Microsoft Addresses Long-Exploited Windows LNK Vulnerability in November 2025 Security Update
Published on: 2025-12-03
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Microsoft Silently Patches Windows LNK Flaw After Years of Active Exploitation
1. BLUF (Bottom Line Up Front)
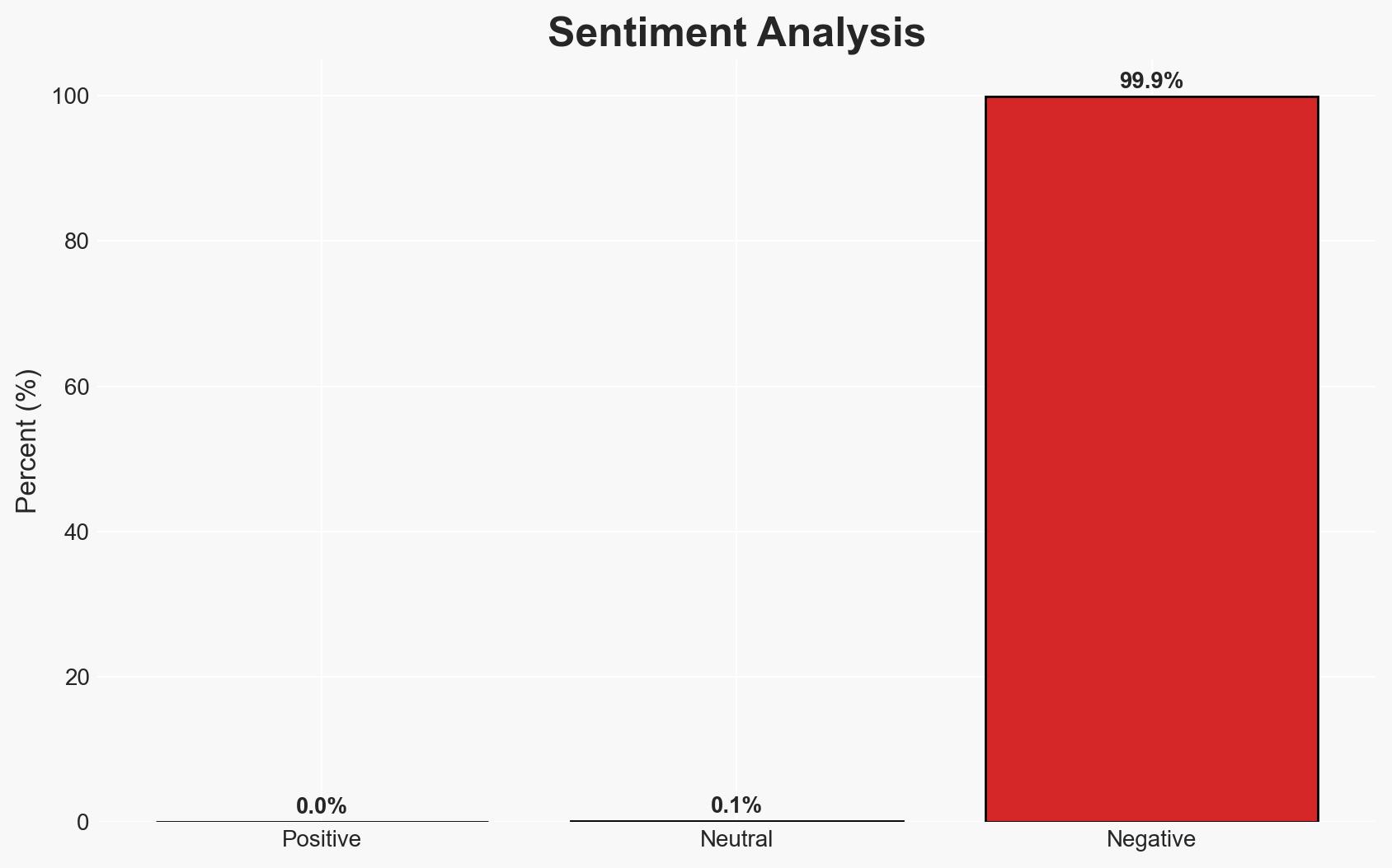
Microsoft has addressed a long-standing Windows LNK file vulnerability (CVE-2025-9491) that has been exploited by state-sponsored threat actors since 2017. The flaw allowed remote code execution through crafted shortcut files. The most likely hypothesis is that the patch was driven by increased exploitation and pressure from the cybersecurity community. This development primarily affects entities targeted by state-sponsored cyber espionage campaigns, with moderate confidence in this assessment.
2. Competing Hypotheses
- Hypothesis A: Microsoft patched the LNK flaw due to increased exploitation by state-sponsored actors and pressure from cybersecurity stakeholders. Supporting evidence includes the recent uptick in attacks and public disclosures by security firms. However, Microsoft’s previous stance that the flaw did not warrant immediate action contradicts this.
- Hypothesis B: The patch was part of a routine update cycle, unrelated to external pressures or specific threat activities. This is supported by Microsoft’s historical approach to patching based on internal prioritization. Contradicting this is the timing of the patch following high-profile exploitation reports.
- Assessment: Hypothesis A is currently better supported due to the alignment of the patch release with increased threat activity and public disclosures. Indicators that could shift this judgment include future statements from Microsoft clarifying their decision-making process.
3. Key Assumptions and Red Flags
- Assumptions: Microsoft was aware of the exploitation scale; state-sponsored actors will continue to seek similar vulnerabilities; the patch effectively mitigates the vulnerability.
- Information Gaps: Details on Microsoft’s internal decision-making process; comprehensive data on the full scope of exploitation; effectiveness of the patch in diverse environments.
- Bias & Deception Risks: Potential bias in public disclosures by cybersecurity firms seeking to highlight their role; Microsoft’s public statements may downplay the vulnerability’s impact.
4. Implications and Strategic Risks
This development could lead to a temporary reduction in exploitation of the LNK vulnerability, but may drive threat actors to seek alternative methods. The patch may influence broader cybersecurity practices and policies.
- Political / Geopolitical: Potential diplomatic tensions if state-sponsored activities are publicly attributed to specific nations.
- Security / Counter-Terrorism: A shift in threat actor tactics, potentially increasing focus on other unpatched vulnerabilities.
- Cyber / Information Space: Increased scrutiny on software vendors’ patching policies; potential rise in zero-day vulnerability markets.
- Economic / Social: Minimal immediate economic impact, but long-term implications for trust in software security could affect market dynamics.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Monitor for new exploitation techniques; ensure patch deployment across affected systems; engage with cybersecurity partners for threat intelligence sharing.
- Medium-Term Posture (1–12 months): Develop resilience measures against similar vulnerabilities; enhance partnerships with software vendors for proactive vulnerability management.
- Scenario Outlook:
- Best: Successful mitigation leads to reduced exploitation and improved cybersecurity practices.
- Worst: Emergence of new vulnerabilities exploited at scale, undermining confidence in software security.
- Most-Likely: Temporary reduction in exploitation with gradual adaptation by threat actors to new vulnerabilities.
6. Key Individuals and Entities
- Microsoft
- ACROS Security
- Trend Micro’s Zero Day Initiative (ZDI)
- HarfangLab
- Arctic Wolf
- State-sponsored groups from China, Iran, North Korea, Russia
7. Thematic Tags
Cybersecurity, state-sponsored threats, vulnerability management, software patching, cyber espionage, Microsoft, information security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us