Mandiant alerts to ongoing exploitation of patched WinRAR vulnerability by state-sponsored and financial hack…
Published on: 2026-01-28
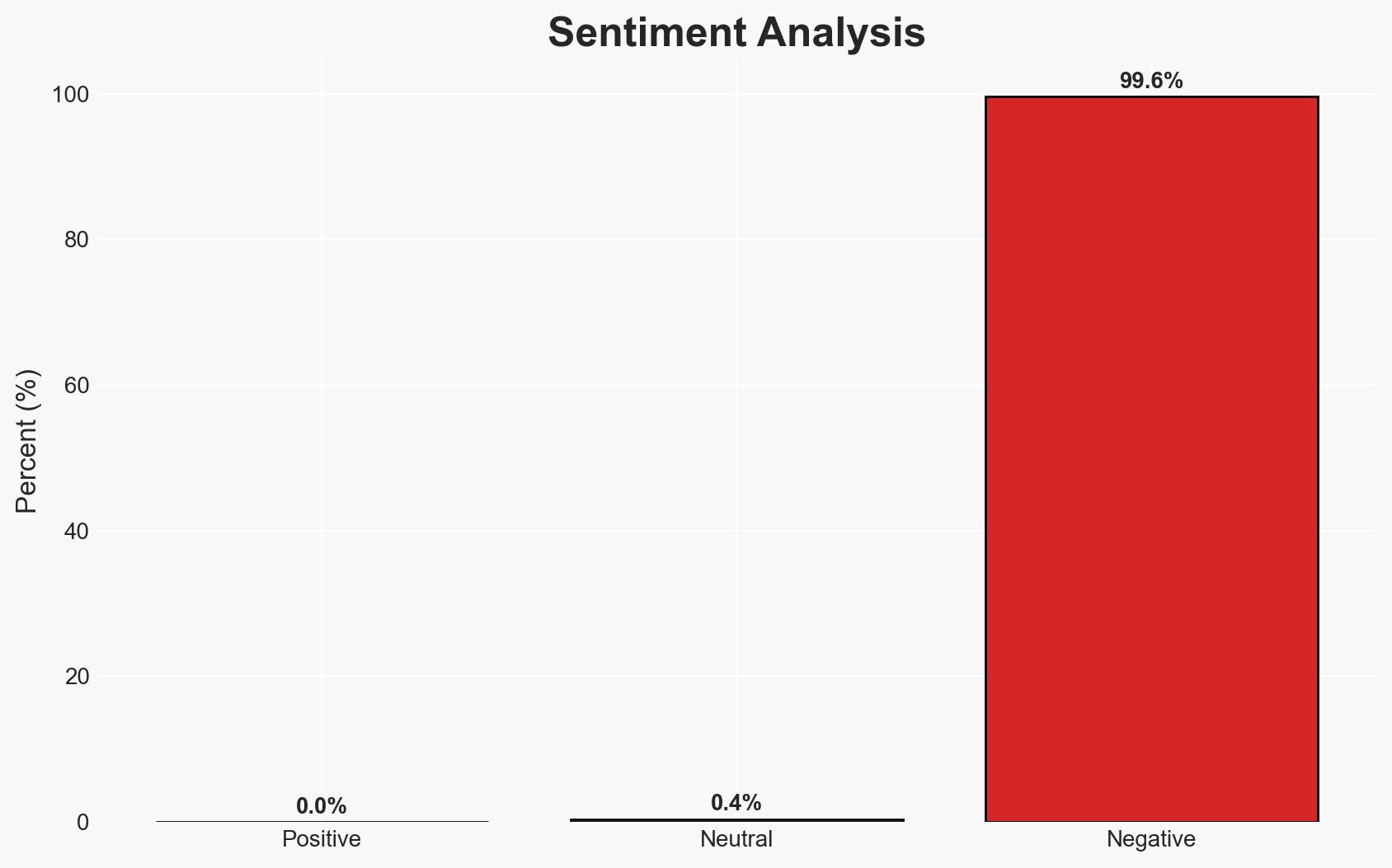
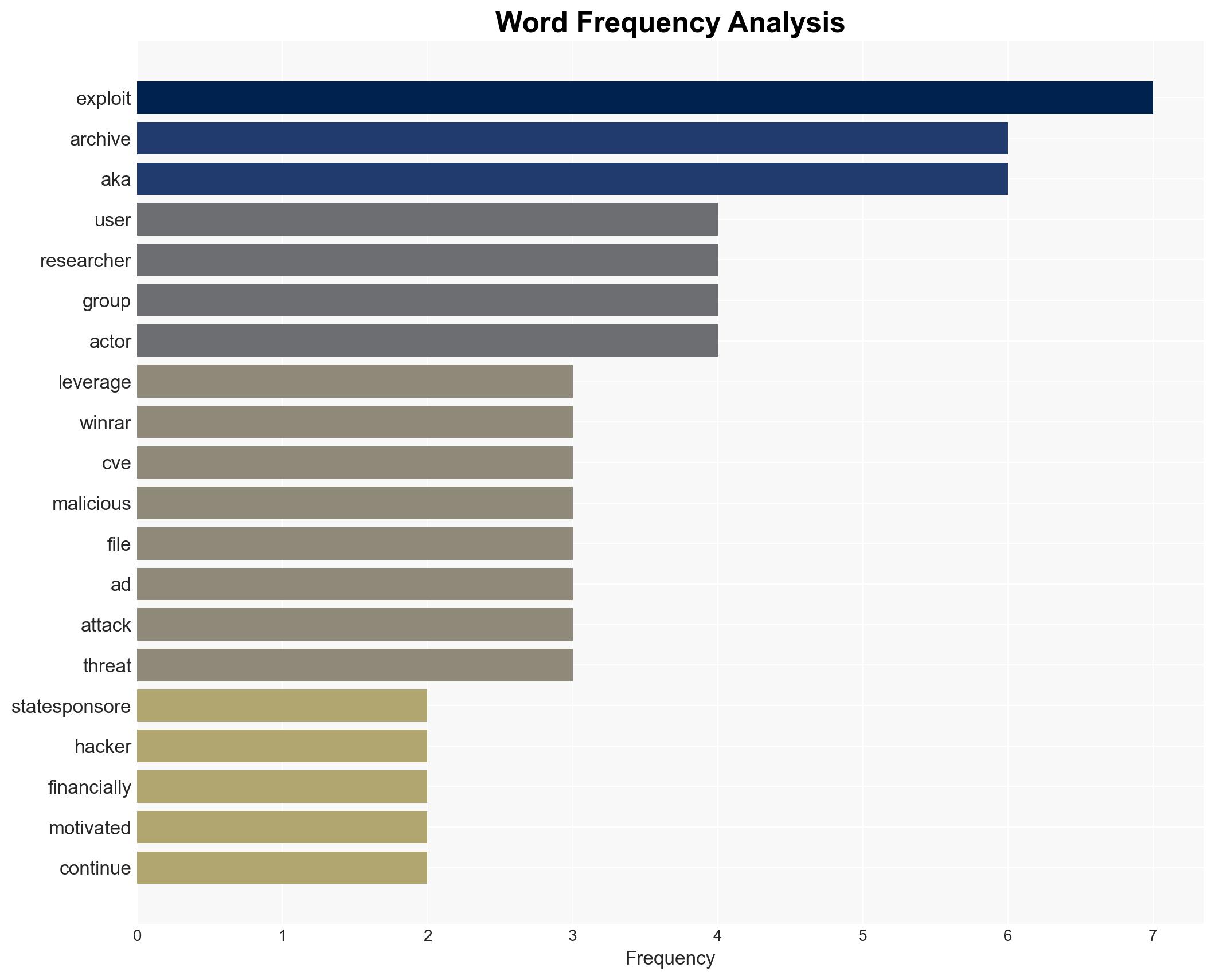
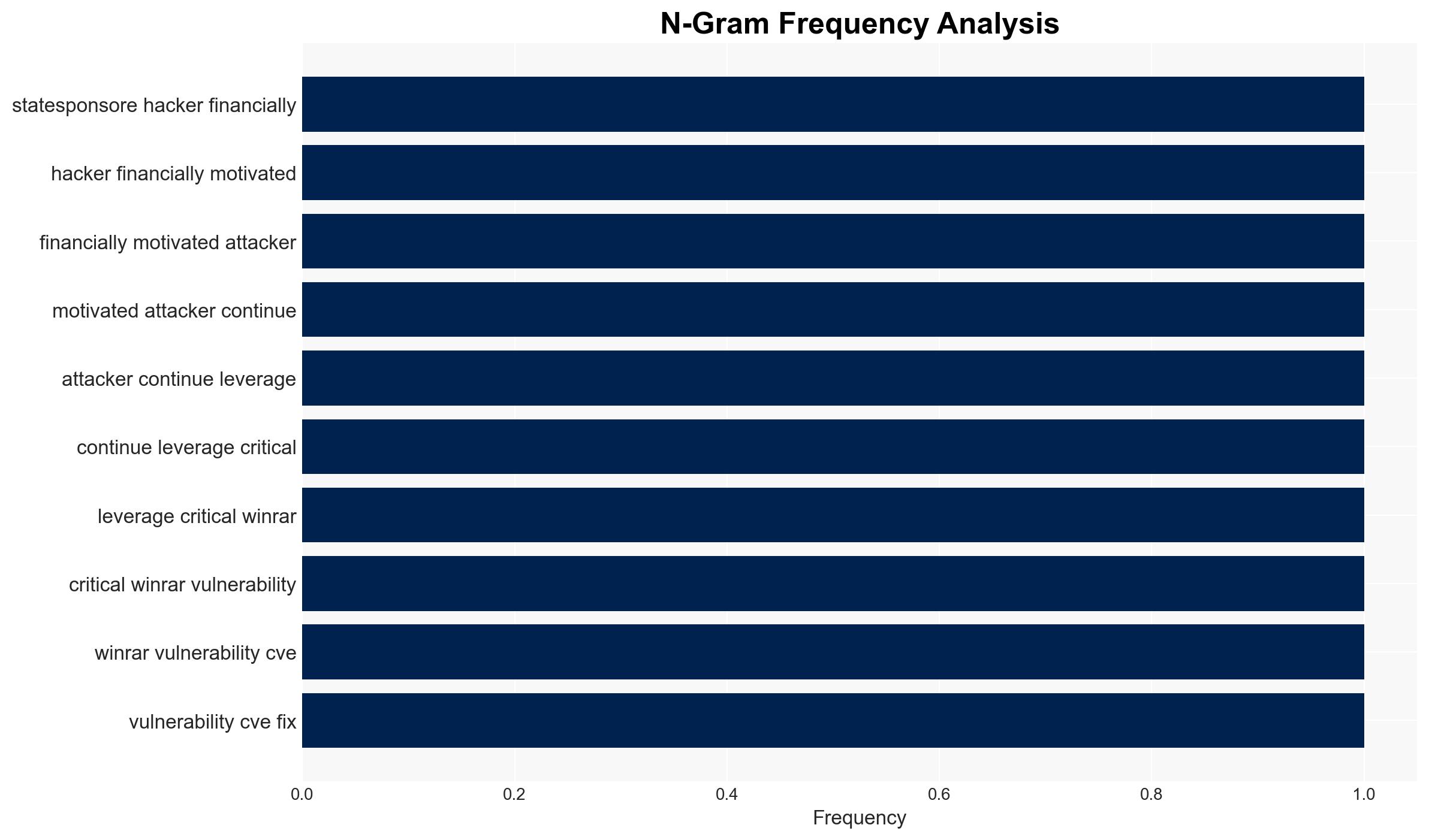
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: WinRAR vulnerability still a go-to tool for hackers Mandiant warns
1. BLUF (Bottom Line Up Front)
The WinRAR vulnerability CVE-2025-8088 remains actively exploited by both state-sponsored and financially motivated threat actors, despite a patch being available. The vulnerability’s exploitation is facilitated by exploit suppliers, reducing technical barriers for attackers. This situation poses ongoing risks to a wide range of sectors globally. Overall confidence in this assessment is moderate due to the reliance on open-source reporting and potential information gaps.
