mcp-scan Real-Time Guardrail Monitoring and Dynamic Proxy for MCP Servers – Darknet.org.uk
Published on: 2025-11-17
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report:
1. BLUF (Bottom Line Up Front)
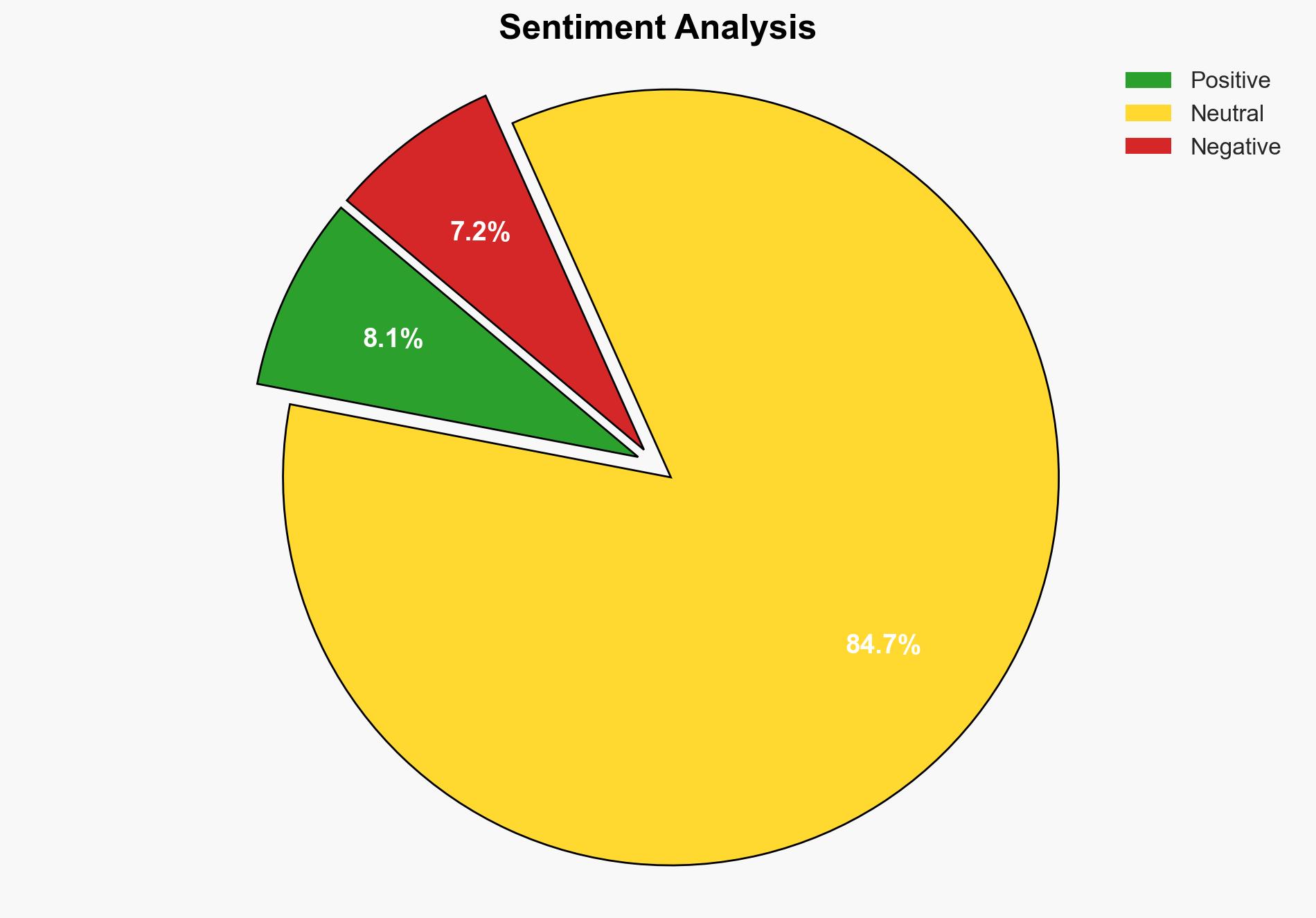
The mcpscan tool presents both a significant opportunity for enhancing cybersecurity through real-time monitoring and a potential risk if misused by malicious actors. The most supported hypothesis is that mcpscan is primarily intended for legitimate security purposes, but its capabilities could be exploited for malicious activities. Confidence Level: Moderate. Recommended action includes implementing strict access controls and continuous monitoring to prevent misuse.
2. Competing Hypotheses
Hypothesis 1: mcpscan is designed primarily for cybersecurity professionals to enhance security through real-time monitoring and dynamic proxy capabilities, helping to identify and mitigate vulnerabilities in MCP servers.
Hypothesis 2: mcpscan, while marketed as a security tool, could be repurposed by malicious actors to exploit vulnerabilities in MCP servers, facilitating unauthorized access and data exfiltration.
Hypothesis 1 is more likely due to the structured and transparent nature of the tool’s documentation and its alignment with common cybersecurity practices. However, the potential for misuse remains a concern, particularly given the tool’s advanced capabilities.
3. Key Assumptions and Red Flags
Assumptions include the belief that the tool’s developers have no malicious intent and that users will adhere to ethical guidelines. Red flags include the tool’s ability to intercept and modify live traffic, which could be exploited for malicious purposes. The lack of clear user authentication mechanisms could also pose a risk.
