MCP Security Vulnerabilities and Attack Vectors – Forgecode.dev
Published on: 2025-07-19
Intelligence Report: MCP Security Vulnerabilities and Attack Vectors – Forgecode.dev
1. BLUF (Bottom Line Up Front)
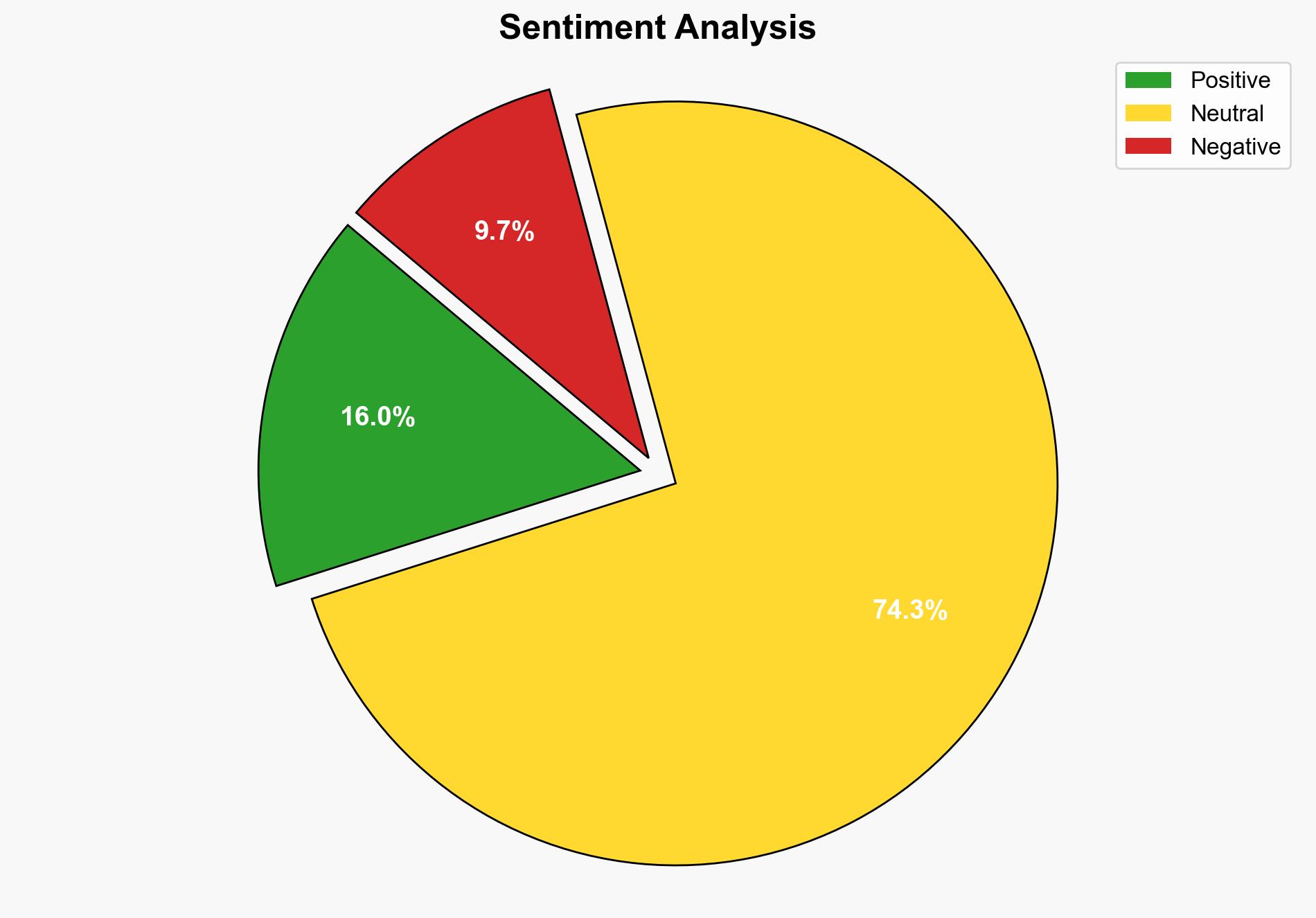
The MCP (Model Context Protocol) presents significant security vulnerabilities, primarily due to inadequate authentication measures and potential for tool description injection attacks. The lack of robust security practices in MCP implementations poses risks of unauthorized data access and manipulation. Immediate attention to authentication protocols and tool description sanitization is recommended to mitigate these threats.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
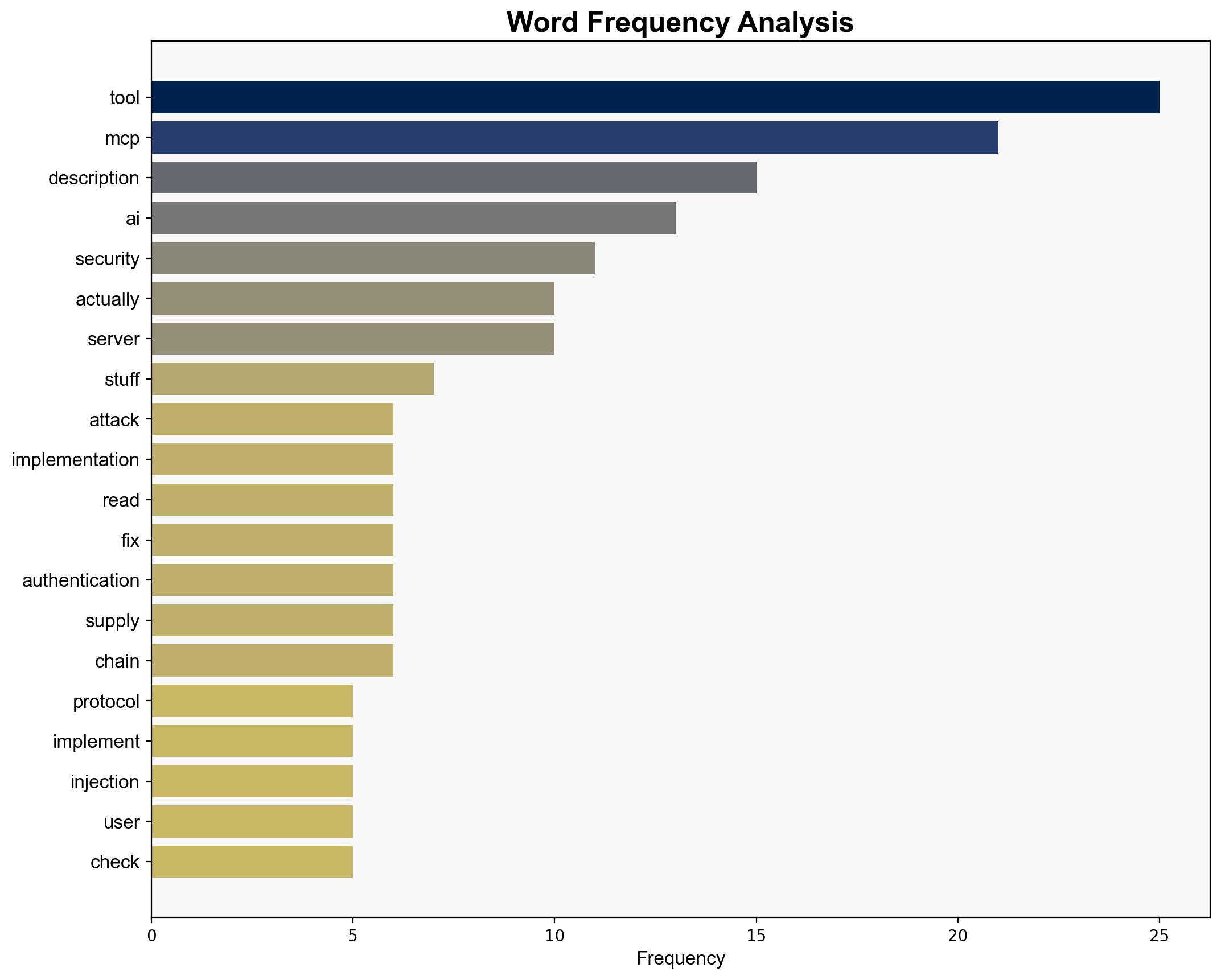
Simulations reveal that MCP implementations are susceptible to tool description injection, allowing adversaries to manipulate AI behavior and exfiltrate data.
Indicators Development
Key indicators include unsanitized tool descriptions and weak authentication checks, which can be monitored to detect potential breaches.
Bayesian Scenario Modeling
Probabilistic models suggest a high likelihood of exploitation through unauthenticated endpoints and supply chain vulnerabilities.
3. Implications and Strategic Risks
The vulnerabilities in MCP could lead to widespread data breaches, affecting both private and public sectors. The integration of MCP tools with AI systems amplifies the risk of unauthorized data manipulation, posing a threat to data integrity and confidentiality. These vulnerabilities could also facilitate supply chain attacks, further compromising system security.
4. Recommendations and Outlook
- Implement robust authentication mechanisms, such as OAuth, to secure MCP server interactions.
- Sanitize and validate tool descriptions to prevent injection attacks.
- Conduct regular security audits and code reviews to identify and rectify vulnerabilities.
- Best Case: Enhanced security measures lead to a significant reduction in successful attacks.
- Worst Case: Failure to address vulnerabilities results in major data breaches and loss of trust.
- Most Likely: Partial implementation of recommendations reduces risk but does not eliminate it entirely.
5. Key Individuals and Entities
Specific individuals are not mentioned in the source text. Focus remains on systemic vulnerabilities and organizational practices.
6. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus