Microsoft Addresses High-Risk Windows LNK Vulnerability Targeted in Zero-Day Exploits
Published on: 2025-12-03
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Microsoft mitigates Windows LNK flaw exploited as zero-day
1. BLUF (Bottom Line Up Front)
Microsoft has implemented a mitigation for the CVE-2025-9491 Windows LNK vulnerability, which has been exploited by state-backed and cybercrime groups in zero-day attacks. Despite the mitigation, the flaw continues to pose a risk due to its exploitation by sophisticated actors. The most likely hypothesis is that the mitigation will reduce but not eliminate the threat, given the persistence of threat actors and the complexity of the cyber landscape. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: Microsoft’s mitigation will significantly reduce the exploitation of the CVE-2025-9491 vulnerability. Supporting evidence includes the change to LNK file properties allowing users to see all characters in the Target field. However, the mitigation is not a complete fix, and user interaction is still required for exploitation.
- Hypothesis B: The mitigation will have limited impact on reducing exploitation due to the sophistication of threat actors and potential bypass techniques. Evidence includes ongoing exploitation by advanced groups and the existence of a Mark of the Web bypass vulnerability.
- Assessment: Hypothesis B is currently better supported due to the continued activity of state-backed groups and the complexity of the threat landscape. Indicators that could shift this judgment include reports of decreased exploitation rates or new vulnerabilities being exploited.
3. Key Assumptions and Red Flags
- Assumptions: The mitigation is correctly implemented across all affected systems; threat actors will continue to seek alternative exploitation methods; user behavior regarding opening suspicious files remains unchanged.
- Information Gaps: Detailed technical analysis of the mitigation’s effectiveness; comprehensive data on exploitation rates post-mitigation; insights into threat actor adaptation strategies.
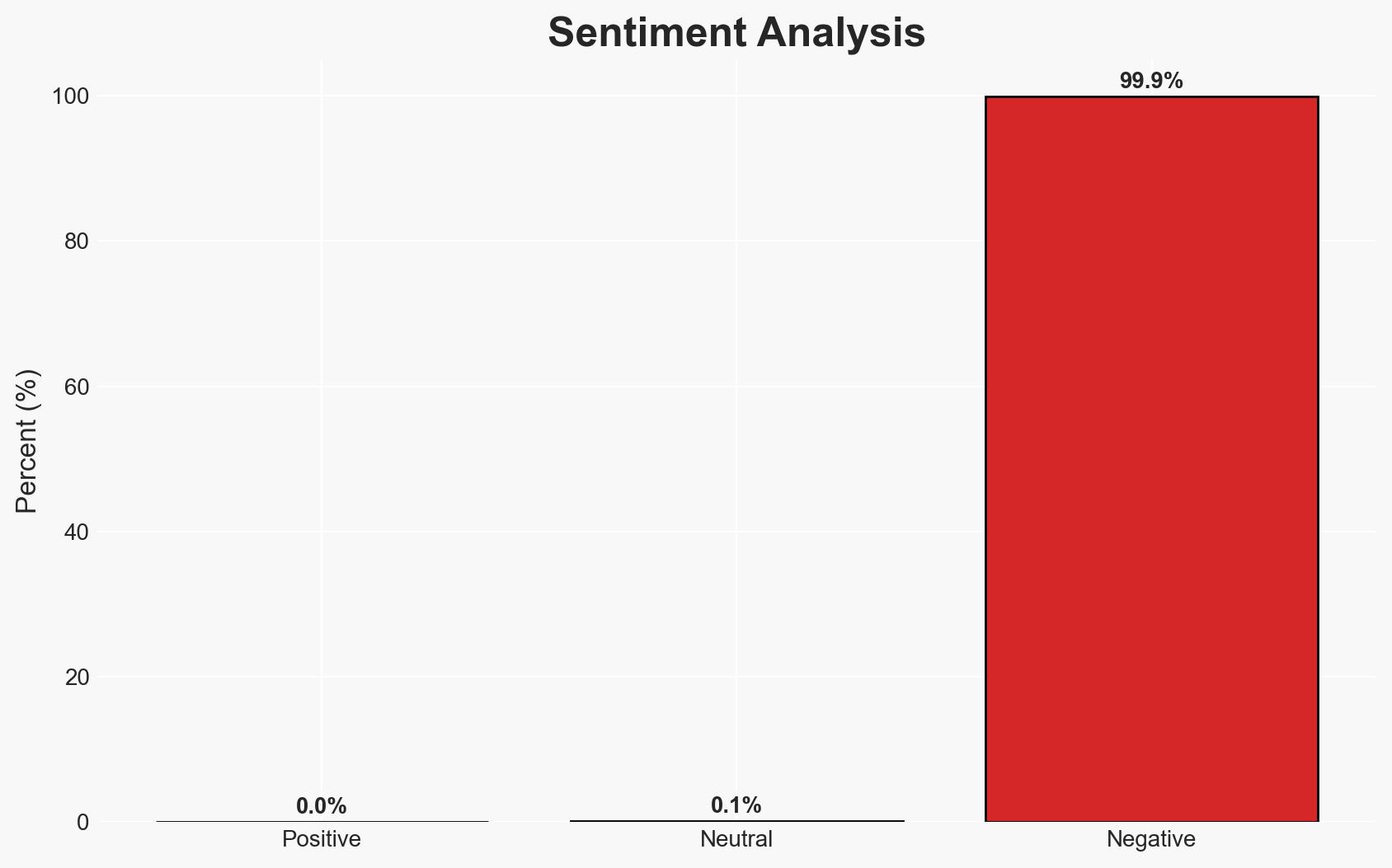
- Bias & Deception Risks: Potential bias in reporting from cybersecurity firms with vested interests; risk of underestimating threat actor capabilities and adaptability.
4. Implications and Strategic Risks
The mitigation of the CVE-2025-9491 vulnerability could lead to a temporary reduction in successful attacks, but threat actors are likely to adapt. This development could influence broader cybersecurity strategies and international cyber norms.
- Political / Geopolitical: Potential for increased tensions between nations accused of supporting cyber operations exploiting this vulnerability.
- Security / Counter-Terrorism: Changes in threat actor tactics could alter the operational landscape, necessitating updated defense measures.
- Cyber / Information Space: Increased focus on developing and deploying new cyber defense technologies and strategies.
- Economic / Social: Potential economic impact on organizations targeted by these attacks, leading to increased cybersecurity investments.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Monitor for new exploitation techniques; update cybersecurity protocols to incorporate the latest threat intelligence; educate users on recognizing suspicious files.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms for threat intelligence sharing; invest in advanced detection and response capabilities; conduct regular security audits.
- Scenario Outlook:
- Best: Mitigation leads to significant reduction in attacks, prompting improved international cyber cooperation.
- Worst: Threat actors quickly adapt, exploiting new vulnerabilities, leading to widespread cyber incidents.
- Most-Likely: Continued exploitation at reduced rates, with gradual improvements in mitigation and detection capabilities.
6. Key Individuals and Entities
- Microsoft
- Trend Micro
- Arctic Wolf Labs
- State-backed groups (e.g., Mustang Panda, APT37, APT43)
- Cybercrime gangs (e.g., Evil Corp)
- ACROS Security
7. Thematic Tags
Cybersecurity, zero-day vulnerabilities, state-sponsored hacking, cybercrime, malware, threat mitigation, international cyber norms
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us