4. Implications and Strategic Risks
The tool’s capabilities could lead to cascading cyber threats if misused, including unauthorized access to sensitive data, lateral movement within networks, and potential cross-tenant access breaches. These risks could escalate into broader cybersecurity incidents, impacting organizational operations and reputations.
5. Recommendations and Outlook
- Implement strict access controls and authentication mechanisms for mcpscan usage.
- Conduct regular audits and monitoring of tool usage to detect and prevent misuse.
- Engage in continuous training for cybersecurity teams to effectively utilize mcpscan’s capabilities while mitigating risks.
- Best-case scenario: mcpscan enhances organizational security posture, effectively identifying and mitigating vulnerabilities.
- Worst-case scenario: Malicious actors exploit mcpscan to conduct sophisticated cyberattacks, leading to data breaches and reputational damage.
- Most-likely scenario: mcpscan is used primarily for legitimate purposes, with isolated incidents of misuse that are quickly detected and mitigated.
6. Key Individuals and Entities
No specific individuals are mentioned in the source text. The focus is on the tool and its potential users, including cybersecurity professionals and potentially malicious actors.
7. Thematic Tags
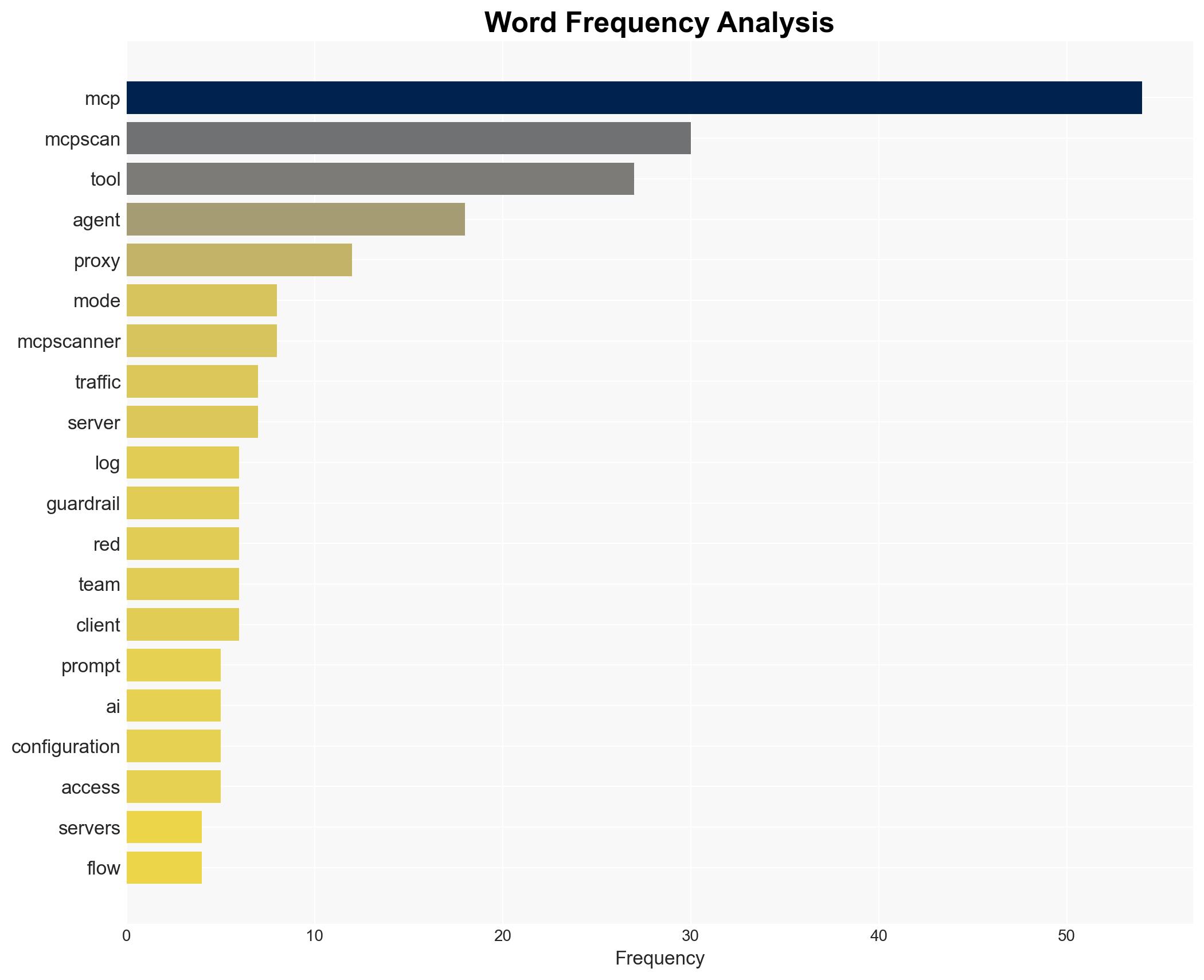
Cybersecurity, Real-Time Monitoring, Dynamic Proxy, MCP Servers, Vulnerability Mitigation, Red Teaming, Data Exfiltration
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Forecast futures under uncertainty via probabilistic logic.
- Network Influence Mapping: Map influence relationships to assess actor impact.
- Narrative Pattern Analysis: Deconstruct and track propaganda or influence narratives.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us
·