Mandiant reveals ShinyHunters exploit SSO through vishing and phishing to access cloud data.
Published on: 2026-01-31
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Mandiant details how ShinyHunters abuse SSO to steal cloud data
1. BLUF (Bottom Line Up Front)
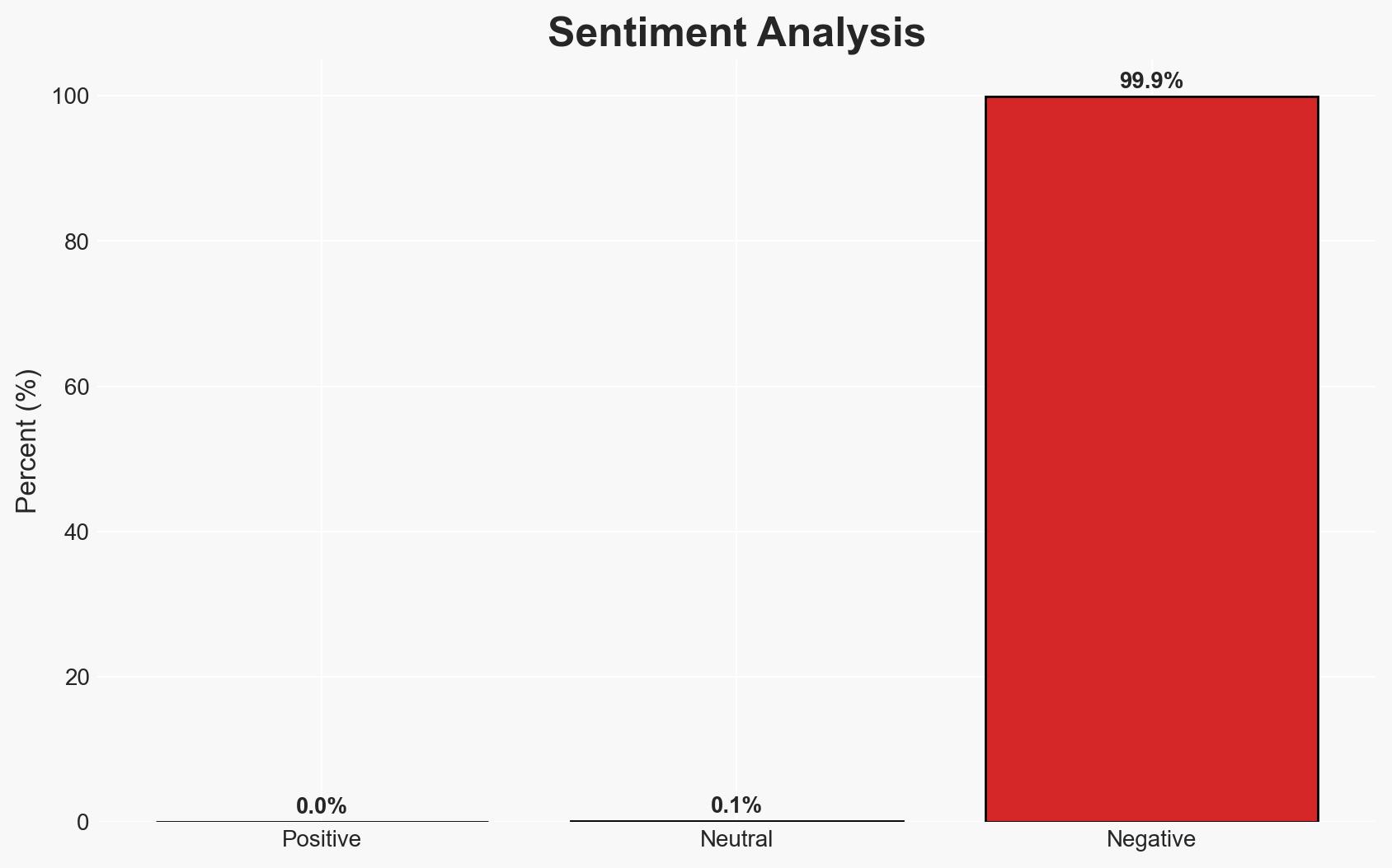
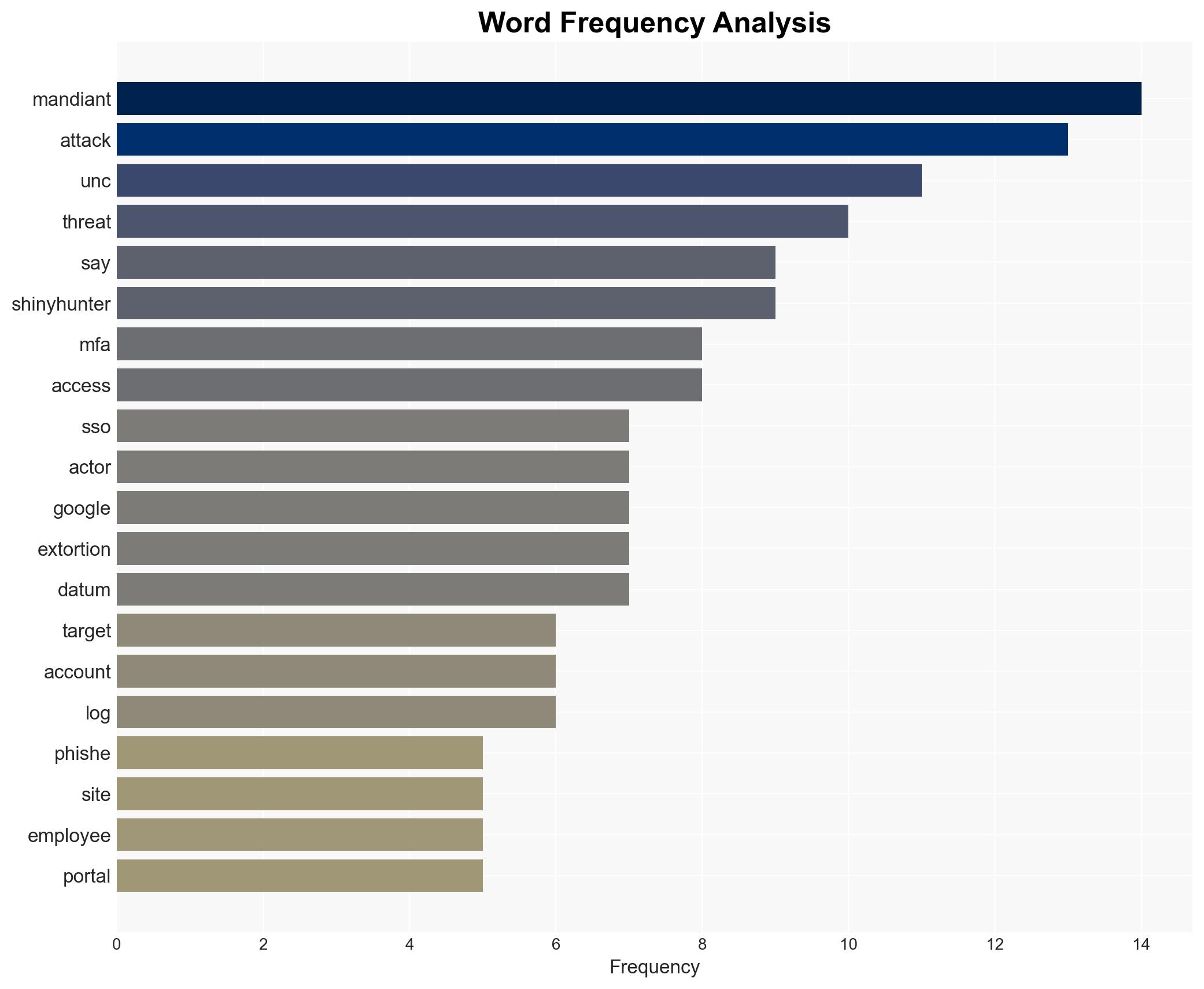
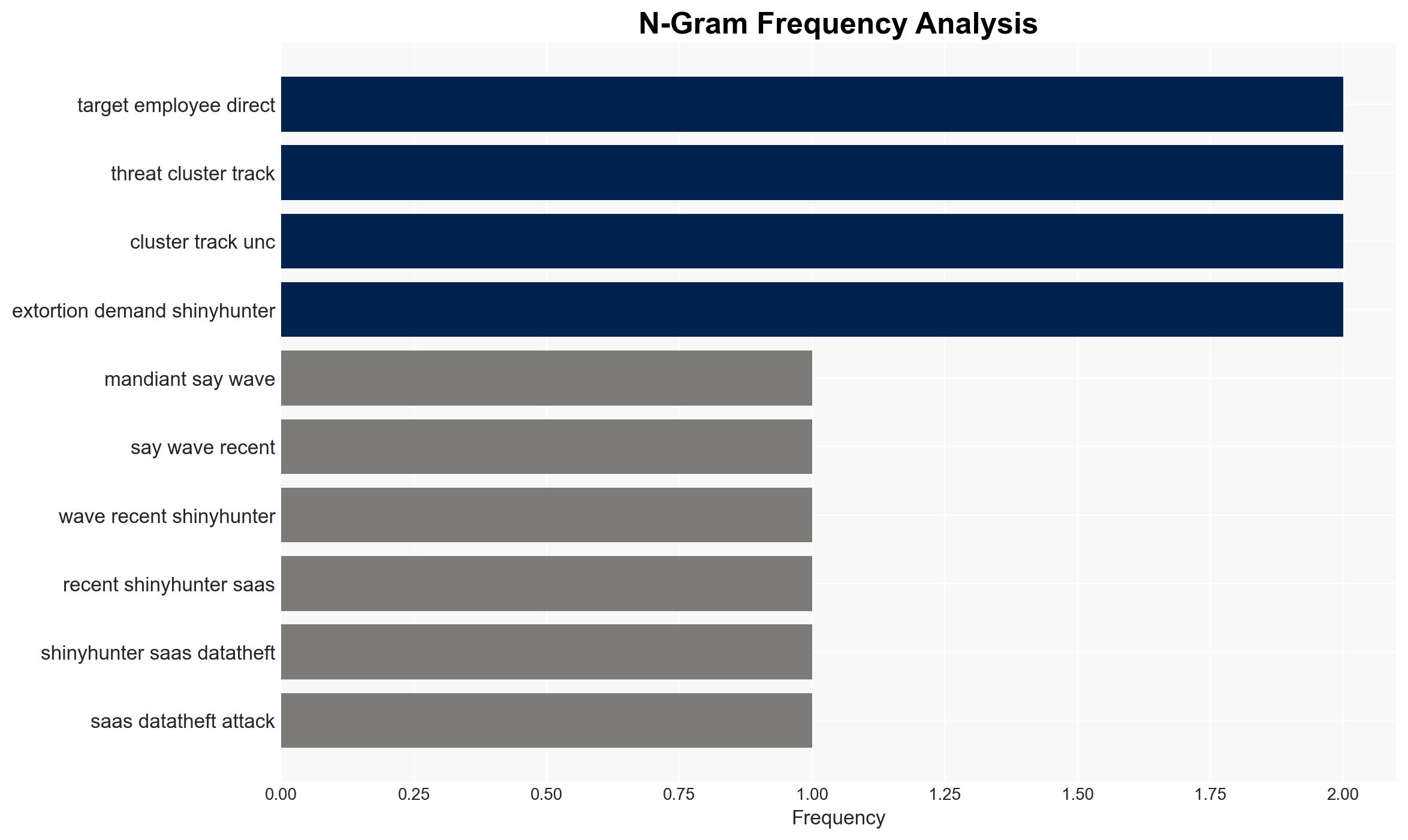
ShinyHunters are conducting sophisticated phishing attacks to compromise single sign-on (SSO) credentials and multi-factor authentication (MFA) codes, enabling access to cloud data across multiple SaaS platforms. This activity primarily targets Salesforce data but is opportunistic in nature. The threat is significant for organizations using SSO systems, with moderate confidence in the assessment due to potential information gaps and evolving threat tactics.
2. Competing Hypotheses
- Hypothesis A: ShinyHunters are primarily targeting Salesforce data as part of a focused campaign. This is supported by ShinyHunters’ own claims and the specific mention of Salesforce as a primary target. However, the opportunistic nature of the attacks suggests a broader scope, creating uncertainty about the true focus.
- Hypothesis B: ShinyHunters are opportunistically targeting any accessible SaaS data, with no specific focus on Salesforce. This is supported by Mandiant’s assessment of the attacks as opportunistic and the wide range of targeted applications. Contradicting evidence includes ShinyHunters’ claims of a primary focus on Salesforce.