2. Competing Hypotheses
- Hypothesis A: The continued exploitation of CVE-2025-8088 is primarily driven by state-sponsored actors seeking to conduct cyber espionage. This is supported by the involvement of Russian and Chinese nexus APTs targeting geopolitical adversaries. However, the presence of financially motivated groups exploiting the same vulnerability suggests a broader utilization.
- Hypothesis B: The exploitation of CVE-2025-8088 is predominantly driven by financially motivated actors, with state-sponsored groups being opportunistic users. The diverse range of targets, including financial institutions and the hospitality sector, supports this hypothesis, although the involvement of state actors cannot be discounted.
- Assessment: Hypothesis A is currently better supported due to the strategic nature of the targets and the involvement of known state-sponsored groups. Indicators such as increased targeting of geopolitical adversaries could further support this hypothesis.
3. Key Assumptions and Red Flags
- Assumptions: The vulnerability remains unpatched in a significant number of systems; threat actors have continued access to exploit tools; state-sponsored actors prioritize geopolitical targets.
- Information Gaps: Specific details on the distribution of unpatched systems; comprehensive attribution of all actors exploiting the vulnerability; full scope of the exploit supplier network.
- Bias & Deception Risks: Potential bias in attributing attacks to state actors; reliance on open-source reporting may omit classified insights; deception by threat actors to obscure true motivations.
4. Implications and Strategic Risks
The persistent exploitation of CVE-2025-8088 could lead to increased geopolitical tensions, particularly if state-sponsored attacks are perceived as acts of aggression. The vulnerability’s exploitation may also embolden financially motivated groups, increasing cybercrime rates.
- Political / Geopolitical: Escalation of cyber conflicts involving state actors, potential diplomatic fallout.
- Security / Counter-Terrorism: Heightened threat environment for targeted sectors, increased demand for cybersecurity measures.
- Cyber / Information Space: Potential for widespread data breaches, increased misinformation campaigns leveraging compromised data.
- Economic / Social: Disruption to targeted industries, financial losses, erosion of trust in digital systems.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Encourage rapid patching of vulnerable systems, enhance monitoring for indicators of compromise, engage with cybersecurity partners for intelligence sharing.
- Medium-Term Posture (1–12 months): Develop resilience measures, strengthen public-private partnerships, invest in cybersecurity training and awareness programs.
- Scenario Outlook:
- Best: Rapid patch adoption reduces exploitation, leading to decreased attack frequency.
- Worst: Exploitation leads to significant geopolitical conflict and economic disruption.
- Most-Likely: Continued exploitation with periodic high-profile incidents, gradual improvement in patch adoption.
6. Key Individuals and Entities
- RomCom (aka Storm-0978)
- Paper Werewolf (aka Goffee)
- Sandworm (aka APT44)
- Trula (aka Secret Blizzard)
- TEMP.Armageddon (aka CARPATHIAN)
- zeroplayer (exploit supplier)
- BI.ZONE researchers
- Mandiant researchers
7. Thematic Tags
cybersecurity, cyber-espionage, state-sponsored threats, vulnerability exploitation, financial cybercrime, geopolitical tensions, information security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us