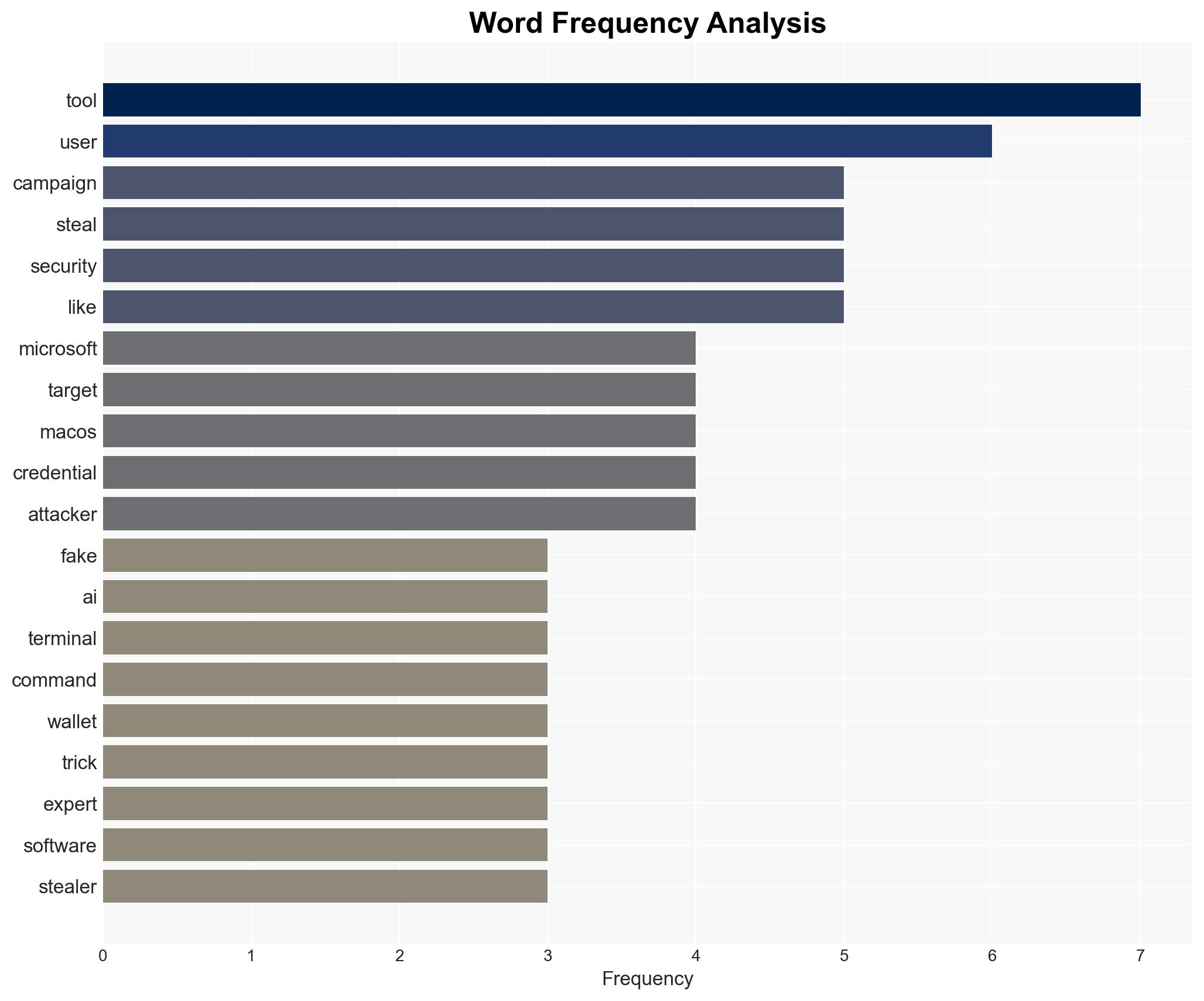
cybersecurity, macOS, infostealers, social engineering, threat actors, malware campaigns, digital security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us