Match Group confirms data breach affecting Hinge, Tinder, OkCupid, and Match user information
Published on: 2026-01-29
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Match Group breach exposes data from Hinge Tinder OkCupid and Match
1. BLUF (Bottom Line Up Front)
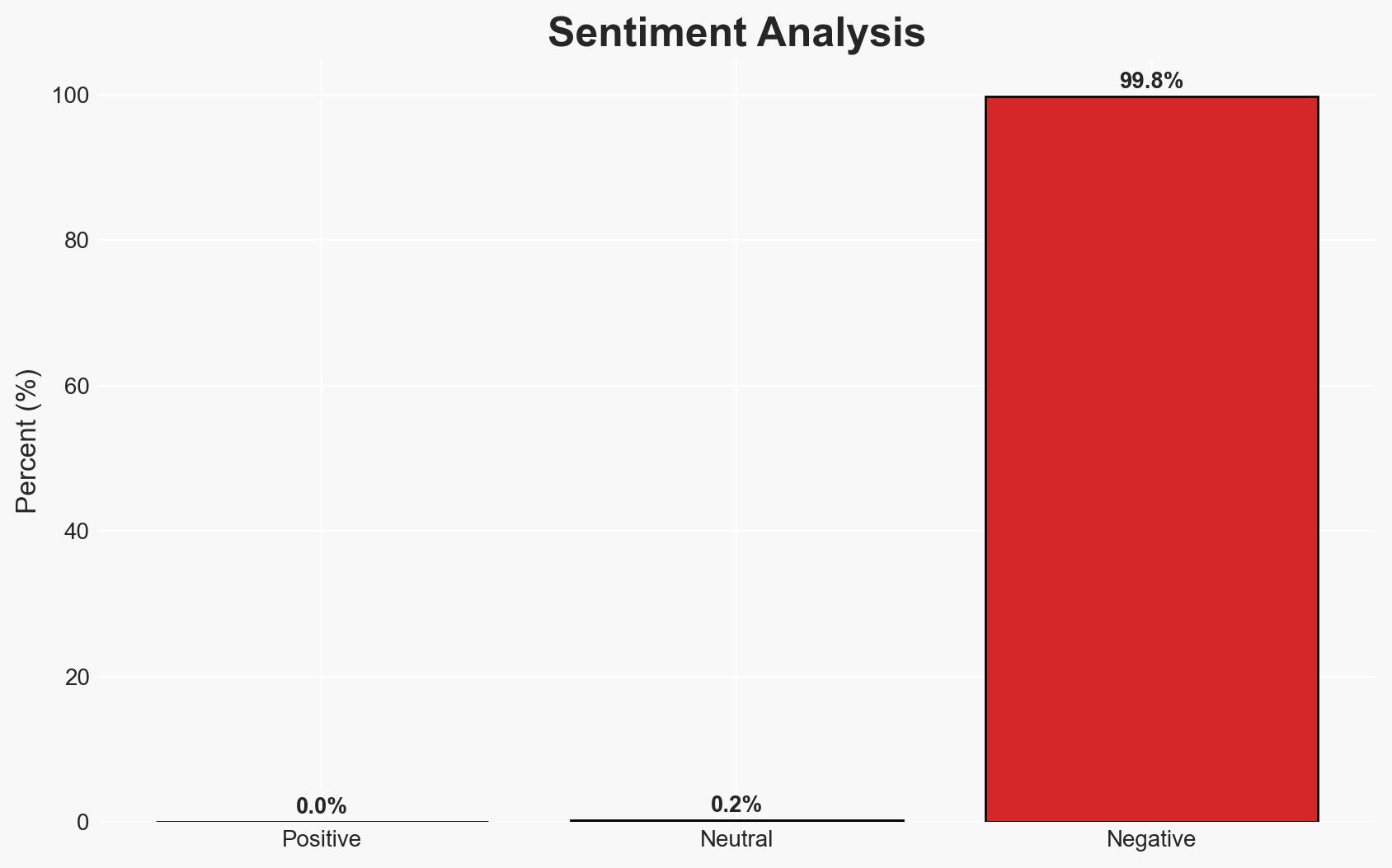
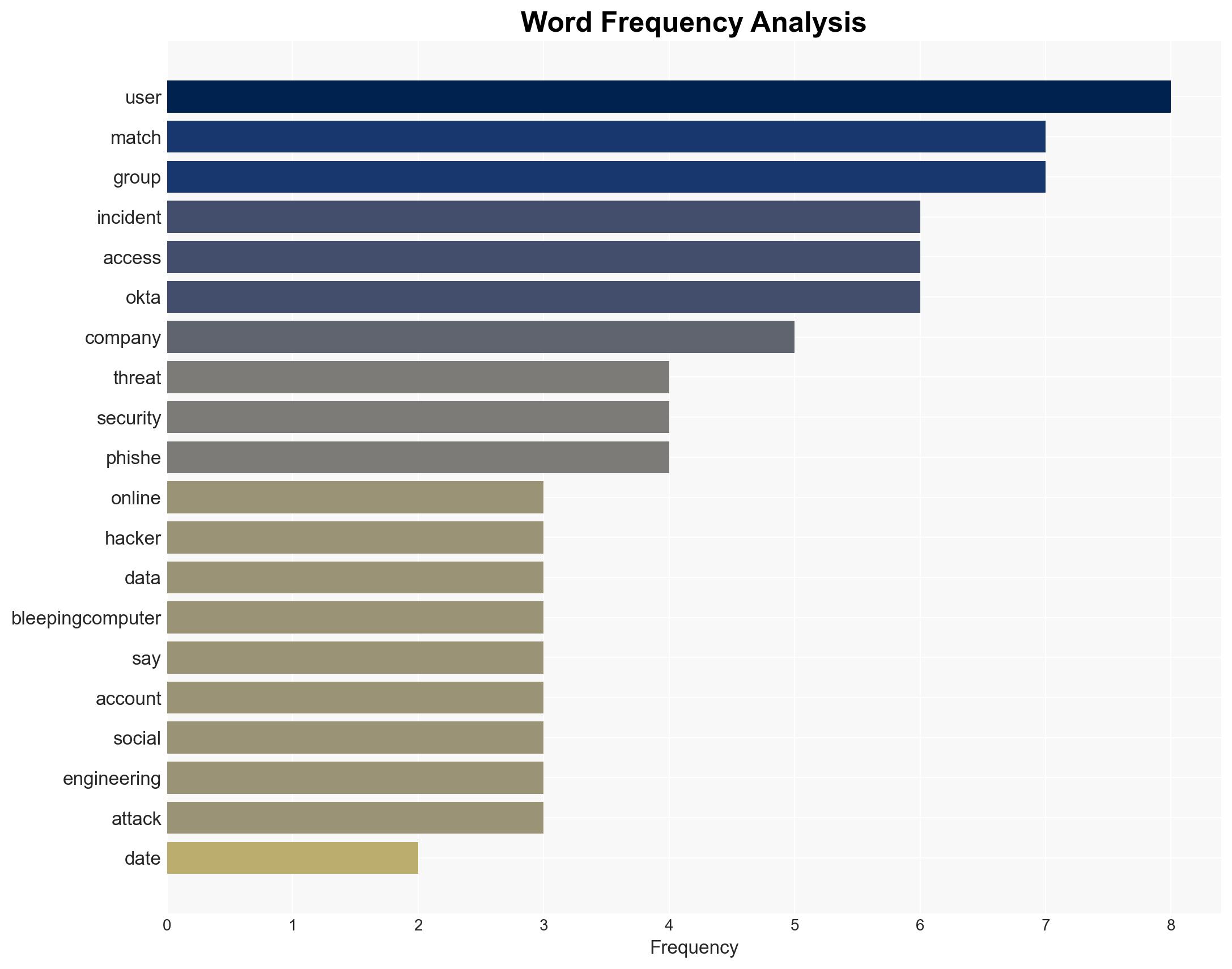
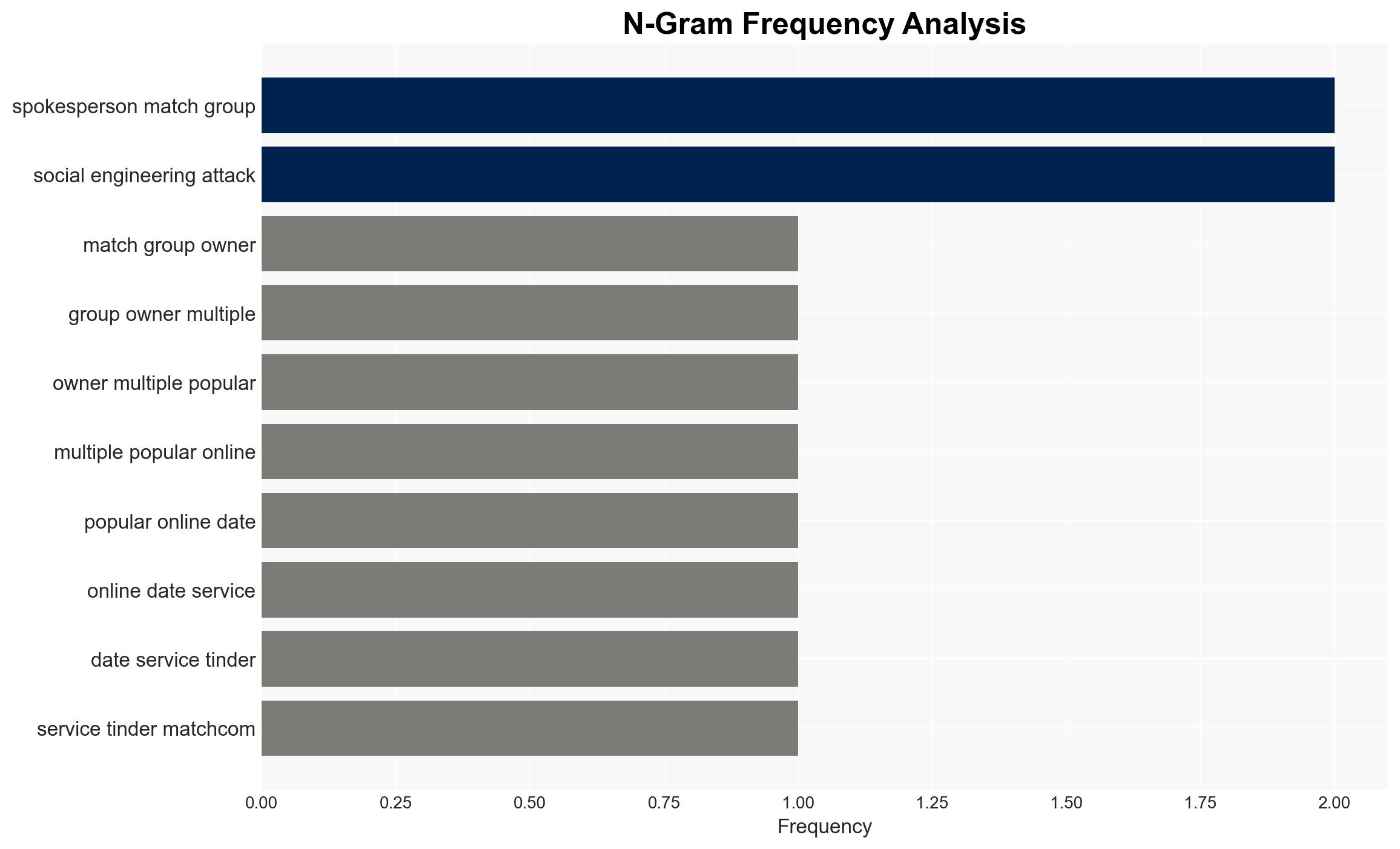
The Match Group has experienced a cybersecurity breach attributed to the ShinyHunters group, compromising user data from its platforms. The breach reportedly involved a limited amount of user data, with no access to log-in credentials or financial information. The most likely hypothesis is that the breach resulted from a compromised Okta SSO account. This incident highlights vulnerabilities in social engineering defenses. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: The breach was primarily due to a compromised Okta SSO account, which allowed access to Match Group’s cloud storage and marketing analytics. Supporting evidence includes the use of a phishing domain and the focus on SSO accounts. However, the exact method of compromise remains uncertain.