- Assessment: Hypothesis B is currently better supported due to the broad range of applications accessed and Mandiant’s characterization of the attacks as opportunistic. Indicators that could shift this judgment include further evidence of targeted campaigns specifically against Salesforce or other SaaS platforms.
3. Key Assumptions and Red Flags
- Assumptions:
- ShinyHunters have the capability to continuously adapt their phishing tactics.
- Organizations are not universally implementing robust security awareness training.
- SSO systems remain a high-value target for cybercriminals.
- Threat actors can effectively impersonate IT staff without immediate detection.
- Information Gaps:
- Specific details on the success rate of these phishing attacks.
- Comprehensive data on the exact number of affected organizations.
- Bias & Deception Risks:
- Potential bias in threat actor claims regarding their primary targets.
- Deception risk in phishing tactics that exploit trust in IT staff.
4. Implications and Strategic Risks
The ongoing ShinyHunters attacks could lead to increased data breaches, impacting organizational trust and operational stability. The evolution of these tactics may influence broader cybersecurity strategies and regulatory responses.
- Political / Geopolitical: Potential for increased international cooperation on cybersecurity measures and policies.
- Security / Counter-Terrorism: Heightened alertness and adaptation in threat detection and response protocols.
- Cyber / Information Space: Escalation in phishing sophistication and potential for widespread data leaks.
- Economic / Social: Financial losses from data breaches and potential reputational damage to affected companies.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance employee training on phishing awareness, review and strengthen MFA policies, and monitor for suspicious login activities.
- Medium-Term Posture (1–12 months): Develop partnerships for threat intelligence sharing, invest in advanced phishing detection technologies, and conduct regular security audits.
- Scenario Outlook:
- Best: Organizations implement robust defenses, significantly reducing successful attacks.
- Worst: Phishing tactics evolve faster than defenses, leading to widespread data breaches.
- Most-Likely: Continued adaptation by both attackers and defenders, with intermittent breaches.
6. Key Individuals and Entities
- ShinyHunters (extortion group)
- Mandiant (cybersecurity firm)
- Google Threat Intelligence Group
- Okta (identity management service)
- BleepingComputer (reporting source)
7. Thematic Tags
cybersecurity, phishing, data theft, SSO vulnerabilities, cloud security, threat intelligence, cyber extortion
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us