Mandiant Discovers Vishing Attacks Mimicking ShinyHunters to Compromise SaaS Platforms and Steal MFA Credenti…
Published on: 2026-01-31
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Mandiant Finds ShinyHunters-Style Vishing Attacks Stealing MFA to Breach SaaS Platforms
1. BLUF (Bottom Line Up Front)
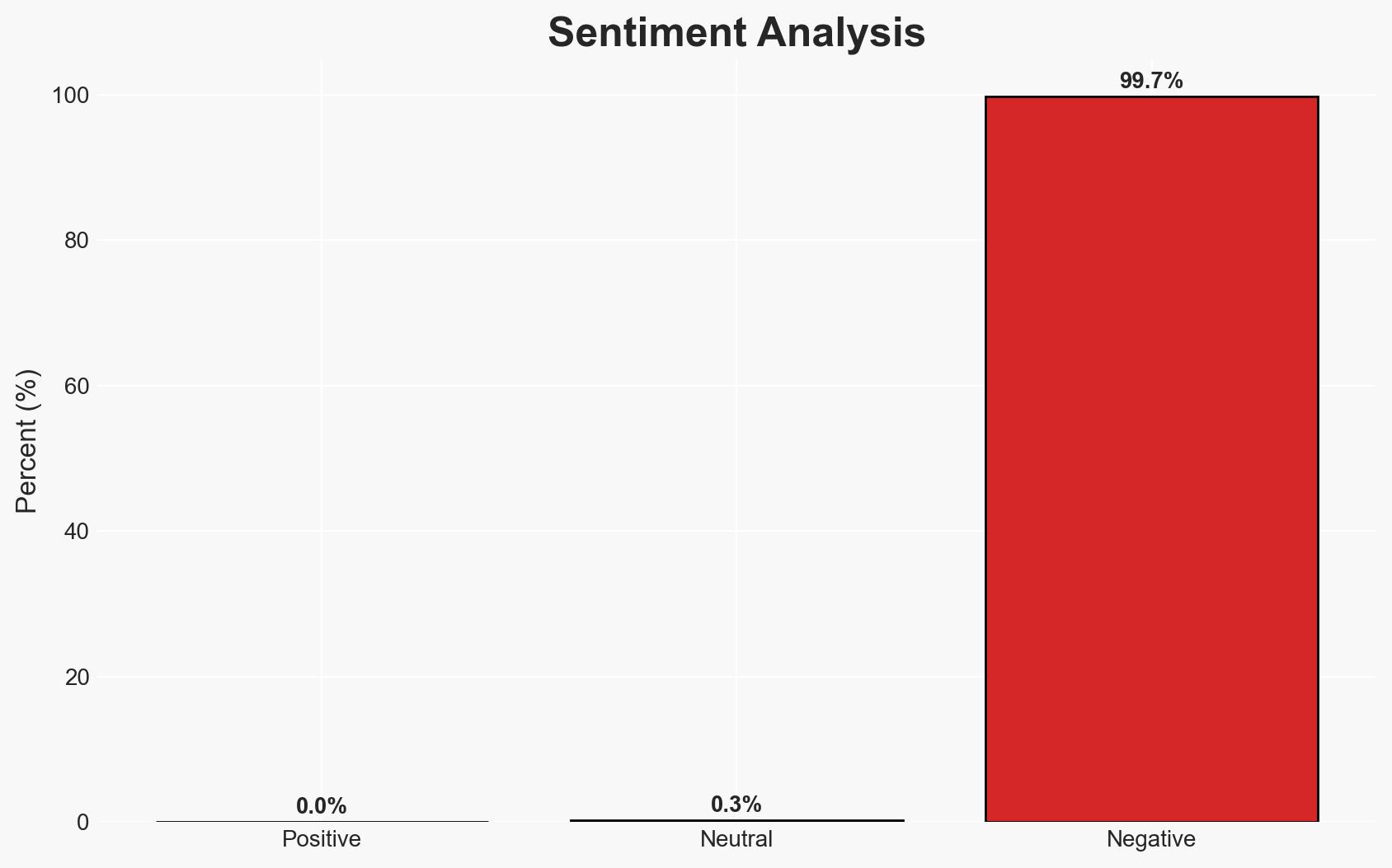
Mandiant has identified an increase in vishing attacks by groups resembling ShinyHunters, targeting SaaS platforms to steal sensitive data and extort victims. The attacks exploit SSO credentials and MFA codes through impersonation and phishing tactics. The primary hypothesis is that these are financially motivated cybercriminals expanding their operations. This assessment is made with moderate confidence due to the evolving nature of the threat actors and their tactics.
2. Competing Hypotheses
- Hypothesis A: The attacks are conducted by financially motivated cybercriminals, specifically ShinyHunters, expanding their operations to include more sophisticated vishing techniques. This is supported by the use of extortion tactics and the targeting of SaaS platforms, consistent with previous ShinyHunters activities. However, uncertainties remain regarding the full scope of their capabilities and the potential involvement of other groups.
