Massive Data Leak Exposes Apple Google and Facebook Passwords – iPhone in Canada
Published on: 2025-06-20
Intelligence Report: Massive Data Leak Exposes Apple Google and Facebook Passwords – iPhone in Canada
1. BLUF (Bottom Line Up Front)
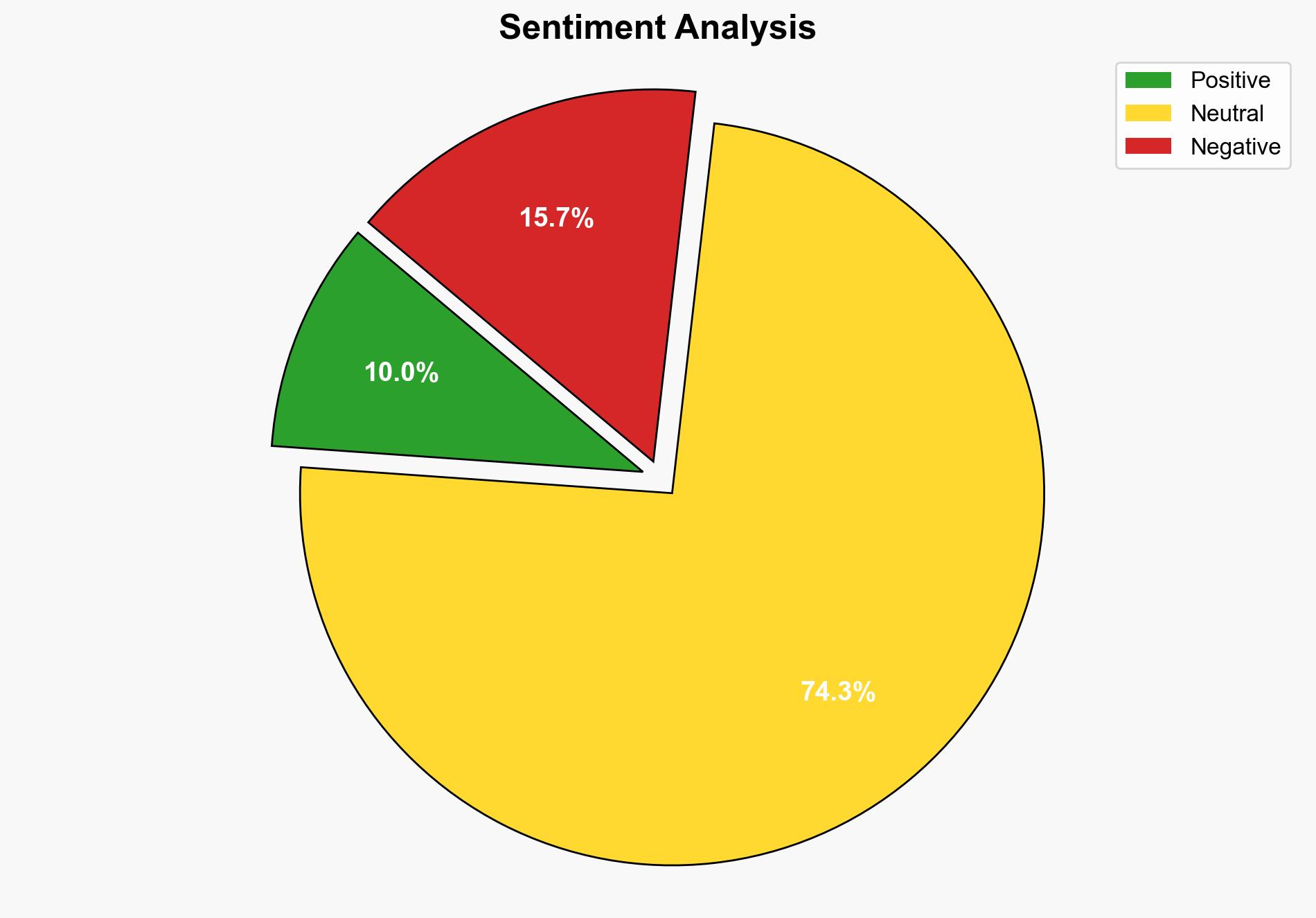
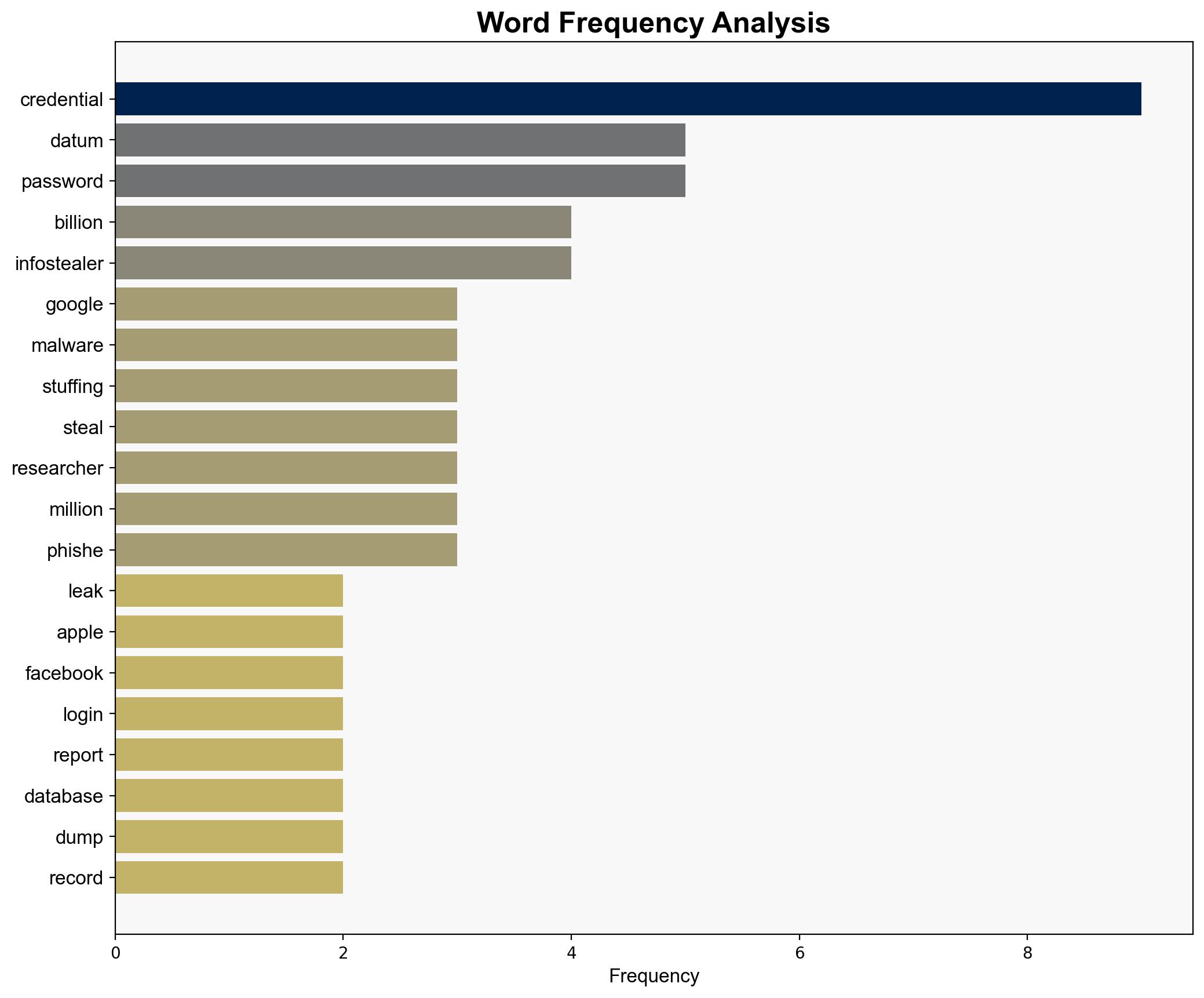
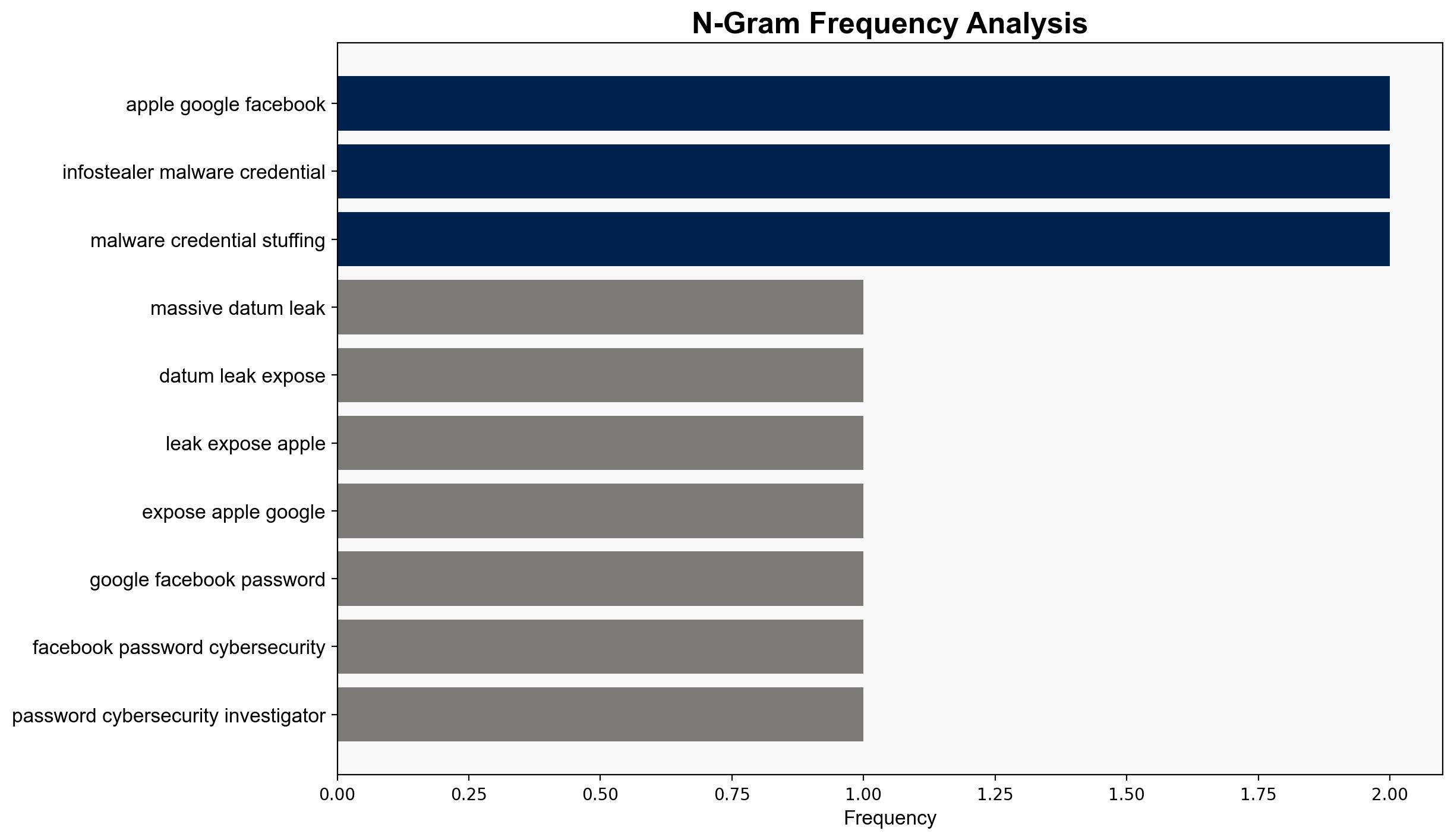
A significant data leak has exposed billions of login credentials from major platforms such as Apple, Google, and Facebook. This leak results from aggregation of previously compromised datasets, facilitated by infostealer malware and credential stuffing schemes. Immediate actions are required to mitigate potential threats, including identity theft and corporate espionage.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