- Hypothesis B: The breach was a result of a broader systemic vulnerability within Match Group’s cybersecurity infrastructure. This hypothesis is less supported due to the lack of evidence indicating a widespread infrastructure failure.
- Assessment: Hypothesis A is currently better supported due to specific evidence of social engineering tactics targeting SSO accounts. Indicators that could shift this judgment include new information on internal security practices or additional breaches.
3. Key Assumptions and Red Flags
- Assumptions: The breach was limited in scope; the compromised data does not include sensitive financial or login information; Match Group’s response will mitigate further risk.
- Information Gaps: Details on the exact nature of the compromised data and the full extent of the breach remain unclear.
- Bias & Deception Risks: Potential bias in relying on company statements; possibility of underreporting the breach’s impact to protect corporate reputation.
4. Implications and Strategic Risks
This breach could lead to increased scrutiny of Match Group’s cybersecurity measures and influence broader industry standards for protecting user data.
- Political / Geopolitical: Potential regulatory actions or legislative changes concerning data protection and cybersecurity standards.
- Security / Counter-Terrorism: Increased risk of similar attacks on other high-value targets using social engineering tactics.
- Cyber / Information Space: Highlighting vulnerabilities in SSO systems and the need for enhanced phishing-resistant measures.
- Economic / Social: Possible loss of consumer trust in online dating platforms, impacting user engagement and revenue.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of SSO accounts, implement phishing-resistant MFA, and conduct a thorough security audit.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms for ongoing threat intelligence and resilience measures.
- Scenario Outlook: Best: Improved security measures prevent future breaches. Worst: Further breaches occur, leading to regulatory penalties. Most-Likely: Incremental improvements in security with occasional minor incidents.
6. Key Individuals and Entities
- Match Group
- ShinyHunters
- Okta
- Microsoft
- Charles Carmakal, Mandiant CTO
7. Thematic Tags
cybersecurity, data breach, social engineering, phishing, online privacy, user data protection, SSO vulnerabilities
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us