- Hypothesis B: The attacks could be the work of new or evolving threat actors mimicking ShinyHunters’ tactics to obscure their identity and intentions. This is supported by the use of similar tradecraft but different domain registrars, suggesting potential deception. Contradictory evidence includes the lack of distinct new tactics that would clearly differentiate these actors from ShinyHunters.
- Assessment: Hypothesis A is currently better supported due to the consistency in tactics and objectives with known ShinyHunters activities. Key indicators that could shift this judgment include the emergence of distinct new tactics or confirmed attribution to different threat actors.
3. Key Assumptions and Red Flags
- Assumptions: The primary actors are financially motivated; the attacks are primarily targeting SaaS platforms; the use of vishing is a deliberate evolution of tactics.
- Information Gaps: Detailed attribution of the threat actors; comprehensive understanding of their operational capabilities and infrastructure.
- Bias & Deception Risks: Potential confirmation bias in attributing activities to ShinyHunters; risk of deception through mimicry by other groups.
4. Implications and Strategic Risks
The expansion of these attacks could lead to increased vulnerability of SaaS platforms and broader implications for data security and corporate extortion. The evolution of tactics may influence other cybercriminal groups to adopt similar methods.
- Political / Geopolitical: Potential for increased tensions if state actors are suspected of involvement or if attacks impact critical infrastructure.
- Security / Counter-Terrorism: Heightened threat environment for organizations relying on SaaS platforms, necessitating improved security measures.
- Cyber / Information Space: Increased sophistication in phishing and vishing tactics could lead to more widespread adoption and adaptation by other threat actors.
- Economic / Social: Potential financial losses for affected companies and erosion of trust in SaaS platforms, impacting market stability.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of vishing and phishing activities; implement robust MFA and credential management practices; conduct awareness training for employees.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms for intelligence sharing; invest in advanced threat detection and response capabilities; strengthen regulatory frameworks for data protection.
- Scenario Outlook: Best: Effective countermeasures reduce attack success rates; Worst: Escalation in attack sophistication and frequency; Most-Likely: Continued adaptation of tactics by threat actors with moderate impact on targeted sectors.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
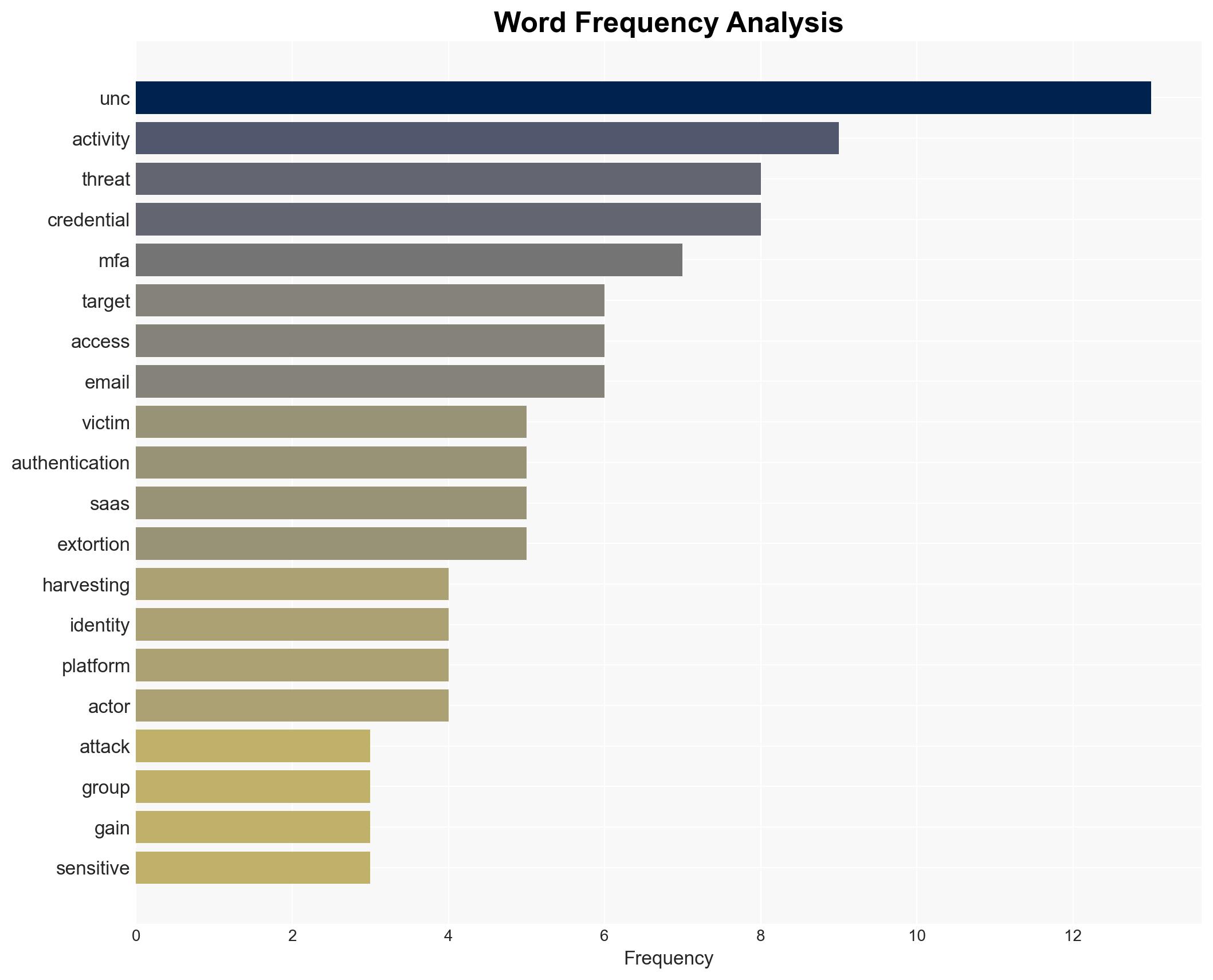
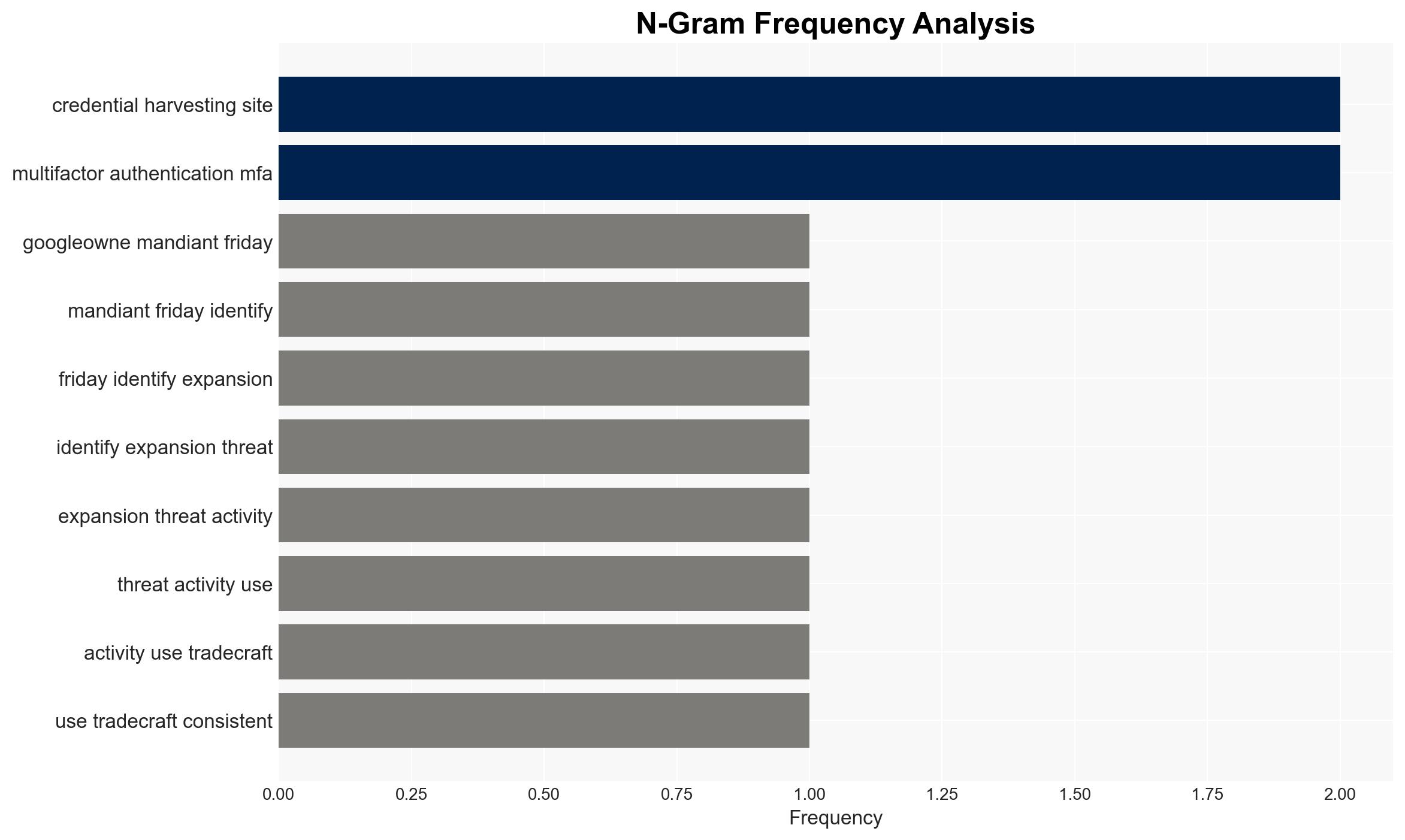
cybersecurity, vishing, SaaS platforms, ShinyHunters, extortion, MFA theft, cybercrime
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us