Simulations indicate that cyber adversaries could exploit these credentials for unauthorized access to sensitive systems, leading to potential data breaches and financial theft.
Indicators Development
Key indicators include unusual login patterns, increased phishing attempts, and unauthorized access alerts. Monitoring these can aid in early threat detection.
Bayesian Scenario Modeling
Probabilistic models suggest a high likelihood of increased credential-based attacks in the coming months, with potential impacts on both individual and organizational security.
3. Implications and Strategic Risks
The leak poses significant risks across multiple domains. Politically, it could lead to tensions if government sites are compromised. Economically, the financial sector may face increased fraud attempts. Cybersecurity threats are likely to escalate, necessitating enhanced protective measures.
4. Recommendations and Outlook
- Immediate password changes and enabling multi-factor authentication (MFA) are critical for affected users.
- Organizations should employ advanced security tools, such as endpoint protection systems, and regularly update them.
- Scenario-based projections:
- Best Case: Rapid response and mitigation reduce the impact of the leak.
- Worst Case: Widespread exploitation leads to significant financial and reputational damage.
- Most Likely: Continued rise in credential-based attacks with moderate impact.
5. Key Individuals and Entities
Jeremiah Fowler (researcher) verified the database containing millions of records.
6. Thematic Tags
national security threats, cybersecurity, data breach, identity theft, credential stuffing