Meet the 17-year-old who helped change Microsoft’s bug bounty program – TechSpot
Published on: 2025-07-03
Intelligence Report: Meet the 17-year-old who helped change Microsoft’s bug bounty program – TechSpot
1. BLUF (Bottom Line Up Front)
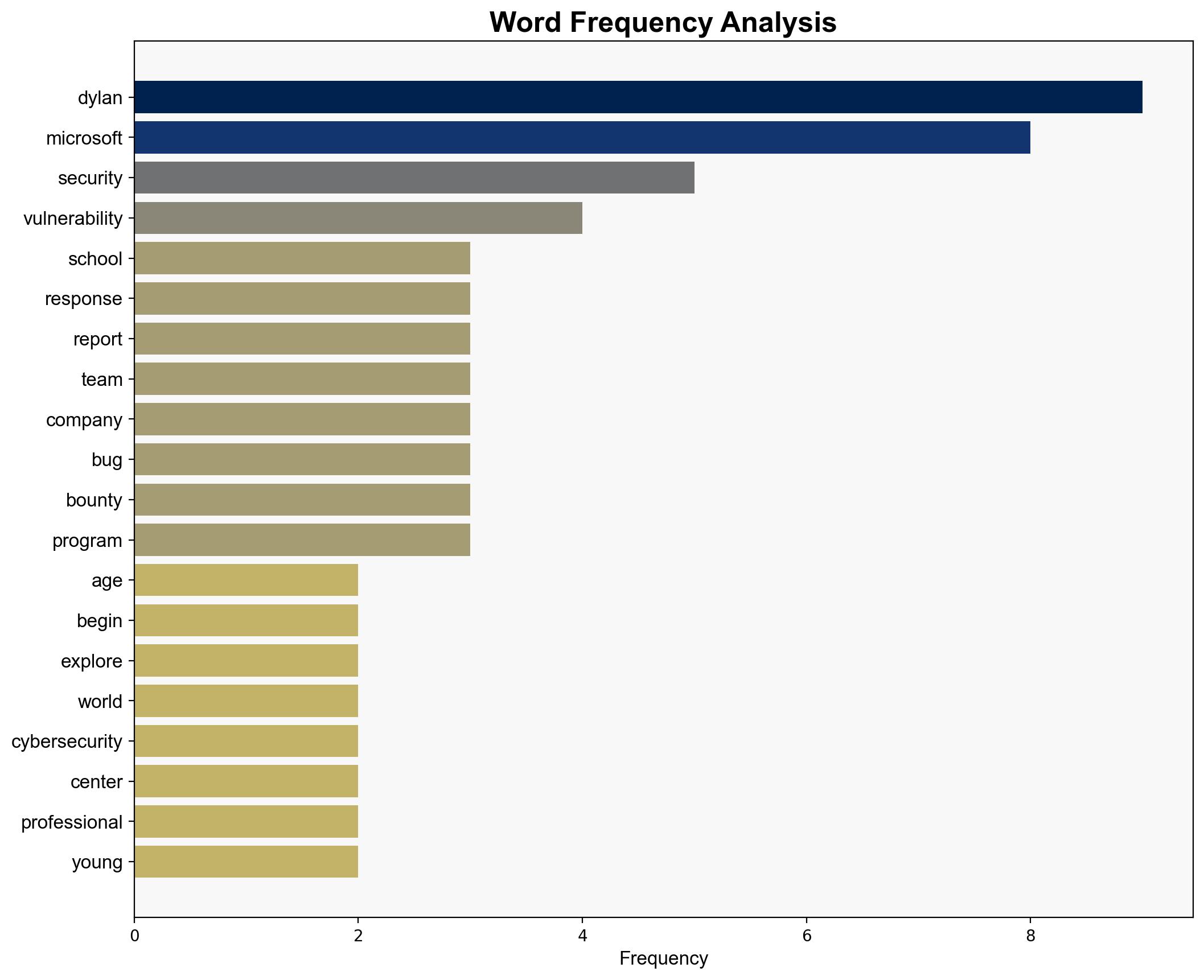
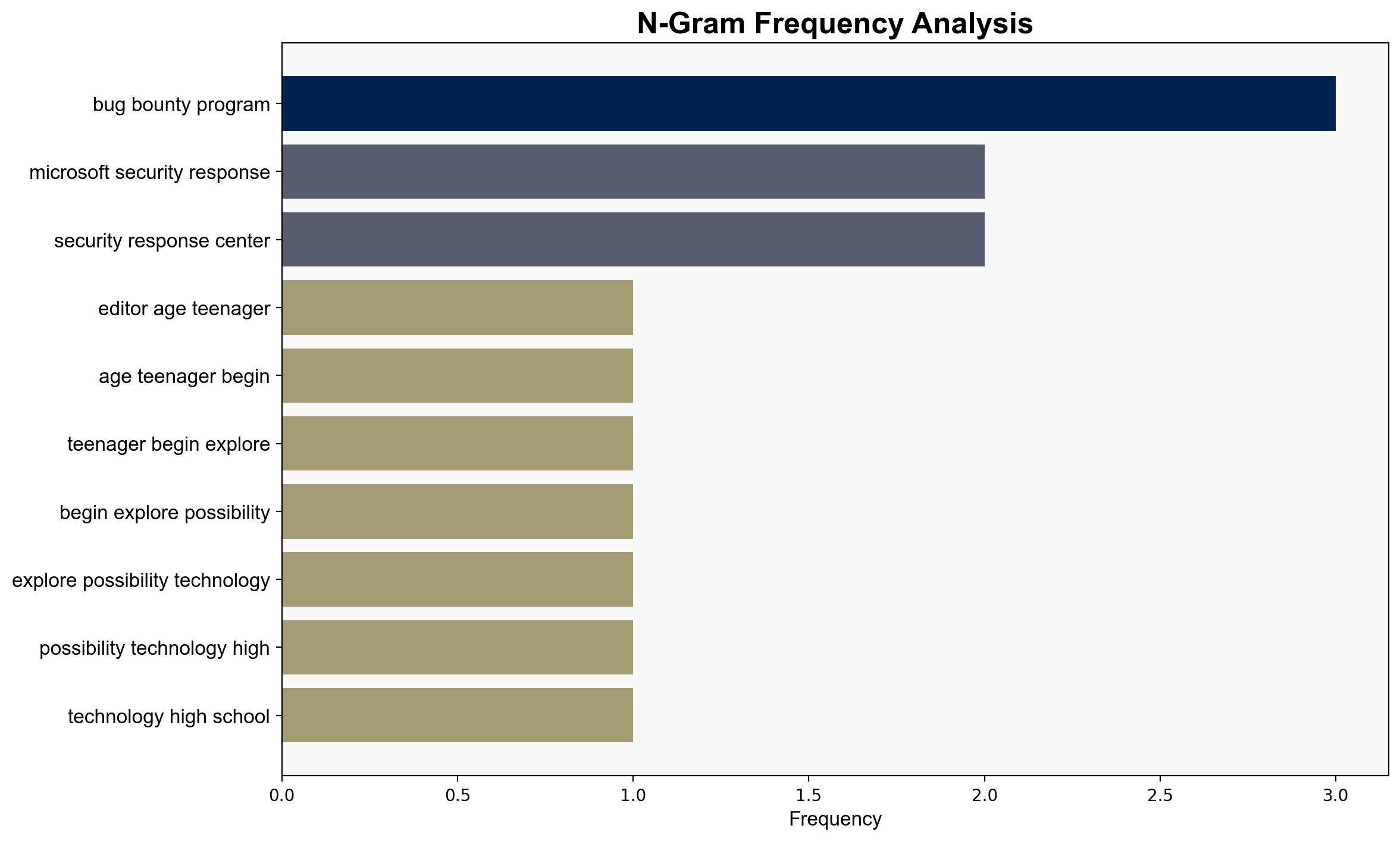
A 17-year-old named Dylan has significantly impacted Microsoft’s bug bounty program by identifying a critical vulnerability, prompting the company to revise its program to include younger participants. This case highlights the importance of engaging diverse talent in cybersecurity to enhance threat detection and response capabilities. It is recommended that similar programs consider expanding their participant criteria to leverage untapped potential in younger demographics.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
By simulating potential actions of cyber adversaries, vulnerabilities like the one Dylan discovered can be anticipated, allowing for improved resilience strategies.
Indicators Development
Developing indicators to detect behavioral or technical anomalies can facilitate early threat detection, similar to how Dylan identified the vulnerability.
Bayesian Scenario Modeling
Using probabilistic inference to quantify uncertainty, this technique can help predict cyberattack pathways and prepare defenses accordingly.
3. Implications and Strategic Risks
The case underscores the potential for emerging cybersecurity threats from unexpected sources, such as young independent researchers. This could lead to systemic vulnerabilities if not properly managed. The expansion of bug bounty programs to include younger participants could mitigate these risks by harnessing diverse perspectives.
4. Recommendations and Outlook
- Encourage cybersecurity programs to include younger participants to tap into diverse talent pools.
- Implement continuous monitoring and simulation exercises to anticipate and mitigate vulnerabilities.
- Scenario-based projections suggest that expanding participant criteria could lead to increased vulnerability detection (best case), while failure to do so may result in missed threats (worst case). The most likely scenario involves gradual adaptation and integration of younger talent.
5. Key Individuals and Entities
Dylan, Microsoft Security Response Center (MSRC)
6. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus