McDonalds in hot water after AI tool with laughably weak password 123456 gets hacked data of 64M job seekers exposed – The Times of India
Published on: 2025-07-12
Intelligence Report: McDonalds in hot water after AI tool with laughably weak password 123456 gets hacked data of 64M job seekers exposed – The Times of India
1. BLUF (Bottom Line Up Front)
The breach of McDonald’s AI hiring tool, McHire, due to a weak password, exposed the data of 64 million job seekers. This incident underscores the critical need for robust cybersecurity measures, especially in AI-driven platforms handling sensitive personal information. Immediate recommendations include revising security protocols and conducting comprehensive audits to prevent future breaches.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
Simulations indicate that cyber adversaries exploited weak authentication protocols, gaining unauthorized access to sensitive data. This highlights the necessity for stronger password policies and multi-factor authentication.
Indicators Development
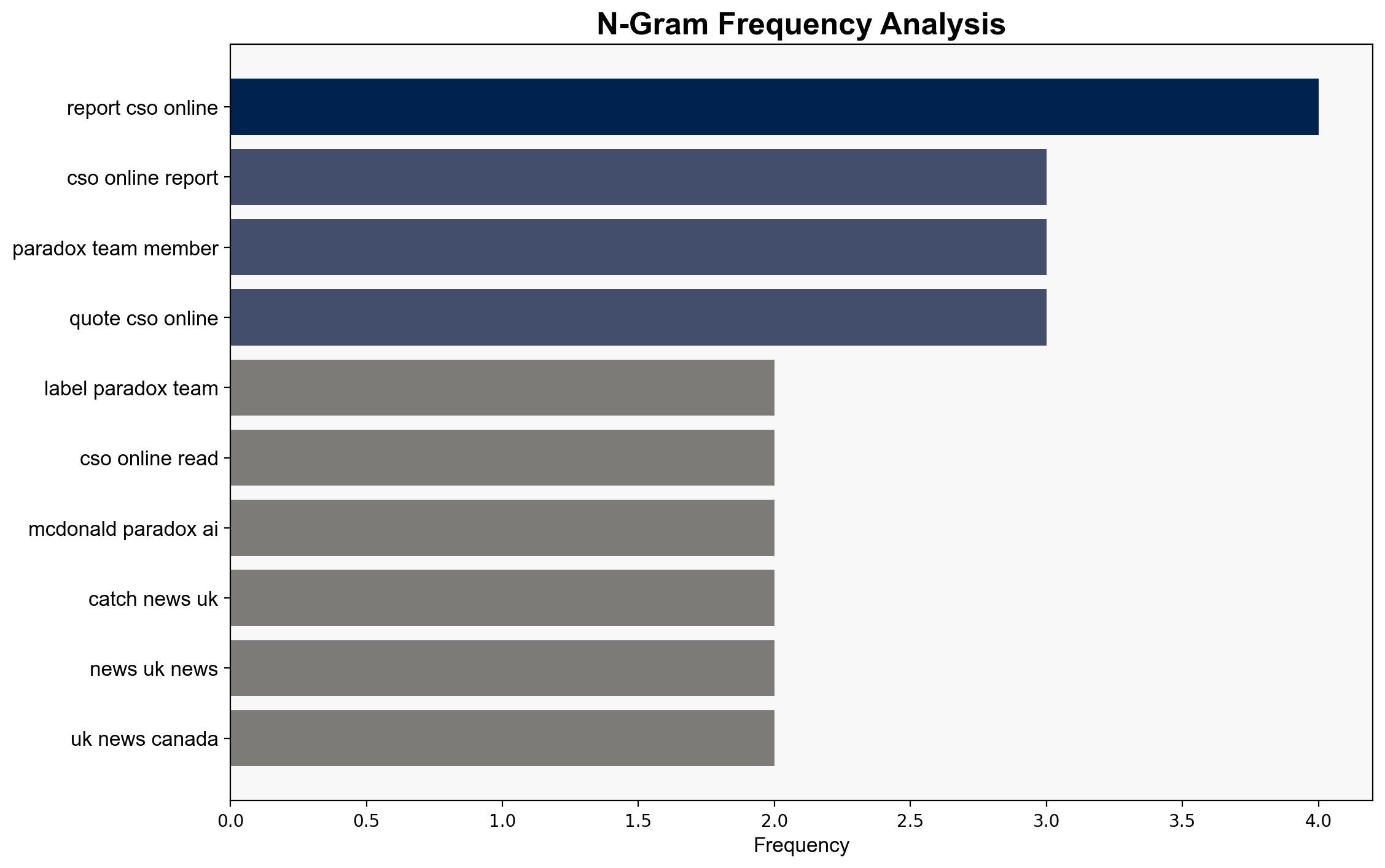
Behavioral anomalies, such as nonsensical responses from the AI chatbot Olivia, were early indicators of system compromise. Enhanced monitoring could facilitate earlier detection of such breaches.
Bayesian Scenario Modeling
Probabilistic models suggest a high likelihood of similar attacks if security measures remain unchanged, emphasizing the need for immediate intervention.
3. Implications and Strategic Risks
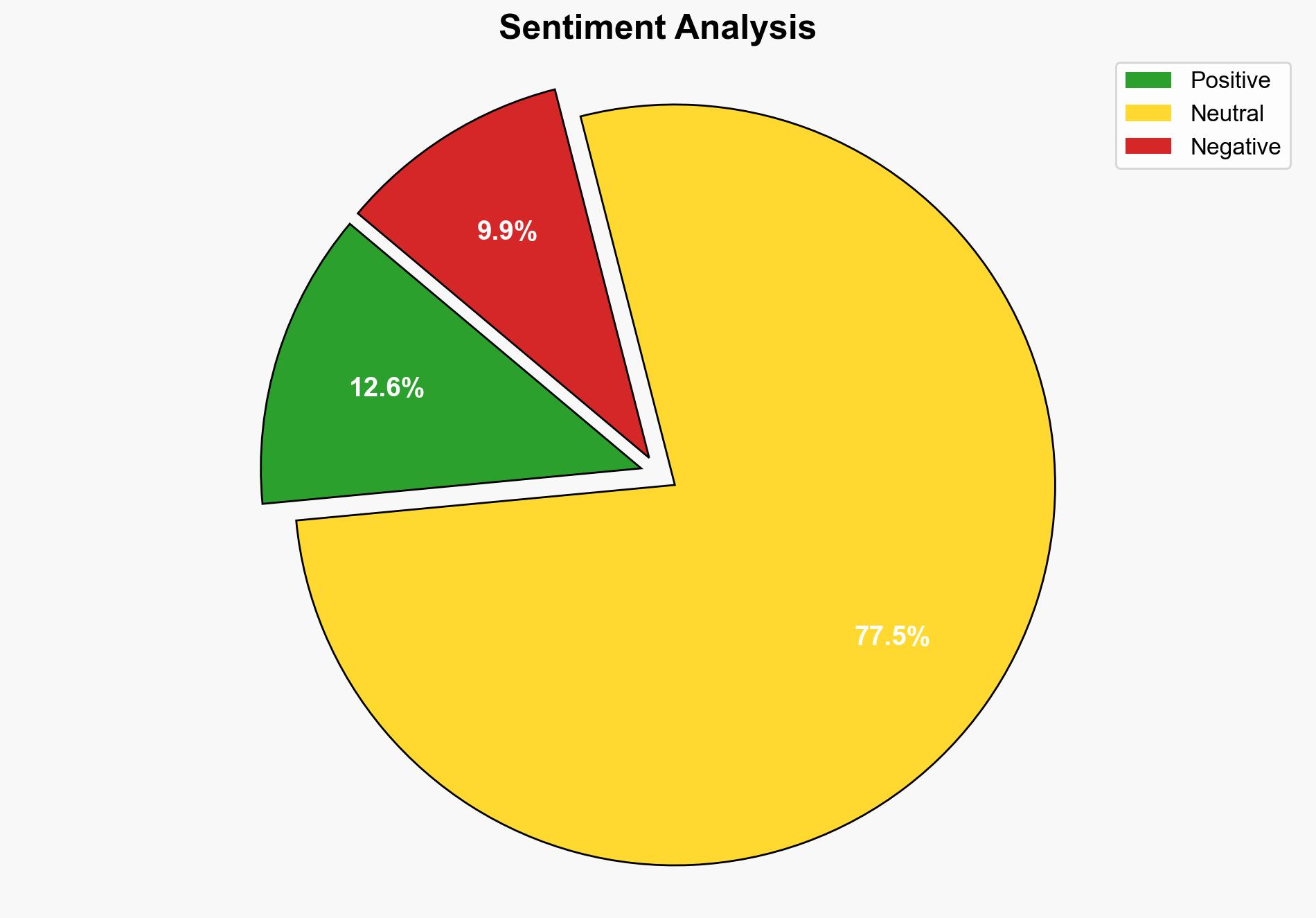
The breach presents significant risks, including potential identity theft and targeted phishing attacks. The exposure of personal data could lead to widespread social engineering campaigns, undermining trust in AI systems and potentially impacting McDonald’s brand reputation and customer loyalty.
4. Recommendations and Outlook
- Implement multi-factor authentication and enforce strong password policies across all platforms.
- Conduct regular security audits and vulnerability assessments to identify and mitigate potential risks.
- Develop a comprehensive incident response plan to address future breaches swiftly and effectively.
- Best Case: Enhanced security measures prevent future breaches, restoring stakeholder confidence.
- Worst Case: Continued vulnerabilities lead to further data breaches, resulting in legal and financial repercussions.
- Most Likely: Incremental improvements in security reduce the frequency of breaches but require ongoing vigilance.
5. Key Individuals and Entities
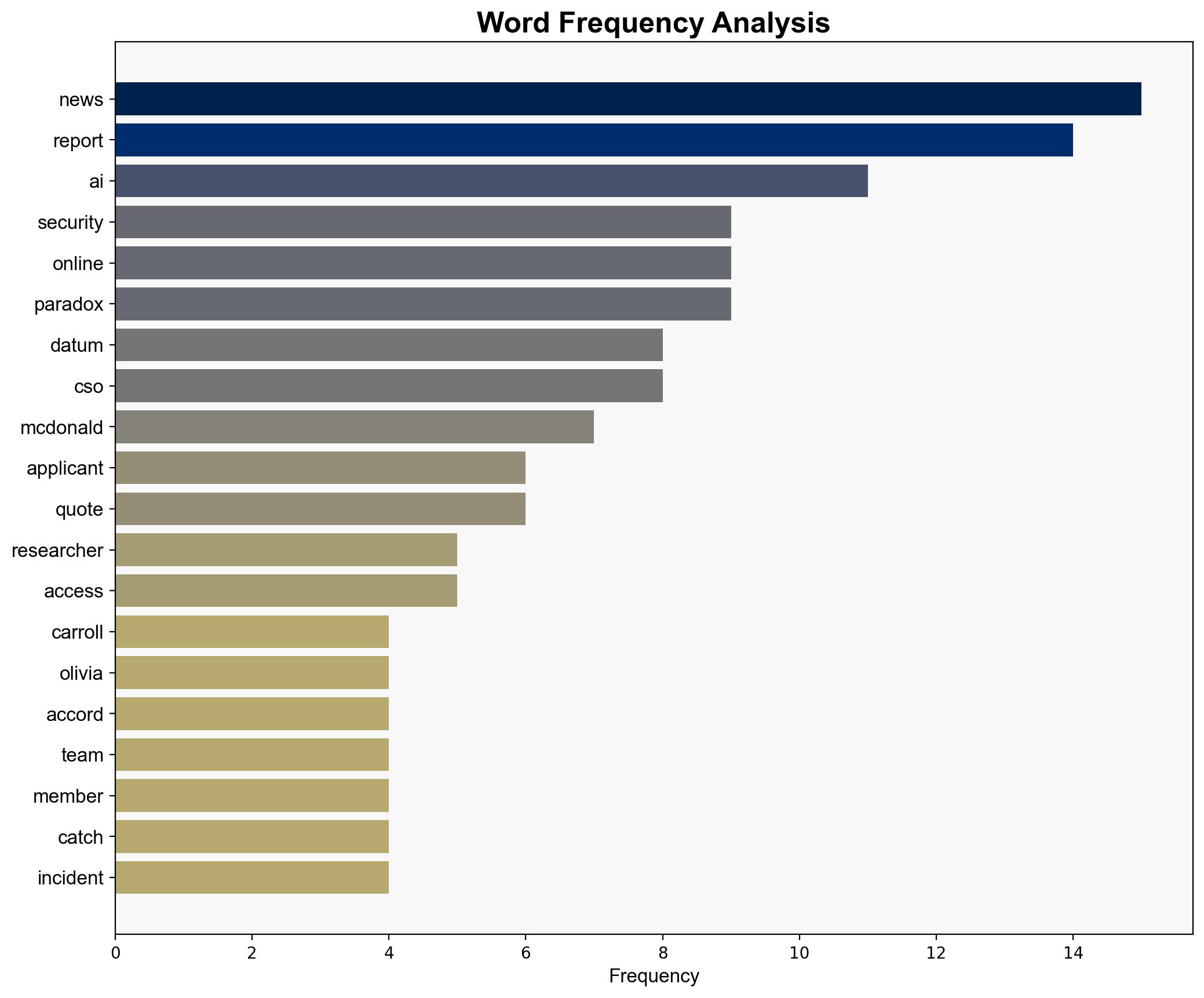
Ian Carroll, Sam Curry, Evan Dornbush, Aditi Gupta, Randolph Barr
6. Thematic Tags
cybersecurity, data breach, AI security, personal data protection, corporate responsibility